What is Third Party Risk Management (TPRM)


Key Takeaways:
Third parties keep your business running.
They power your supply chain, support your operations, and connect you with critical services.
But every vendor you work with also brings risk.
A single weak link can trigger disruptions, compliance failures, financial losses, or reputational damage that ripple across your entire organization.
Managing these risks requires a structured discipline called Third Party Risk Management (TPRM).
In this article, we explain what TPRM is, why it matters, the main risks to watch for, and the best practices to protect your vendor ecosystem.
Third Party Risk Management (TPRM) is the process of identifying, assessing, and reducing risks that come from working with outside organizations.
That could be vendors, suppliers, partners, contractors, or service providers.
In large enterprises, these third parties often have direct access to sensitive systems, data, and operations.
A single weakness on their side can open the door to problems on yours.
To put it into perspective, Deloitte’s Global Survey found that 87% of companies experienced a third-party incident that disrupted their operations.

Illustration: Veridion / Data: Deloitte
This highlights how widespread third-party risks are, and why managing them should be a priority.
While cybersecurity is a major part of TPRM, the scope is broader.
A well-structured program also addresses operational disruptions, compliance failures, financial risks, strategic underperformance, and potential damage to your reputation.
By managing these areas proactively, you reduce the chance of small issues escalating into costly business setbacks.
Ultimately, a strong TPRM program gives you visibility into your third-party network—who they are, how you rely on them, and what safeguards they maintain.
Third-party risks rarely exist in isolation.
A single incident, such as a vendor’s data breach, can set off a chain reaction, shutting down operations, drawing regulatory attention, draining financial resources, and damaging your reputation all at once.
Below are the most common types of third-party risks, explained with real examples.
Cybersecurity risk arises when a vendor’s systems or products contain vulnerabilities.
It can surface anywhere in your network of third parties, and when they do, the consequences can be severe.
A single breach can expose sensitive data, disrupt services, and erode customer trust.
Unfortunately, statistics reveal that too many companies are constantly dealing with third-party cybersecurity risks.
In 2023, a CyberGRX and ProcessUnity survey found that over 60% of organizations had experienced a third-party cyber incident.
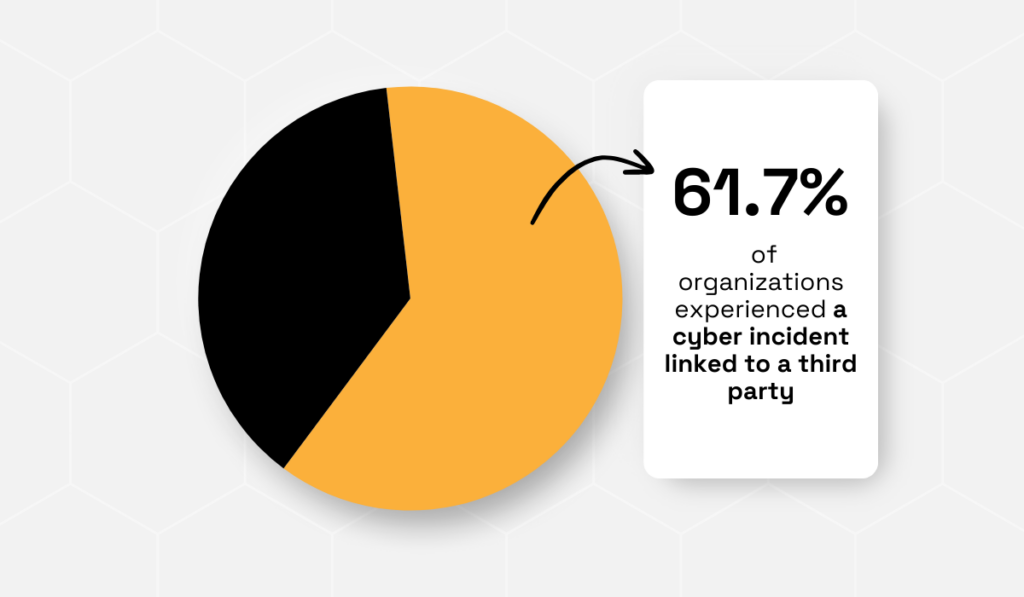
Illustration: Veridion / Data: Cyber GRX
A striking example is the SolarWinds attack in 2020, where hackers inserted malicious code into a software update, infiltrating thousands of organizations, including U.S. government agencies.
