5 Financial Consequences of Ignoring Third-Party Risks


Key Takeaways:
Many companies skip third-party risk management (TPRM) because it seems expensive or unnecessary.
The problem is that ignoring it often incurs far greater costs in the long run, through breach remediation, fines, downtime, and lost revenue.
Third-party risks may be invisible until they strike, but their financial consequences are very real.
We’ll share data and real-world examples that illustrate this and show why proactive risk management is essential. Let’s dive in!
Third-party security failures are one of the main reasons companies suffer data breaches.
This usually happens when vendors have access to sensitive systems and data but lack sufficient security measures.
And this is more common than you might think.
In fact, according to IBM’s Cost of a Data Breach Report 2025, attacks through vendors or supply chains are the second most common way companies get breached.
To make matters worse, such attacks also take the longest to resolve.
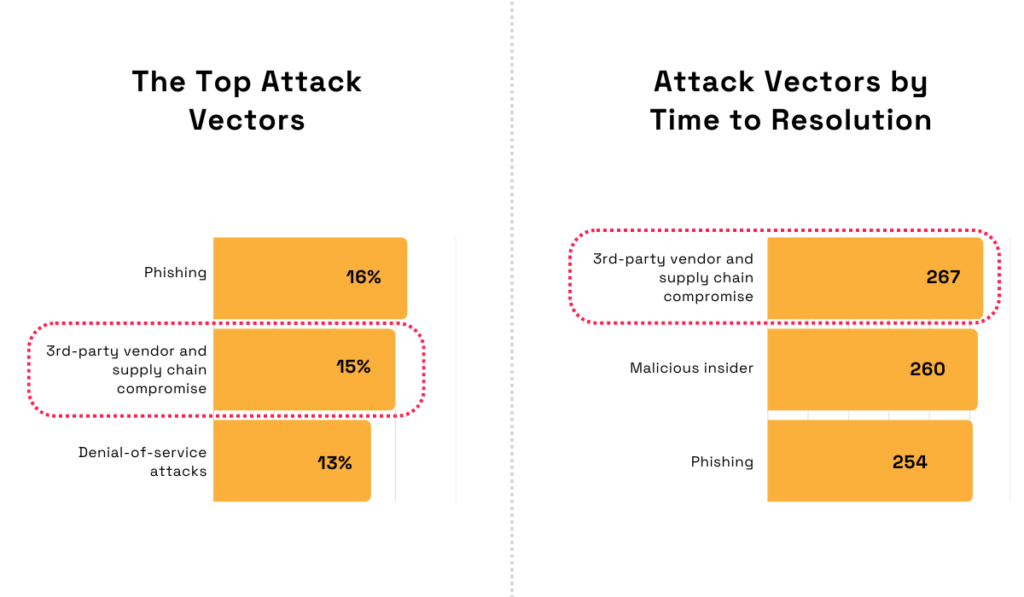
Illustration: Veridion / Data: IBM
The report explains that the reason this type of data breach drags on is that it’s the hardest to detect.
It’s more difficult to identify a breach that exploits vendor-to-customer communications than one that happens entirely inside a company’s network.
To be more precise, detecting it alone takes an average of 196 days.
This gives malicious actors ample time to achieve their objectives, whether that includes stealing customer data, exfiltrating intellectual property, or manipulating financial records.
And the financial fallout of such months-long, undetected access is substantial.
So, it shouldn’t surprise us that breaches caused by third parties are the second most costly type of incidents, surpassed only by insider attacks.
