Debunking 5 Common Myths About Third Party Risk Management


Key Takeaways:
You’ve outsourced the work, but can you outsource the risk?
Third-party risk management is often dismissed as a mere compliance checkbox, and many companies assume their current approach is sufficient.
But some of the most common “truths” leaders rely on are nothing more than myths. These myths create dangerous blind spots, leaving organizations vulnerable to breaches and disruptions.
Organizations that fall prey to these misconceptions often miss early warning signs that could prevent supply chain disruptions altogether.
In this article, we debunk five TPRM misconceptions and show you a clearer, more strategic view of how effective TPRM can protect your business, strengthen resilience, and improve vendor decisions.
Many procurement teams still believe that third-party risk scales with the number of vendors they use.
That’s misleading.
You might think a small supplier list means less risk to manage, but risk doesn’t scale with vendor count.
Risk is determined by access, not quantity.
A single vendor with access to your critical systems can cause more damage than dozens of low-risk suppliers combined.
Look at recent history.
Marks & Spencer’s cyber-attack was traced to a third-party supplier, and it hit the business hard.
Their online platform went down for weeks following the incident, leading to over £40 million in weekly losses.

Source: Connect CeFPro
This wasn’t some massive vendor network failure. One compromised entry point brought down a national retailer.
The 2013 Target breach started the same way.
Attackers used credentials from a small HVAC subcontractor to move into Target’s network.
That compromise exposed 40 million payment card records and cascaded into huge costs and reputational damage.
Source: NBC News
Here’s what attackers know that many procurement teams don’t: smaller vendors often have weaker security.
They make the perfect backdoors into larger enterprises.
You could manage just five vendors and still face catastrophic risk if one of them has privileged access to your data.
As Siân John, CTO at NCC Group, a cybersecurity consulting firm, warns:

Illustration: Veridion / Data: Cybernews
The numbers don’t lie either. Data breaches cost an average of $4.88 million in 2024.
That’s too expensive to gamble on assumptions.
The reality, however, is simple: any vendor with access to sensitive data, critical systems, or customer information needs robust risk management.
When you share your assets with an outsider, TPRM becomes essential. It doesn’t matter if it’s one vendor or one thousand.
Understanding that risk extends beyond vendor quantity leads us to another vital insight: not all vendors deserve equal attention, as they present different levels of risk.
If you’re applying the same level of scrutiny to your cloud infrastructure provider as you do to your employee training software, you’re wasting resources and creating dangerous blind spots in your risk management strategy.
This flawed approach is surprisingly common.
According to a 2023 Navex Global survey, 27% of organizations apply the same risk management process to all third parties, regardless of their actual risk level.
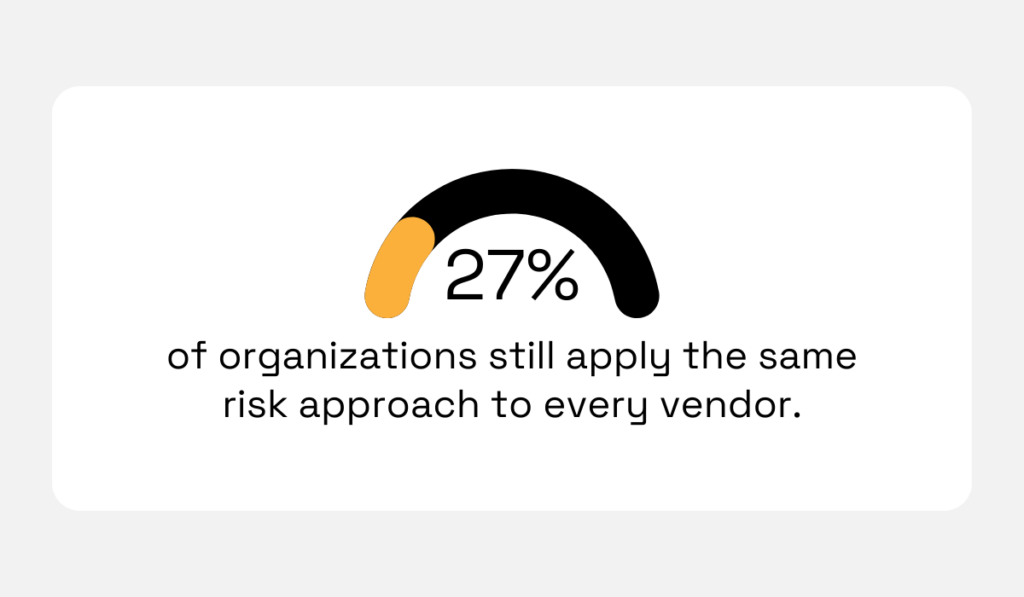
Illustration: Veridion / Data: Navex
This mistake stems from a fundamental misunderstanding of how vendor relationships impact your business operations.
