Vendor Impersonation Fraud: How It Happens & How to Prevent It


Key Takeaways:
Nearly 60% of BEC scams now involve vendor impersonation.
As criminals shift focus to trusted supplier relationships, it’s clear that even the most secure organizations face mounting risks.
This article explores how vendor impersonation fraud unfolds, the role of AI in amplifying its impact, and what you can do to prevent it.
Let’s dive right in.
Vendor impersonation fraud occurs when cybercriminals pose as legitimate vendors to trick organizations into making payments or sharing sensitive information.
Like all other impersonation attacks, vendor-centric fraud leads to major financial losses, data breaches, and reputational damage.
However, its growing effectiveness is also reshaping broader business email compromise (BEC) tactics.
According to the 2025 AFP Payments Fraud and Control Survey, 60% of BEC scams attempted in 2024 involved vendor impersonation.
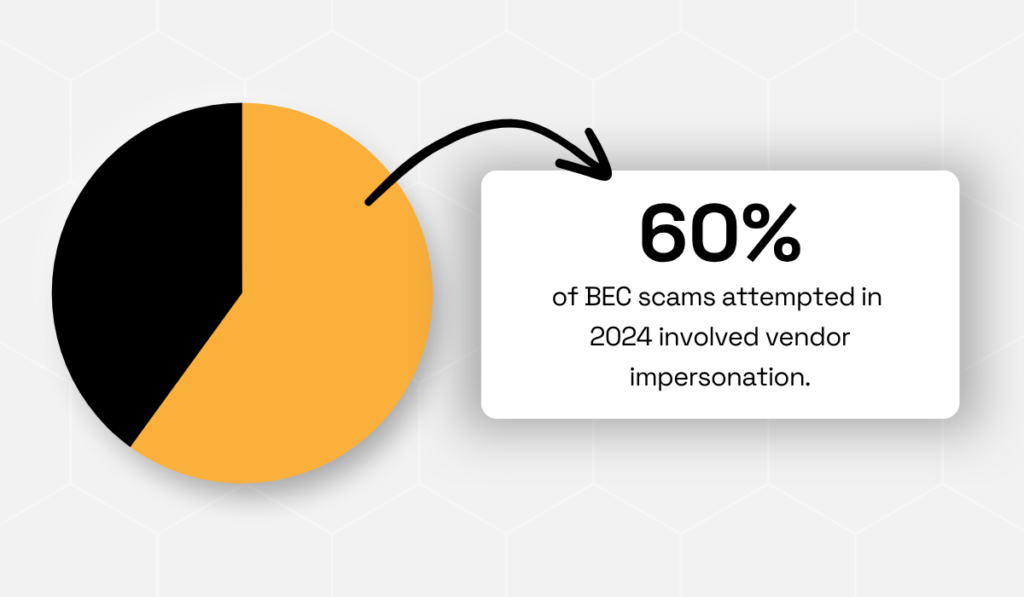
Illustration: Veridion / Data: AFP
These numbers indicate a sharp shift from traditional “CEO fraud” schemes toward attacks that exploit trusted business relationships.
The latest research on these vendor email compromise (VEC) attacks shows that employees often struggle to recognize this type of deception.
After monitoring over 1,400 organizations over twelve months, the email security platform Abnormal found that nearly half of all vendor scam emails triggered employee interaction.
In other words, employees opened, replied to, and/or forwarded the fraudulent message.