Losses averaged $12 million per affected company, showing the scale of supply chain breaches.

Source: Heimdal
All in all, cybersecurity threats can quickly spread, disrupting operations and causing lasting financial and reputational harm to everyone involved.
Operational risk arises when a third party can’t deliver the products or services your business depends on.
This can happen for many reasons, from process failures and human error to natural disasters, IT outages, or cyberattacks.
These issues, regardless of their source, can interrupt normal operations and slow down your organization’s work.
In a recent EY survey of 500 corporate executives from major companies, 57% said operational risk is their top concern in managing third parties.

Illustration: Veridion / Data: EY
This reflects how heavily organizations depend on vendor reliability.
Without backup suppliers or clear contract standards, a single disruption can stall entire operations.
Many industries are governed by strict regulations such as GDPR, HIPAA, or PCI-DSS.
If a third party fails to comply, both they and your organization face fines, lawsuits, and business interruptions.
The challenge multiplies when different vendors follow different rules. One supplier may fall under GDPR, another under sector-specific standards, creating confusion and potential gaps.
Effective TPRM requires knowing which regulations apply and ensuring every vendor aligns with them.
Reputation risk is the potential damage to your brand’s credibility and public image when customer trust is broken.
That trust is directly tied to your revenue, company value, stock price, and future opportunities. The challenge is even bigger when third parties are involved.
If a vendor acts unethically or makes a serious mistake, your customers won’t always see the difference between their actions and your own.
Reputational risk in the supply chain can surface in many ways:
A recent example is Marks & Spencer in 2025, when attackers exploited a supplier to launch a ransomware attack.

Source: The Grocer
The incident forced the company’s online store offline, erased £750 million in market value, and triggered a 21% drop in customer willingness to recommend the brand.
This shows how vendor mistakes can become your crisis, with long-lasting trust implications.
Financial risk comes into play when a vendor’s money problems become your problem.
If a vendor struggles with funding, loses customers, or carries heavy debt, they may fail to meet obligations, deliver subpar services, or miss deadlines.
Suddenly, deliveries slow down, product quality drops, and your business is left to deal with unhappy customers and lost sales.
In some cases, you might even face fines or unexpected costs to fix the damage.
The collapse of Carillion in 2018 illustrates this.

Source: Supply Chain Digital
Once one of the UK’s largest outsourcing suppliers, its insolvency left hospitals, schools, and transport projects in chaos.
Hundreds of subcontractors went unpaid, causing widespread financial losses.
For procurement teams, the Carillion case is a clear reminder of how a vendor’s financial instability can quickly spill over into your own operations.
That’s why it’s critical to monitor their financial stability and run regular supplier audits.
Strategic risk happens when a third party’s actions don’t align with your organization’s long-term goals.
For example, a vendor that cuts corners on quality, misses delivery deadlines, or doesn’t treat your partnership as a priority can slowly undermine your strategy.
The risk grows even larger if the vendor faces internal challenges, like frequent leadership changes, outdated technology, or high employee turnover, all of which can weaken their ability to support your objectives.
A well-known case is Boeing’s 787 Dreamliner project, where reliance on a wide network of suppliers led to coordination issues, delays, and quality problems.
Several vendors struggled to meet expectations, forcing Boeing into costly fixes and delays that hurt both its reputation and profitability.

Source: Supply Chain Digital
When left unchecked, these misalignments don’t just create short-term frustration.
They can hold back innovation, damage customer relationships, and even derail key initiatives.
Managing third-party risk sounds simple in theory.
Assess your vendors, spot the weaknesses, and put safeguards in place.
In practice, large organizations often deal with hundreds or thousands of third parties, each with unique contracts, systems, and risks.
