Vendor Risk Management Frameworks: An Overview


Key Takeaways:
Enterprise businesses deal with thousands of third-party vendors on a daily basis.
As these businesses grow, so does their vendor ecosystem, and with it, the associated security risks.
Managing such a vast network of vendors manually or in a fragmented way is both inefficient and risky.
That’s why a structured, automated approach to vendor risk management is essential.
This is where vendor risk management frameworks come in.
So, in today’s article, we’ll explain what they are and share guidance on how to choose a framework that aligns with your organization’s specific needs.
Put simply, a vendor risk management framework is a structured set of guidelines that help you manage everything related to third-party vendor risk.
That includes everything from identifying risks and evaluating them to monitoring vendors and possible risks and finding ways to avoid them.
Companies may develop their own VRM frameworks or incorporate existing standards with their risk assessment tools.
But not every framework is the same.
They fall into two main categories:
A framework that most closely aligns with your organization’s specialties will help you outline clear processes, roles, and vendor assessment criteria.
On top of that, if you implement the right VRM frameworks, you are less likely to waste time on partners without robust security measures that keep cyberattackers out of their system.
VRM frameworks come with a range of benefits.
Firstly, a well-defined and appropriate framework makes vendor risk identification and evaluation consistent.
This ensures your reports are consistent and complete, while also saving you both time and money.
Large organizations with many vendors are obligated to comply with different industry regulations, internal policies, and requirements from external audits.
This goes especially for high-risk industries like healthcare or finance that deal with sensitive end-user data.
For example, healthcare organizations need to be HIPAA-compliant because they’re dealing with very private patient information.
Gaurav Kapoor, co-CEO of MetricStream, a company providing governance, risk management, and compliance services, explains:

Illustration: Veridion / Quote: Clinician
That is where a VRM framework comes in, helping them align their vendor risk management process with these strict regulations.
But one of the most important benefits of these frameworks is that they allow businesses to easily detect potential risks on time and take the necessary measures on time, instead of reacting to a crisis.
In practice, many reactions come late because supply chain attacks are often hard to detect.
According to IBM’s 2025 Cost of a Data Breach report, it took organizations a staggering 267 days to detect and contain third-party vendor and supply chain compromises.
But with an incorporated VRM framework, detecting a breach first, before third parties or attacker disclosure, is possible.
Then, security teams can limit the damage and save the organization money in the process.
This was also shown in the aforementioned IBM report: the average cost of a breach in that case was $4.18 million.
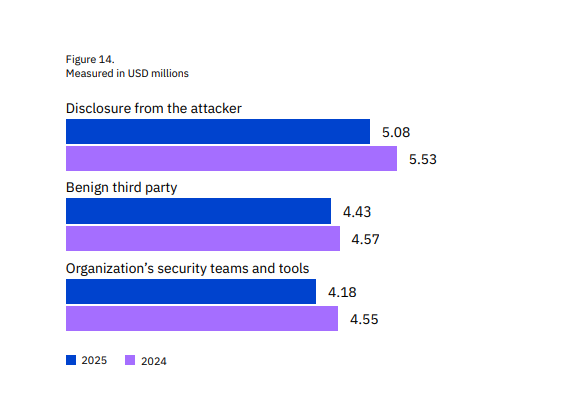
Source: IBM
That is still a lot of money, but when you take into account the cost of a breach disclosed by the attacker stood at $5.08 million, a breach identified early and internally is a better scenario.
Overall, VRM frameworks are a must-have tool in an organization’s workflow because they ensure the safety of sensitive data, speed up compliance and certification processes, and prevent risks from escalating.
Now, let’s break down some of the most widely used VRM frameworks.
The NIST SP 800-161: Cybersecurity Supply Chain Risk Management framework sets the baseline for many cybersecurity regulations.
It outlines how to identify, assess, and respond to cyber risks that arise through third-party vendors.
This framework is mandatory for businesses contracted by the US federal government.
But it’s also a first choice for many private companies serious about making their businesses as secure as possible.
Considering that supply chain attacks are on the rise and can have devastating consequences, this framework gives you a solid playbook.
Just ask British Airways.
A Magecart supply chain attack exposed the personal data of 500,000 customers back in 2018.