For instance, your marketing agency handles brand assets, while your payment processor handles millions in transactions and sensitive financial data.
These aren’t the same.
Treating them identically wastes resources on low-risk vendors and creates dangerous oversights with high-risk ones.
And the consequences are real.
An EY study found that operational risk tops the list of executive concerns in third-party risk management.

Illustration: Veridion / Data: EY
When a critical vendor fails, it directly disrupts core business functions.
Instead of treating all vendors equally, prioritize them based on their actual impact on your business.
Focus deeper assessments on high-impact relationships and maintain proportional oversight for the rest.
The Kraljic Matrix offers a proven starting point.
Originally developed as a supplier management model, it can also be adapted for TPRM.
It segments suppliers into four categories—Strategic, Leverage, Bottleneck, and Non-Critical—based on profit impact and supply risk.
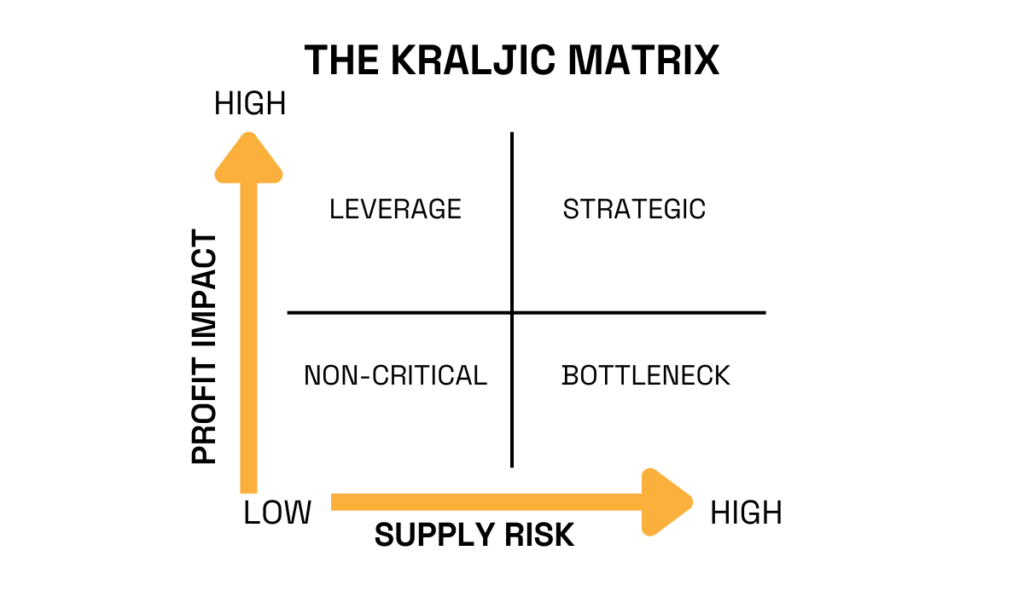
Source: Veridion
Each category gets its own tailored management strategy.
