Vendor Fraud Schemes: 5 Real-Life Examples to Learn From


Key Takeaways:
With sophisticated scams evolving across industries, vendor fraud today is hardly limited to forged invoices or delayed deliveries.
To understand what makes these schemes succeed, we’ve examined five real-life cases, outlining the key weaknesses exploited by fraudsters and the technologies they’re using.
If you manage high-value vendor networks in an enterprise setting and want to strengthen your procurement and finance teams’ expertise, this is the article for you.
For procurement and finance teams, vendor payment fraud remains one of the most persistent operational risks, and the recent incident in Baltimore shows how quickly it can materialize.
The city of Baltimore inadvertently wired $1.5 million to criminals posing as one of its contractors for development projects.
Source: The Banner
How did the deception unfold?
The fraudsters initially gained access to the vendor’s legitimate email account and monitored correspondence until a payment was due.
They could then insert new banking information into an active thread, creating the impression of a simple, routine update.
AP ended up processing the change without requiring a secondary verification step.
In total, $1.52 million was diverted and roughly $721,000 recovered, leaving the city with an $803,000 loss.
While the public sector faces its own operational constraints, the underlying failure points mirror what many enterprises face:
This pattern fits a broader trend.
According to the 2025 AFP Payments Fraud and Control Survey, 60% of all BEC scams in 2024 targeted organizations by impersonating vendors.
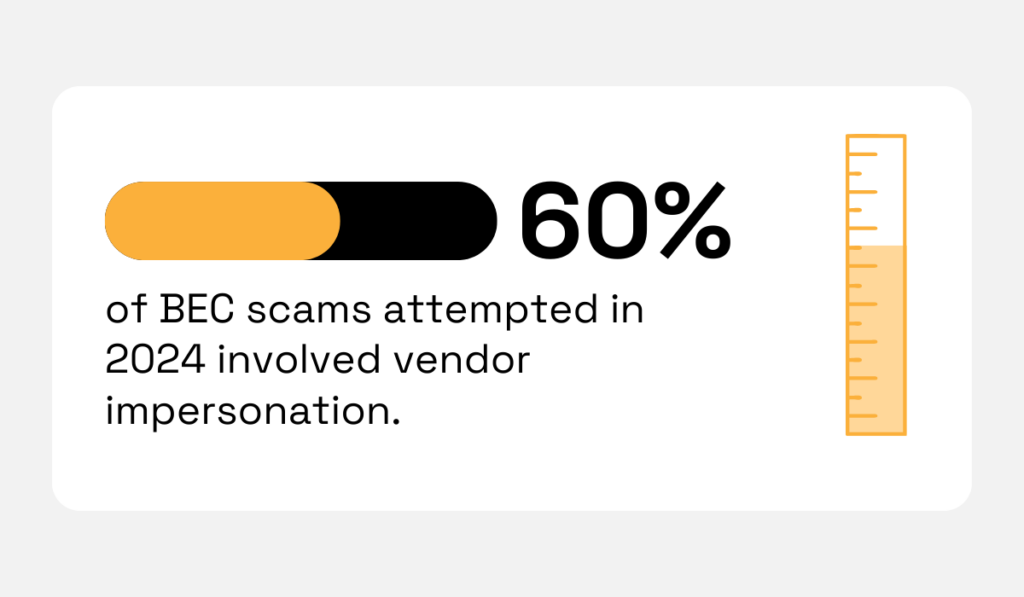
Illustration: Veridion / Data: AFP
While more and more scammers are going after large transfers, the ideal targets have well-documented weaknesses.
Baltimore had already seen two similar incidents in recent years, losing $62,000 in 2019 and $376,000 in 2022, both of which involved fraudulent requests to update banking details.
This trail of incidents suggests the need for more rigorous procedures.
According to the Office of the Inspector General, the AP policies did not require phone-based verification for vendor updates, and no vendor signatory lists were maintained.

Illustration: Veridion / Quote: PYMNTS
Both gaps are common failure points in organizations with fragmented vendor management workflows.
However, the human factor amplified the exposure.
The scammer provided a personal email address rather than an official domain, but the employee who was the first point of contact still approved it.