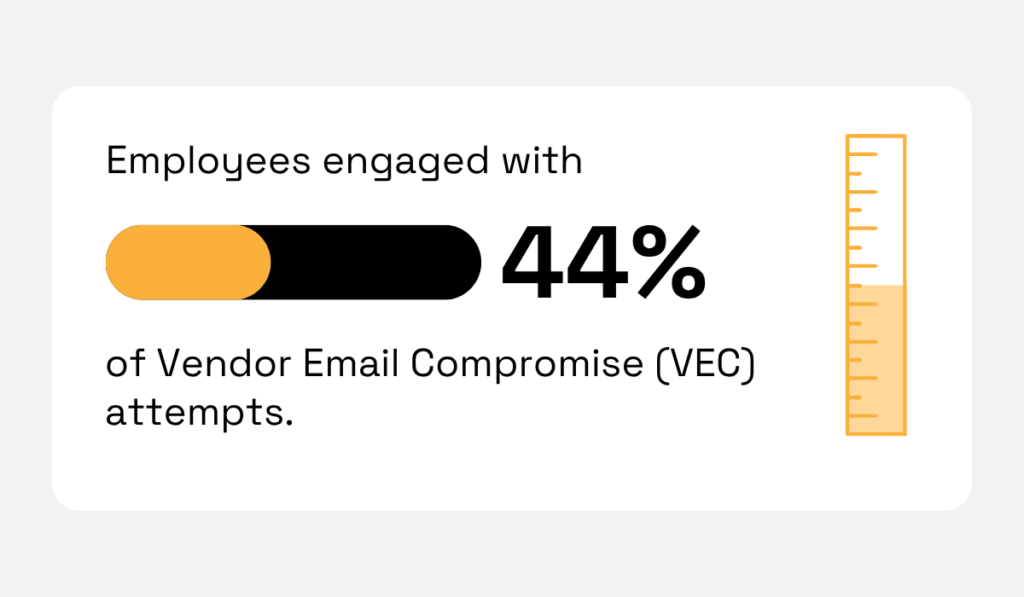
Illustration: Veridion / Data: Abnormal
In large enterprises, where employees simply can’t know the nuances of every vendor’s operations or correspondence style, this engagement jumped to 72.3%.
And this comes as no surprise.
Without that context, subtle anomalies like unusual phrasing or unexpected requests often go unnoticed.
Fraudsters operate in that very space of uncertainty.
They meticulously mimic vendors by spoofing email domains, replicating invoice templates, or setting up lookalike websites to redirect payments to their own accounts.
Common indicators of vendor impersonation fraud include:
In a typical scenario, the invoice looks legitimate and the PO numbers match, but the payment details have been quietly altered.
What makes these attacks particularly dangerous is how authentic they appear, thanks to genuine purchase data or forged letters from real banks, as was the case in the U.S. recently.
Namely, Milwaukee city officials lost nearly $461,000 after fraudsters impersonated a vendor and used a forged bank letter to convince staff to update payment details.
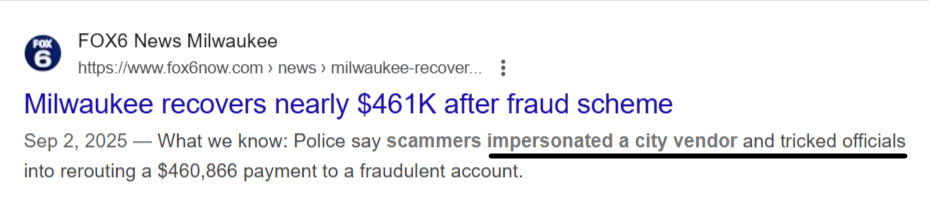
Source: Fox6 Milwaukee
The only indication that something wasn’t right?
An email that originated from a “.us” domain rather than the vendor’s usual “.com.”
Upon closer inspection, it’s clear that the criminals’ initial success depended on two things:
Both of these reflect broader organizational vulnerabilities, namely weak internal controls and insufficient employee awareness.
Of course, it’s not just poor defenses.
Scammers can easily harvest data from individual social media profiles, corporate websites, and even conference listings to craft convincing personas.
With professional and personal identities blending online, attackers gain access to rich material for tailored impersonations, notes Ronnie Manning, Chief Brand Advocate at Yubico.
