Types of Vendor Fraud You Need to Know About


Key Takeaways:
In procurement, vendor fraud is a threat that can quietly drain resources and erode trust.
Fraud, in its many forms, is a continuous battle that smart procurement teams must be vigilant about.
From bogus invoices to AI-driven impersonations, staying alert is key to preventing these threats.
For enterprise procurement specialists, a deep understanding of the evolving landscape of vendor fraud is not just about loss prevention.
It’s a strategic move to safeguard your organization’s financial health, operational integrity, and competitive advantage.
In this comprehensive guide, we’ll explore the six forms of vendor fraud and provide actionable strategies to fortify your defenses.
Billing fraud represents one of the most common and persistent forms of vendor deception, where suppliers exploit weaknesses in accounts payable processes through various invoicing schemes.
This type of fraud may include:
According to accounts payable automation provider Medius, the financial impact of fraudulent invoices is substantial, with U.S. companies losing an average of $300,000 per year.
This underscores the urgency and necessity of robust prevention strategies.
Jim Lucier, CEO of Medius, underlines the rising trend of invoice fraud in the context of complex global supply chains.
He stresses the role of technology in empowering finance and accounts payable teams to combat invoice fraud and streamline manual tasks, instilling confidence in their defense strategies.

Illustration: Veridion / Quote: PR Newswire
In practice, a vendor, often aided by a colluding employee, will slip fake or padded invoices into the accounts payable stream.
Even requesting advance payment for a false order constitutes billing fraud.
In 2024, the hospitality group Cipriani filed a lawsuit alleging a decade-long fraudulent invoice scheme.
According to the claim, a vendor created bogus invoices and a shell company to bill Cipriani for services, including fridge maintenance.
The alleged total fraud amounted to approximately $3 million in kickbacks and around $5 million in fake invoices between 2013 and 2023.

Source: New York Post
So, how do you beat billing fraud?
Simply put, by tightening invoice controls.
Require three-way matching (invoice vs. purchase order vs. goods receipt) to catch duplicates or padded charges.
Better yet, use automated accounts payable tools or fraud detection software to flag any invoices that don’t match purchase order terms.
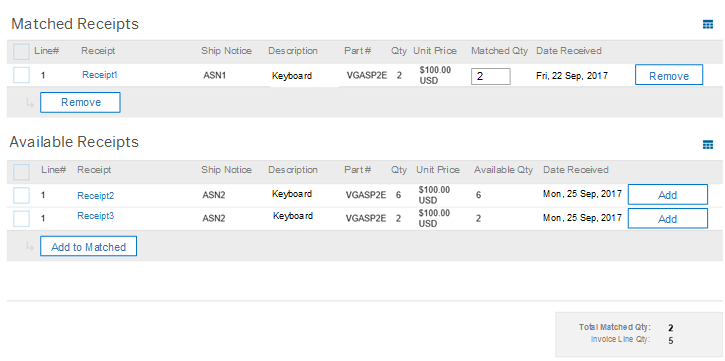
Source: SAP
Maintain strong audit trails that document every step of the approval process, verifying who approved each payment and creating accountability and visibility.
But most importantly, regularly review your vendor master to verify every vendor’s address, tax ID, and bank account details before making a payment.
Bid rigging represents a particularly insidious form of procurement fraud that undermines the very principle of competitive pricing.
This scheme occurs when vendors (and sometimes insiders) conspire to skew a competitive bidding process.
Rather than competing fairly, the conspirators agree in advance on who will win a contract—often rotating winners or splitting bids—and they submit artificially high proposals to keep prices inflated.
Essentially, the bidders create an illusion of competition while secretly cooperating.
This collusion destroys competition and drives up costs.
As the U.S. Department of Justice warns, collusion results in inflated prices and cheated customers.
For large enterprises, this means paying significantly more for goods or services than the market rate would dictate.
Research confirms bid rigging is widespread.
In fact, research shows, it is the second most common fraud type globally.
Over a third of organizations worldwide have already been victimized by rigged contracts.