Source: Travelmole
Although the attack happened in a third-party vendor’s system, BA were still the ones left to deal with the fallout.
But these types of breaches aren’t a thing of the past.
Fast forward to 2025, and an astonishing 30% of data breaches were linked to third parties.
That is twice as many as in 2024. And that’s just the data for the first part of the year.
These cases are more than enough reason to incorporate a framework like NIST that focuses on safeguarding your system against third-party risks.
But, you’ll also need a framework that’s focused on signaling to your partners and suppliers that you take security seriously.
That’s where ISO 27001 comes in.
This international standard for information security helps organizations build, manage, and continually improve their information security management system (ISMS).
Because of its quality and the growing number of companies that implement it, ISO 27001 is practically a shorthand for reliability both in the eyes of your vendors and customers.

Illustration: Veridion / Data: ISO
Holding this certification gives you an upper hand both in attracting new clients and when looking for new vendors.
And if you’ve partnered with vendors who’re handling cloud-based services or sensitive customer data, SOC 2: Service Organization Control Reports is one more framework to pay attention to.
Developed by the AICPA (the American Institute of Certified Public Accountants), it focuses on five trust principles:
There are two types: SOC 2 Type I and Type II.
Type I reports are focused on assessing whether your organization’s risk control measures in your cloud data are by the book.
Type II, on the other hand, reports on the quality of your organization’s control performance.
The main difference between the two lies in their time frames: Type II is more thorough and takes more time (from 3 to 12 months).
That’s why it’s sometimes a first choice for highly regulated and risk-prone industries like finance or healthcare.
Questionnaires are another big part of the vendor risk assessment process.
However, they can be a big time and resource drain.
A recent report by EY found that nearly 4 in 10 companies use multiple questionnaires for different risk domains and send an average of 55 questionnaires to third parties.

