Apache Log4j – Can the 8 million companies affected by this massive vulnerability impact your supply chain?


We love our data, and now that you're here, you're one step closer to loving it too.
A wide sample of data, so you can explore what is possible with our data
Choose ->
built with procurement in mind. Focused on manufacturers, products and more
Choose ->
built with insurance in mind. Focused on classifications, business activity tags and more
Choose ->
built with sustainability in mind. Focused on sustainability commitments, and environmental and social governance insights.
Choose ->
built with strategic insights in mind. Focused on market trends, competitor analysis, and industry-specific data
Choose ->
A wide sample of data, so you can explore what is possible with our data
A wide sample of data, so you can explore what is possible with our data
built with procurement in mind. Focused on manufacturers, products and more
built with insurance in mind. Focused on classifications, business activity tags and more
A wide sample of data, so you can explore what is possible with our data
built with procurement in mind. Focused on manufacturers, products and more
built with insurance in mind. Focused on classifications, business activity tags and more
built with sustainability in mind. Focused on sustainability commitments, and environmental and social governance insights.
built with strategic insights in mind. Focused on market trends, competitor analysis, and industry-specific data

Keep up to date with our technology, what our clients are doing and get interesting monthly market insights.


According to The Indian Express “the Log4j vulnerability–first reported on Friday– is turning out to be a cybersecurity nightmare that likely impacts a wide range of products from Apple’s iCloud to Twitter to Microsoft’ Minecraft and a number of other enterprise products.”
The scope of the issue is huge
In a phone call with CNN, Jen Easterly, director of the US Cybersecurity and Infrastructure Security Agency (CISA), said this week:
“This vulnerability is one of the most serious that I’ve seen in my entire career, if not the most serious.”
The Indian Express adds: “the vulnerability is also dubbed as Log4Shell and was first highlighted by researchers at LunaSec.
The issue was discovered in Microsoft-owned Minecraft, though LunaSec warns that “many, many services” are vulnerable to this exploit due to Log4j’s “ubiquitous” presence.
The reason is that this particular open-source Java library is used in almost all major Java-based enterprise apps and servers across the industry.”
It’s not just your infrastructure that’s susceptible. It’s your upstream and downstream suppliers, the one’s that you count on to ensure the smooth running of your organization, that are being impacted. In other words, the companies that you rely on to generate revenue, to meet quarterly earnings or ensure your customers’ expectations are met, are being equally impacted by this cyberbreach.
So, if any one of your supplier’s systems are at risk, if their focus has shifted away from the delivery of goods and services to your organization, what happens if 10 or 100 or 1,000 of your suppliers are facing the same problem?
Do you know how big a problem this could be? Do you know how long this will last? Do you know the extent to which this could impact your business?
We used to see cybersecurity somewhat narrowly as a form of technology or operational risk. Then, our focus shifted to understanding the impact on our customer’s data security and the obligations we have to protect their data (GDPR and CCPA are the most common examples of these obligations).
Now, the interconnectedness of the technology world has intersected with our supply chains and our sustainability (ESG) policies.
 Figure #1: SASB Sustainability Topics
Figure #1: SASB Sustainability Topics
Redefining Supply Chain Risk for Public and Private Corporations
The traditional approach to managing risk within the supply chain had much to do with examining supplier dependencies and their operational performance.
Do I have too many eggs in one basket? Does that create potential supply chain vulnerabilities for my organization? Are they financially stable enough to maintain the supply of goods and services that we rely on?
