Third Party Risk Management vs Vendor Risk Management: Key Differences


Key Takeaways:
Companies are increasingly relying on external partnerships to drive growth and innovation.
However, this reliance also exposes them to reputational, financial, and cybersecurity risks.
While many use the terms interchangeably, Third-Party Risk Management (TPRM) and Vendor Risk Management (VRM) are different approaches to managing these external partners, each with distinct scopes, stakeholders, and strategic implications.
Understanding these differences is essential for building a risk management program that matches your organization’s needs and risk tolerance.
Today, we’ll explore the difference between VRM and TPRM, when to use each, and how a VRM program can evolve into a comprehensive, cross-functional TPRM strategy.
All vendors are considered third parties, but not all third parties are vendors.
This distinction is important, which is why third-party risk management has become a critical part of modern risk management.
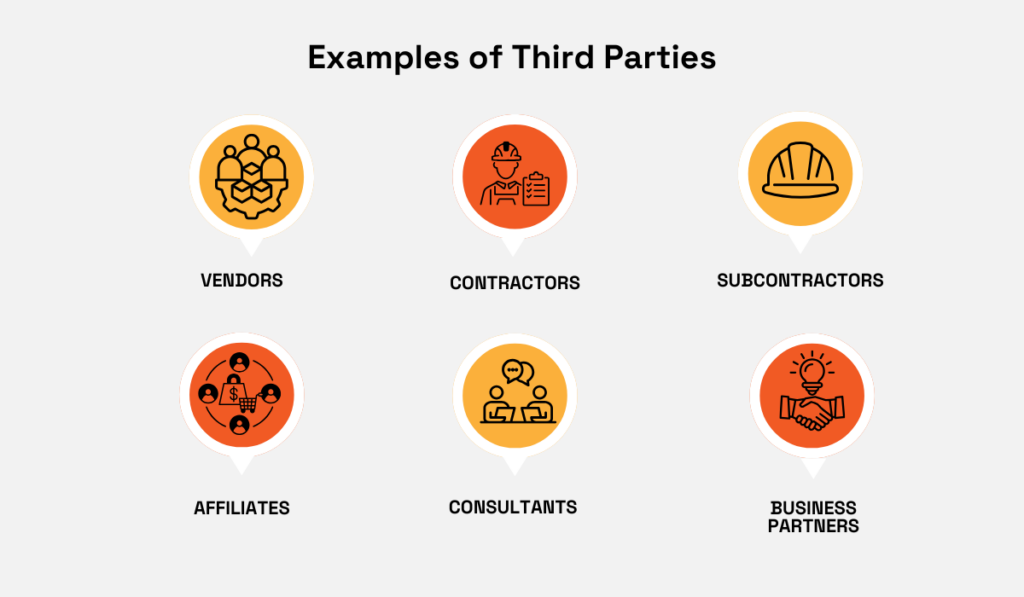
At its core, TPRM is a broad, strategic discipline that evaluates risks across the full spectrum of external entities that interact with your systems, data, or operations.
This includes your direct vendors, contractors, affiliates, business partners, cloud service providers, legal and consulting firms, as well as subcontractors and software tools that your vendors rely on.
Source: Veridion
Unlike VRM, which typically focuses only on direct suppliers, TPRM considers the broader ecosystem, making it both cross-functional and future-oriented.
TPRM also evaluates an extensive range of risk categories that extend far beyond cybersecurity, including:
| Reputational risk | Potential damage to brand image through association with unethical or non-compliant third parties |
| Geopolitical risk | Challenges arising from third parties operating in politically unstable regions or under shifting regulations |
| ESG risk | Sustainability, ethical labor, and carbon footprint concerns within your supply chain |
| Fourth-party risk | Vulnerabilities introduced by your third parties’ own vendors |
| Strategic risk | Misalignment between your organisation’s long-term goals and a third party’s ability to support them |
The scale of third-party risk is significant.
KPMG’s Third-Party Risk Management survey revealed that 73% of organisations experienced at least one third-party incident in the past three years.
These incidents have real operational and reputational impacts on organizations.
Cybersecurity data further confirms growing third-party risks.
The 2025 Verizon Data Breach Investigations Report (DBIR) shows that breaches involving third parties have doubled, now accounting for 30% of confirmed incidents, making third parties one of the fastest-growing attack vectors.

Illustration: Veridion / Data: DBIR
On top of that, breaches involving third parties cost, on average, $370,000 more than other breaches, directly impacting your bottom line.
These findings underline the urgent need for stronger third-party risk management.
Procurement executives, CISOs, and compliance leaders are rethinking risk management, realizing that protecting the enterprise today requires looking beyond direct vendor contracts.