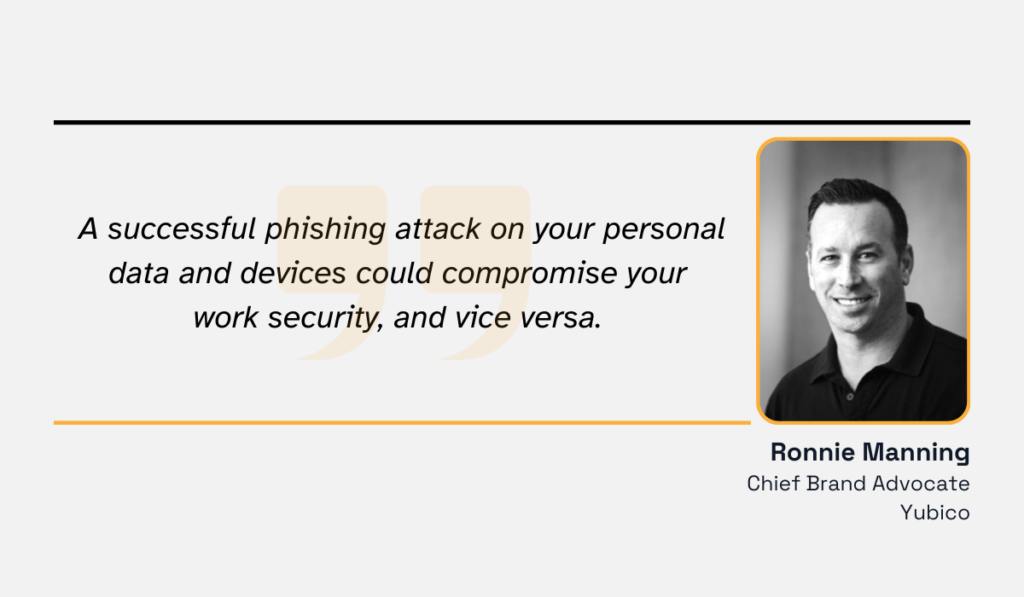
Illustration: Veridion / Quote: Talker Research
Reducing one’s digital footprint helps, but it’s only part of the solution.
Vendor impersonation fraud continues to evolve, and emerging technologies such as generative AI make it easier than ever to replicate vendor communications, documents, and identities at scale.
And as we’ll see next, this technological shift is redefining how impersonation fraud operates, and how organizations must respond.
Artificial intelligence has made vendor impersonation fraud not just more sophisticated, but also far harder to detect.
The closer one gets to mimicking a trusted vendor, the more convincing their fraudulent email or call will be.
Malicious actors are increasingly using AI to craft attacks, which makes them cheaper to execute, faster to iterate, and more likely to succeed.
The main question is: are your current defenses ready for this new level of deception?
According to Teleport, over half of the surveyed senior managers and C-level executives reported that protecting against AI-powered impersonation attacks was either moderately or extremely difficult.
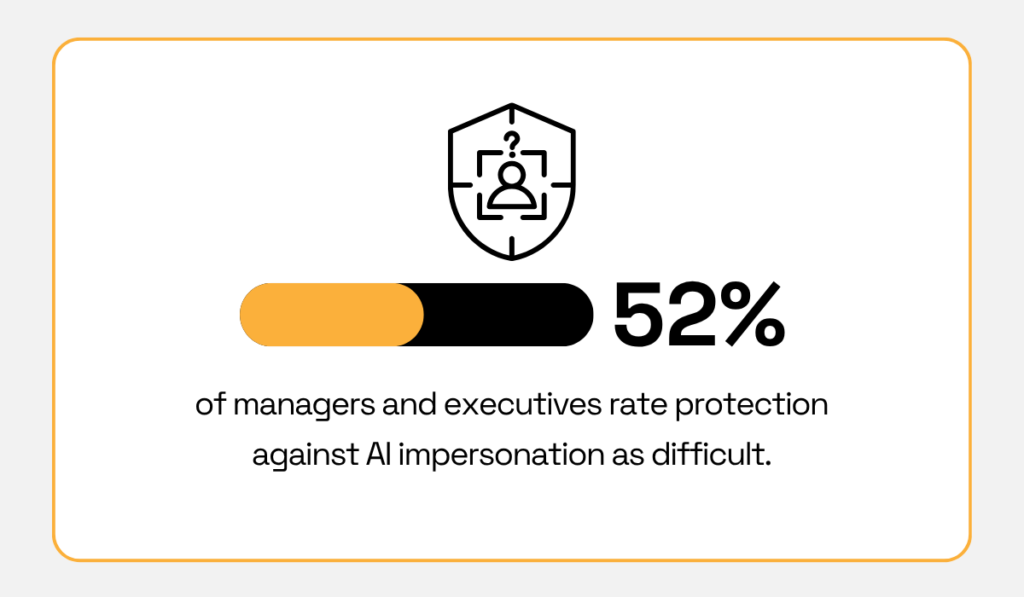
Illustration: Veridion / Data: Teleport
In fact, AI impersonation emerged as the most challenging type of attack to defend against, surpassing even traditional social engineering and compromised credentials.
