A Guide to Vendor Invoice Fraud

Key Takeaways:
Have you ever heard stories of people around you who lost a lot of money and assets in an unpredictable incident or a fraud case?
Every accounts payable manager has nightmares about this moment.
You are reviewing monthly payments when something catches your eye.
A wire transfer for hundreds of thousands of dollars has been sent to the wrong bank account, and the money went straight to a scammer.
This actually happened to the City of Hamilton in 2023, and they never recovered the money.
Vendor invoice fraud is more common than many organizations realize, and it can happen to anyone.
In this guide, we’ll break down what vendor invoice fraud is, highlight four common schemes that fraudsters use, and share actionable strategies to protect your organization from falling victim.
Vendor invoice fraud occurs when criminals manipulate or fabricate invoices to steal money from your organization.
Some impersonate real vendors that you already work with and trust. Others create completely fake vendor profiles that look authentic.
Many exploit weak internal controls to submit illegitimate payment requests that your team processes without realizing the danger.
What makes invoice fraud so dangerous is that it often looks completely legitimate.
Counterfeit invoices have proper branding and correct invoice numbers. The amounts seem reasonable and do not raise red flags.
And your accounts payable team processes hundreds of invoices every month, so a single fraudulent document can slip through without anyone noticing until it is too late.
Plus, with the rise of AI, it’s becoming more and more difficult to spot fraud.
According to the 2025 Phishing Threat Trends Report, 83% of phishing emails sent between September 2024 and February 2025 used AI.
This is up 54% compared to the year before.
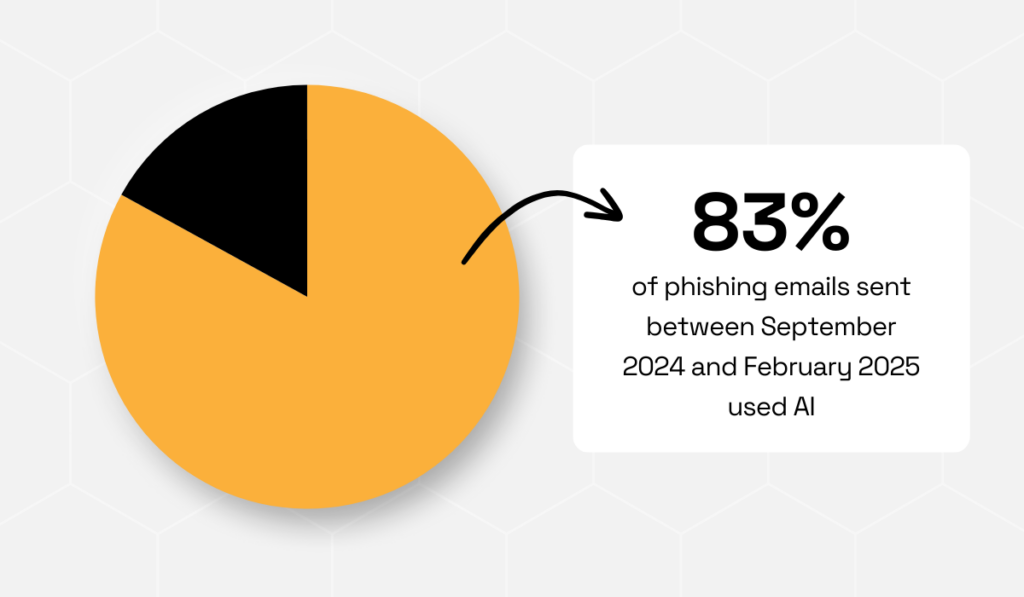
Illustration: Veridion / Data: KnowBe4
And the economic impact of invoice fraud is staggering.
According to a report by Medius, American companies lose about $300,000 annually to fake invoices.
Given this staggering figure, it’s not surprising that 98% of U.S. businesses worry about vendor fraud exposure.
