6 Vendor Risk Assessment Challenges to Overcome


Key Takeaways:
If vendor risk assessments are so critical, why do so many organizations struggle to get them right?
Many companies treat them as one-time projects or assume that a checklist and a few questionnaires are enough to uncover risks.
But the reality is far more complicated.
Incomplete data, uncooperative vendors, and constantly changing risks can all derail even the best-intentioned efforts.
Companies that overlook these challenges often end up with vulnerabilities, missed warning signs, and a false sense of security in their vendor relationships.
In this article, we break down six of the most common vendor risk assessment challenges and show you practical ways to overcome them.
That way, your process can become clearer, more accurate, and more effective at protecting your business.
Thorough vendor risk assessments are resource-intensive, requiring time, expertise, and personnel.
According to the 2024 Benchmark Survey Report, 26% of organizations still use spreadsheets to manage third-party risks.
That’s a 13% increase from the previous year, which means manual work is overwhelming many teams.
Brad Hibbert, COO/CSO at Brinqa, a cybersecurity company that specializes in risk management solutions, agrees this is a big problem:

Illustration: Veridion / Data: Businesswire
At the same time, there just isn’t enough personnel to handle all this work.
The numbers back this up: Nearly 70% of TPRM teams report being understaffed, meaning they actively manage risk for only about 40% of their vendors.
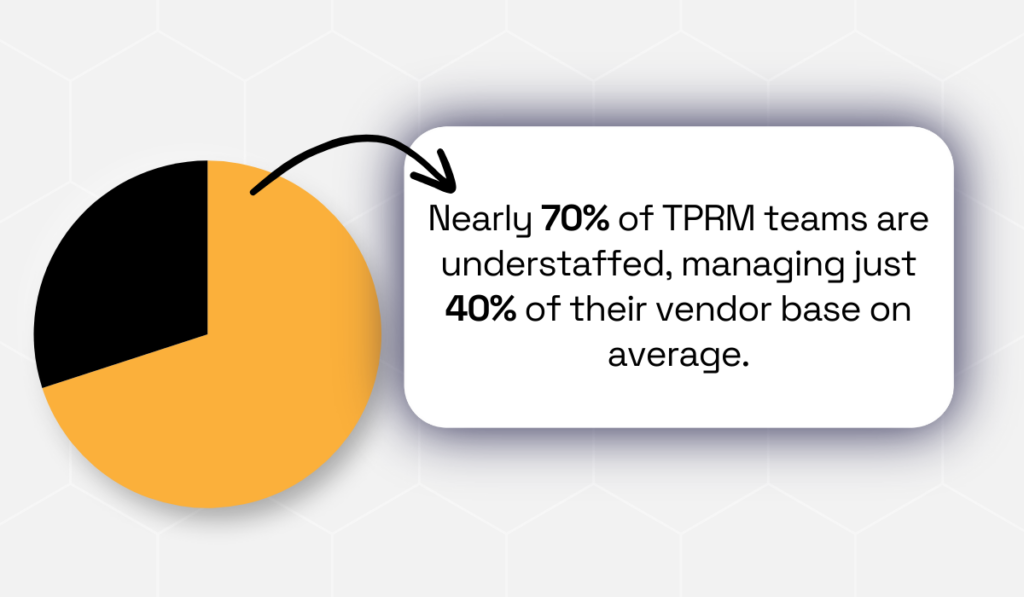
Illustration: Veridion / Data: Mitratech
When you don’t have enough staff or the right tools, it’s easy to cut corners. Your team rushes through questionnaires and skips deep-dive reviews.
This results in superficial assessments that miss important risks.
This happens more often than you might think: 61% of companies experienced a third-party data breach in 2023, according to Prevalent Inc.
No wonder thorough assessments feel impossible without more help.
How do you address this?
Start by prioritizing vendors.
You don’t need to assess every vendor with the same level of scrutiny, so identify your most critical suppliers first.
Tier your vendors by risk level and focus on high-impact ones. Give the lower-tier vendors a lighter touch.
According to Venminder, the majority of companies already recognize this as a best practice.