Plus, two additional AP employees validated the fraudulent change without checking documentation, which means a total of three employees didn’t feel that anything was amiss.
For enterprise procurement teams, the lesson is clear: strengthen verification workflows, implement regular employee training, and reduce reliance on email as the sole channel for vendor updates.
The Baltimore case underscores that while evolving tactics are a cause of concern, most scams succeed because organizations rely on assumptions rather than structured, enforced controls.
Collusion changes the difficulty level of vendor fraud entirely, with the Intel Israel case showing just how quickly internal cooperation can neutralize standard controls.
In 2025, the company filed a lawsuit against former supplier Yafim Tsibolevsky and former employee Natalia Avtsin, alleging a joint scheme that cost Intel Israel more than $840,000.
Source: Tech in Asia
Intel Israel’s investigation found that Avtsin had been submitting fraudulent invoices for over a year by manipulating transaction classifications.
After legitimate approvals were granted, she allegedly reclassified certain purchases from “components” to “services.”
Why does that matter?
Intel’s service payments didn’t require a signed delivery note or confirmation of receipt from another internal party, while component purchases had this additional verification step.
So, by switching these two categories, the former employee neutralized the mechanisms that would have prevented unverified and fraudulent invoices.
This reclassification created an opening for Tsibolevsky, who received payments without additional oversight.
According to the lawsuit, Avtsin strengthened the scheme even further by keeping every invoice below her approval threshold of $20,000.

Illustration: Veridion / Quote: CTech
Anything above that amount required a second sign-off, which would have added scrutiny neither party could afford.
Between October 2023 and November 2024, the pair allegedly submitted dozens of these low-value, service-classified invoices.
The pattern only surfaced after Avtsin was dismissed for unrelated reasons and routine internal audits flagged suspicious irregularities.
But this raises a bigger question for enterprises: how often do finance or procurement teams truly run real-time checks across every transaction?
Trustpair research indicates that this is rarely the case, with most firms still relying on periodic account reviews rather than continuous, real-time monitoring.

Illustration: Veridion / Data: Trustpair
That’s exactly how even relatively small invoices can accumulate into large losses.
If each transaction was capped at around $20,000, the $840,000 total suggests dozens of payments slipping through the cracks.
And when insiders know precisely which labels deactivate controls, manual reviews and threshold-based approval systems lose much of their defensive power.
So what can procurement teams take from this?
Three practical tweaks stand out:
Besides increasing awareness of internal-external collusion, the Intel Israel case illuminates how the smallest gaps create some of the easiest entry points for fraud.
Between 2013 and 2015, two U.S. tech giants fell victim to a single fraudster posing as a vendor.
Using forged invoices, fake contracts, and lookalike email addresses, Evaldas Rimasauskas tricked Google and Facebook into sending massive payments, totaling over $100 million, before his scheme came to light.

Source: The Guardian
Subsequent investigations revealed several key details, starting with the fact that Rimasauskas registered a company in Latvia under the same name as a legitimate Asian hardware manufacturer.
He then sent fraudulent emails to employees and agents of the victim companies, all of whom regularly conducted multimillion-dollar transactions with the actual vendor, and therefore thought nothing of it.
To make the scam convincing, Rimasauskas also forged corporate letters, invoices, stamps, and contracts, creating an appearance indistinguishable from the real vendor.
Several years later, the total losses were confirmed at $120 million, and Rimasauskas was sentenced to five years in prison.

Source: U.S. Attorney’s Office
While it took place over a decade ago, this episode underscores a simple but crucial point for enterprises:
Recent data highlights the scale of the risk.
A Trustpair report reveals that 55% of surveyed companies experienced fraud attempts rooted in supplier credential changes, while 33% reported incidents of business email compromise and phishing.