Why?
Because AI tools can generate highly realistic fake emails, replicate writing styles, and even produce synthetic voices or videos that convincingly impersonate vendors.
Suddenly, the old red flags like unfamiliar email addresses, typos, or awkward phrasing aren’t enough to protect your organization.
And the consequences can be devastating.
In early 2024, several media outlets reported on a case in which scammers used an AI-generated deepfake video and voice to impersonate senior executives, convincing an employee to transfer them roughly HK$200 million (around US$25 million).
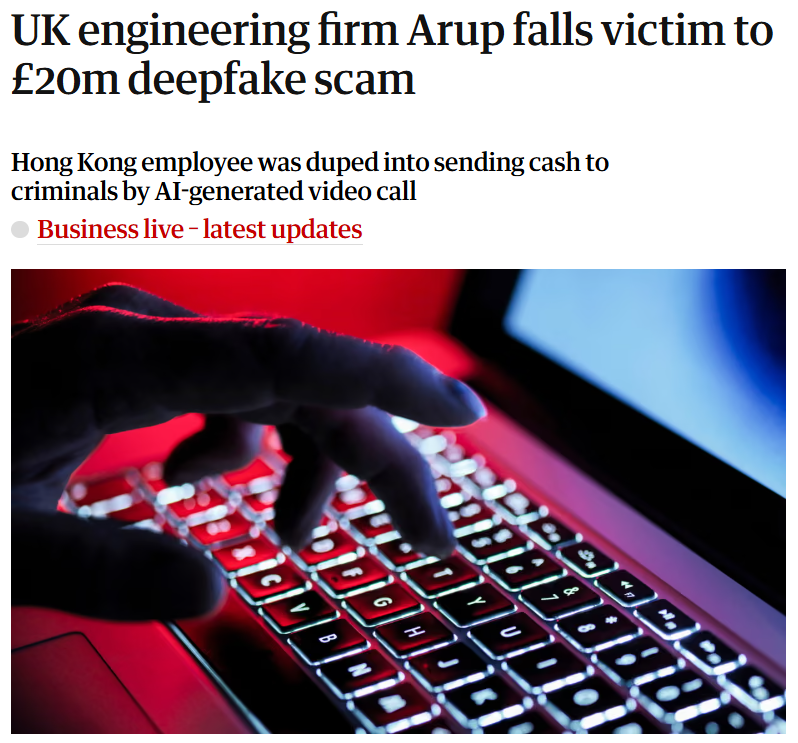
Source: Guardian
The fraudsters recreated the look and sound of company leaders in a live video call, swiftly bypassing the human “gut check” that usually stops such scams.
Just imagine a similar level of sophistication applied to vendors instead of executives.
A deepfake “vendor representative” could just as easily initiate a call and demand payment for supposedly ignored invoices.
Paired with AI-generated email threads or forged documentation, even the most vigilant employees could be deceived.
In reality, a successful scam doesn’t require video.
AI-written emails can now mimic tone, formatting, and phrasing well enough to trick trained professionals.
This can transform what used to be a clumsy phishing attempt into a routine-looking vendor update.