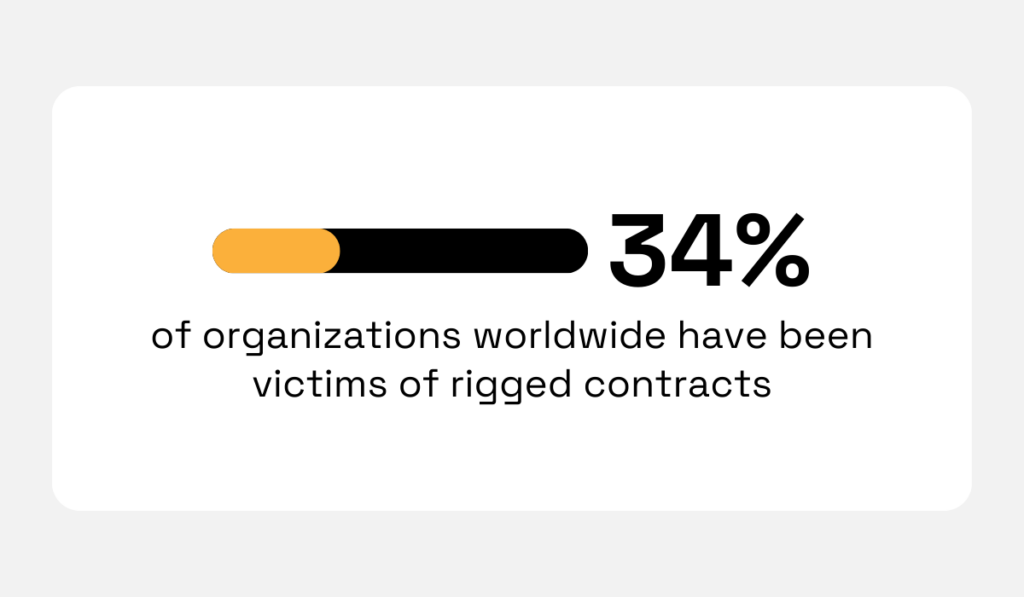
Illustration: Veridion / Data: SAS
Rigged contract fraud often involves complicit employees who may receive kickbacks in exchange for steering contracts to predetermined vendors.
The tactics used?
They can vary from simple price-fixing agreements among established suppliers to more sophisticated approaches where vendors take turns submitting the lowest bid or deliberately submit non-competitive proposals to ensure a specific company wins the contract.
Oak View Group (OVG) LLC Chair and CEO Tim Leiweke was recently indicted for bid rigging in connection with the construction of the University of Texas’ Moody Center.
Leiweke allegedly struck a deal that the rival firm would agree to avoid bidding for the contract in exchange for OVG providing it with the project’s subcontracts.
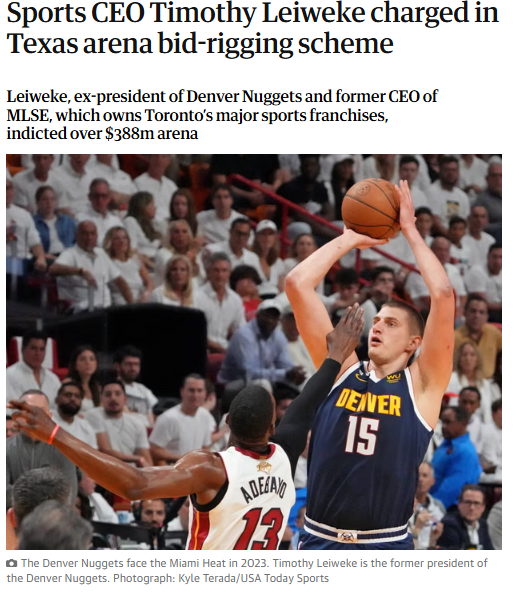
Source: The Guardian
To combat bid rigging, enforce a transparent and well-documented bidding process.
You can do this by implementing clear evaluation criteria and requiring vendors to submit sealed bids, keeping bid details confidential until the award is made.
On top of that, make sure to conduct vendor due diligence: verify that competing bidders are independent.