But the worst part is that, by the time you discover the fraud, the money is usually gone forever.
But how do fraudsters pull this off so convincingly?
To protect your business, you need to know the most common invoice schemes and how they slip through even well-run AP processes.
Invoice fraud comes in many different forms, and each type targets specific weaknesses in your payment processes.
Understanding how these schemes work is your first line of defense.
After all, you cannot protect yourself against threats you do not recognize.
So, let’s explore the four most common types of invoice fraud that hit organizations today.
In business email compromise schemes, attackers impersonate a legitimate vendor by hacking into or spoofing their email address.
These attacks have become one of the most dangerous and costly types of fraud facing organisations today.
FBI’s Internet Crime Report for 2023 confirms this, showing that $2.9 billion was lost to BEC attacks during that calendar year.

Illustration: Veridion / Data: FBI
But why are BEC attacks so common? Because they look so real.
Imagine this scenario:
The attackers request urgent payment to a new bank account.
The emails use real-looking signatures that match your vendor’s communication style, and they include authentic company logos that you recognize.
The invoice formats mirror legitimate communications perfectly, so everything appears normal when your team reviews the request, right?
Well, these attacks succeed because they exploit the trust you have built with vendors over time.
When an email appears to come from a vendor you have worked with for years, your team naturally assumes it is legitimate and processes the payment quickly.
But attackers are becoming more and more sophisticated in their methods.
They went from changing one letter in a well-known vendor’s email address to completely compromising their email system.
When this happens, emails genuinely originate from the vendor’s servers, which makes detection virtually impossible.
Brian Honan, president of Dublin-based cybersecurity consultancy BH Consulting, provides a vivid example:
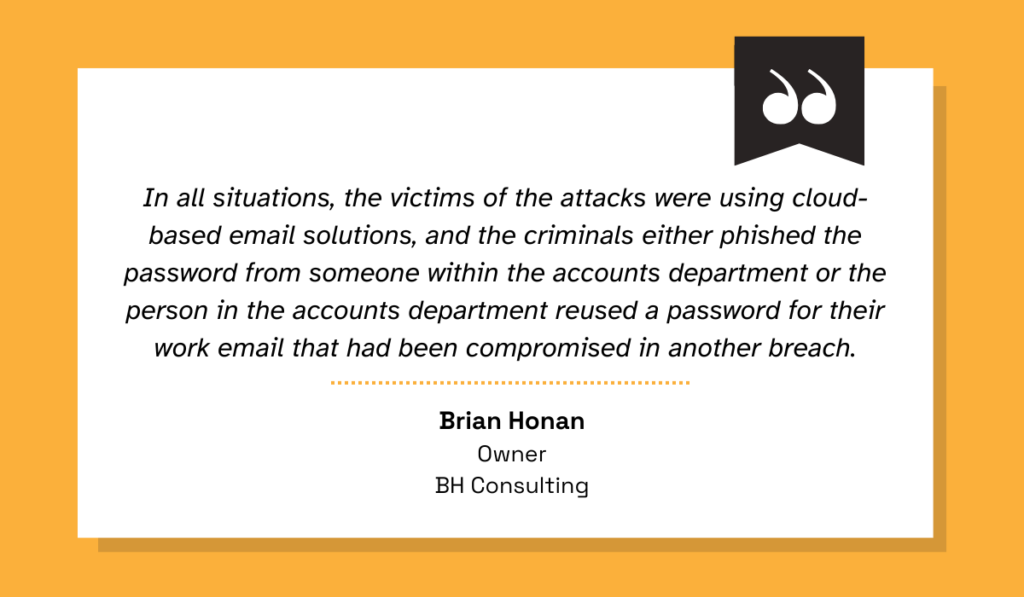
Illustration: Veridion / Quote: Bank Info Security
Not even tech giants are immune to sophisticated BEC attacks.
Between 2013 and 2015, a Lithuanian man orchestrated a massive BEC scheme targeting Google and Facebook.