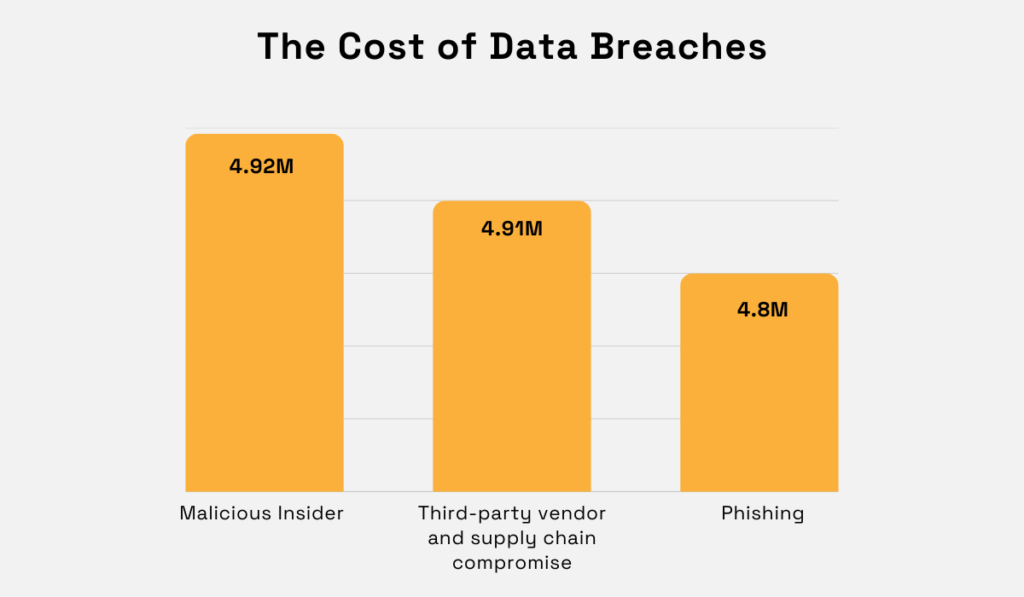
Illustration: Veridion / Data: IBM
It’s worth noting that the costs go beyond just fixing the immediate problem.
Companies also often have to cover things like notifying customers, running forensic investigations, dealing with long-term customer loss, legal fees, and sometimes even lawsuits.
A recent example of this comes from AT&T, a major telecommunications company.
In 2023, one of their cloud vendors was hacked, which led to a third-party data breach impacting nearly 9 million AT&T wireless customers.
A subsequent investigation found that the telecommunications company not only failed to adequately protect customer data but also to delete it on time.
In fact, Reuters reported that the exposed data should have been deleted by 2018.

Source: Reuters
Eventually, as the headline above reveals, AT&T paid a staggering $13 million just to resolve the investigation.
This doesn’t include additional expenses like operational downtime or reputational damage, which we’ll get to in a minute.
So, even though the incident originated with a vendor, and not AT&T itself, the data breach ended up being very costly for the company.
The same fate can befall any organization that doesn’t take appropriate TPRM measures.
Organizations can incur penalties when their vendors mishandle personal or regulated data, even if they’re not directly at fault.
This is because many regulations, such as GDPR, HIPAA, and others, impose joint liability on businesses and their third parties.
Let’s take GDPR as an example.
According to Sara Pegarella, Legal Editor at TermsFeed, an online platform that generates customizable legal agreements, so-called joint controllers are always “jointly and severally liable for GDPR violations.”
In translation, all parties that have a say in the purposes and means of data processing can be held liable for any violations of the GDPR.

Illustration: Veridion / Quote: TermsFeed
So, if you and your vendors are joint controllers, you could be held liable for data breaches caused by both their actions and inaction.
To illustrate this, Pegarella uses an example many might overlook: business owners using a social media platform like Facebook for marketing.
In this case, a business owner and Facebook are considered joint controllers.
Although there’s no direct relationship in this example, both parties influence how the data is used and are therefore both responsible and can be fined for data breaches.
Such potential repercussions are not exclusive to the GDPR.
Even if we take another regulation, like CCPA, it’s clear they could be significant.
For instance, intentional CCPA violations can incur penalties up to $7,500 per incident. Unintentional ones can reach $2,500 per violation.
Multiply that by thousands of records, and a single vendor mistake can trigger seven-figure enforcement actions.