This scale creates blind spots, making effective management far more complex.
Below are three of the most common challenges organizations face.
When businesses rely on too many third-party vendors without proper control, they experience vendor sprawl.
At first, it may feel like more vendors mean more support, but over time, the opposite is true.
With dozens or even hundreds of partners, it becomes harder to track performance, monitor compliance, or spot security weaknesses.
Instead of supporting the business, a sprawling vendor network increases exposure to cyber threats and regulatory scrutiny.
Research underscores how quickly vendor networks can grow.
SecurityScorecard found that information services firms manage an average of 25 third-party vendors, healthcare averages 15.5, while finance manages 6.5.
Some large enterprises manage hundreds or even thousands of third-party relationships, making oversight extremely complex.
On a global scale, 59% of organizations source vendors from five or fewer countries, but 14% manage vendors across ten or more.
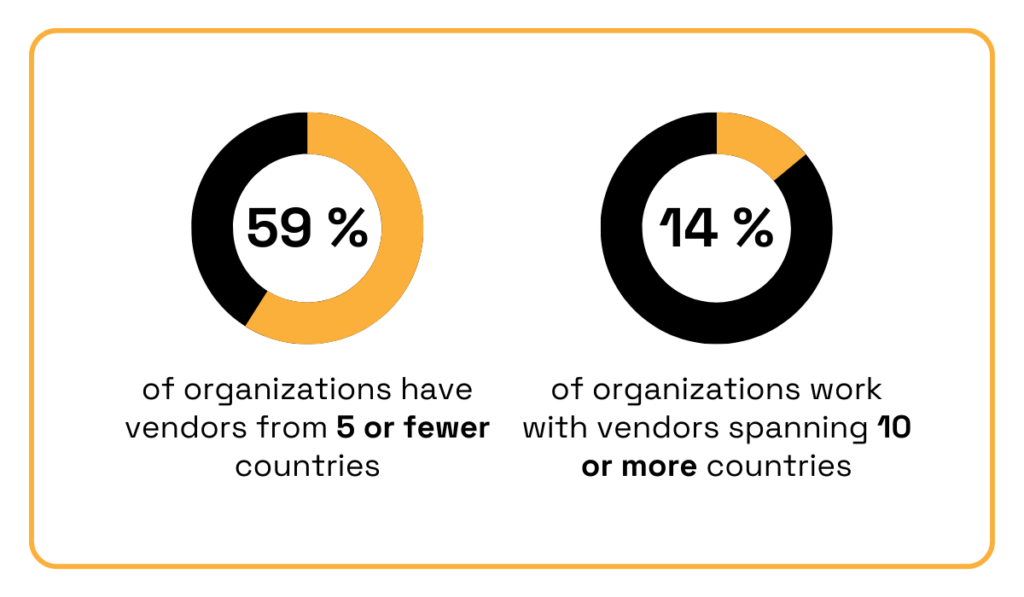
Illustration: Veridion / Data: SecurityScorecard
These figures show that vendor sprawl is not a rare issue—it’s a structural challenge across industries.
The more vendors and regions involved, the harder it becomes to monitor risks consistently.
Inefficient manual processes make third-party risk management harder than it needs to be.
Spreadsheets, emails, and ad hoc tracking might work in the beginning, but they don’t scale as vendor networks grow.
Assessments take longer, human error creeps in, and important details slip through the cracks.
A common example is the vendor cybersecurity self-assessment questionnaire, which often runs 200+ questions and is completed only once a year.