In other words, there should be no overlapping ownership or addresses.
Rotate your bidding managers, watch for any patterns of identical bid prices or suspicious timing, and train procurement staff to spot collusion.
And remember: bid rigging is illegal under antitrust laws, so involving legal counsel or reporting suspicious collusion to regulators is an option in extreme cases.
Shell company fraud occurs when fictitious vendors are explicitly created to funnel payments for non-existent goods or services.
These phantom entities often appear legitimate on the surface, complete with fabricated documentation, including bank account details, tax identification numbers, and business addresses.
This scheme frequently involves internal collusion, where employees help establish or approve these fake vendors and then authorize payments for services that were never rendered.
Shell schemes exploit weaknesses in vendor onboarding and approval.
For instance, in a weakly controlled environment, an employee can slip a “ghost vendor” into the system.
The fake vendor may even use a real name or address stolen from a legitimate company, making it look authentic.
Often, the fraudster will make small initial payments that go unnoticed before increasing to larger amounts.
In a 2022 case, an employee of the Oregon Health Authority (OHA) created a sham company and used it to issue false invoices, thereby garnering payments that she deposited into a fraudulent bank account.
The employee submitted 35 invoices for non-existent events and deposited close to $1.5 million into the shell company’s bank account.

Source: ACFE
So how can you protect yourself from shell company fraud?
Diligent verification is the key.
Before adding any new vendor, require proof: confirm their business registration, tax ID, website, and contact details.
Visit new vendors whenever possible, or at the very least, verify their addresses and phone numbers independently to ensure accuracy.
Check for duplicate or similar addresses in your vendor master because sometimes a fake vendor uses the same address as an employee or vendor partner.
Most importantly, use tools like Veridion to confirm vendor data legitimacy.
Our global business database provides continuously updated information on millions of companies worldwide, including compliance records, industry details, and corporate hierarchies.
Source: Veridion
With Veridion’s Match & Enrich API, you can instantly validate vendor identities by cross-checking company names, addresses, tax IDs, and ownership structures against trusted global data.
The API also enriches vendor profiles with additional risk indicators, helping you quickly spot inconsistencies or suspicious gaps that often signal fraudulent activity.
Source: Veridion on YouTube
Access to such verified data makes it much harder for a shell company to infiltrate your system.
In short, treat every new vendor with scrutiny: verify their identity through a second source and involve more than one person in the approval process.
This keeps phantom suppliers from draining your budget.
Quality substitution occurs when a vendor delivers inferior goods or different materials than agreed, but still charges the full price.
For example, a supplier might ship cheaper plastics instead of metal parts, or deliver used or refurbished components as new.
This deliberate deception causes more than direct financial loss through overpayment, though.
It also triggers downstream consequences, including product failures, safety issues, and significant damage to a brand’s reputation when inferior components are incorporated into finished products or services.
In the public sector alone, product substitution fraud is estimated to cost billions in extra replacement and repair expenses.
The quality fraud is particularly prevalent in industries with complex supply chains or those that utilize specialized materials, where quality verification requires specific technical expertise.
Fraudulent vendors bank on the assumption that your receiving and quality control teams won’t detect the substitution, especially if the inferior goods appear superficially similar to what was ordered.
In 2016, Target cut ties with Welspun, a leading home textile supplier, after discovering that some 750,000 sheets and pillowcases from the company had been mislabeled as Egyptian cotton.
Target alleged that the Mumbai-based company had violated supply contracts by passing off cheaper sheets as premium Egyptian cotton for a period of two years.