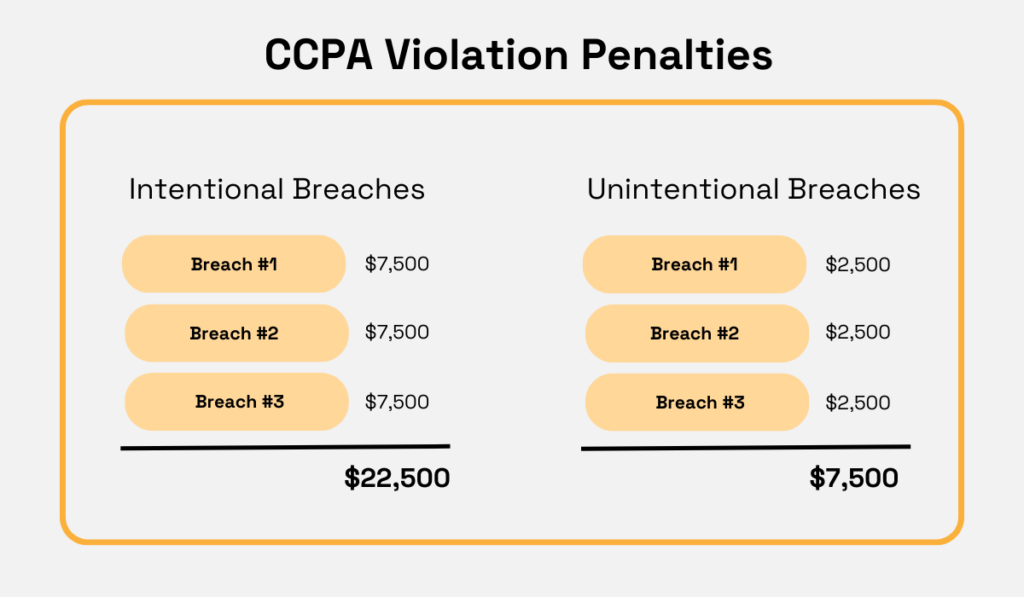
Illustration: Veridion / Data: Sprinto
So, the fines can be quite steep. But, even if they weren’t, they would still be entirely avoidable.
If you ask us, that means even a single dollar paid for fines is one dollar too many.
And as if that wasn’t enough, the financial woes usually don’t stop there.
Data breaches and regulatory penalties are often followed by at least partial operational downtimes, which further result in lost revenue.
As noted, when data breaches occur, companies can be forced to temporarily shut down critical activities.
But other third-party risks can also grind operations to a halt, such as vendor outages, cyberattacks, and missed service delivery.
Amazon’s 2025 bug-caused outage is the perfect example of this.
This outage, which “affected thousands of companies and millions of people,” is estimated to have cost Amazon’s customers an eye-watering $581 million.
Mind you, it lasted just over 15 hours.
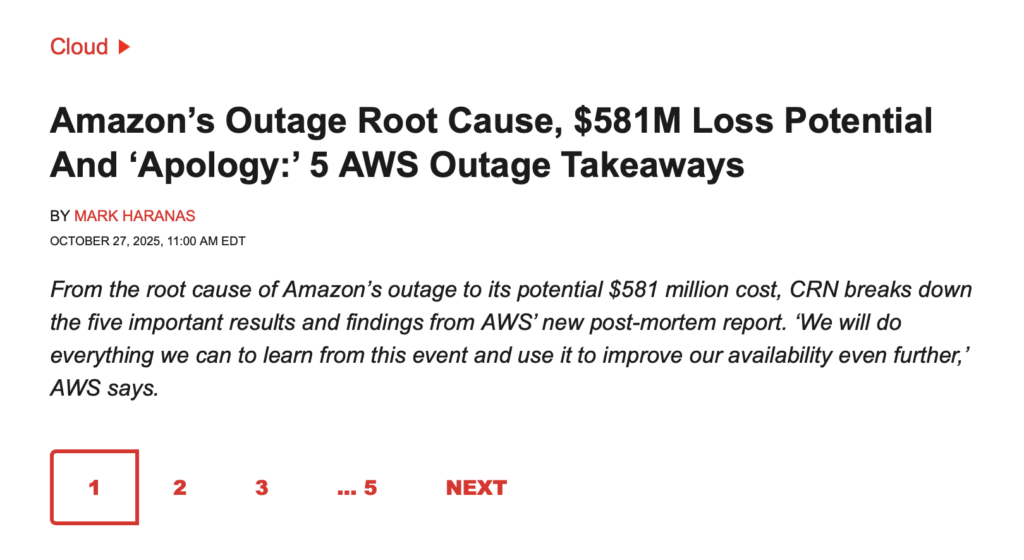
Source: CRN
Despite being relatively short, the outage caused widespread disruption, leaving numerous global companies affected.
Snapchat users could not send snaps, Ring smart cameras failed to deliver alerts, and Delta Airlines reportedly experienced stalled check-ins.
The fallout was even worse for financial services customers.
For instance, crypto platforms like Coinbase, Robinhood, and Trust Wallet reportedly went offline. Customers were not even able to log in, let alone execute trades.
Source: ForkLog
This goes to show that even brief downtime can be crippling.
Beyond just losing productivity or missing new revenue, affected companies may also face SLA penalties or service credits, as well as remediation costs.
All of this can quickly compound into significant financial and operational impacts.
In ITIC’s 2022 Global Server Hardware Security survey, for example, 44% of mid-sized and large enterprises said that just one hour of downtime can cost them more than $1 million.
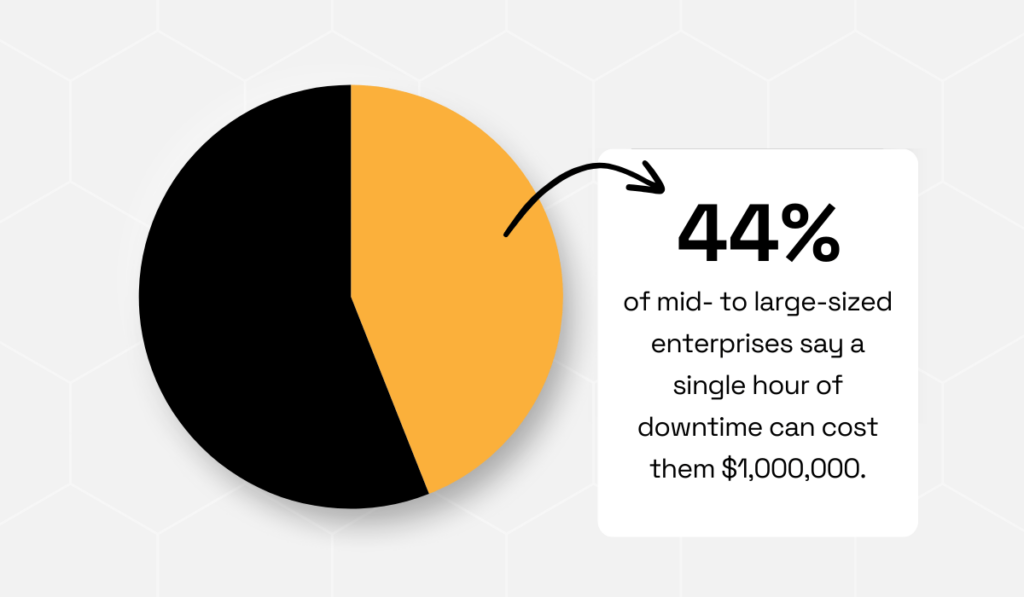
Illustration: Veridion / Data: ITIC
So, what’s the solution to this issue?
Three words: vendor risk management.
Proper vendor oversight is crucial for business continuity. There’s just no getting around it.