What’s even more alarming?
Talker Research shows that AI-powered scams are effective across generations, with Gen Z, millennials, Gen X, and baby boomers alike struggling to differentiate human from AI-generated correspondence.
With threats coming from multiple angles, the need for connected systems and greater vigilance has never been more urgent.
As Shai Gabay, CEO of Trustmi, warns:
“GenAI has weaponized fraud into a coordinated business attack. Attacks now cross multiple systems, exploiting every gap between teams and tools. Without unified visibility and coordination, enterprises will continue to face threats no single control can stop.”
So, where does that leave organizations?
While AI certainly complicates the threat landscape, it can also be part of the solution, but more on that soon.
The key takeaway for executives and procurement teams is this:
AI reshapes the very nature of trust in vendor interactions, and your teams need to be ready to spot the next generation of sophisticated, AI-enabled scams.
When it comes to vendor impersonation fraud, one misstep can lead to lost funds, data breaches, and reputational damage.
Let’s explore some practical steps organizations can take to safeguard both payments and trust, focusing on verifying vendor identities, centralizing data, and educating employees.
Using multi-channel verification is essential for confirming vendor identity and preventing fraud.
As we’ve established, email channels are frequently exploited in impersonation fraud.
However, relying on any communication channel in isolation is a recipe for disaster.
The surest way for organizations to strengthen trust is to maintain multiple channels, such as phone calls, secure procurement portals, video verification, and authenticated messaging apps.
This makes it easier to spot anomalies that wouldn’t stand out in email alone, thereby flagging suspicious activity before any funds are transferred.
Impersonation attacks exploit pre-existing trust, which is why ongoing relationships are often the target.
Gartner’s 2019 research underscores this point, showing that eight in ten organizations discover third-party risks after the due diligence period.

Illustration: Veridion / Data: Gartner
Ongoing vigilance is, therefore, essential.
Multi-channel verification provides an additional layer of security.
Take procurement portals equipped with two-factor authentication (2FA).
2FA methods include one-time passwords, biometric verification, or trusted device access, requiring users to confirm their identity beyond a simple username and password.
Source: Clinked
This extra step may seem small, but it significantly strengthens security.
Of course, companies that are ready to bolster their security measures are best equipped to protect their bottom line.
The aforementioned Teleport research shows that organizations investing in robust security infrastructure experience 90% lower annual costs related to fraud and breaches compared with companies with minimal protection.
Ultimately, establishing multi-channel verification protocols ensures that payment instructions are legitimate and secure, reducing the risk of falling for fake invoices or altered bank details.
Scattered or outdated vendor records make impersonation easier.
When contact details, payment information, or ownership data sit across multiple systems, it becomes much harder for employees to verify vendors.
And that much easier for fraudsters to slip through the cracks.
Having a centralized source of truth ensures that every department, from procurement to finance, works with the same verified information.
But implementing a solution and making it work is often easier said than done.
Transparent’s recent report, which focused on vendor data quality, showed that even mature organizations have serious gaps in their vendor data.
This ranges from missing bank details and outdated VAT numbers to incomplete contact information, as detailed below.