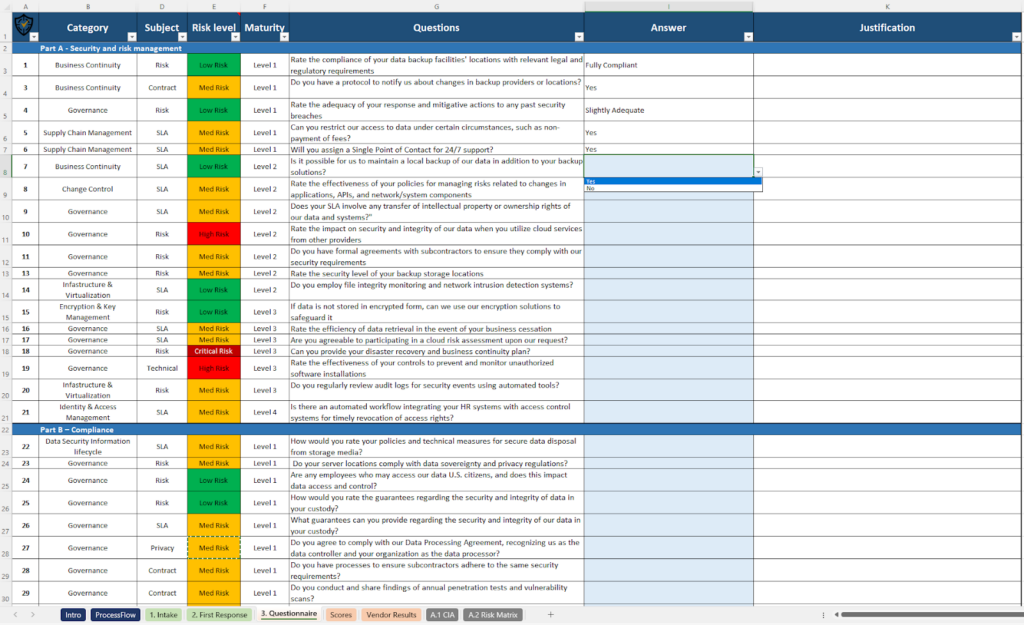
Source: Cyberzoni
This approach to TPRM is not only time-consuming but also limited in scope, and relies heavily on how honest or accurate the vendor’s answers are.
Emma Smith, CISO at Vodafone, points out that this traditional approach to TPRM is still a problem across all sectors:
“How do we stop this paper chase of questionnaires and assessments? This is a problem that spans all sectors; solving it has to be an industry effort.”
Her point reflects a broader truth: as long as organizations depend on manual processes, third-party risk management remains slow, fragmented, and prone to blind spots.
Strong TPRM depends on security, procurement, legal, compliance, and business teams working together.
But in many organizations, these departments operate in silos, each with different priorities and fragmented data.
In fact, according to IBM, 82% of enterprises report that data silos disrupt their workflows, while 68% of enterprise data remains unanalyzed.
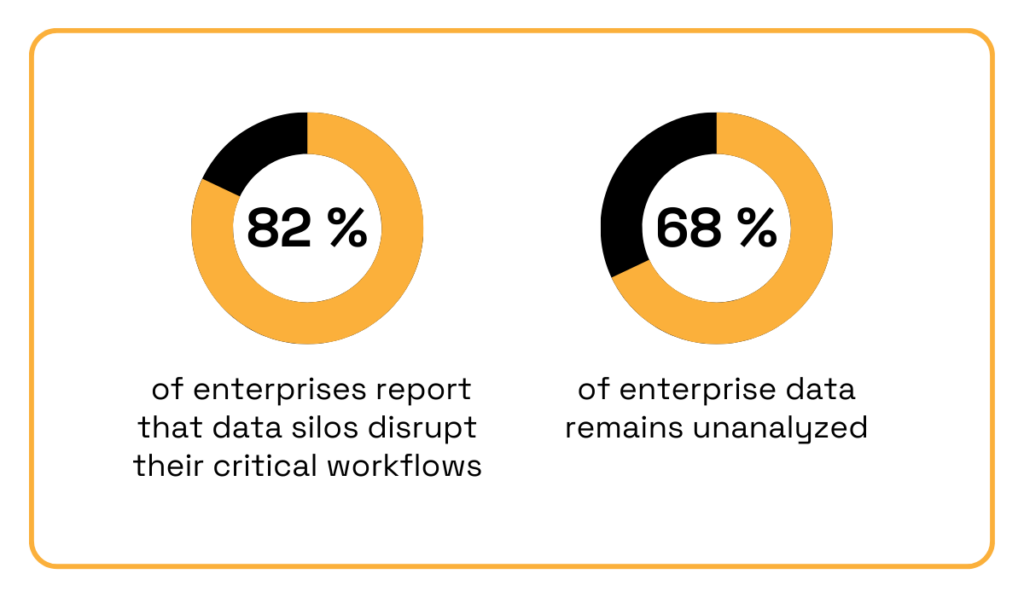
Illustration: Veridion / Data: IBM
This lack of coordination leads to inconsistent vendor evaluations, duplicated efforts, and unclear accountability.
