How to Identify Vendor Fraud


Key Takeaways:
Most businesses rely on vendors every day for supplies, services, and to keep operations running smoothly.
But behind some of those transactions, fraud could be hiding in plain sight.
Vendor fraud is one of the most costly and persistent threats organizations face today. They could take the form of duplicate invoices, falsified contracts, or insider collusion.
These schemes quietly drain resources and erode trust before they’re even detected.
To help you stay ahead, this article breaks down how to identify vendor fraud before it spirals into financial or reputational damage.
By following the steps below, you’ll learn how to recognize red flags early, verify vendor legitimacy, and build stronger controls that protect your business from within.
Your vendor onboarding process is the first and most critical line of defense.
This is where fraudulent actors are often caught. Or, unfortunately, where they sneak in.
The scale of the problem is significant.
Creditsafe’s Battling Vendor Fraud Study found that 47% of fraud cases involved fake identities or bad actors.
That made identity-related schemes the top B2B fraud type in 2024, meaning that nearly half of all fraud starts with falsified information.
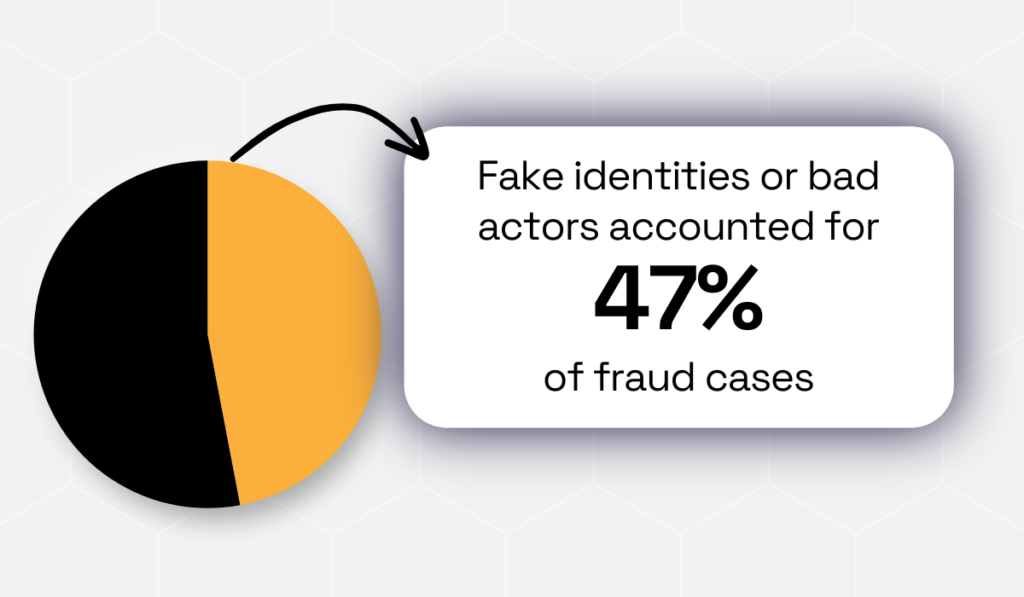
Illustration: Veridion / Data: Creditsafe
Fraudulent vendors often provide incomplete or inconsistent business details because they are counting on you not to check.
A major tip-off is a supplier profile without a verifiable tax ID number. Other warning signs include a missing physical address, or, worse, an address that matches one of your employees’.
These aren’t minor oversights, but rather deliberate tactics.
So the old approach to verification, where data is simply assumed to be reliable, is no longer good enough.
Steve Carpenter, Country Director of North America at Creditsafe, a credit information, risk assessment, and business intelligence services provider, puts it this way:

Illustration: Veridion / Data: Businesswire
Relying on manual methods like email callbacks is slow, prone to error, and easy for fraudsters to manipulate.
The solution?
To systematically cross-check every piece of vendor registration data against verified, independent sources.
This is where modern platforms prove indispensable.
Using a comprehensive platform like Veridion, which maintains an extensive database of verified company profiles and continuously updates this information, automates this vital due diligence.
Source: Veridion
Instead of relying on self-reported data, you can access complete and accurate vendor profiles that are updated weekly.
That way, you can always be sure you’re working with the latest, freshest data available.
Most importantly, this automation flags inconsistencies or missing details before a vendor is ever onboarded.
Source: Veridion
So, with solutions like this at your disposal, taking a vendor’s submitted information at face value should become a thing of the past.
A few minutes of rigorous, technology-backed verification can prevent massive financial and reputational losses.
It is the simplest, most effective step you can take to secure your supply chain from the start.
Payment fraud is a pervasive threat.
Don’t believe us?
The 2025 AFP® Payments Fraud and Control Survey found that 79% of organizations experienced actual or attempted payment fraud.