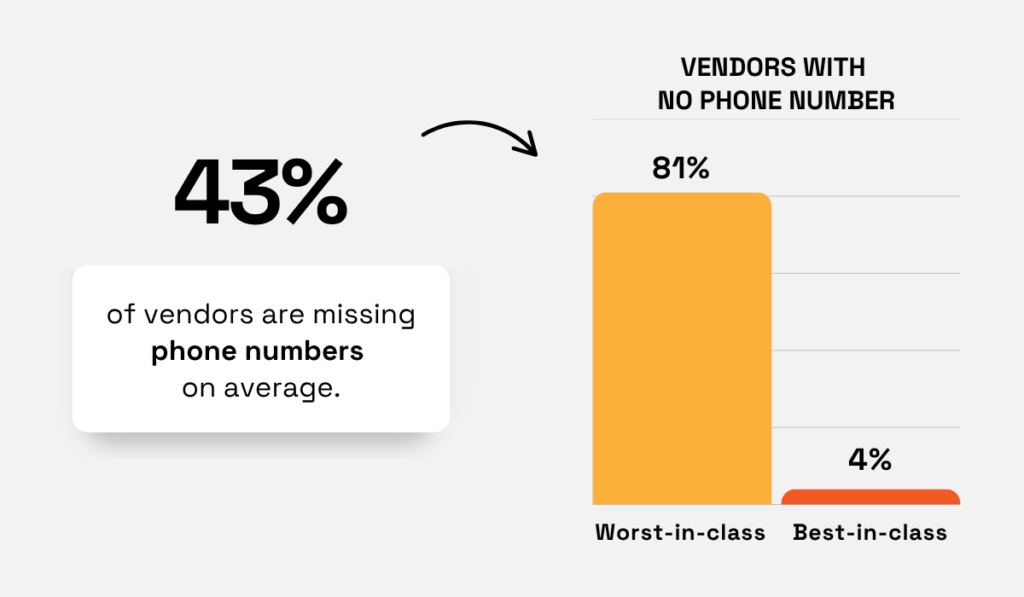
Illustration: Veridion / Data: Transparent
If even enterprises equipped with advanced ERP or procure-to-pay (P2P) systems struggle to maintain accurate vendor records, what’s the missing piece?
The answer lies in data enrichment and validation powered by reliable external sources.
Integrating verified data from business intelligence platforms like Veridion strengthens vendor validation by providing accurate company identifiers, contact details, and real-time business updates.
The platform’s AI-driven network covers 130+ million verified company profiles, including hard-to-track SMBs, refreshed weekly to capture any changes in ownership, status, or activity.
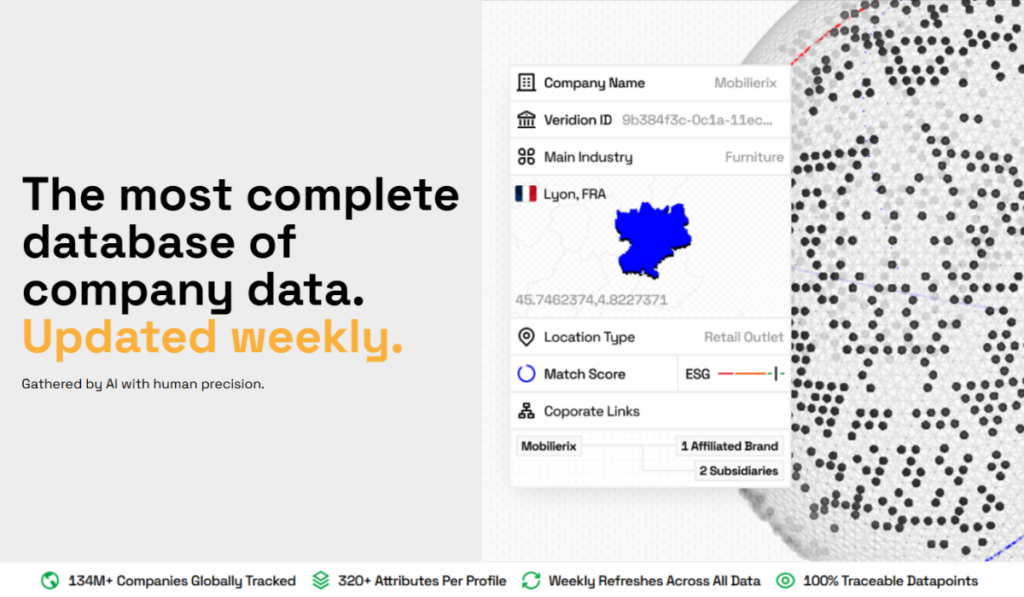
Source: Veridion
With fraudsters often exploiting the gap between data updates, solutions that support smart, continuous updates make those gaps virtually disappear.
Each vendor profile includes over 320 data points, from industry classification to ownership structure, giving enterprises a complete view of every supplier they work with.