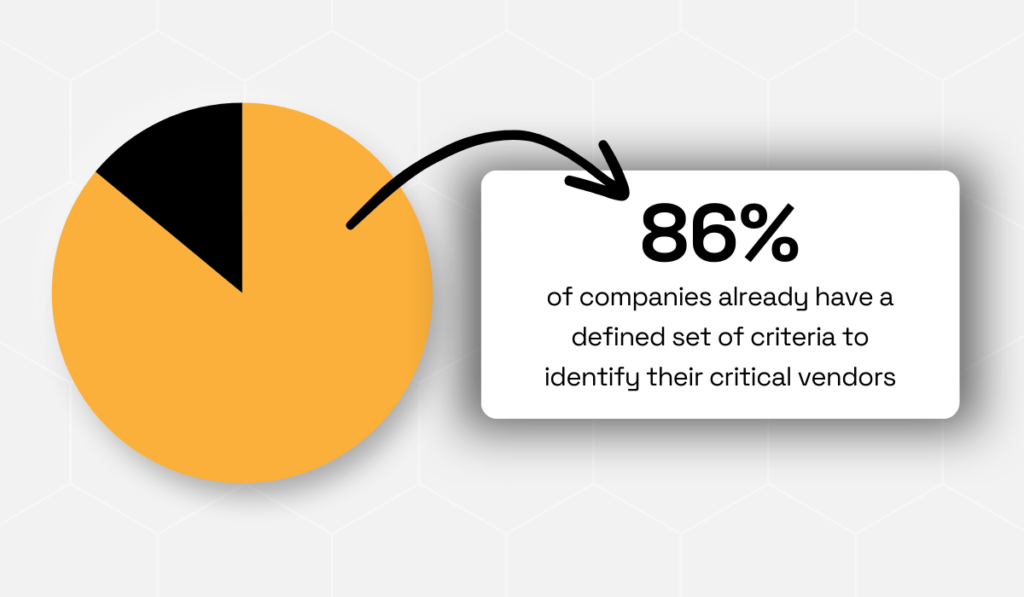
Illustration: Veridion / Data: Venminder
Next, invest in process improvements.
Look for technology solutions that can automate parts of your assessment workflow: many platforms will send questionnaires, track responses, and flag delays automatically.
Standardizing and automating repetitive tasks significantly lightens the workload.
Building a culture of shared responsibility also helps.
Communicate with sales and business units about the need for timely vendor information, so procurement gets the cooperation it needs.
With clearer communication and the right tools, you can alleviate your resource crunch and achieve better, more thorough assessments.
The questionnaire you send out is the core of any vendor assessment.
But crafting questions that elicit real risk insights is an art many organizations get wrong.
For example, if your questions are too broad, vague, or off-topic, vendors skip them or give shallow answers.
Imagine receiving a massive form with hundreds of generic security terms. You’d probably rush through it, give incomplete answers, or opt out entirely.
Long, irrelevant, or one-size-fits-all questionnaires frustrate suppliers, which often lead to incomplete or inaccurate responses.
Forcing vendors to wade through 500+ questions leads to vendor fatigue.
In other words, bloated questionnaires do more harm than good by yielding poor data.
To fix this, follow these three rules:
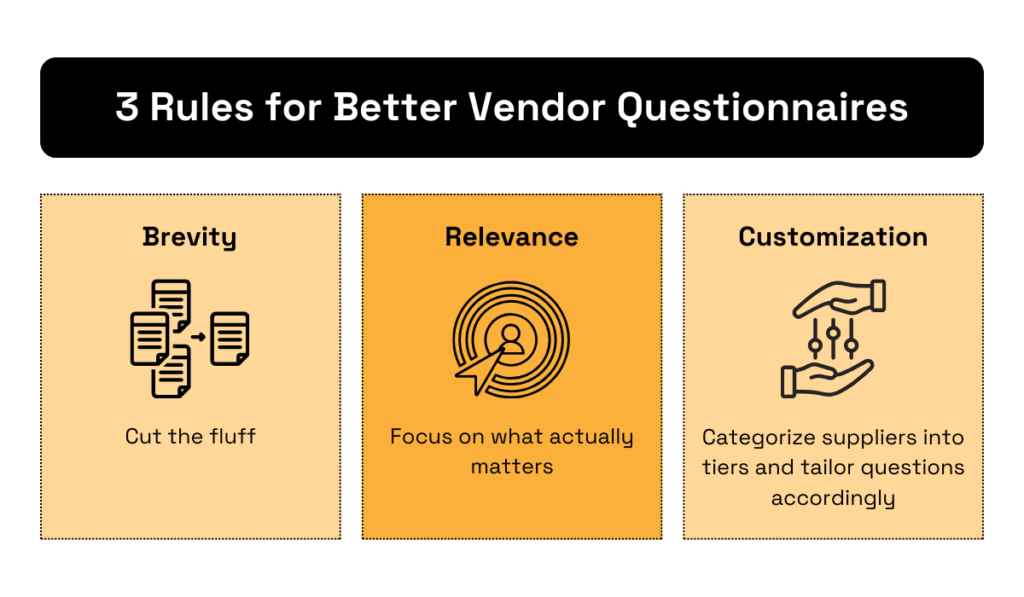
Source: Veridion
Most importantly, aim for brevity and relevance.