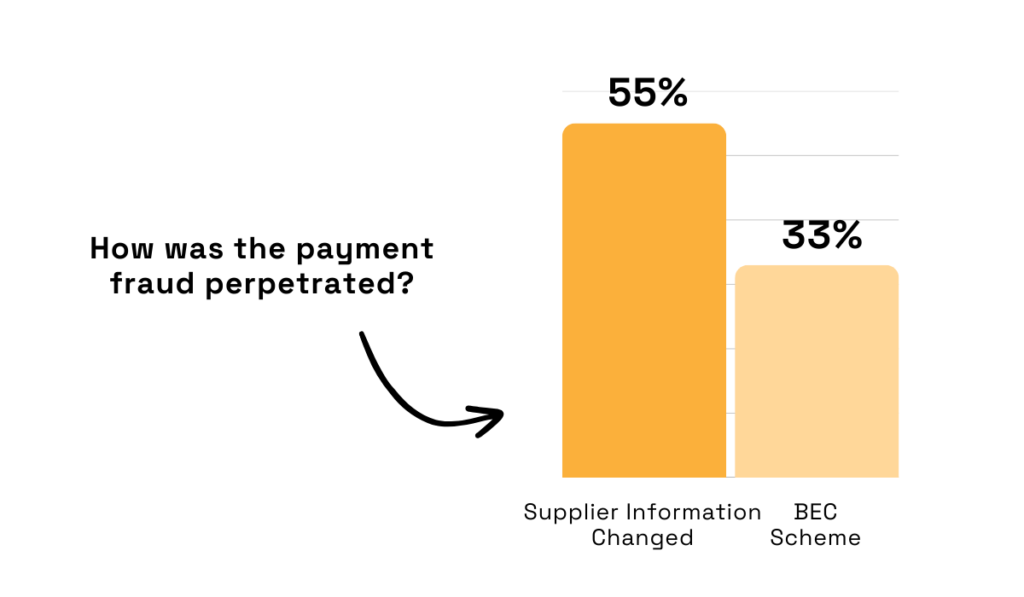
Illustration: Veridion / Data: Trustpair
But the main question is: how can procurement teams detect a lookalike vendor before the first payment is sent?
Teleport’s 2024 research highlights the effectiveness of implementing phishing‑resistant passwordless authentication.
Many enterprises are also turning to different types of software for vendor fraud prevention.
However, maintaining a clean, verified vendor master creates a solid foundation for all prevention efforts, helping you:
To scale these efforts, enterprises can leverage automated solutions, such as our AI-powered vendor data verification platform, Veridion.
Veridion provides access to a global repository of fresh vendor data comprising 130+ million verified company profiles worldwide, including SMBs, with 320+ attributes available per profile.
Moreover, weekly updates capture changes in business status, ownership, or activity, giving teams real-time visibility into anomalies.
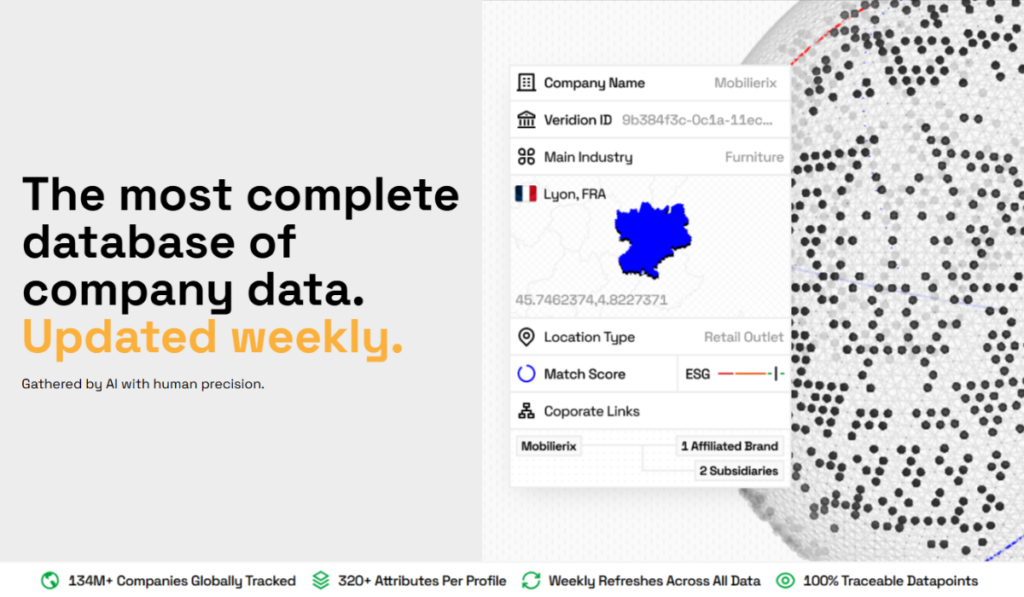
Source: Veridion
With this platform, you can automatically deduplicate, enrich, and validate supplier data using AI and machine learning, with alerts and monitoring configured to track any suspicious changes.
