7 Sources of Data for Third Party Risk Management


Key Takeaways:
Third-party data breaches are becoming an unavoidable reality for organizations that rely on external vendors.
Every time you bring on a new vendor, you’re opening a potential door for attackers.
Cloud providers, payment processors, and software companies all become part of your attack surface.
The uncomfortable truth?
You can’t just take their word for it when they say they are secure.
Sure, their questionnaires might look impressive. Their certifications seem solid.
But what’s really happening behind all that?
To protect your business, you need data from multiple sources that show you the full picture of vendor risk.
So, let’s explore seven key data sources you should consider.
The first place to look for vendor risk information is inside your own organization.
Your teams interact with vendors every day.
Procurement negotiates contracts, IT manages system access, and the operations team tracks delivery performance.
All these interactions create a paper trail that reveals how vendors actually behave.
That historical track record becomes a reliable indicator of future performance.
Let’s analyze these internal data sources in more detail.
When you bring a new vendor into your ecosystem, the onboarding process generates your first formal risk assessment.
You collect business registration documents, ownership disclosures, insurance certificates, and security certifications.
They fill out your risk questionnaire, listing their controls and compliance status.
This documentation creates your initial baseline.
You learn details such as:
But there’s one fundamental problem with onboarding data.
It captures a snapshot in time that starts aging the moment you receive it.
Six months later, that vendor’s ISO certification might have expired.
Their financial situation could have deteriorated. Or they might have been acquired, changing their ownership structure entirely.
Yet, your onboarding records still show that they’re ISO compliant, financially stable, and independently owned.
The solution?
Start treating onboarding documentation as a living baseline.
Scott McCowan, EY Americas Risk Management Leader, is in favor of continuous monitoring:

Illustration: Veridion / Quote: EY
So, set automatic reminders to refresh vendor information in regular intervals or whenever contracts change.
This approach keeps risk assessments current instead of letting you rely on outdated artifacts.
Your vendor contracts do more than define what you’re buying. They establish the legal boundaries of risk between your organization and theirs.
Every contract spells out performance expectations, data protection requirements, liability limits, and what happens when things go wrong.
These terms determine what recourse you have when a vendor fails, for instance:
The liability cap is where many organizations discover they’re not actually protected.
John Nicholson, counsel for the global sourcing practice at the law firm of Pillsbury Winthrop Shaw Pittman LLP, explains what a third-party vendor might do:

Illustration: Veridion / Quote: Dark Reading
He elaborates that this lands you in a situation where you’re the one paying for the rest.
For instance, your contract might limit the vendor’s liability to one quarter of annual service fees.
Sounds reasonable until you face a breach that exposes customer data and costs you millions in regulatory fines, legal fees, and remediation.
If your vendor’s maximum liability is $50,000 but your actual losses exceed $5 million, you’re absorbing nearly all the damage yourself.
Service level agreements create similar exposure when they lack teeth.
Consider an e-commerce company whose payment processing vendor goes down for 12 hours during Black Friday weekend.
The outage costs, say, $2 million in lost sales.
But the SLA just promises 99% uptime with service credits as the only remedy.
The vendor issues a $500 credit and apologizes. That doesn’t come close to covering the actual business impact.
Smart SLA contracts include more than just service promises:
You also need to review contracts regularly as relationships evolve and understand that not all third parties need the same level of risk management.
Yet, according to a 2023 Navex Global survey, 27% of organizations do just that, regardless of their vendors’ actual risk level.