Illustration: Veridion / Data: EY
So, if your company is also juggling a large number of questionnaires, you can solve the chaos with the SIG Questionnaire.
Maintained by Shared Assessments, SIG offers a standardized way to evaluate vendor risk across 19 domains, including security, privacy, compliance, and operations.
You can choose between the SIG Lite (for basic due diligence) or SIG Core (855 questions, for high-risk vendors).
One of the biggest benefits of having a standardized questionnaire is that it brings consistency and cuts down on all the back-and-forth.
With growing pressure from regulators and stakeholders, incorporating ESG into vendor risk management is becoming an imperative.
One of the best ways to make sure your organization is aligned with ESG compliance requirements is the Global Reporting Initiative (GRI) standards framework.
These standards provide a robust structure for evaluating a vendor’s sustainability, labor practices, and ethics.
Reports show that more and more companies use GRI standards as a framework for measuring their own ESG performance.
In a recent survey by NAVEX, this framework is the third most used one, with 28% of respondents disclosing that they use it.
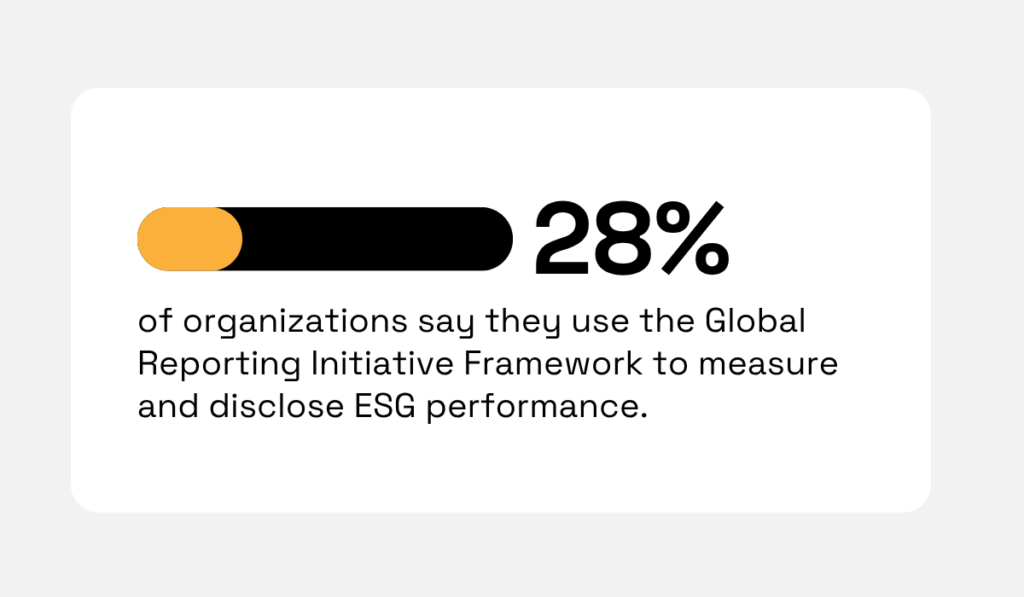
Illustration: Veridion / Data: NAVEX
GRI gives your organization a clear and thorough overview of your vendors’ ESG practices.
That’s why it’s a must for any business that’s serious about being ethical in the modern world.
Each of these frameworks has its own specificities, so you may use them at different times and with different types of vendors.
But at their core, all of them can help you avoid blind spots, build trust with stakeholders, and reduce the risk of reputational or financial damage from third-party failures.
VRM frameworks are not plug-and-play solutions that are applicable to any context.
That’s why it’s important to choose the one most appropriate for your organization’s needs.
Here are a few tips on how to make the best decision.
Before you choose a VRM framework, first ensure that it aligns with your company’s core objectives.
The more these two are aligned, the more robust your organization’s cybersecurity will be.
Why does this matter?
Because, if your framework of choice doesn’t match your company’s goals, you risk creating unnecessary complexity.
Worse yet, you could end up missing critical risks that could threaten your operations.
This happened to Yale New Haven Health System, the largest healthcare organization in the state of Connecticut.
The company was affected by a data breach that originated in MOVEit, a tool used by one of its vendors, the customer activation platform Welltock.
More than 800,000 people’s personal data was compromised, including Social Security numbers, names, addresses, and health insurance information.
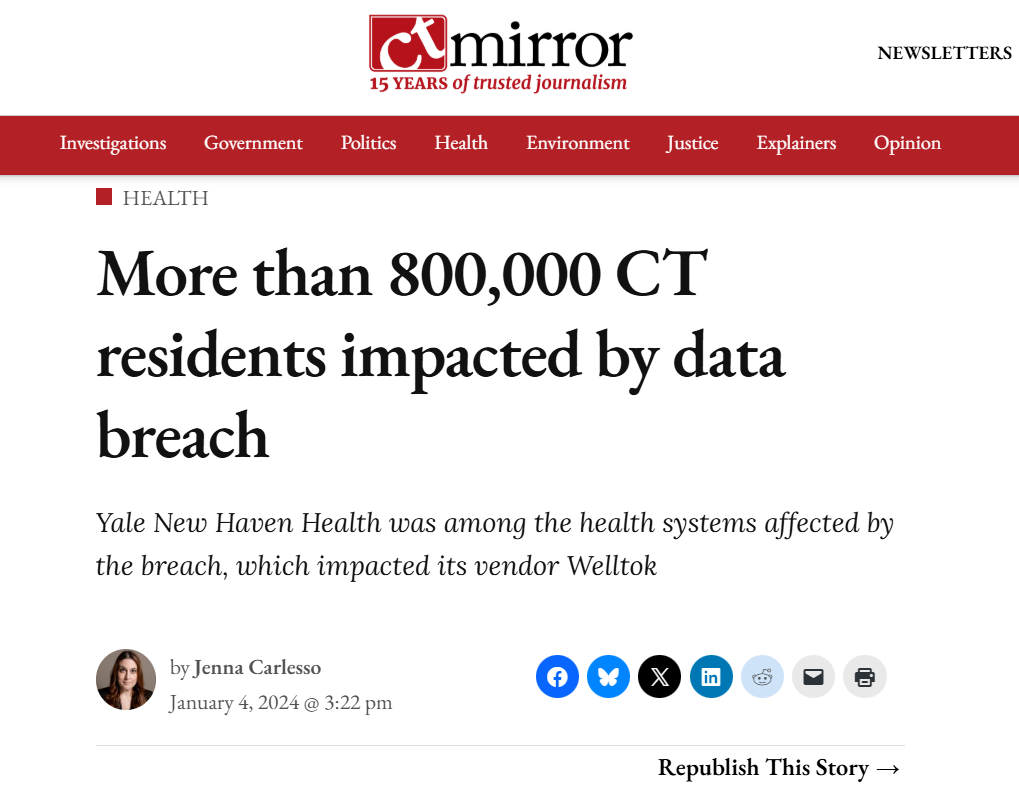
Source: CT Mirror
The original breach in MOVEit happened in May 2023, but Yale New Haven System was notified by Welltock of it five months later.
But had both YNHS and Welltock noticed this intrusion into their user data on time with the help of more robust vendor risk management frameworks, they probably would have mitigated this danger.
Your risk management efforts should reflect your business priorities, regulatory obligations, operational model, and risk tolerance.
A framework that aligns with those things will help your team stay focused, make smarter decisions, and avoid wasting time on risk areas that don’t actually matter to your business.
For example, if your organization is prioritizing global expansion, you’ll want internationally recognized frameworks like ISO 27001.
And if you’re working in highly regulated sectors—think finance, healthcare, or government contracting—then NIST SP 800-161 or SOC 2 Type II might be more relevant, giving you the depth and documentation you need to stay compliant and protected.
Also, take note of your risk appetite.
Are you a fast-scaling tech company that needs agility? Or are you a legacy financial institution with low risk tolerance?
Your choice of framework should reflect that.
If your framework is out of sync with your objectives, you’ll feel it fast.
So, choose frameworks that align with your goals if you want smarter vendor selection, faster onboarding, and stronger relationships with partners who actually support your long-term goals.
Organizations have a long list of priorities, so it might seem easier to simply conduct a general risk assessment of every vendor.
It’s the most logical solution when strapped for time, right?
Well, not really. In fact, a general risk assessment may bring you more harm than good.
Especially if you’re in an industry with specific risk factors and compliance needs like healthcare or finance.
Not to mention, you’re dealing with very vulnerable and personal data.
Let’s say you’re in healthcare.
If a cloud service provider is storing patient data and they aren’t HIPAA-compliant, it doesn’t matter how good their general cybersecurity looks. You’re still on the hook.
As Michael Herrick, Founder and HIPAA risk analyst at HIPAA for Humans, points out, you can expose your patients to serious issues.