He posed as an employee of Quanta Computer, a legitimate hardware supplier to both companies. He submitted carefully crafted fake invoices that looked completely authentic.
The scheme netted approximately $122 million before authorities caught him, making it one of the largest BEC frauds in history.
Fraudsters create entirely fake vendors or impersonate real ones to submit invoices for goods or services that were never actually delivered to your organization.
This type of fraud thrives when your vendor onboarding and verification processes are weak or nonexistent.
In other words, when you do not have strong controls in place to verify new vendors, fraudsters can easily slip into your system.
This is what happened to thousands of businesses that were victims of an office supply scam.

Source: FTC
A-1 Janitorial sent unsolicited invoices to businesses for products that were never ordered.
After researching their target companies, the criminals referenced specific employee names in the invoices.
This significantly increased the likelihood that someone would pay without questioning the request.
Those who paid the fraudulent invoices received more products and additional invoices, creating an ongoing fraud cycle.
The Federal Trade Commission eventually refunded more than $2.6 million to affected businesses through 30,374 checks averaging $86 each.
In more sophisticated operations, fraudsters create entire shell companies with official registrations.
They register business names similar to recognized vendors in your industry, so your busy accounts payable team approves these invoices without questioning them because the names look familiar.
With high volumes of invoices coming in daily, even the most diligent accounts payable teams can miss subtle red flags.
Manual checks are time-consuming and prone to human error, which is why technology plays a critical role in catching fraudulent activity before payments are processed.
Jim Lucier, CEO, Medius, explains:

Illustration: Veridion / Quote: PR Newswire
Ultimately, preventing vendor invoice fraud requires a combination of vigilance, strong internal controls, and the right technological tools.
By verifying vendors, monitoring invoice patterns, and leveraging automation to flag anomalies, organizations can dramatically reduce the risk of falling victim to these sophisticated scams.
Overbilling occurs when a vendor intentionally charges more than what was agreed upon in your contract or purchase order.
This sneaky type of fraud does not raise immediate red flags because you are actually receiving goods or services.
So, how does it work? Dishonest vendors inflate the quantities they claim to have delivered.
They raise prices without authorization from your team by adding hidden fees that were never part of the original contract terms.
Essentially, they bet that you will not notice the extra charges buried within legitimate transactions.
This scheme can involve dishonest vendors working alone or employees within your organization colluding with vendors to split the excess payments.
Organizations without granular spend visibility or proper contract tracking often miss these discrepancies completely.
A notorious example involved twin sisters who ran C&D Distributors LLC.
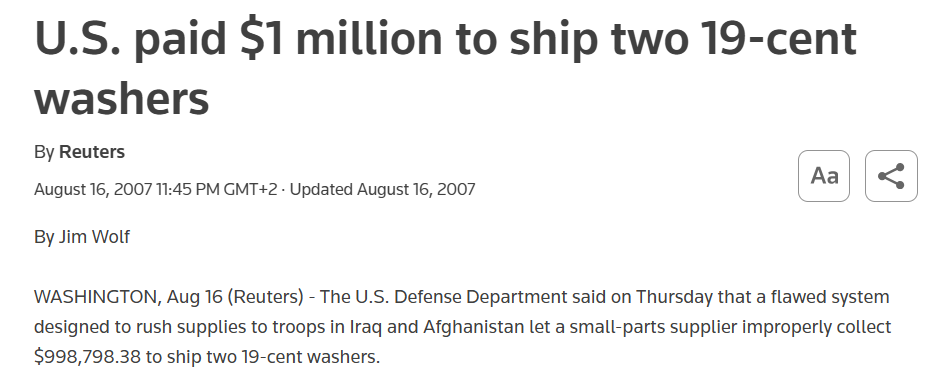
Source: Reuters
They realized they could alter their invoices to greatly inflate shipping costs and prices.