Think carefully about what you really need to know and tailor questions to each vendor’s role and your organization’s priorities.
If a vendor handles financial data, focus on data protection and audit history; for healthcare vendors, emphasize HIPAA controls.
Avoid one-size-fits-all forms. Using the same questionnaire for every vendor creates unnecessary workload and dilutes focus where it matters most.
Instead, customize your questionnaire by vendor category and risk tier.
Use industry-standard templates as well.
For instance, the Cloud Security Alliance offers a 261-question Consensus Assessments Initiative Questionnaire (CAIQ) with a shorter 124-question CAIQ-Lite version.
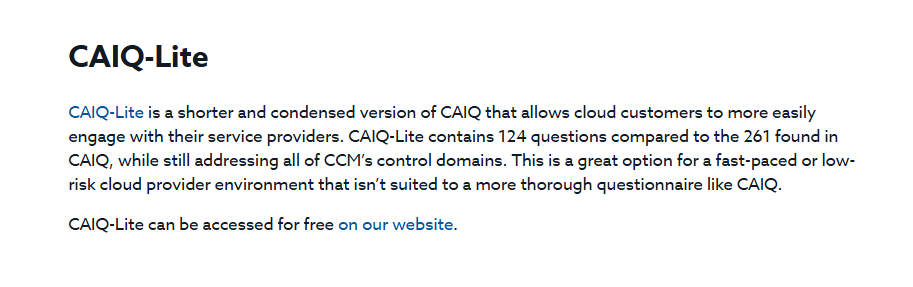
Source: Cloud Security Alliance
Similarly, Shared Assessments provides the widely used SIG Questionnaire for comprehensive vendor risk coverage.
Source: Shared Assessments
Finally, make every question clear and concise. Write in plain language and explain why you’re asking each question.
Group related questions into sections like “Data Security” or “Business Continuity” so vendors can answer more efficiently.
Keep the form as short as possible while covering the essentials. When you send it out, tell vendors how long it should take and offer help or clarification upfront.
Well-designed questionnaires raise response rates and improve data quality, making your risk assessments much more accurate.
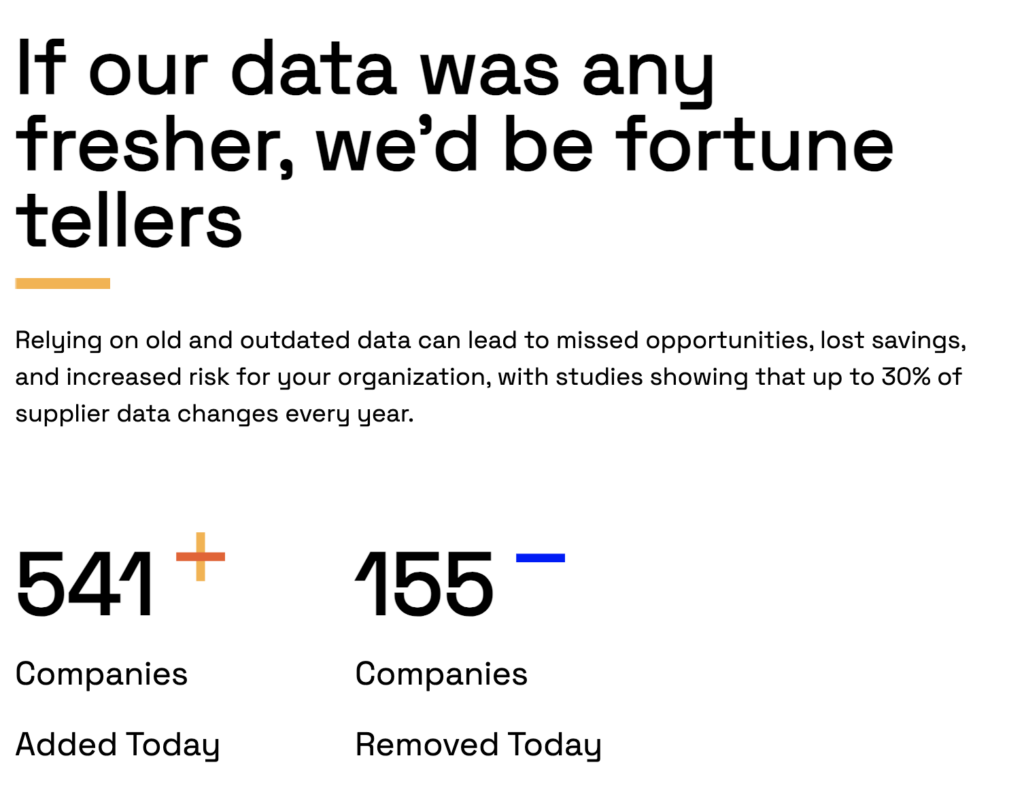
Bad data is another major headache.