That figure is staggering, and so is the cost.
Nearly 60% of companies reported that payment fraud in 2024 cost them more than $5 million, with 20% reporting losses exceeding $25 million.
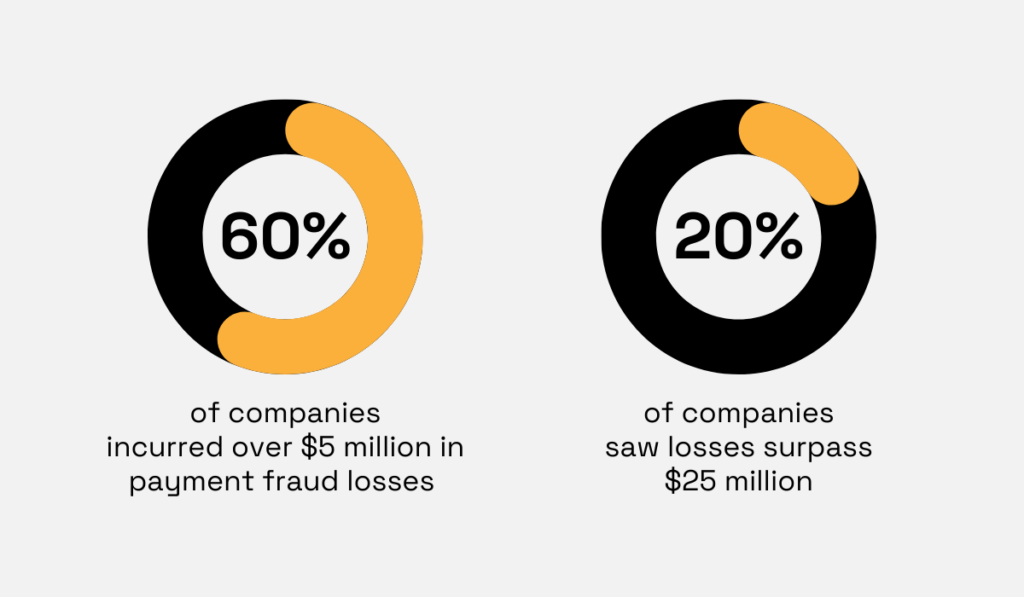
Illustration: Veridion / Data: Trustpair
The common thread in these losses? Irregular payment activity is often the first visible sign.
If you’re not actively analyzing these patterns, you’re operating with a significant blind spot.
Fraud rarely starts with a massive, obvious theft. It begins with small, consistent irregularities that test your controls.
Take, for instance, duplicate or fake invoices.
A fraudster will submit a slightly altered version of a legitimate invoice, hoping to get paid twice for the same service.
Recent studies show that this type of fraud scheme isn’t extinct: 1% of all invoices get paid more than once.

Illustration: Veridion / Data: Liberata
Another major red flag that screams “fraud” is payments strategically designed to bypass approval.
Be suspicious of any vendor that consistently submits invoices just below a review threshold, like, for example, always billing $9,900 when $10,000 requires extra sign-off.
Even a sudden, one-time payment far above a vendor’s normal average deserves immediate scrutiny.
These aren’t random errors.
Consistent oddities in timing or amounts often signal something more deliberate, like internal collusion or a fake supplier scheme.
These patterns are easy to miss when you’re manually processing hundreds of invoices.
Consider what happened to Alan Steven, a farmer in Fife, Scotland, who runs a family farm near St Andrews.
He unknowingly paid thousands to scammers posing as his regular suppliers.
Alan regularly received invoices from his trusted suppliers. Everything always looked normal, and the amounts were consistent.
Until one day, there was a small change: the bank account details.
Without suspecting anything, he paid £12,000 to a building contractor and another £16,000 to a grain merchant.

Source: BBC
It wasn’t until one of his actual suppliers called asking for overdue payment that Alan realized something was wrong.
Scammers had hacked into his email, cloned real invoices, and swapped in their own account details to divert payments.
Like many business owners, Alan was juggling fieldwork, paperwork, and payments on his own, so by the time he caught on, it was already too late.
Though he managed to recover part of the money, he still lost £16,000, which is nearly equivalent to his annual wages.
Alan’s story shows how easily altered payment details or cloned invoices can go unnoticed, particularly in fast-moving operations where payments are processed quickly.
This is a common tragedy.
The average vendor-fraud scheme goes undetected for 18 months, according to EisnerAmper, an accounting and advisory firm.
By the time you find it, the financial damage is already severe.
This is where technology becomes non-negotiable. You need a system that works faster than a fraudster.
Implement automated accounts payable tools or analytics platforms. These systems can flag unusual patterns in real time, before payments are processed.
They can instantly spot a duplicate invoice number, highlight a payment looming below a threshold, or alert you to a sudden spike with a rarely-used vendor.