More specifically, if companies want to prevent single points of failure, they should consider implementing best vendor management practices.
This could include monitoring service-level guarantees, establishing geographic redundancy, and creating recovery plans together with third parties.
That would prevent not just direct financial losses, but reputational damage, too.
Beyond immediate losses, third-party risks can also damage your reputation and trigger long-term financial consequences.
And yes, that is correct: your reputation is at stake even if it’s your vendor’s security that failed, and not yours.
The public might still hold you accountable, especially if you’re the brand they interact with.
Perimeter illustrates this with a perfect example: a 2024 incident often described as “the Comcast data breach.”
Despite what media coverage might have you believe, it actually wasn’t Comcast directly that suffered a data breach. It was the company’s debt collection vendor, FBCS.
Nonetheless, this attack affected approximately 270,000 of Comcast’s users, which caused the media to focus more on Comcast than on the vendor in question.
Source: Enterprise Management 360
This illustrates a critical point.
When a security incident hits, public scrutiny typically falls on the company serving the affected customers, regardless of who actually caused it.
And, of course, the consequences don’t stop there.
Reputational damage often leads to more tangible business repercussions, like clients churning, deals falling through, and pipelines slowing down.
This pattern is nothing new.
Target, for example, experienced it firsthand all the way back in 2013.
After the company suffered a data breach, sales dropped 4%, profits plunged nearly 50% the following quarter, and the CEO was ultimately dismissed.
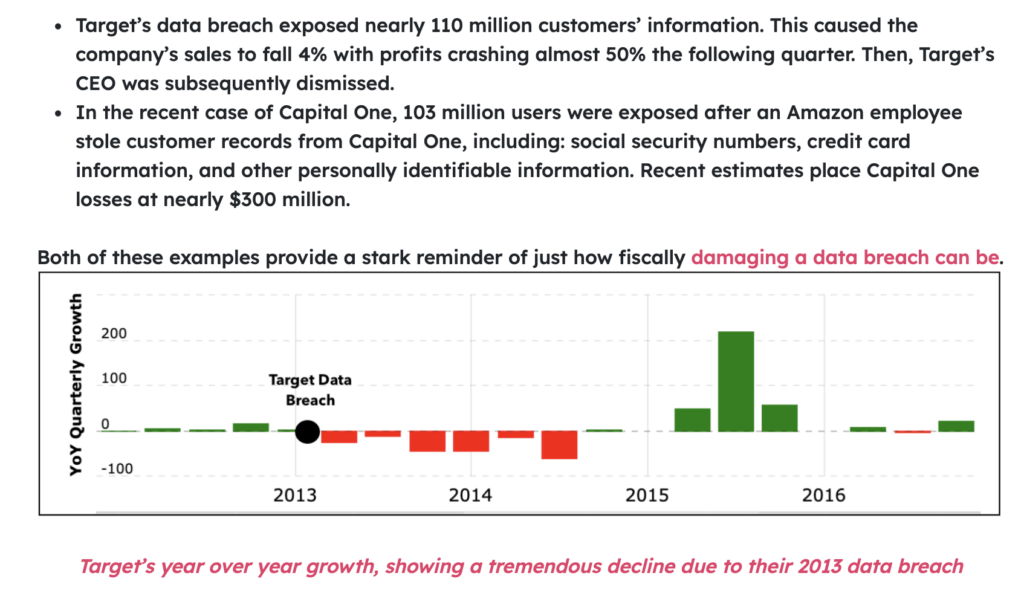
Source: CybelAngel
So, while reputational harm might be harder to quantify, it can still be far more costly than direct incident expenses.
It’s the compounding effect that matters.
But let us just briefly mention that bad press can often further lead to costly litigation processes.
Once the dominoes start falling, it’s difficult to stop them.
News today spreads like wildfire across news sites and social media, and public outrage can quickly turn into lawsuits.
And, according to Peter Selvin, a Partner at ECJ’s Litigation Department, data breach lawsuits usually involve both the vendor and the affected company.