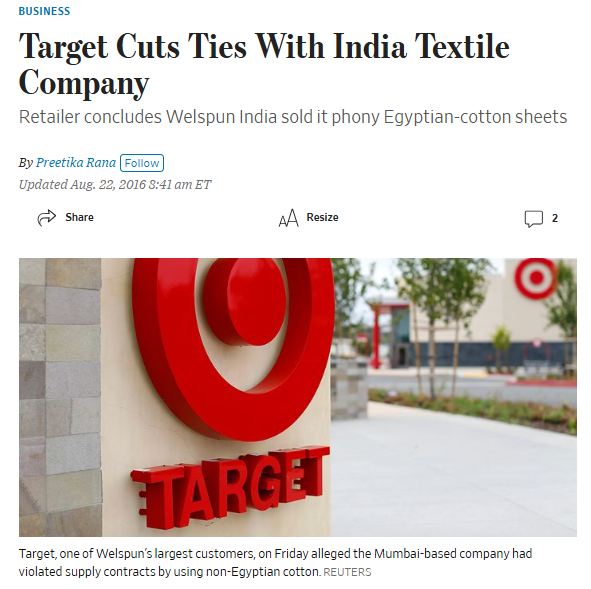
Source: Wall Street Journal
Strong quality controls are the defense against scenarios like this.
So, make sure to perform incoming inspections of shipments and sample tests, ideally by an independent quality team.
Regular audits and quality checks, especially surprise ones, make it less attractive for a vendor to slip subpar goods past you.
Ultimately, preventing quality substitution means verifying that what’s on the invoice matches what’s in your warehouse and defending your standards every step of the way.
Vendor email compromise (VEC) has emerged as one of the most financially damaging forms of cyber-enabled vendor fraud.
VEC is a form of business email compromise (BEC) in which cybercriminals impersonate legitimate vendors through hacked or spoofed email accounts to redirect payments or request sensitive information.
The fraudster either hacks a real vendor’s email account or spoofs an address to send fraudulent invoices or payment-change requests.
The issue is, such emails often appear authentic.
They use the same name, tone, and invoice style as the real ones, but they contain falsified wire instructions or requests for confidential data.
And because companies often pay invoices by email, these scams can be highly effective.
The bad news is, these attacks are on the rise.
According to recent research, as of March 2025, there was a 30% increase in BEC attacks.
BEC scams are also reported to have resulted in an average of USD $2.9 billion losses in 2023.
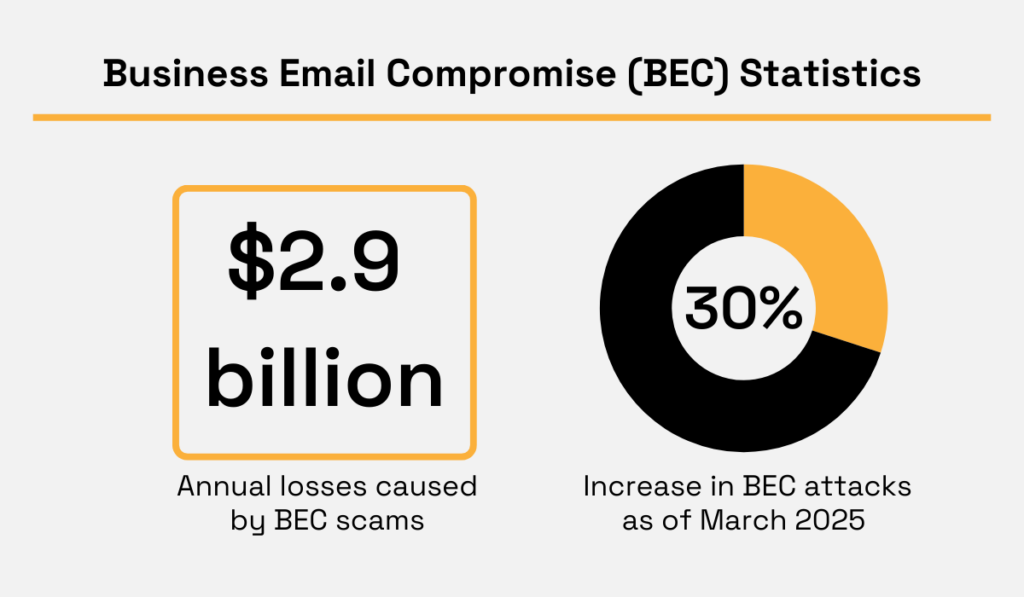
Illustration: Veridion / Data: Surefire Cyber and FBI
A high-profile example of VEC occurred in 2020.