Illustration: Veridion / Quote: Smartsheet
This is where tailoring your VRM framework to industry-specific standards pays off.
For example, in healthcare, you might layer HIPAA assessments into your VRM process, alongside ISO 27001 or SOC 2.
In finance, on the other hand, integrating NIST SP 800-53 or PCI DSS controls could be essential.
Also, take into account that not all risks are the same.
A biotech firm outsourcing lab data analysis faces a very different set of risks than a SaaS provider contracting with a cloud storage vendor.
Industry-specific frameworks ensure you’re asking the right questions and watching for the right red flags.
That said, not every vendor needs a full deep dive. You can still tier your vendors based on risk level.
But even then, your risk model should factor in industry-specific exposure.
A vendor that might seem “low-risk” in a generic sense could be high-risk in your context if they touch sensitive data or support regulated operations.
A risk management framework is powerful by itself, but imagine how powerful it can be when integrated with existing workflows in your organization.
Integration gives you tons of benefits, from saving time and a sharper bird’s-eye view of your entire security and compliance processes to giving you an upper hand in mitigating risks.
Veridion gives you just that.
Powered by AI, it provides reliable, up-to-date company and compliance information for vendor assessments.

Source: Veridion
It collects global vendor data for over 134 million companies across the globe.
The collected data—updated on a weekly basis—is then analyzed with proprietary machine-learning models so it always stays current and relevant.
So, in case one of your vendors experiences a data breach or a legal issue, Veridion can surface that change almost immediately, and you can react before the risk escalates.
You can also integrate Veridion with tools like Coupa, Snowflake, and MarketDojo, giving you real-time visibility into supplier performance and risk.
Integrating your VRM frameworks with enterprise solutions like Veridion is a surefire way to always be one step ahead when it comes to managing risks associated with your vendors.
VRM frameworks are key in helping companies stay compliant with regulations, safeguard sensitive data, and protect their reputation.
But only a framework aligned with company goals and integrated into existing systems can make a difference in your organization.
So, don’t approach VRM frameworks as just another addition to your to-do list.
Take your time and choose them with intention.
That way, both your vendor relationships and your business can thrive, despite possible risks.