Illustration: Veridion / Quote: Mondaq
So don’t think it’s just your reputation taking a momentary hit.
Negative publicity can have drastic and very real financial consequences, both in the short term and the long run.
Finally, we shouldn’t overlook the high costs of cleaning up after a third-party incident.
Although IBM’s study showed that they have somewhat declined in 2025 compared to 2024, they are still significant, especially for third-party compromises.
The reason is that, according to the same study, breaches with longer lifecycles have higher costs. And we already saw that third-party breaches take the longest to resolve.
267 days, to be precise.
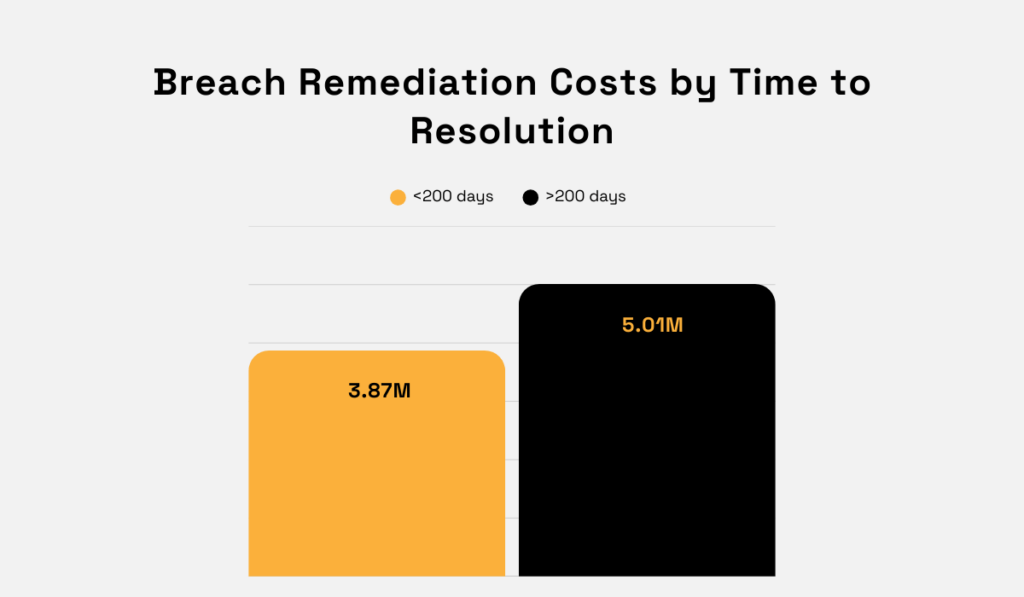
Illustration: Veridion / Data: IBM
So, by time-to-resolution alone, third-party compromises are among the most expensive ones to resolve.
Yusuf Purna, Chief Cyber Risk Officer at MTI, a Japanese technology company focused on mobile services, helps explain why.
He says that remediating third-party incidents requires extensive coordination and communication between multiple organizations.
For instance, before containment can even begin, companies must first determine what the vendor had access to and precisely what occurred.
This process by itself often takes significant time and effort.

Illustration: Veridion / Quote: LinkedIn
Of course, on top of that, companies still need to apply all the usual remediation techniques, including system restoration, crisis PR, compliance audits, and security overhauls.
The aftermath often requires months of internal resources, external consultants, and technical improvements, all of which further drive down your revenue and increase costs.
This is especially counterproductive considering that remediation expenses often exceed the cost of proactive third-party risk management (TPRM).
As Vendminder’s 2023 whitepaper explains, avoiding even a single vendor breach through TPRM could literally save you millions of dollars.

Illustration: Veridion / Quote: Venminder
With that in mind, it’s hard not to see the benefits of proactive over reactive risk management.
Let’s assume you now realize that third-party risks are best managed upfront. Your company should aim to prevent them rather than deal with them after they happen.