We see a broader definition emerging, one that builds UPON those still-useful perspectives to include new aspects of risk that are very real. We think these two questions need to be addressed:
The chart below illustrates the top 12 countries globally and the number of private companies per country which may be at risk. Not surprisingly the list consists of developed countries led by the US and UK.
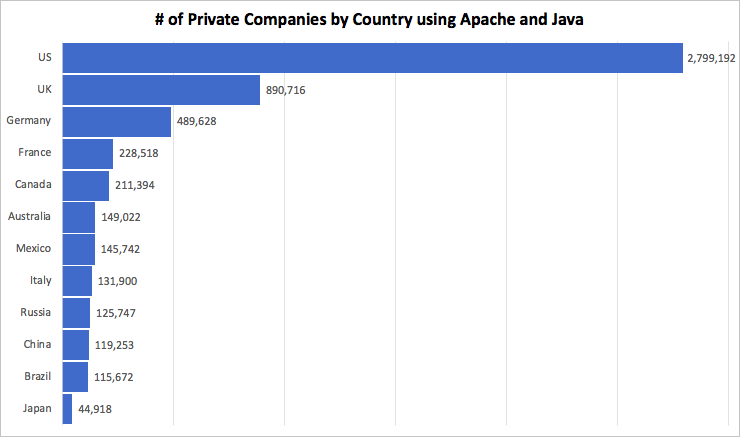 Figure #2: Top Country
Figure #2: Top CountryWhat is potentially concerning is when we look at the global distribution of companies that are using Apache and Java by industry sector. Retail companies lead the list, however, there are over 400,000 NGO and Non-Profits who are also at risk. This indicates that Log4j vulnerability can impact NGO’s humanitarian missions and other infrastructure projects such as health, water and food that are critical for many individuals.
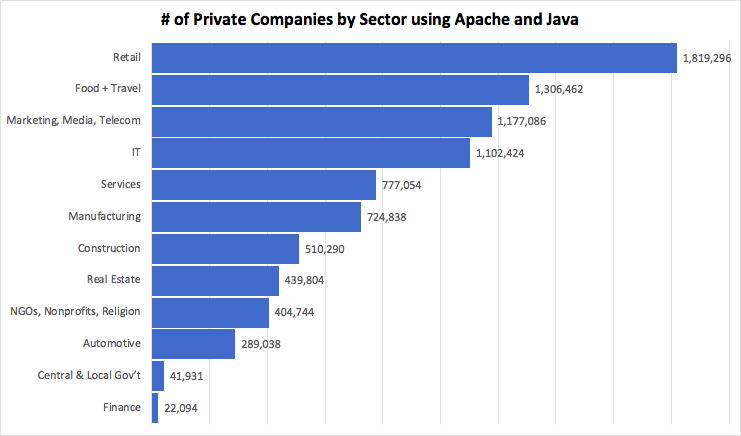 Figure #3: Top Industry Sectors
Figure #3: Top Industry Sectors[bg_collapse view=”button-blue” color=”#FFFFFF” icon=”arrow” expand_text=”Soleadify Methodology – Click Here” collapse_text=”Soleadify Methodology – Click Here” ]
Soleadify analyzes over 700B webpages every month, and scans for signals indicating technologies used on a specific website, including:
All the signals gathered from across the internet are then compared and matched to known patterns indicating specific technologies.
Using this approach, Soleadify is able to identify almost 40M websites active as of this week on the internet, using Apache Software Foundation technologies (the publisher of Log4j)
Log4j is a Java-based logging utility. The mere condition of using other Apache technologies is not a good enough indication that a company is also using Log4j.
So we went a step further, and filtered down the 40M websites by adding a second criterion: the website also has to indicate that the developers use Java (alone or with other programming languages).
This leaves us with 9.5M websites, associated with 8.6M distinct companies.
The industry classification
Soleadify collects company descriptions recently published on the internet (e.g. the “About” page of the company’s website, a press release, a local association etc.) and applies NLP technologies to classify companies by business activities and identify the relevant product and services provided by each company.
This ensures the company classification reflects what the company actually does. In other words, it’s up-to-date, accurate and as granular as needed, as opposed to traditional sources that rely on outdated and rigid SIC/NAICS/NICE codes.
The company location
Similarly, Soleadify collects the addresses of office and retail locations of a company by finding relevant snippets of information across the internet, and using NLP to break down and standardize the address.
This means that the company location is where the business actually located, and not just where it’s registered with the relevant Authorities.
Limitations and other considerations
A company using Apache and Java doesn’t necessarily mean they use Log4j. In both possible interpretations, making this the perfect nightmare for any data scientist out there:
This is just to say that the analysis is not perfect, and we are aware of the limitations.
However, this should be a statistically relevant sample. We expect the distributions to follow reality very closely, as this report is based on the analysis of 40M websites that use Apache technologies.
Last but not least, we expect false negatives to be significantly more than false positives. Log4j is very popular, and we expect the tech combo of Apache technologies + Java to be a good indicator. And the use of all three, just like in the case of our tech stack, to be even more popular “behind the scenes”. [/bg_collapse]
Better Insight is Available…and Soleadify can help!
Our data solutions are designed to provide accessible insights into what makes business’ tick. We see across entire geographic markets and key economies and drill down to the individual company level for over 70 million organizations around the globe. We have developed ESG solutions for third-party risk assessments and we couple that with a deep, proven understanding of what technology that those companies are using to power their business.
Together, our B2B insights can help you address the complex, conflated risks that companies are experiencing more than ever. We can specifically help you: