2025 Best Practices for Procurement
By: Cristina Iani12 August 2024

We love our data, and now that you're here, you're one step closer to loving it too.
A wide sample of data, so you can explore what is possible with our data
Choose ->
built with procurement in mind. Focused on manufacturers, products and more
Choose ->
built with insurance in mind. Focused on classifications, business activity tags and more
Choose ->
built with sustainability in mind. Focused on sustainability commitments, and environmental and social governance insights.
Choose ->
built with strategic insights in mind. Focused on market trends, competitor analysis, and industry-specific data
Choose ->
A wide sample of data, so you can explore what is possible with our data
A wide sample of data, so you can explore what is possible with our data
built with procurement in mind. Focused on manufacturers, products and more
built with insurance in mind. Focused on classifications, business activity tags and more
A wide sample of data, so you can explore what is possible with our data
built with procurement in mind. Focused on manufacturers, products and more
built with insurance in mind. Focused on classifications, business activity tags and more
built with sustainability in mind. Focused on sustainability commitments, and environmental and social governance insights.
built with strategic insights in mind. Focused on market trends, competitor analysis, and industry-specific data

Keep up to date with our technology, what our clients are doing and get interesting monthly market insights.

Unfortunately, these challenges also highlighted the degree of risk to which we are all exposed to, derived from these long and sometimes hard to visualize global business chains.
In this context, third party risk management emerged as a top executive concern and has become a crucial agenda for any company large enough to be exposed to a high degree of risk from the multitude of third parties they are working with, and it all starts from the information level.
Here is a summary of what you can expect to find in the report:

and what are the exact ways to leverage it for a better understanding of the third parties that your organization is working with and how they might impact the flow of goods, information or become a liability from an asset? We’re exploring all the unique data points that are crucial for rethinking TPRM with several steps ahead of trouble and keeping your organization safe.
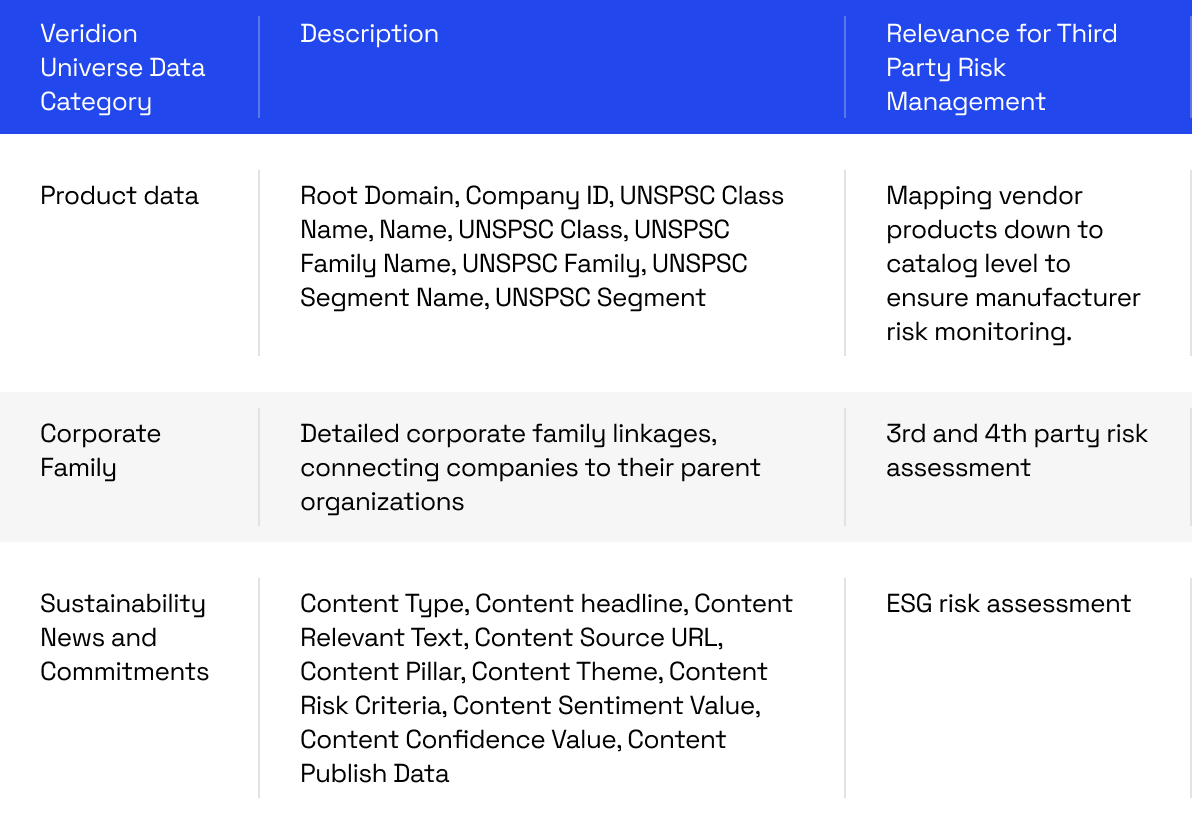





Deep dive into the key challenges for developing timely TPRM initiatives
Learn more about data for TPRM
“Securing Third Party Risk Management with the Right Data”
Effective TPRM often requires you to have solid and carefully thought out alternatives ahead of disruption actually taking place. The report discusses how you can build this kind of resilience that companies increasingly need.
Gain the insights you need to discover whether one of your suppliers will not be able to meet your demand due to climate events or if one of your partners is connected to another business entity that faces sanctions or poses a reputational risk for you.
Get a better idea of the challenges that can hinder your TPRM progress so you can preemptively address them starting from a position of strength.
Have a better overview over the crucial data sets that you must plan around in order to make the informed decisions and backups that will consolidate your TPRM strategy.