So, to do that, where should you start?
Well, the first step is getting accurate data on your vendors. Today, the best way to do this is by using external, unbiased data providers such as Veridion.

Source: Veridion
Veridion provides continuously updated, high-accuracy data on vendor identity, business operations, and risk-related attributes.
That data gets updated weekly based on changes detected in various sources, from company websites to news outlets.
This helps organizations detect risky or non-legitimate third parties early and ensures key information doesn’t slip through the cracks.
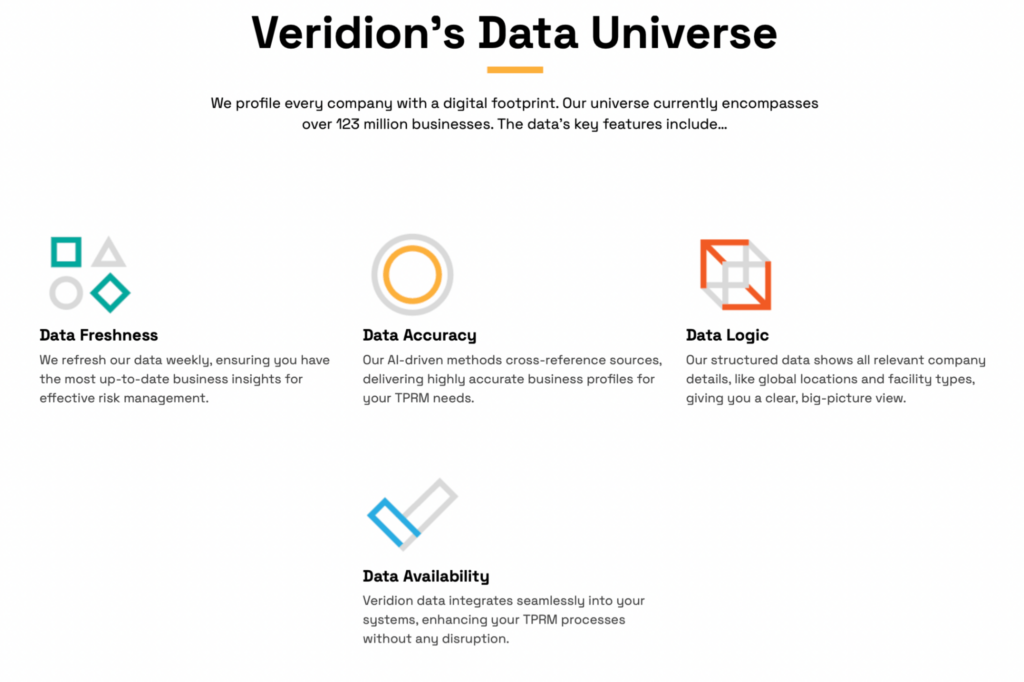
Source: Veridion
But beyond just helping you stay on top of existing vendors, Veridion also enables you to make better choices from the start.
With Veridion’s Scout, you can uncover dozens of verified vendor details using natural language.
That way, you can select reputable, safe partners from the get-go and minimize your exposure to fraud, compliance violations, and operational disruptions.
Source: Veridion
Even if you already have some internal vendor data, Veridion can help both verify and enrich it to ensure you’re working with complete and accurate vendor profiles.
This is key to avoiding costly mistakes, such as underestimating vendor risk and failing to take timely action.
The bottom line is this: if your goal is to protect your organization with proactive risk management, complete and accurate vendor data is a non-negotiable foundation.
Few solutions can match Veridion in providing it.
Third-party risks are not just a security concern but carry serious financial consequences.
We saw how high remediation costs, regulatory fines, operational downtime, and lost business opportunities all add up to substantial losses for organizations.
Additionally, we saw that companies that underestimate these risks often spend far more reacting to incidents than they would preventing them.
The key takeaway is clear: understanding and managing third-party risk protects revenue and long-term finances.
So, start today. You got this!