To make this work in practice, build your tiering system around key dimensions such as data sensitivity, business criticality, regulatory exposure, geographic risk, financial stability, and cybersecurity maturity.
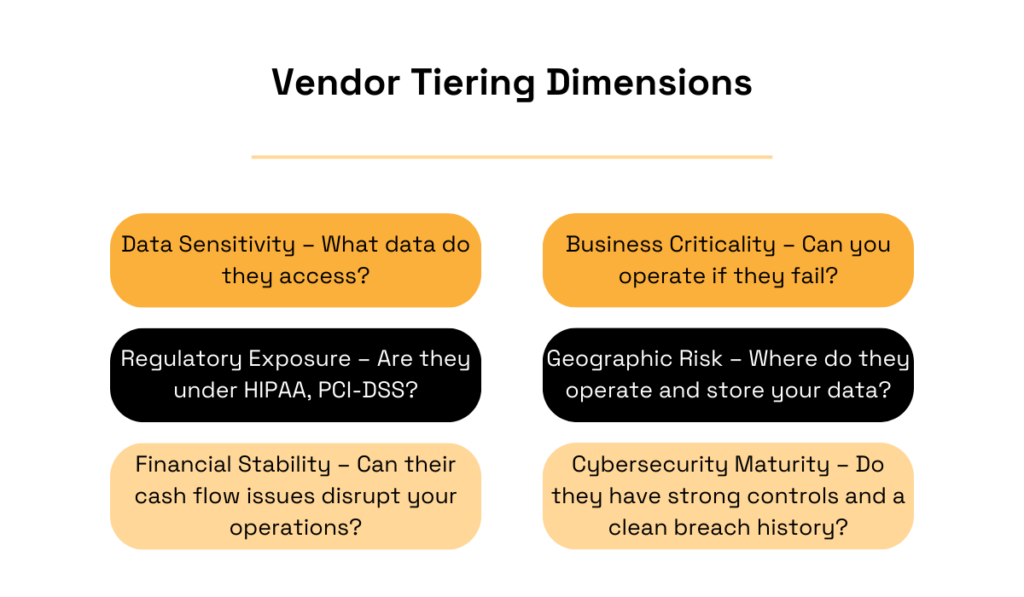
Source: Veridion
By segmenting your vendor base into risk tiers (typically critical, high, medium, and low), you can allocate resources where they matter most.
High-risk vendors can undergo quarterly assessments and continuous monitoring, while low-risk vendors receive annual reviews.
This approach guarantees that high-risk relationships get the attention they deserve, while low-risk ones don’t drain your budget.
Ultimately, you strengthen your overall risk posture without overspending on low-priority oversight.
This is a myth that sounds logical but backfires.
You might think bombarding vendors with risk assessment questionnaires gives you better visibility.
Actually, it does the opposite.
Lengthy questionnaires create information overload. They dilute your focus instead of sharpening it.
And what happens when you overwhelm vendors with endless assessments?
They take shortcuts by:
This “questionnaire fatigue” produces rushed, inaccurate data.
Your procurement team then wastes time sifting through unreliable information, while real red flags slip away unnoticed.
When that happens, the consequences aren’t just inefficiency—they’re costly.
According to a Mitratech report, 61% of companies experienced a vendor-related data breach in 2023.