Unusual payment patterns are your earliest warning system. The faster you can detect them with automation, the more effectively you can protect your organization.
In 2024, vendor fraud schemes impacted nearly 7 out of 10 U.S. companies.
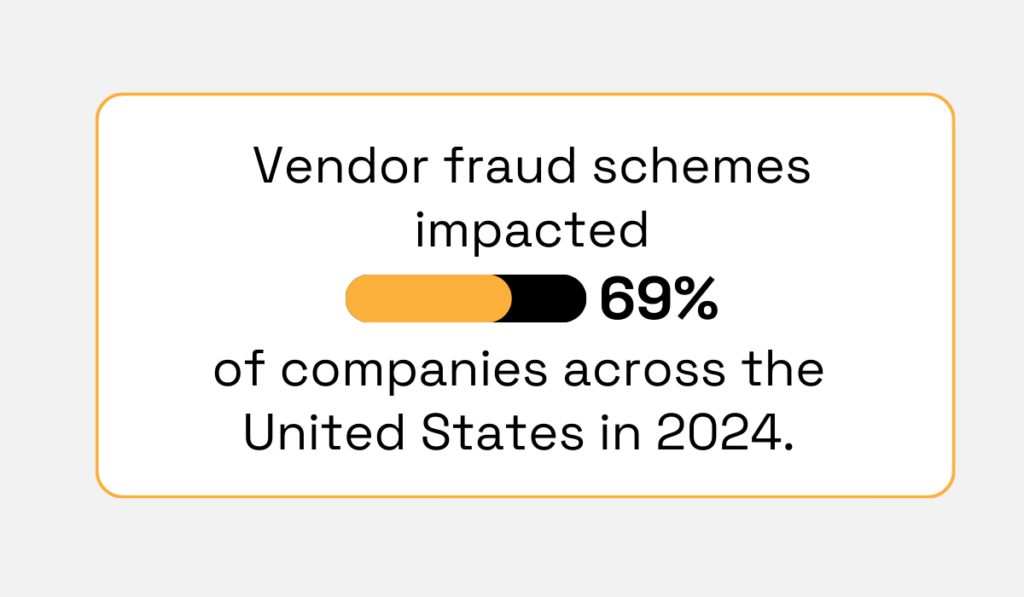
Illustration: Veridion / Data: Trustpair
Among the most common tactics is the use of duplicate vendor accounts.
But how does that work?
It’s simple: a fraudster creates a second account for a legitimate vendor, or they set up a completely fake vendor with a name or address that’s slightly different from a real one.
Then, they divert payments to this ghost account.
Over time, this can drain funds without anyone noticing.
Take what happened at a trucking brokerage firm in Fairmont, where a trusted employee and her son managed to quietly siphon more than half a million dollars over three years.
A long-time employee who processed company transactions created a duplicate vendor account that looked almost identical to a legitimate one in the system.

Source: Bring Me The News
Over the years, she transferred nearly $350,000 from the company’s account into her own, and she funneled another $268,000 to her son’s account.
The scheme only came to light when the company’s owner spotted unusual bank activity and decided to investigate.
When confronted, she admitted to transferring the money. Investigators later confirmed her son had been receiving these fraudulent payments on top of his regular full salary and commissions by paper check.
This is a typical example of asset misappropriation, which makes up 86% of occupational fraud cases, with a median loss of $100,000.
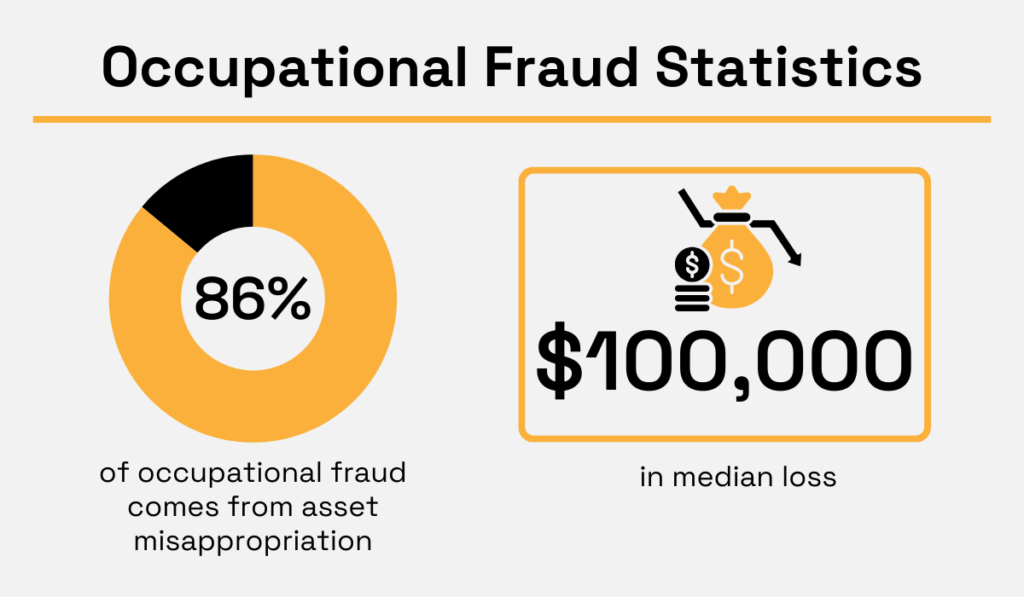
Illustration: Veridion / Data: ACFE
But as this story shows, the damage can climb much higher when duplicate vendors exist.