Without a unified approach, organizations end up with blind spots in risk coverage, leaving them vulnerable to the very issues TPRM is meant to prevent.
The challenges of third-party risk management may seem overwhelming, but they’re not impossible to overcome.
With the right practices, you can move from reacting to vendor problems to preventing them altogether.
Here are three proven approaches that strengthen TPRM programs.
Procurement teams are the first line of defense. Their choices decide whether risk enters the supply chain or stays out.
By involving procurement early, risk requirements can be built into vendor evaluations, RFP scoring, and contract negotiations, so weak spots are caught before the contract is signed.
According to Deloitte’s 2021 Global CPO Survey, procurement leaders are no longer just cost-cutters.
They drive innovation, guide demand, and team up with suppliers to stay compliant while scaling faster.
Their expanded role makes them vital partners in third-party risk management.
Ed Thomas, Senior Vice President at ProcessUnity, points out a statistic worth noting:

Illustration: Veridion / Source: Procurement Magazine
This is why bringing procurement in early matters.
Their decisions lay the foundation for stronger partnerships and fewer surprises down the road.
Not all vendors pose the same level of risk, and treating them like they do spreads your resources too thin, and leaves the most critical suppliers under-monitored.
Vendor tiering solves this problem by classifying partners based on their access, criticality, and data sensitivity.
The table below breaks down vendor risk into clear tiers, helping you understand which partners require the highest level of oversight:
| Risk Tier | Vendor Access | Vendor Services |
|---|---|---|
| 1 – Critical | Highly sensitive data, critical network infrastructure, core revenue-generating systems | CSPs, MSSPs, banking, payroll |
| 2 – High | Important, but perhaps not immediately catastrophic, data or systems | Marketing operations, customer support, HR |
| 3 – Moderate | Limited or indirect access to sensitive data or critical systems | Productivity suites, physical security, facilities management |
| 4 – Low | No direct access to critical systems or sensitive data | Catering, landscaping, one-off software purchase |
Source: Safe
For example, critical vendors, such as payroll providers, banks, or cloud service platforms, require the highest level of oversight, while low-risk vendors, such as catering or landscaping, require far less.
By segmenting vendors according to inherent risk, business criticality, and data sensitivity, you can manage risk more strategically and avoid wasting time on low-impact partners.
When your vendor network spans hundreds or even thousands of suppliers, relying on spreadsheets and manual workflows simply isn’t sustainable.
It slows down decision-making, introduces inconsistencies, and leaves too much room for human error.
That’s why automation has become a cornerstone of modern TPRM.
It allows organizations to move faster, apply consistent evaluation standards, and respond to risk signals in real time.
For enterprises managing complex supply chains, real-time data enrichment is especially critical.
Instead of relying on outdated questionnaires or static reports, enriched data ensures every vendor profile is current, complete, and risk-relevant.
Veridion streamlines this process through its big data platform, which covers more than 130 million companies worldwide.