And it’s all accessible from a single, centralized dashboard.
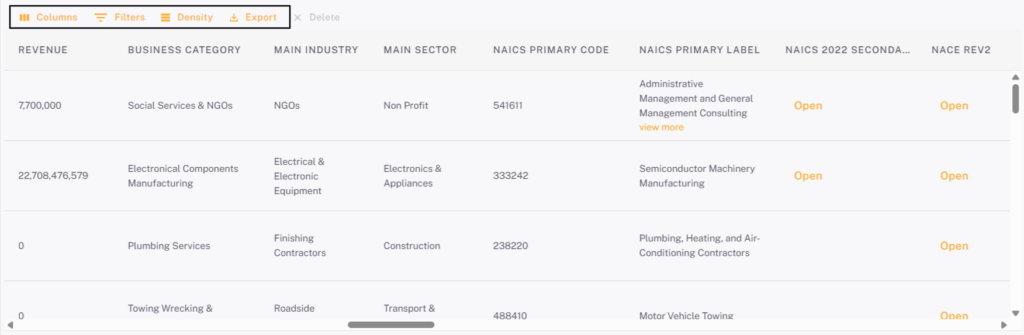
Source: Veridion
Seamless ERP and procurement integrations through APIs or batch updates ensure that records stay current automatically, reducing manual effort while closing data gaps.
In short, centralizing and enriching vendor data transforms it from a passive repository into an active safeguard that continuously validates trust.
Employees are often the first (and sometimes only) line of defense against vendor impersonation fraud.
That’s what makes ongoing fraud awareness and cybersecurity training core operational safeguards.
Yet, many companies still underestimate its importance.
According to Talker Research, 40% of employees say their organization has never provided them with cybersecurity training.
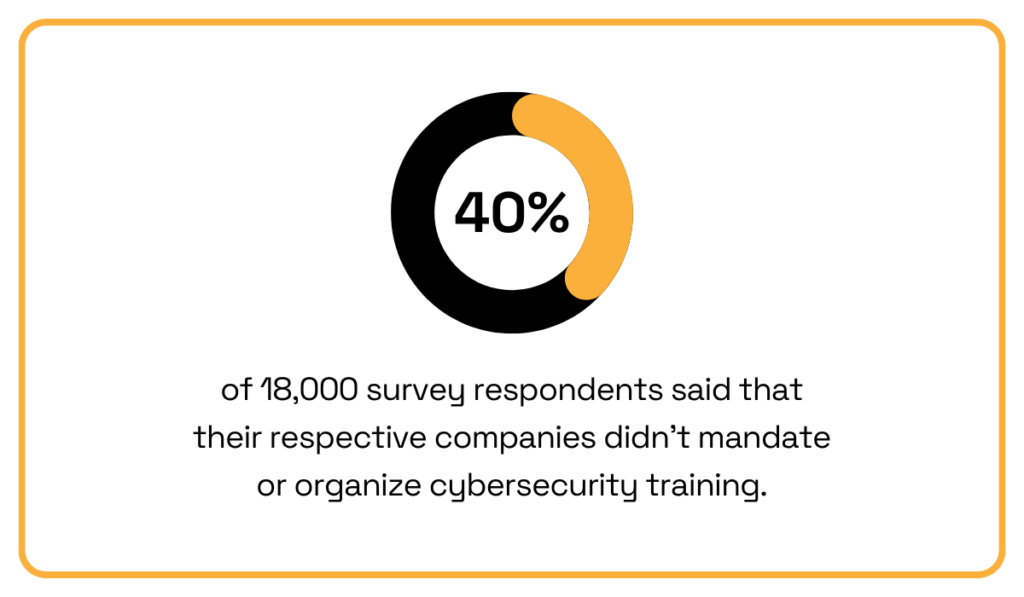
Illustration: Veridion / Data: Talker Research
Of course, effective education doesn’t translate to holding annual workshops.