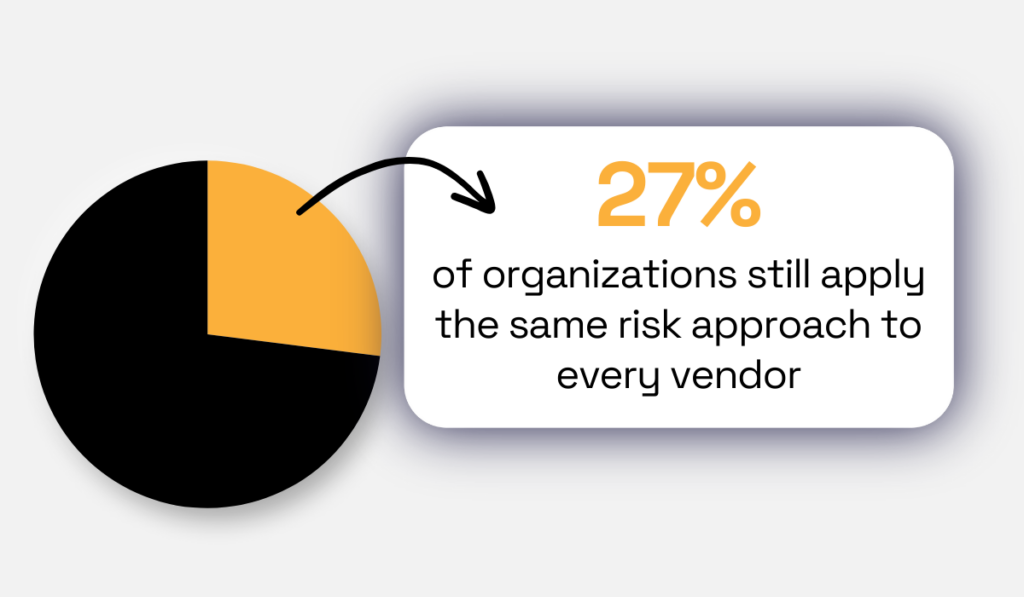
Illustration: Veridion / Data: Navex
This highlights how weak liability caps and ineffective SLAs leave organizations absorbing most of the damage when vendors fail, while contractual remedies fall far short of real-world losses.
Contracts and SLAs must therefore be treated as active risk management tools, with enforceable controls, ongoing oversight, and clear exit options as vendor risk evolves.
Most importantly, organizations need to apply proportional risk management rather than relying on generic, checkbox-style approaches.
Without this shift, vendor relationships can quietly become one of the largest and least controlled sources of enterprise risk.
Vendor incident reports reveal something that no questionnaire can capture.
They show how vendors actually perform when systems fail, when attackers strike, or when operations break down under pressure.
Your incident tracking system should capture every vendor-related disruption.
For each incident, document what happened, when it occurred, how severe the impact was, how quickly the vendor detected it, and how effectively they resolved it.
Equally important, pay attention to how the vendor is addressing the issue and preventing it from recurring.
Matt Klein, COO of SideChannel, a company that identifies, develops, and deploys cybersecurity and privacy risk management solutions, notes:

Illustration: Veridion / Quote: Cybersecurity Dive
This highlights that incident reports aren’t just data.
In reality, they show how vendors respond under real pressure and whether they take accountability for fixing systemic problems.
But the real value comes from pattern recognition.
When you see the same vendor experiencing repeated service disruptions during high-traffic periods, you’re looking at a capacity planning problem that won’t fix itself.
A pattern like that should trigger risk rating changes.
For instance, a vendor classified as low-risk during onboarding who suffers three security incidents in six months needs immediate reclassification and enhanced monitoring.
Their actual performance has revealed risks that weren’t visible in their initial assessment.
By tracking trends across incidents, you gain a forward-looking view of vendor reliability and security posture.
Building robust incident reporting processes now creates the audit trail you’ll need to demonstrate due diligence later.
Internal data tells you about your direct experience with vendors.
External data sources, on the other hand, tell you what’s happening beyond that
They provide independent verification of vendor claims and reveal risks vendors might want to keep under wraps.
This independent verification becomes critical when vendors have access to sensitive systems or data.
Business Data Platforms
Business data platforms aggregate information from hundreds of sources to create comprehensive vendor profiles.
They pull data from corporate registries, financial filings, regulatory databases, news feeds, and research networks.
Veridion is an example of one such platform.
It is a data-as-a-service provider that uses AI to aggregate and enrich global business data.
The platform delivers verified firmographics, ownership structures, operational details, financial signals, ESG indicators, and corporate linkages across millions of companies globally.