Whether it’s outdated contact info, missing financial details, or conflicting security histories, flawed data can cripple your assessment.
This is a huge issue for many companies, research shows.
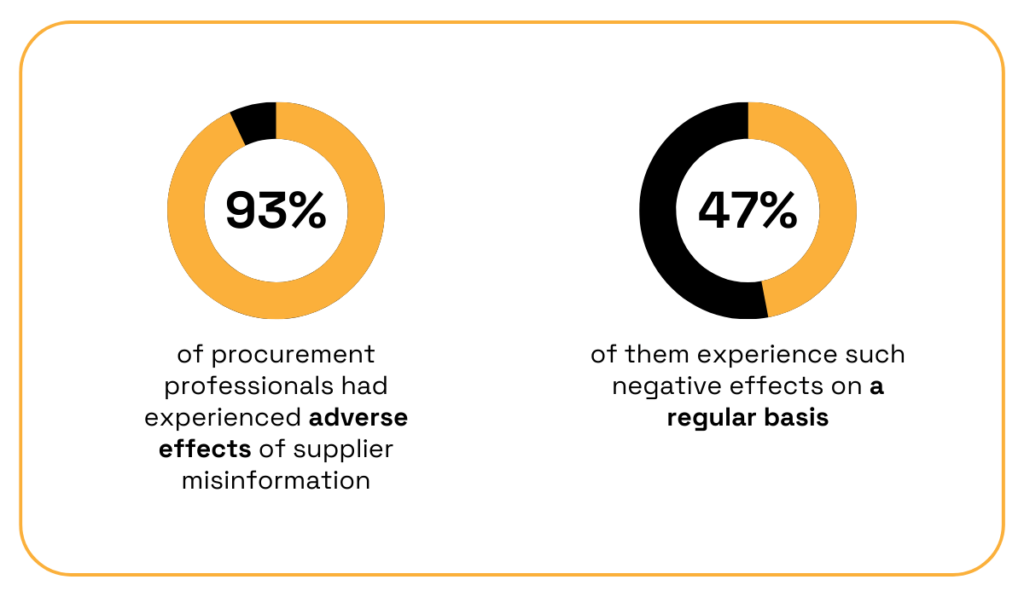
Illustration: Veridion / Data: TealBook
When vendor information is stale, outdated, or fragmented across spreadsheets, you become blind to new issues.
This challenge cuts both ways. Vendors themselves may submit outdated or partial information – a busy supplier might send a stale report or omit key details.
On your side, internal teams can end up with duplicate vendor lists and conflicting records.
As a result, you can’t trust the data you have, so decisions based on it can be wrong, leaving you exposed to hidden risks.
The solution is centralized, verified data. Use a single vendor master database and insist all teams feed every change into it.