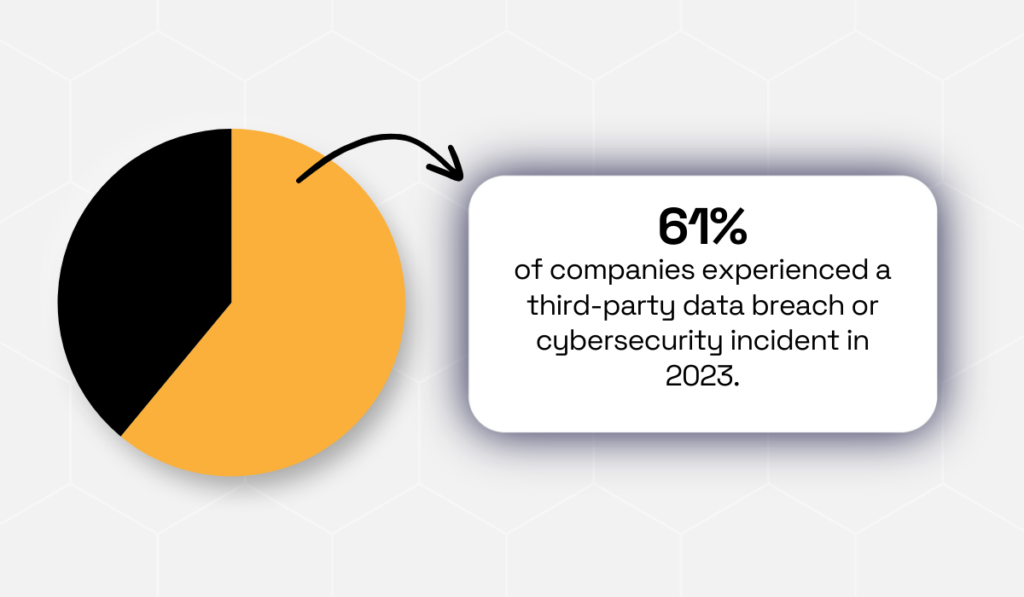
Illustration: Veridion / Data: Mitratech
These breaches often trace back to overlooked risks, showing how missed warning signs can quickly escalate into multimillion-dollar losses.
So, what’s the better approach?
Tailor your assessments to actual risk levels.
Start with a brief, adaptive questionnaire that scales based on each vendor’s profile. Don’t use the same stereotyped survey for everyone.
This shift is becoming the industry standard—and for good reason.
According to EY’s 2023 Global Third-party Risk Management Survey, 63% of organizations are moving toward automation and external data providers.
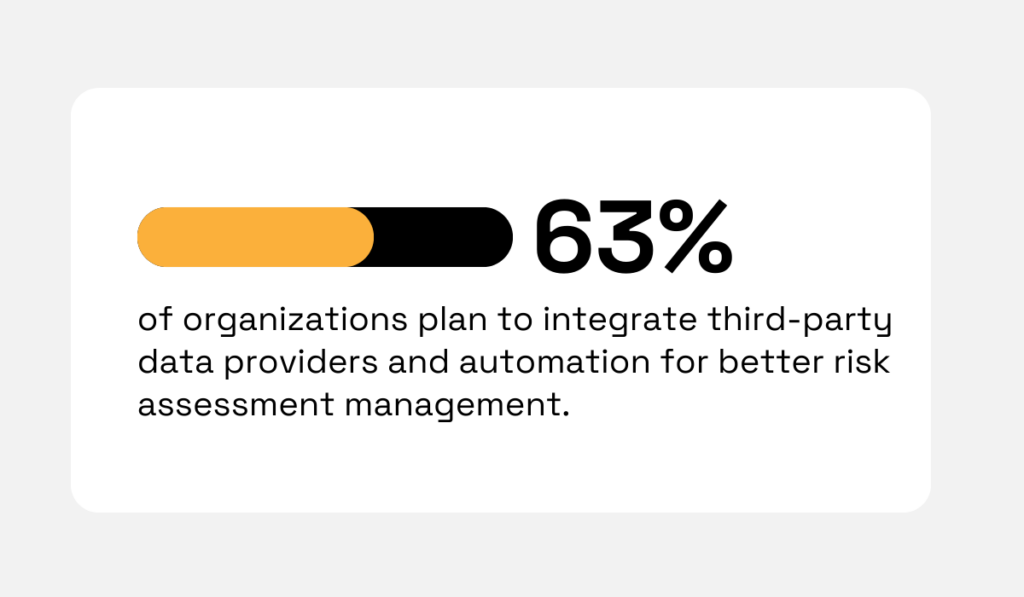
Illustration: Veridion / Data: EY
Why?