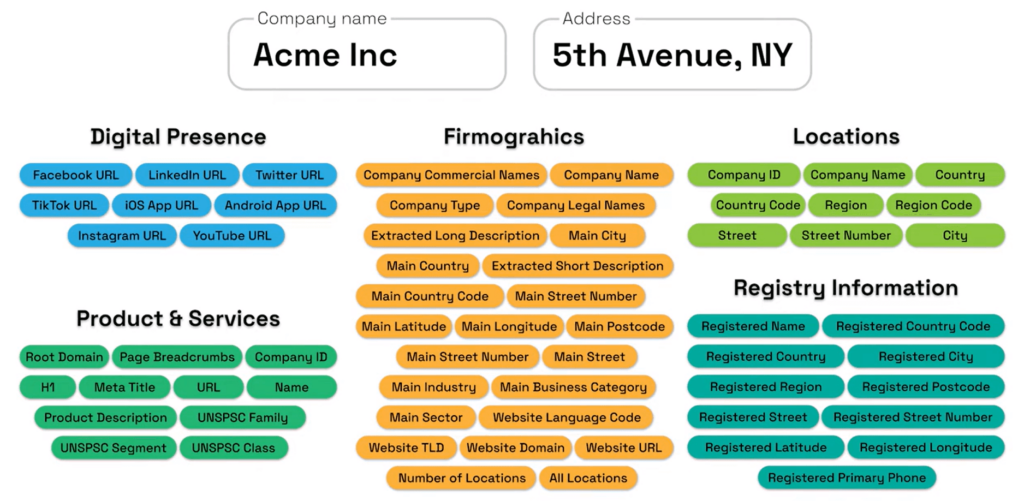
Source: Veridion
But the real power comes from cross-referencing vendor claims against independent data.
Let’s say a vendor informs you they operate a single facility in the United States.
Business data platforms might reveal a complex corporate structure with parent companies in offshore jurisdictions.
Or that a property listed by the vendor as a warehouse is, in fact, a storage and logistics facility.
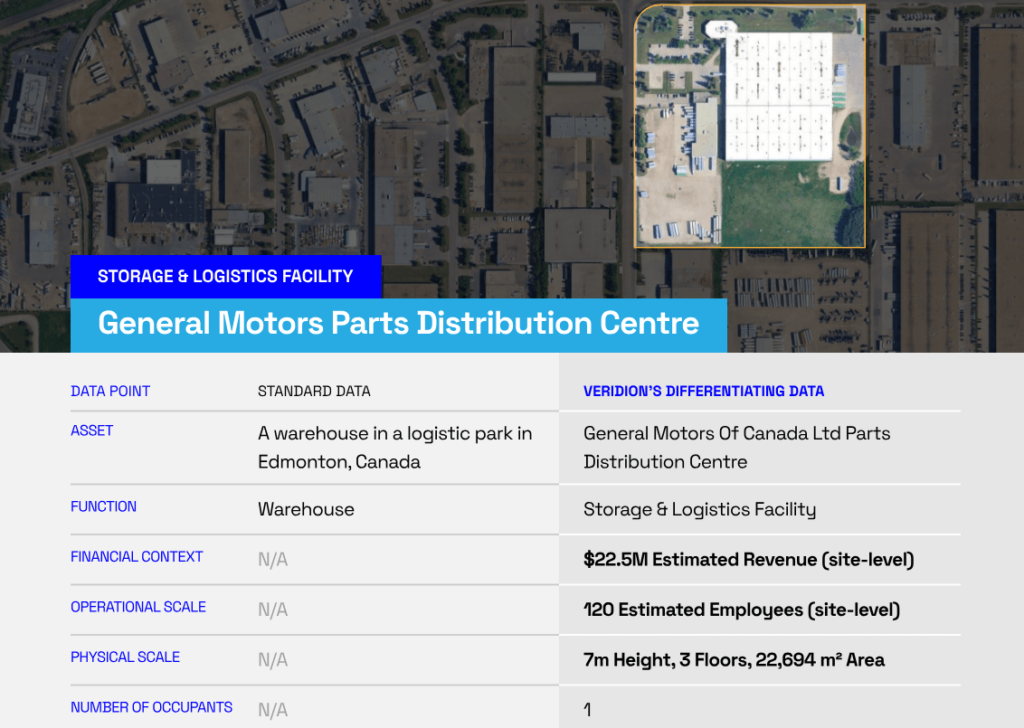
Source: Veridion
That kind of discrepancy signals hidden risk worth investigating, and business intelligence platforms make that task easier.