Small parts, such as washers and bolts that cost pennies, were invoiced to the U.S. Department of Defense for hundreds of thousands of dollars.
The DoD later admitted to automatically paying invoices to expedite shipments to troops in Iraq and Afghanistan.
By the time auditors caught the fraud, the sisters had fraudulently received more than $20.5 million.
As this example goes to show, overbilling drains budgets gradually and can persist for years, completely undetected.
The fraud often starts very small, with just a few extra dollars here and a slightly higher quantity there.
But it compounds over time into substantial losses that impact your bottom line.
Duplicate invoicing fraud involves submitting the same invoice multiple times, often with slight changes to invoice numbers, dates, or formatting to avoid detection by basic checking systems.
This can be intentional fraud by external parties seeking double payment or opportunistic exploitation of weak accounting controls.
Companies that rely heavily on manual invoice review are especially vulnerable to this type of scheme.
When your accounts payable teams process hundreds of invoices weekly without automated matching systems, duplicate payments can slip through completely unnoticed.
First Brands, a major auto parts supplier, learned this lesson during its Chapter 11 bankruptcy proceedings.

Source: Bloomberg
Investigators alleged that the company had sold some receivables more than once through invoice factoring, meaning the same invoices were effectively pledged to multiple financial institutions.
According to court filings, payments that should have gone to factoring partners were instead retained internally.
This resulted in a high-stakes duplicate invoicing scheme with millions of dollars at stake.
Without automated three-way matching systems, duplicate payments can just keep accumulating over time.
But by strengthening controls and implementing automated matching tools, organizations can sharply reduce the risk of duplicate payments slipping through the cracks.
Preventing invoice fraud requires multiple layers of defense working together.
You need to combine technology solutions with improved internal processes and vigilant human oversight.
No single solution will eliminate all fraud risk, but implementing these three essential strategies together will significantly reduce your vulnerability and protect your financial assets.
First and foremost, organizations need to verify that all their vendors are genuine and licensed before making any payments to them.
This is a basic measure that will avoid a host of invoice frauds ever having an opportunity to enter your payment systems in the first place.
So, what information do you actually need to confirm?
Start with the basics, such as the name of the business, physical address, tax identification number, and banking details.
The key is to verify them using credible and independent sources, instead of blindly relying on the information presented in the invoice itself or in email exchanges.
Katy Worobec, Senior Fraud Consultant for Azymus Consilium Fraud Consultancy, agrees.

Illustration: Veridion / Quote: RBS
Vendor verification should occur when initially onboarding a new vendor.
In the case of existing vendors, it is important to re-verify the vendors frequently, particularly when they request to change their payment information.
But doing all of this manually can be extremely time-consuming for your already busy payments teams.
That is where tools like Veridion come in.
Veridion’s Match and Enrich API automates and strengthens this entire verification process.
The API compares the vendor information you have against a continually updated global database covering more than 134 million suppliers with over 220 data points for each one.
It detects wrong registration details, concealed ownership connections that could indicate shell companies, and warning signs that manual verification would miss.
Source: Veridion on YouTube
The system processes patterns across large data volumes updated weekly, identifying anomalies in business registration, ownership structures, operations, or financial status quickly.
This acts as a preventive measure that stops fraud before you make any payments.
Payment instructions should never be verified through a single channel, especially not through email alone.
Why?
Because this creates a critical vulnerability that fraudsters actively exploit in BEC schemes.
When you receive any request to change vendor accounts or payment details, always confirm the change through alternative methods before processing it.
Use verified phone numbers from your existing vendor records, not numbers provided in the email request itself.
Dr. Matthew Grosse, Senior Lecturer in Accounting at UTS Business School, advises:

Illustration: Veridion / Quote: CPA Australia
On top of that, you can use secure vendor portals that require proper authentication.
This verification principle applies even to vendors you have trusted and worked with for many years.