It calls for a comprehensive, real-time approach to TPRM that can identify and address risks as they arise.
Vendor Risk Management (VRM) is a focused subset of TPRM that deals specifically with organizations supplying goods or services to your company.
While TPRM looks at all external relationships, VRM focuses on vendor-related risks in more transactional, supplier-based relationships.
It typically emphasises contractual controls, service-level performance, cybersecurity posture, and regulatory compliance for these suppliers.
VRM involves assessing key vendor-specific risk areas, outlined below:
| Risk Area | Tactic |
|---|---|
| Onboarding | Conducting assessments using questionnaires and evidence collection |
| Cybersecurity posture | Evaluating security controls and protocols (SOC 2, ISO, regulatory proof) |
| Regulatory compliance | Ensuring vendors meet relevant industry regulations |
| Operational stability | Assessing business continuity and financial health |
| Quality assurance | Monitoring product/service quality consistency |
| Contractual compliance | Verifying adherence to agreement terms, data handling, breach notification, and audit rights |
If there’s ever been a time to prioritise VRM, it’s now—especially with cyberattacks increasingly targeting supply chains.
In 2023, the Change Healthcare cyberattack paralyzed medical billing systems across the U.S., disrupting patient treatments and incurring significant financial repercussions.
Source: Reuters
Incidents like this highlight the need for proactive, real-time vendor risk management to reduce disruptions and protect sensitive information.
VRM programs simplify risk coverage by concentrating on known, contractual relationships and are often owned by procurement or IT security.
You evaluate vendor financial health, security protocols, on-time delivery, and contract adherence—but usually only for direct suppliers.
Effective VRM reduces operational disruptions, supports regulatory compliance, improves visibility, increases efficiency through automation, and lowers costs by avoiding breaches and fines.
Additionally, it builds trust among stakeholders by demonstrating a commitment to third-party security.
The most significant difference between TPRM and VRM lies in the breadth of relationships each approach encompasses.
VRM focuses mainly on your direct suppliers (those you contract with).
It may miss exposures introduced by your supplier’s suppliers unless those have been explicitly documented or surfaced.
VRM scope typically includes:
On the other hand, TPRM maps the entire external ecosystem, including cloud vendors, contact centre providers, outsourced payroll, professional services, joint venture partners, affiliates, and the vendors they use (4th parties).
It asks: If any external link fails or is breached, how does it affect our business?
TPRM scope typically includes:
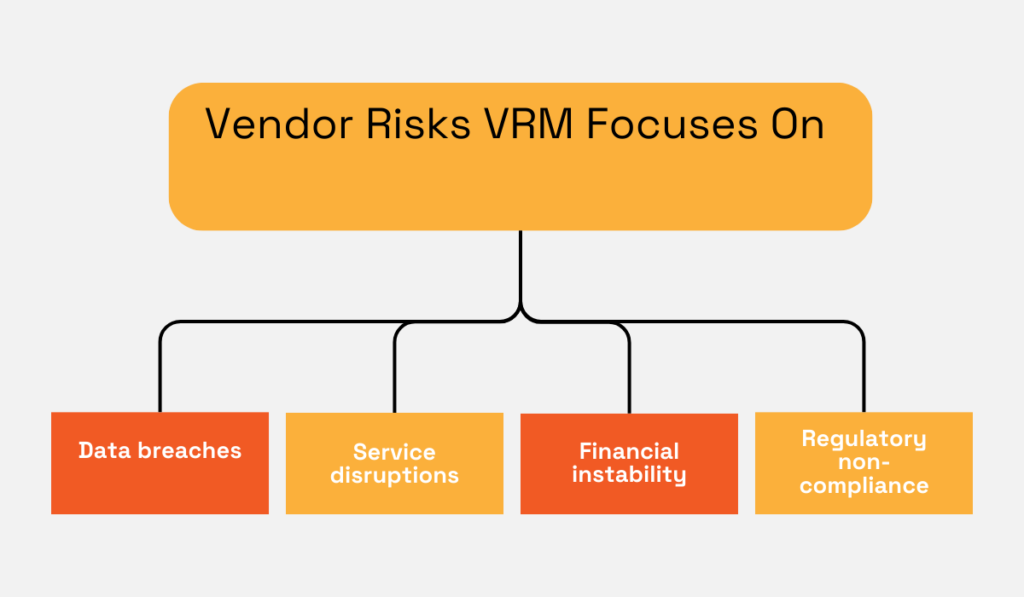
When it comes to the scope of risks that a VRM addresses, they include data breaches, service disruptions, financial instability, and regulatory non-compliance.