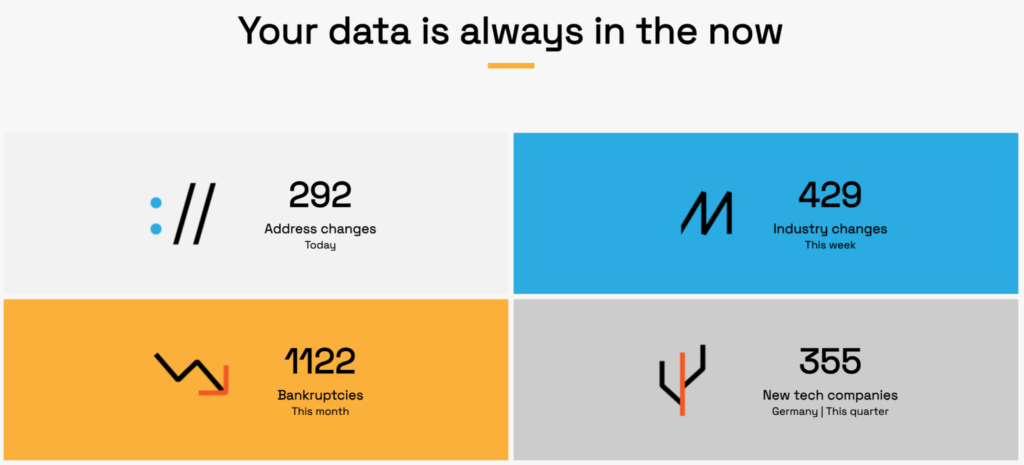
Source: Veridion
This breadth makes it far less likely that third-party providers remain hidden in the supply chain.
The platform automatically aggregates essential details such as ownership structures, corporate family trees, geographic footprint, and firmographic data.
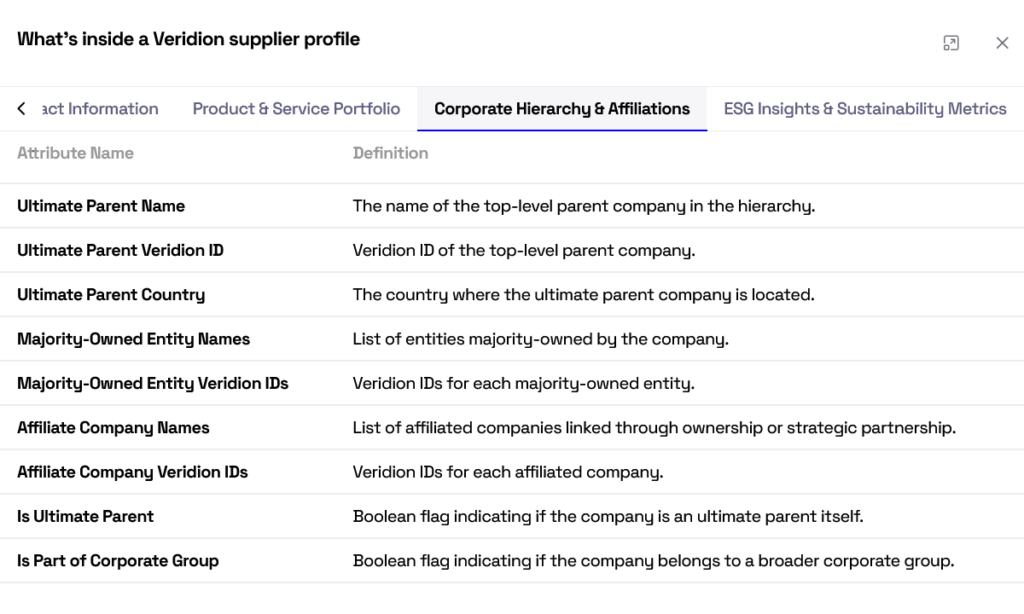
Source: Veridion
With this visibility, teams can quickly identify red flags like foreign ownership, concentration in unstable regions, or opaque corporate hierarchies.
Beyond structural risk, Veridion also enriches data with insights into supply chain exposure, product categories, and ESG performance, helping organizations spot issues such as environmental violations or social compliance risks.
By combining automation with enriched supplier intelligence, enterprises can shift from reactive risk checks to proactive, data-driven TPRM.
Every new third party adds value, but also introduces risk.
Left unmanaged, those risks can grow quietly until they surface as major disruptions.
That’s why organizations need a deliberate approach to oversight.
A strong TPRM program provides visibility into vulnerabilities, the ability to act early, and the assurance that your vendor network supports business growth instead of threatening it.