By highlighting discrepancies and giving a clear view of a vendor’s operations, business data platforms help organizations spot hidden risks early.
They turn scattered information into useful insights, making it easier to manage vendors effectively.
In short, these platforms make vendor risk visible and easier to control.
Financial stability directly impacts vendor reliability.
When suppliers struggle financially, quality suffers, deliveries get delayed, and companies become vulnerable to insolvency.
A 2023 Deloitte survey found that 72% of CFOs identified supply chain issues as a top business risk.
Many of those issues trace back to supplier financial distress that organizations failed to identify early enough.
That is where credit data providers like Dun & Bradstreet, Experian, and Moody’s Analytics come in, translating complex financial information into risk scores.
They track credit ratings, payment behavior, debt levels, liquidity ratios, and bankruptcy filings.
Before diving into the details, it’s helpful to see how D&B Finance Analytics organizes its capabilities to manage risk, streamline operations, and optimize cash flow across credit and receivables functions.
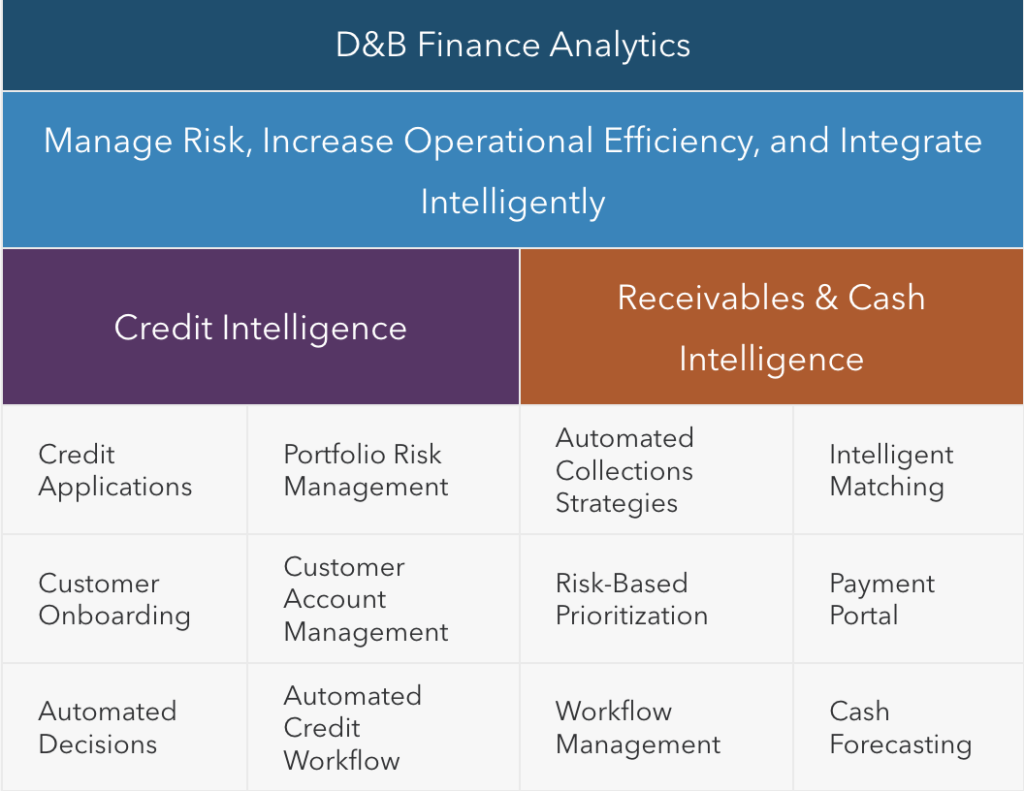
Source: D&B Finance Analytics
This visibility enables proactive risk management.
When you spot declining revenues or late payments to other suppliers, you can act before vendor failure disrupts operations.
That might mean negotiating better terms, requiring performance bonds, or beginning the search for replacements.
Coca-Cola demonstrates this approach using credit research from Moody’s Analytics to continuously monitor supplier health.