Source: Veridion
In addition to the risks VRM addresses, TPRM encompasses the following broader risks:
| Cybersecurity | While VRM primarily focuses on the direct vendor’s cybersecurity posture, TPRM delves deeper, assessing your broader ecosystem, including third parties and service dependencies. |
| Operational & supply chain disruption | Disruptions caused by natural disasters, pandemics, labour strikes, ransomware attacks, or even raw material shortages that affect third parties and cascade down to your business. |
| Reputational risk | Brand damage from association with unethical, non-compliant, or compromised third parties. |
| Geopolitical risk | Exposure from operating through partners in unstable or sanctioned regions. |
| ESG risk | Sustainability, ethical labour practices, and governance shortcomings in your supply chain. |
| 4th and n-th party risk | Vulnerabilities inherited from your vendors’ own suppliers or software dependencies. |
| Strategic & concentration risk | Misalignment with long-term objectives, or over-reliance on a single partner for critical functions. |
Let’s use a practical example to illustrate the difference between VRM and TPRM in terms of scope.
Your company uses an HR outsourcing service (a direct vendor). That HR firm uses a cloud-based payroll SaaS to process employee data.
Under VRM, you assess the HR firm.
Under TPRM, you map and monitor that payroll SaaS as a 4th party, because a breach there would still impact you. Visibility into those extended dependencies is a hallmark of TPRM.
Take, for instance, a recent ransomware attack on CDK Global. It not only disrupted CDK’s operations but also shut down operations for 15,000 automotive dealerships.
A security lapse by a single vendor impacted the entire supply chain.
Source: ExtraHop
What can you do to protect yourself from such a devastating breach of security?
Invest in advanced solutions like Veridion.
By using Veridion’s real-time supplier intelligence and enriched profiles, you can map deeper dependencies and identify risks among lesser-known third parties (such as 4th parties or sub-tier vendors).
Doing so improves discovery, prioritization, and continuous monitoring.
Source: Veridion
This comprehensive visibility is essential, as 54% of companies lack a complete list of all the third parties with whom they share sensitive information.
The organizational stakeholders involved in TPRM versus VRM programs reveal another critical distinction between these approaches.
VRM often sits within Procurement or IT/security—focused, transactional, and siloed.
Procurement leads vendor selection and contract negotiation, while IT/security assesses cybersecurity controls.
TPRM, in contrast, has matured into a multi-disciplinary responsibility, requiring a broader cross-departmental collaboration: Compliance, Legal, Finance, ESG, IT, Security, and Procurement must align.
Let’s break down the role of each team in enhancing TPRM:
This cross-functional nature of TPRM creates both challenges and opportunities.
Without proper coordination, organizations risk duplicated efforts and significant blind spots.
According to industry research, 27% of organizations employ the same risk management approach for all third parties, regardless of risk level, which indicates a lack of maturity in their approach.
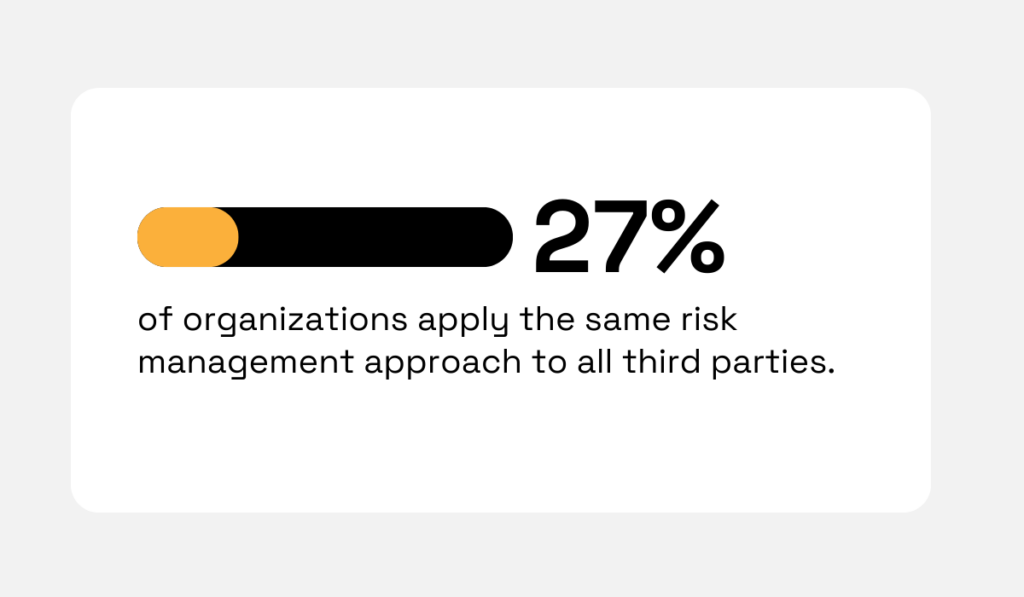
Illustration: Veridion / Data: Navex
Mature TPRM programs typically implement centralized data platforms to break down silos and ensure consistent risk evaluation across the organization.