It means equipping your team with the practical ability to spot subtle red flags, be it urgent payment requests, small visual discrepancies in logos or email domains, or unusual phrasing in vendor communications.
Training should also reinforce authentication standards, such as confirming requests through independent channels, and emphasize contextual awareness.
And while AI has made impersonation harder to detect, it’s also becoming a key part of the defense strategy.
Solutions like StrongestLayer deliver AI-driven training simulations that replicate realistic phishing and impersonation attempts based on the latest threat patterns.
These adaptive systems provide instant feedback, explaining how fake emails mimicked vendor branding and highlighting subtle cues employees missed, as well as powerful data visualization options.
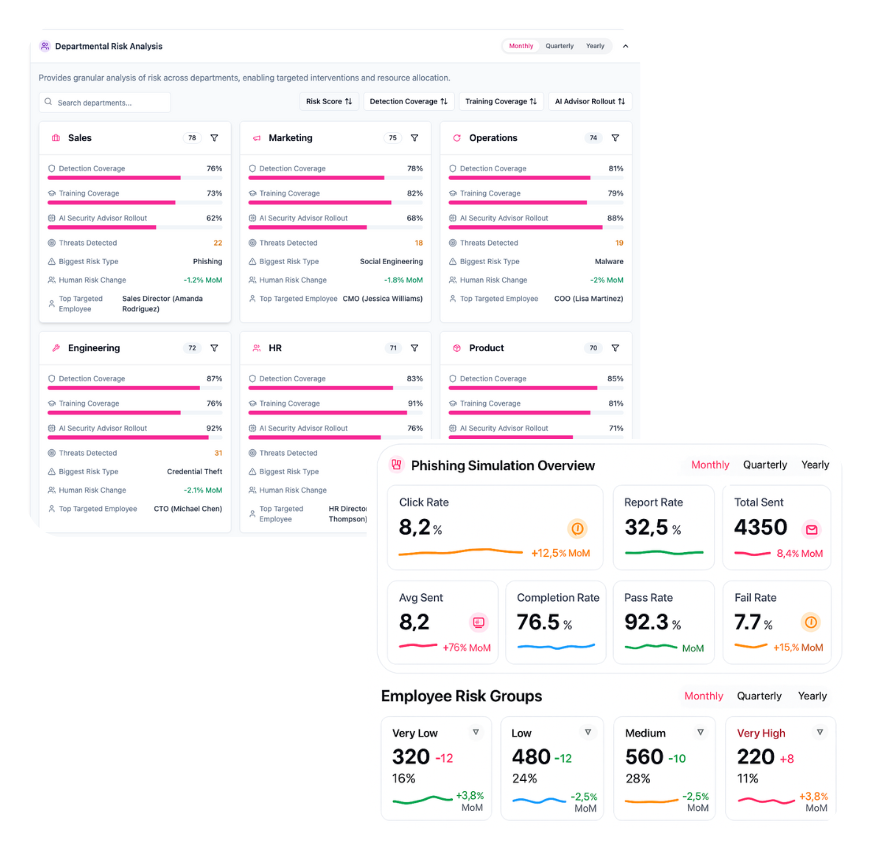
Source: StrongestLayer
Over time, the system refines learning material automatically, helping each individual improve where they’re most vulnerable.
Still, awareness is only effective when employees understand why it matters.
As Brad Deflin, cybersecurity expert and founder of Total Digital Security, notes:

Illustration: Veridion / Quote: AFP
Using real-world case studies and interactive exercises can make this message resonate across departments.
Empowered, informed employees form the cornerstone of a proactive, fraud-aware culture that actively detects, reports, and prevents vendor impersonation before it causes harm.
Vendor impersonation fraud is not a niche cyber threat, but a structural challenge for modern enterprises.
The good news?
With multi-channel verification, centralized vendor data, and regular, adaptive employee training, organizations can dramatically reduce their exposure.
AI may have raised the stakes, but it also provides new tools for smarter, proactive defense.
The key is to act before fraudsters do and reinforce trust at every point of vendor interaction.