Because you can leverage pre-existing data to work smarter, not harder.
For example, security ratings and certifications can pre-fill answers automatically.
SecurityScorecard research shows that 98% of organizations have relationships with at least one breached third party.
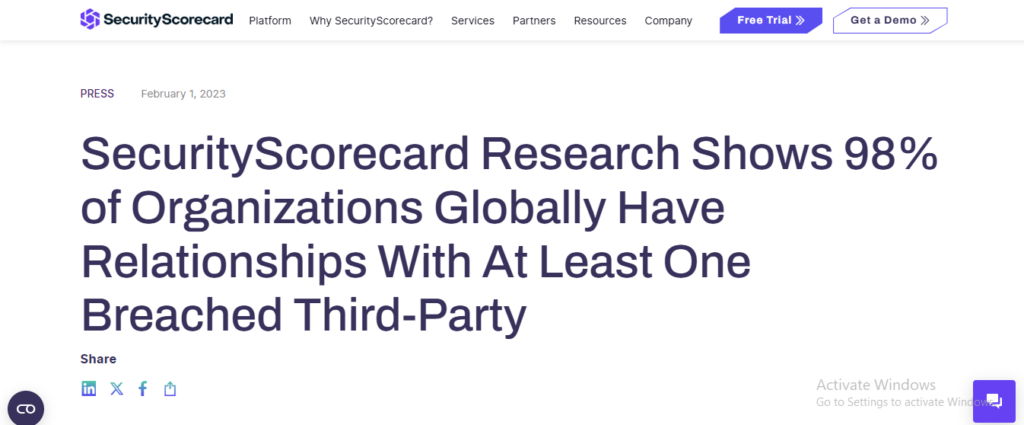
Source: SecurityScorecard
Real-time security ratings help you flag these high-risk vendors before they become problems.
Modern platforms make this possible by automating data collection and flagging anomalies.
But here’s the key part: you need to supplement these lean assessments with continuous monitoring.
A snapshot questionnaire only captures risk on one day. It can’t show you how that risk evolves over time.
Continuous monitoring, by contrast, provides real-time visibility into changes.
By combining continuous, risk-based assessments with automated alerts, you will get deeper visibility without overwhelming your teams with excessive paperwork.
Many companies are still guilty of this:
Treating third-party risk management like a checkbox you tick during vendor onboarding.
Once the vendor is “cleared,” they assume the risk is managed for good.
This complacency is exactly what attackers count on.
Here’s the reality: SecurityScorecard’s 2024 report found that 29% of all data breaches stem from third-party vendors, showing that many organizations stop monitoring after onboarding and miss emerging risks.
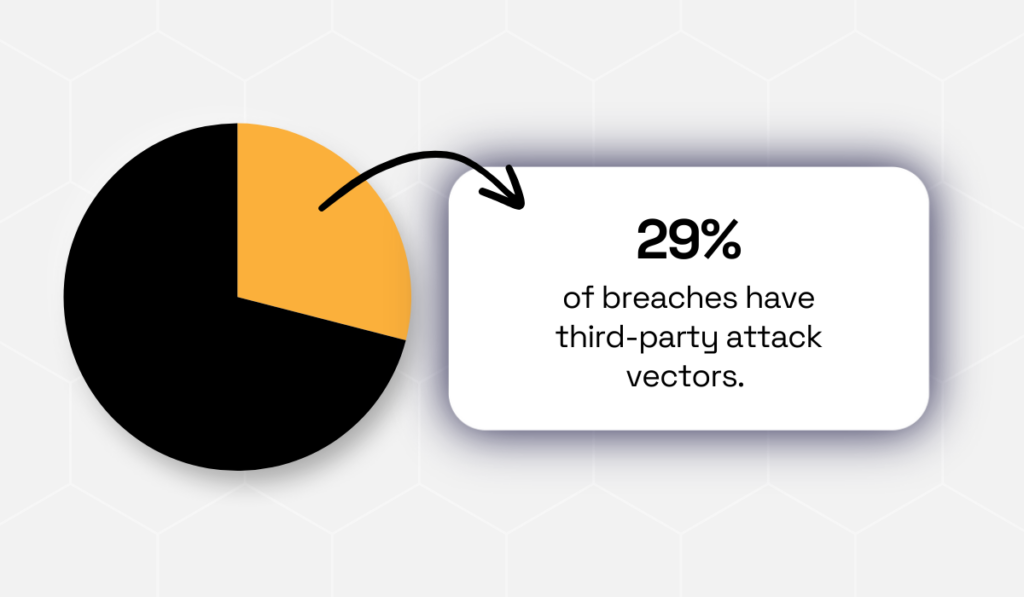
Illustration: Veridion / Data: SecurityScorecard
Vendor risk does not stay frozen in time after your initial assessment. It evolves, shifts, and grows.