These platforms provide a single source of truth for all third-party relationships, enabling coordinated assessment and monitoring while eliminating redundant efforts.
Choosing between implementing a VRM or TPRM program depends on your organization’s size, complexity, and risk exposure.
Start with VRM if you’re a small or mid-size company with a limited number of direct suppliers, simple contractual interactions, and limited regulatory exposure.
VRM will help you establish contractual hygiene, perform basic security checks, and enforce SLAs.
Move to TPRM when:
Other trigger signals to move to TPRM could be supply-chain incidents affecting partners, increased use of third-party software, or a material cyber event originating from a supplier.
Additionally, the upward trend of breaches involving third parties is a warning that many organizations are taking seriously.
In fact, most organizations evolve from VRM to TPRM as their risk exposure grows.
This natural progression typically occurs as companies realize that their vendor-centric approach overlooks critical risks associated with other types of relationships.
Research indicates that 90% of organizations are moving toward centralized risk management, reflecting this evolution from siloed VRM to comprehensive TPRM.
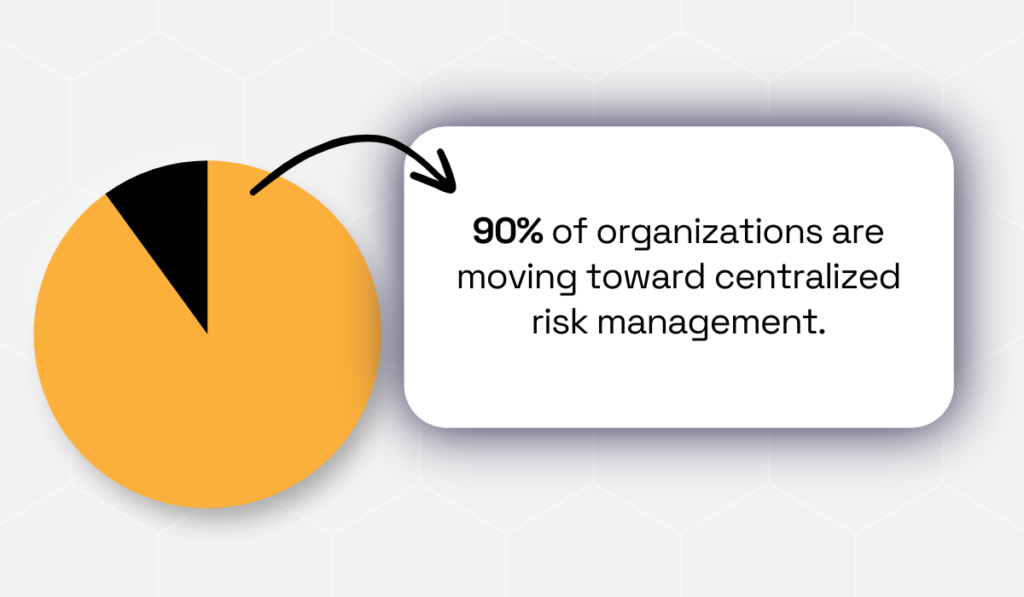
Illustration: Veridion / Data: EY
The transition points that typically trigger this evolution include:
To make it all a bit clearer, we’ve prepared a table showing the evolution from VRM to TPRM:
| Stage | Focus | Key Characteristics | Typical Triggers for Evolution |
|---|---|---|---|
| Basic VRM | Vendor compliance | Reactive assessments, procurement-led, limited scope | Initial vendor management needs |
| Maturing VRM | Vendor risk reduction | Proactive assessments, security involvement, and critical vendor focus | Vendor-related incidents, audit findings |
| Early TPRM | Third-party risk identification | Expanded relationship coverage, cross-functional involvement, and initial monitoring | Regulatory pressure, business expansion |
| Mature TPRM | Enterprise resilience | Comprehensive coverage, continuous monitoring, strategic alignment | Major incidents, board oversight, ESG requirements |
Understanding the difference between Third-Party Risk Management (TPRM) and Vendor Risk Management (VRM) is essential for creating an effective risk management strategy.
While VRM focuses on vendors that supply goods and services, TPRM takes a broader view of all external relationships and the risks they may introduce.
By implementing a framework that addresses your organization’s current needs while planning for future growth, you can build a resilient risk management program that mitigates threats and supports strategic partnerships.
As you strengthen your risk management practices, keep in mind that the goal is not to eliminate third-party relationships, but to manage them safely and strategically.