Attackers spoofed a bookkeeper’s email at One Treasure Island, a nonprofit organization, and convinced staff to send a large payment to the fraudster’s account.
The organization lost $650,000 before catching the scam.

Source: Wall Street Journal
The best defense against VEC is proper vendor verification and employee training.
Educate staff to be suspicious of any emailed request to change payment details, even if it looks legitimate.
On top of that, utilize email authentication tools (SPF, DKIM, DMARC) to block spoofed domains.
And most importantly, never process a significant invoice change or new payment instruction without independent confirmation.
For example, if a regular vendor suddenly requests funds to be transferred to a new account, call them on a known phone number, not the one listed in the potentially suspicious email, to confirm.
In short, build in a “trust but verify” step for all email payment requests. This simple check will stop most VEC attempts.
The latest frontier is deepfake fraud, where criminals use AI-generated images, audio, or video to impersonate a real person, such as a company executive or supplier representative, and authorize bogus transactions.
Using publicly available audio or video of, say, your CEO or a known vendor contact, the attacker can create a convincing fake live call or voicemail.
This emerging threat has evolved from a theoretical concern to a practical reality, with sophisticated fraudsters using readily AI tools to create convincing impersonations.
In one notorious 2024 case, a finance worker transferred $25 million after participating in a video call with what appeared to be the company’s CFO, who turned out to be an AI-generated deepfake.
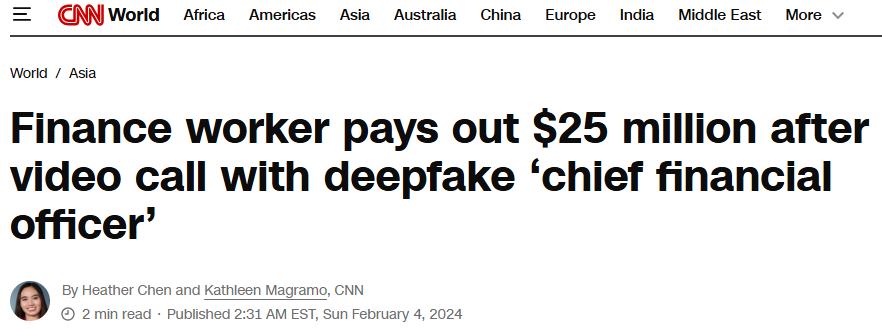
Source: CNN
Deepfakes are extremely convincing.
And research confirms the scale of the issue: in the U.S. and the UK alone, 53% of companies report being targeted by a deepfake-powered fraud, and 43% have fallen victim to it.
Even if only some attempts succeed, the losses are enormous.
Generative AI fraud is projected to reach $40 billion in the U.S. by 2027.
According to Ahmed Fessi, Chief Transformation and Information Officer at Medius, an AP automation provider, deepfake scams are on the rise.

Illustration: Veridion / Quote: CFO Dive
Defeating deepfakes requires layered safeguards.
First, raise awareness.
Ensure that finance and procurement staff understand that voice and video can now be fabricated and are aware of the proper protocols for verification.
Then, establish strict authentication protocols for any high-value or unusual request.
For example, require at least two people to sign off on large wire transfers. One person should never send money based on a single, possibly fraudulent, request.
Finally, follow experts’ advice: use multi-factor authentication for financial approvals, keep robust records of who approved what, and practice vigilance in communications.
By combining education, strict procedures, and technology, you can blunt the deepfake threat.
Vendor fraud comes in many guises.
A bogus invoice, a rigged bid, a phantom company, substituted goods, a spoofed email, or a deepfake video.
You can defeat these schemes by enforcing checks at each stage, from vetting vendors and matching invoices to multi-person approvals and real-time authentication.
Use tools like Veridion’s verified business database to confirm supplier identities, and keep everyone trained to question any unusual requests.
By staying vigilant and proactive, you protect your budget and build a culture of security in procurement.
You can spend confidently, knowing fraudsters are being shut out of your supply chain.