Source: Coca-Cola
This ongoing assessment enables proactive programs rather than reactive crisis response.
Setting financial health thresholds in vendor qualification creates clear decision points.
When vendors fall below these marks, you implement additional oversight, require letters of credit, or begin contingency planning.
Cyber risk platforms continuously monitor vendors’ external digital footprints for security vulnerabilities.
They assess exposed infrastructure, patching cadence, SSL certificate status, DNS configuration, and breach history.
Given that third-party cyber incidents can quickly escalate into regulatory investigations and reputational damage that extends beyond the breached vendor, these platforms are exceptionally important.
The Change Healthcare breach in February 2024 illustrates this point well.
Attackers exploited weak access controls in third-party vendor systems and compromised 145 million records containing patient names, Social Security numbers, and medical information.
The breach disrupted healthcare systems, patients couldn’t access medical records, and hospitals faced delays in processing insurance claims.
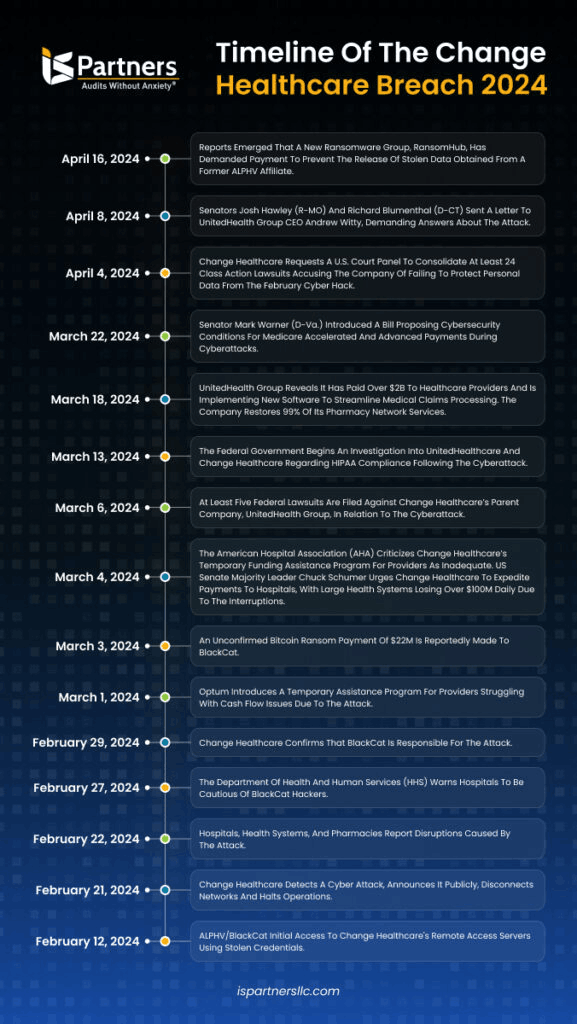
Source: I.S. Partners
As a result, Change Healthcare faced regulatory investigations and lawsuits.
But the reputational damage extended to every healthcare provider that relied on their services.
Each faced questions from patients about data protection.
The incident demonstrated how a single vendor’s security failure creates compliance violations and trust erosion throughout an entire industry.
Continuous monitoring platforms like BitSight, SecurityScorecard, and UpGuard scan vendor networks constantly.
Their risk scores update in real time, showing which vendors pose the greatest threats.
Given that, according to research, supply chain cyber incidents surged 431% between 2021 and 2023, utilizing cyber risk intelligence tools is now more important than ever.
This increase has elevated third-party cyber risk from an IT concern to a strategic board priority.
Setting cyber risk thresholds gives you clear action points when vendor security ratings drop below acceptable levels.
Effective third-party risk management requires data from multiple sources working together.
Your internal sources provide the track record of actual vendor performance.
External sources validate that information and reveal risks vendors won’t disclose.
The most successful organizations layer internal and external data sources to build a complete picture.
So, start by strengthening your internal data collection for onboarding, contracts, and incidents.
Then add external validation through business intelligence platforms, financial monitoring, cyber risk assessment, and compliance screening.
The benefits of third-party risk management become tangible when you make decisions based on verified data rather than vendor promises alone.