That security review you did six months ago? It might already be outdated.
Consider what can happen after you have “cleared” a vendor:
They could suffer a breach like the 2023 MOVEit zero-day vulnerability.
This flaw in a file transfer tool caused massive breaches across multiple organizations through their vendors.
Also, a supplier could get acquired by a foreign company or fall out of regulatory compliance.
Without continuous oversight, these changes create serious blind spots.
Here’s another proof of what happens when oversight fails: the CDK Global ransomware attack.
One vendor’s security failure took down 15,000 automotive dealerships.

Illustration: Veridion / Data: Cyberscoop
Even your most trusted partners can become liabilities without ongoing monitoring.
The solution is to treat TPRM as a continuous process, not a one-time task.
Leading organizations now use continuous security monitoring (CSM) to track vendor risk in real time. CSM automatically pulls from news feeds, threat intelligence, and security reports to detect issues before they escalate.
This matters because, as Aleksandr Yampolskiy, CEO and Co-founder of SecurityScorecard, explains, an organization’s vulnerabilities stem from its technology and that of third-party vendors and partners.

Illustration: Veridion / Quote: SecurityScorecard
This explains why you need visibility across third- and fourth-parties to know whether a partner still deserves trust.
And that’s why a modern TPRM works this way:
Veridion, for instance, continuously updates its global database of 130+ million companies with 200+ attributes per profile.
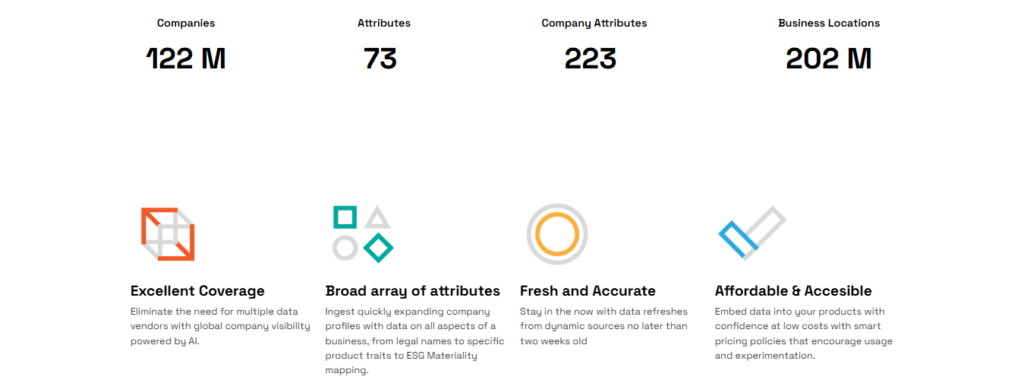
Source: Veridion
When a supplier’s ownership changes or they hit sanctions lists, you get automated alerts.
No manual re-checks needed.