Long-standing relationships do not make you immune to fraud because vendor email systems can be compromised without your knowledge.
The City of Hamilton learned this lesson the expensive way.

Source: The Public Record
Had employees simply verified the banking change requests through a phone call to the vendor’s established number in their records, they would have discovered the fraud immediately and prevented the entire $274,000 loss.
Multi-channel payment verification may seem cumbersome or potentially slow payment processing by a day or two.
But it is far less costly than trying to recover from a six-figure fraud loss or explaining to leadership why basic verification was not performed.
Legitimate vendors understand security measures and prefer a brief verification call over dealing with payment issues when fraud strikes.
Frame these protocols as protecting both your organization and your vendors from financial crime.
Invoice fraud often targets finance teams directly, but anyone in operations, procurement, management, or even executive leadership can become a victim.
Fraudsters do not discriminate when looking for weak points to exploit in your organization.
According to research from Abnormal AI, employees frequently struggle to differentiate between legitimate messages and sophisticated attacks, especially when emails appear to come from known vendors with familiar branding.
In large enterprises with 50,000 or more employees, 72.34% of workers who read a vendor email compromise message engaged with it further by replying, forwarding it, or both.
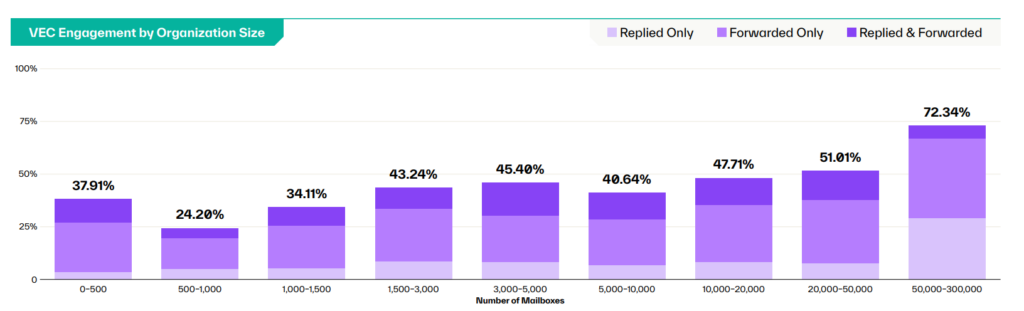
Source: Abnormal AI
But why is this such a common occurrence?
Mick Leach, field CISO of Abnormal AI, elaborates:
“Larger organizations can struggle, to some extent, with context, understanding who works with this person. You receive a message, you go, ‘Oh, I, I don’t handle these, but Marjorie, over in finance, does let me just send this over to her.’ The fact that it’s now being forwarded from a colleague, and you see someone that you typically do business with and a company you do business with, further escalates the engagement rate of those attacks because now it’s doubly coming from a trusted source.”
Forwarding suspicious emails to the right person without flagging concerns actually amplifies the fraud’s credibility, rather than protecting against it.
Extensive training is supposed to assist the employees in every department in identifying important warning signs.
So, take the time to educate the staff on how to be suspicious about ambiguous or desperate-sounding invoice notices that compel them to take action without explaining the reasons.
Suspect any communications that seek to alter payment information, most especially when it comes through email.
In addition to educating employees to understand the red flags, instill a culture in which employees are sincerely encouraged to ask questions when they receive suspicious directives without the fear of being targeted.
It is necessary to make it very clear that the additional time needed to confirm suspicious invoices is not only welcome but also preferred by management.
Vendor invoice fraud threatens every organization regardless of size or industry, but most schemes are preventable with the right defenses.
By verifying vendor identities through reliable data sources, implementing multi-channel verification for payment changes, and empowering employees to recognize and report suspicious activity, you significantly reduce your exposure to these costly schemes.
The difference between a close call and a catastrophic financial loss lies in the systems you implement today.
Do not wait for fraud to strike before building your defenses.