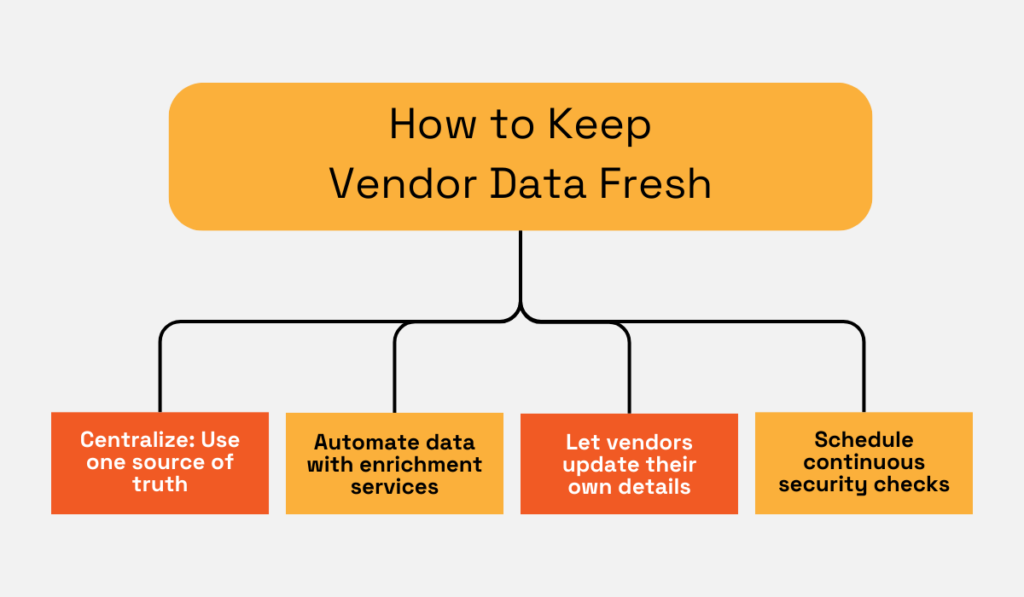
Source: Veridion
Moreover, consider data-enrichment services like Veridion, which automatically scour and update vendor profiles from reliable sources.
This means missing or outdated details, like ownership changes, compliance flags, or financial shifts, are automatically filled in.
Source: Veridion
This keeps supplier records accurate and complete without the heavy lifting of manual research.
With a more complete view of your vendors, you can spot risks faster and reduce the chance of making decisions based on flawed information.
Source: Veridion
That way, whenever you get questionnaire responses, you can cross-check answers against known data and follow up immediately on any discrepancies.
Instead of relying solely on your team to clarify information, you can make the process even easier by allowing suppliers to update their own records directly.
Encourage them to update their details via a secure portal so records stay fresh.
Also, establish a regular data hygiene schedule: verify key fields (legal names, addresses, certifications, contacts) annually, and refresh financial and compliance checks continuously.
By keeping vendor data clean and current, your risk assessments will be grounded in real facts.
Vendors don’t always appreciate jumping through hoops or sharing sensitive information.
Long, complex questionnaires and audits can feel intrusive or burdensome, especially for small suppliers without big compliance teams.
Some vendors worry that revealing details will expose them to liability or invite more scrutiny.
When suppliers slow-walk their responses or refuse to cooperate, your assessment stalls, and you end up with unanswered questions.
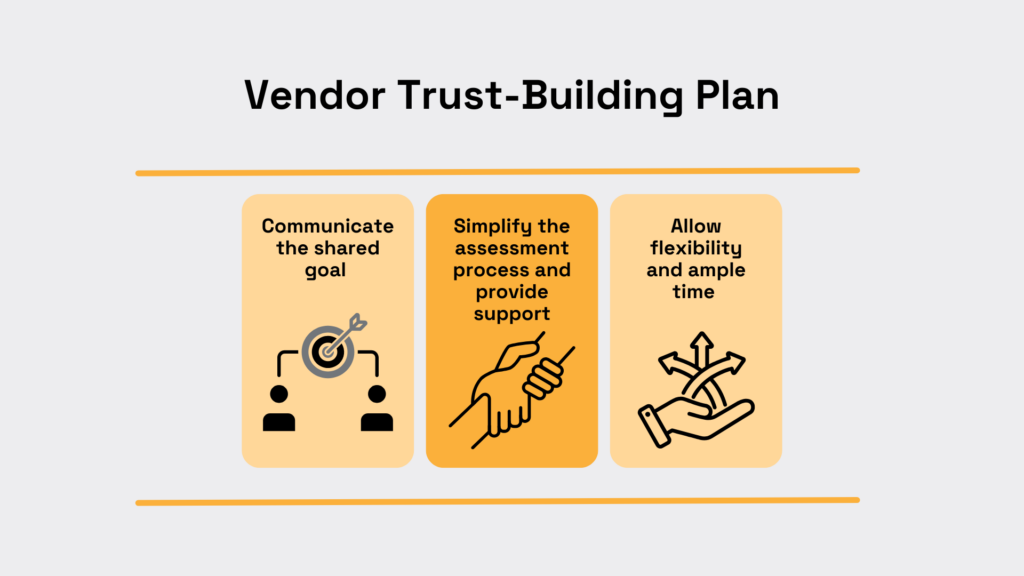
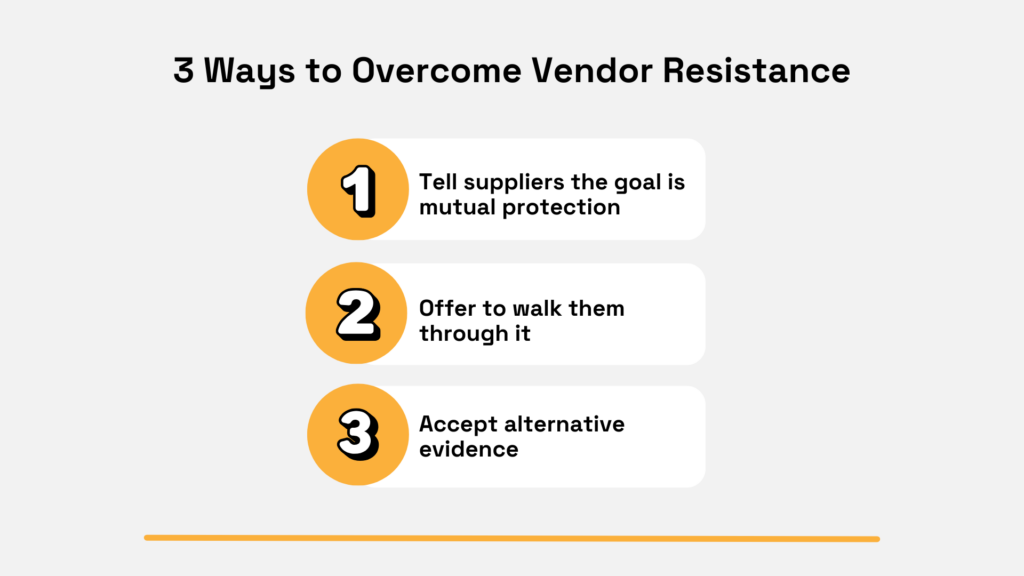
To overcome this hurdle, start with clear communication and trust-building.
Source: Veridion
Explain why the assessment matters for both parties. Emphasize that the goal is mutual protection and a secure partnership, not punishment.
For example, you might say:
“We’re asking these questions because we both handle sensitive customer data; it’s in both our interests to avoid breaches.”
Make clear what you’ll do with their information and how it will be protected. Vendors cooperate more when they understand you’re on the same team.
Next, simplify the process for them. Provide a real person as a contact for any questions, and offer to walk through the questionnaire in a quick call if needed.
Source: Veridion
Give vendors ample time to respond: sending the questionnaire well in advance of deadlines can reduce pushback.
Be flexible on evidence: for very busy or reluctant suppliers, allow substitutes when possible.
For example, you can accept a recent SOC 2 or ISO 27001 audit report instead of requiring every form field to be filled out.
By making the process as painless as possible, while still collecting the needed information, you can encourage cooperation and get more complete data from your vendors.
Third-party risk monitoring is hard enough. But there are often fourth parties lurking down the line, including the subcontractors and services used by your vendors.
These indirect relationships can hide serious risk. Especially because you don’t see them right away.
As Maria Phillips, Senior Counsel, Privacy & Compliance at Imprivata, a digital identity security company, explains, fourth-party vendors are a major blind spot for many:

Illustration: Veridion / Data: Help Net Security
Many firms focus on auditing their direct suppliers but fail to see the risk coming through their vendors’ own vendors.
For instance, 59% of companies admit they don’t monitor third parties for cybersecurity risks to begin with, meaning that fourth-party exposures routinely go unnoticed.
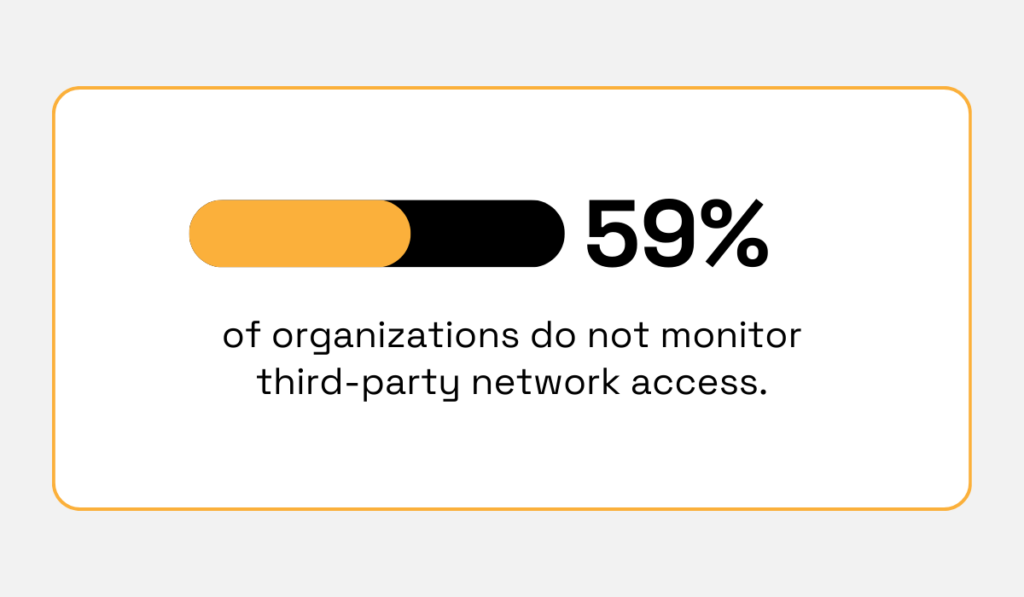
Illustration: Veridion / Data: Imprivata
How do these hidden parties create risk?
Imagine your cloud provider outsources backups to another company. If that backup firm is breached, your data could be exposed without you even knowing.
These gaps introduce compliance blind spots and new cybersecurity vulnerabilities. And if any subcontractor fails (for example, goes offline), it can disrupt your operations too.
To tackle fourth-party risk, you need visibility and tracking.
Start by mapping your extended supply chain and building a diagram of vendor relationships.
Ask each key supplier to list their own major vendors; this simple step often uncovers dozens of hidden partners.
Document who these fourth parties are, what roles they play, and which handle critical data or systems.
Include sections in your contracts requiring vendors to notify you whenever they add or change important subcontractors.
Where possible, request audit reports or attestations that cover significant fourth-party arrangements.
Finally, leverage continuous monitoring tools: many services can scan news feeds, sanction lists, or breach feeds and alert you if a downstream vendor in the chain is compromised.
By putting these measures in place, you can proactively mitigate hidden fourth-party risks before they become unexpected breaches.
Treating vendor risk assessment as a one-and-done is a common but critical mistake.
Vendors’ circumstances can change rapidly: a new breach, a merger, a regulatory shift, or even a financial problem can alter their risk profile overnight.
Relying on one-time or even periodic assessments provides only a limited snapshot of your supplier risk profile, meaning you could easily miss emerging risks.
Therefore, risk monitoring must be continuous.
Here’s what to monitor:
Source: Veridion
You need a system that watches vendors over time, not just at onboarding.
Industry data support this.
For instance, a Gartner survey shows that organizations that track changes in the third-party landscape are more likely to remediate risks before they have a material impact

Illustration: Veridion / Data: Gartner
In other words, ongoing checks ensure no significant issues slip through the cracks without you noticing.
So, incorporate vendor monitoring into your program.
Set up periodic check-ins and automated alerts. For example, ask important vendors to submit short update surveys quarterly or biannually.
Use automated tools, such as Veridion, that flag key events, like vendor breaches, failed audits, changes in ownership, or new negative news.
Keep an eye on non-cyber changes too: if a vendor starts handling new types of data or shows signs of financial trouble, update their risk profile accordingly.
Incorporate reminders and ownership into your process. For instance, appoint someone to review each vendor’s status on schedule.
Source: Veridion
Continuous monitoring provides dynamic insights, so the next big risk won’t sneak up on you. You’ll catch the warning signs early and be ready to act before they become crises.
These six challenges reveal why vendor risk assessments often feel overwhelming.
Ignoring them can leave blind spots in your supply chain, while tackling them directly helps you make smarter decisions and safeguard your organization.
Essentially, effective vendor risk management involves accurate data, clear communication, and continuous monitoring.
Begin by prioritizing your highest-risk suppliers, developing targeted questionnaires, and deploying automation to keep records current.
Even one improvement today reduces risk and simplifies vendor assessments. While risks evolve, building continuous monitoring into your process keeps you ahead of new threats rather than falling behind.