This always fresh and updated TPRM data transforms TPRM from a static checklist into a dynamic defense system.
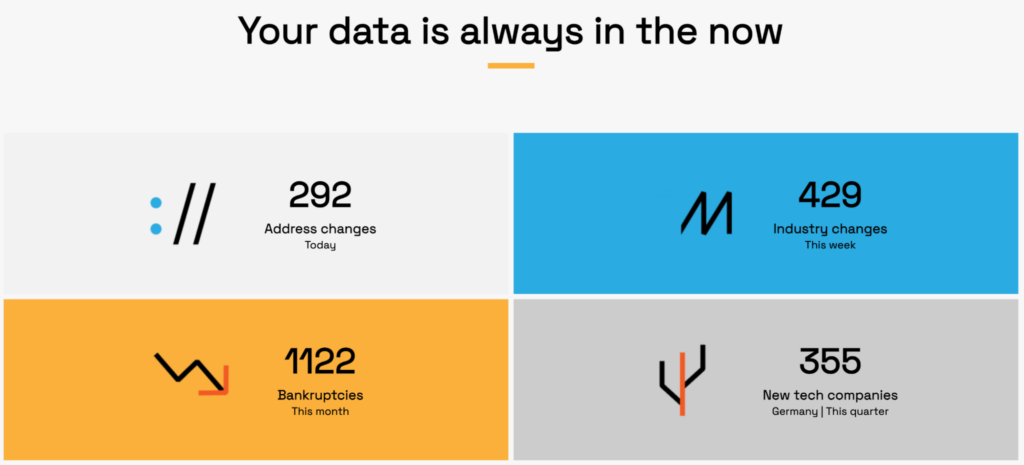
Source: Veridion
You maintain trust with your partners, spot risks as they emerge, and protect your business from evolving threats.
Many organizations assume that complying with regulations and standards automatically means their third-party risk is effectively managed.
Compliance feels safe because it provides a clear checklist.
But why is this problematic?
Well, compliance sets a baseline, not a finish line. Meeting regulatory rules doesn’t necessarily reduce real-world exposure.
When TPRM is treated as a compliance exercise, the focus shifts from preventing vulnerabilities to proving adequacy to auditors.
The result is a false sense of security and unaddressed vulnerabilities.
The 2017 Equifax breach is a cautionary example.
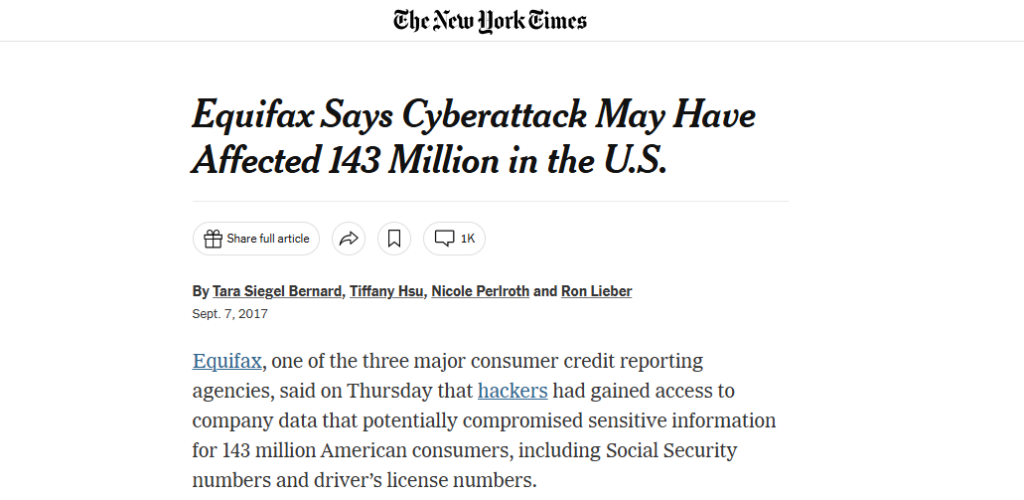
Source: NY Times
Despite operating in a heavily regulated environment, the company was compromised because of an unpatched Apache Struts vulnerability.