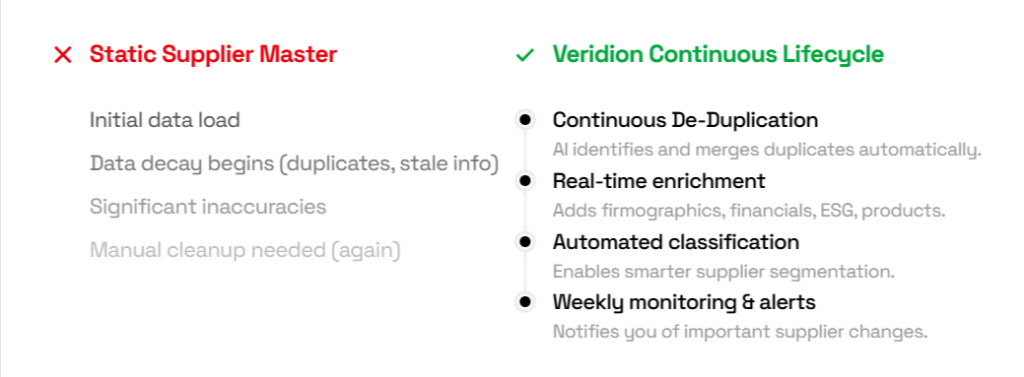
Source: Veridion
Most importantly, the data enrichment process itself is nearly effortless, as demonstrated in the video below.
Source: Veridion on YouTube
Ultimately, this case is a cautionary tale for enterprises handling large and complex vendor networks, but also a valuable lesson on which mechanisms and tools you need to improve or introduce.
Unfortunately, AI technology has helped amplify both vendor and executive impersonation, with one early example occurring in 2019.
Namely, a company lost $243,000 due to AI-generated voice mimicry.
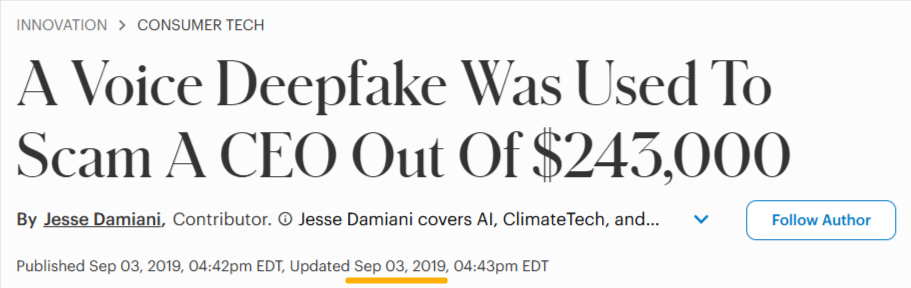
Source: Forbes
While this case involved an executive rather than a vendor, it illustrates how easily machine learning can bypass human verification.
Thanks to the subtle German accent and closely replicated speech patterns, the CEO of an unnamed UK-based energy firm was convinced he was contacted by the chief executive of their German parent company.
The request for a follow-up payment alerted him that something was wrong, but the first payment had already been executed.
At the time, little was known about the software used or how the voice data had been obtained, yet the case clearly demonstrates how AI can exploit familiar communication cues.
Fast forward to 2024, and the technology had become significantly more sophisticated.
A multinational firm in Hong Kong authorized a $25 million payment after a video call where the CFO and several staff appeared present, but all participants were deepfake recreations.

Source: CNN
Although the employee was initially suspicious of a CFO’s email regarding a large transaction, seeing familiar colleagues at the meeting convinced them to approve the $25 million payment.