This is something a compliance checklist might not have flagged.
The incident exposed personal data of over 140 million people.
Moreover, many regulations only address known risks, leaving the door open for zero-day exploits, cloud misconfigurations, or newer threats like AI-powered phishing attacks.
Detection times add another layer of risk.
IBM’s Cost of a Data Breach report found it takes an average of 292 days (nearly 10 months) to identify and contain breaches involving stolen or lost credentials.
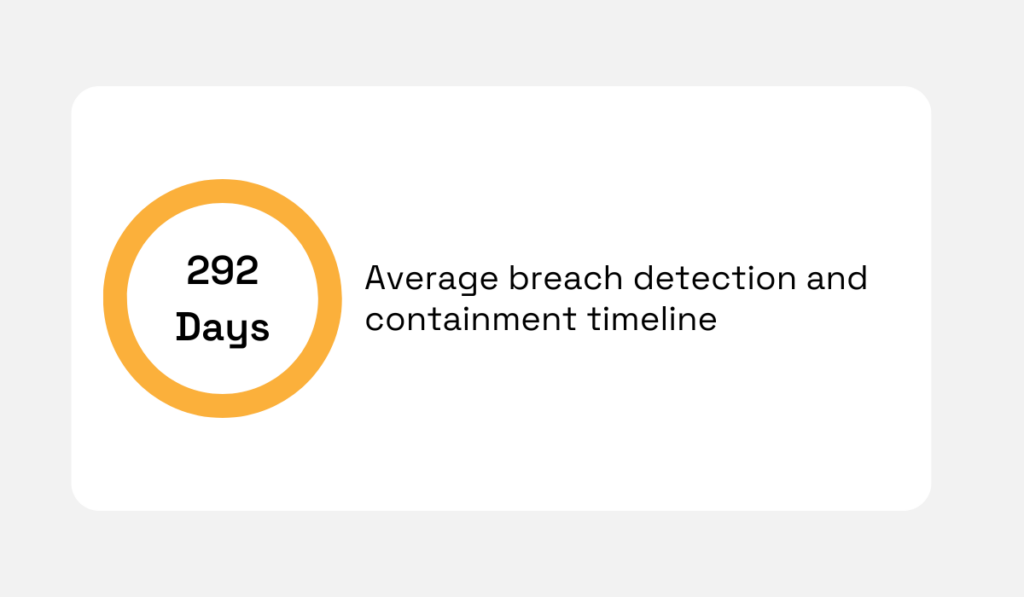
Illustration: Veridion / Data: IBM
That’s a long window for attackers to move undetected.
Compliance also only provides a snapshot of risk at one moment in time. It does not account for shifting threats, changes in vendor operations, or whether a vendor can withstand and recover from a major disruption.
Overall, compliance is necessary, but it is not sufficient.
If you want to protect operations and reputation, build a proactive TPRM program that combines compliance with continuous monitoring of vendors and third-party networks, performs resilience testing to evaluate vendor readiness for disruptions, and implements real-time alerts to respond quickly to new threats.
Source: Veridion
When a vendor fails, your organization will feel the impact.
Designing your program to prevent failures, detect them fast, and recover confidently ensures that TPRM protects both operations and reputation—not just checkboxes.
These five myths show that third-party risk management is often misunderstood.
Believing them can cost time, money, and security, while embracing the realities lets you act decisively and protect your supply chain.
At its core, TPRM is about controlling data access, assessing criticality, and maintaining continuous insight.
Start by addressing your highest-risk suppliers, leveraging data and automation, and making TPRM a cross-functional habit.
Even one meaningful improvement today builds momentum, strengthens your enterprise, and ensures your vendors are assets—not liabilities.