Ev Kontsevoy, CEO at Teleport, explains why AI impersonation is a major concern for enterprises today:
“The reason AI impersonation from cyber criminals is so difficult to defend against is that it is getting better and better at mimicking legitimate user behavior with high accuracy, making it challenging to distinguish between genuine and malicious access attempts.”
In the face of such a threat, simple verification steps like recognizing familiar voices or email addresses are clearly insufficient.
And if AI can fool employees familiar with executives, it can be even more effective in tricking staff handling vendor payments.
Fortunately, AI detection tools are becoming a necessary mitigation element.
Textual analysis solutions, such as Proofpoint, flag anomalous email patterns, while platforms like Sensity focus on video and audio deepfake detection.
Teleport study shows that organizations leading in security infrastructure are 35% more likely than peers to employ AI to strengthen their safeguards.

Illustration: Veridion / Data: Teleport
To sum up, key practical steps include:
As the technology behind deepfakes advances, relying solely on traditional verification is increasingly insufficient, so be sure to revamp your workflows and consider integrating AI detection tools.
Bid rigging is a distinct form of vendor fraud, where suppliers conspire to manipulate competitive bidding processes for their own gain.
In the case of Pontiac-based Asphalt Specialists (ASI), executives colluded with other contractors to create the illusion of competition while the winners were predetermined.
From 2013 through 2018, ASI conspired with Al’s Asphalt, F. Allied Construction, and other co-conspirators to submit noncompetitive bids for asphalt paving contracts in Michigan.
By sharing pricing information and designating winners, the companies secured $17.3 million in sales across 46 organizations, which resulted in a flurry of convictions.
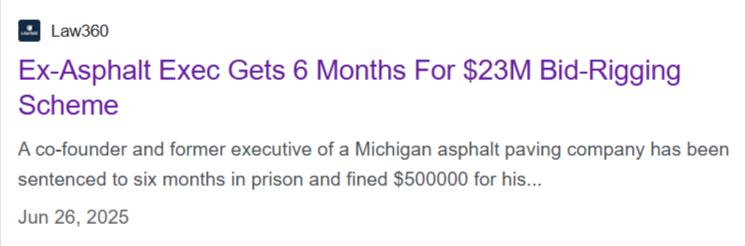
Source: Law360
Daniel Israel, former ASI president, was recently sentenced to six months in prison and ordered to pay a $500,000 fine.
However, he is just one of seven individuals and three companies charged in the ongoing federal antitrust investigation, which has already resulted in over $8.2 million in criminal fines.
Source: Office of Inspector General, U.S. Department of Transportation
How does this impact companies exactly?
While precise figures are hard to pin down, one seminal study shows that a typical bid-rigging scheme can raise prices by over 20% for over 4 years.
Although bid rigging can be viewed as a distinct criminal activity, it shares core characteristics with other forms of vendor fraud, namely:
So, what do procurement teams need to keep in mind?
Simply put, taking specific supplier behaviors at face value and relying on a narrow pool of vendors can conceal collusion just as effectively as fraudulent invoices or vendor impersonation.
Mitigating the financial risks of bid rigging starts by being aware of key warning signs and implementing corresponding practices.
| Warning Sign | Recommended Practice |
|---|---|
| Repeated winning bids by the same vendor | Rotate vendors and maintain a diverse supplier pool |
| Predictable bid patterns across projects | Benchmark bids using market rates and historical data |
| Unusual pricing alignment | Conduct independent audits of bids and contracts |
| Limited supplier participation | Encourage open tendering and competitive solicitations |
| Vendors sharing information or aligning proposals | Implement segregation of duties and confidential bid handling |
Bid rigging hides behind familiar vendors and predictable patterns, but recognizing these patterns and implementing structured verification measures will help your team identify potential collusion before it results in financial loss.
Vendor fraud schemes can impact even the largest, most sophisticated organizations.
From AI-driven impersonation to collusion and bid rigging, all of the schemes we covered exploit predictable processes and gaps in verification.
Strengthening your safeguards usually involves structured process reviews, increased employee awareness, and leveraging technology that improves visibility and automates processes.
Begin today, and you’ll be able to catch anomalies early on and avoid any financial or reputational blows.