A single fake entry in your vendor database can open the door to large-scale theft.
You can counter this by regularly cleaning up your vendor master files.
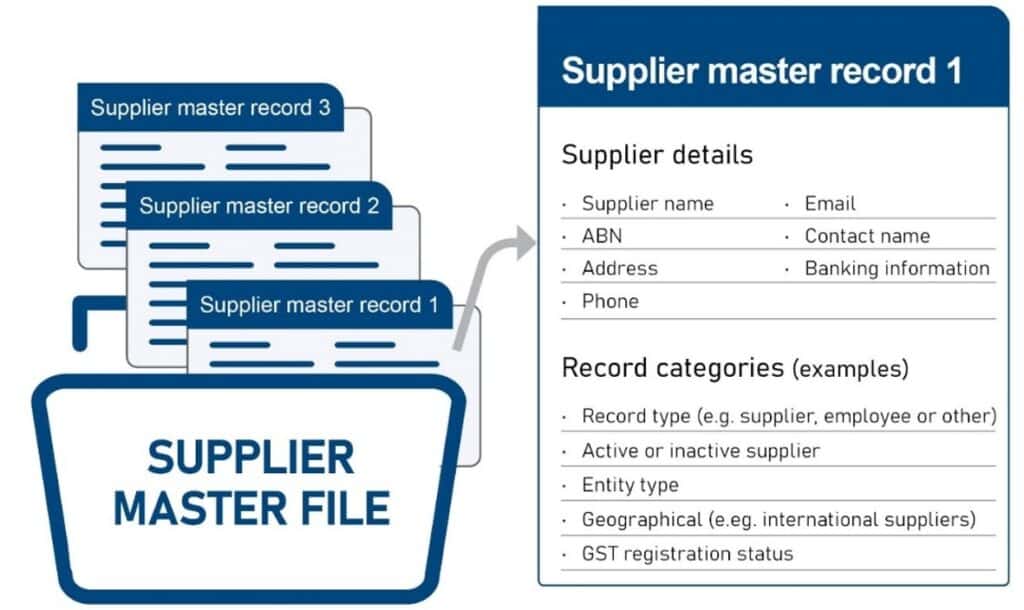
Source: OAG
Run periodic data audits that look for shared identifiers across vendor records, including bank accounts, VAT numbers, or similar names.
If you find multiple entries sharing the same details, investigate immediately.
Automated data deduplication software should also be used here.
These systems can flag nearly identical vendor records, even catching small typos that human eyes might miss.
Failing to remove duplicate vendors leads to duplicate payments, whereas using an automated solution to identify duplicate vendors greatly reduces risk.
This simple safeguard can stop ghost accounts before they become a problem.
Insider collusion is one of the biggest fraud enablers out there.
An employee teams up with an external supplier (or creates a fake one themselves), and together, they swindle money from your organization.
To guard against this, audit the connections and overlaps between your employees and vendors.
Cross-reference vendor information with employee records.
Does a supplier’s address match an employee’s home address? Does their bank account belong to an employee’s relative?
These overlaps are red flags, so investigate them immediately.
Also, enforce strict segregation of duties, meaning that no single employee should control a vendor relationship from selection all the way through payment approval.
This is where experts reinforce the need for caution.
Keith Parsons, Senior VP and Director of Financial Crimes at BOK Financial, a financial services company, explains the risk clearly:

Illustration: Veridion / Data: Biz Journals
This solidifies the importance of companies regularly reviewing vendor activity and the interpersonal relationships between employees and vendors.
In other words, what looks like a harmless friendship might actually be masking a deeper scheme that puts your organization at serious financial and reputational risk.
Parsons’ warning played out in one of the most notorious vendor fraud cases in recent years.
A senior manager at United Airlines’ Newark Liberty International Airport pocketed over $1.6 million in bribes and kickbacks over eight years.
Source: Simple Flying
As a vendor manager, he had the power to influence which companies won United Airlines’ contracts.
Instead of serving the company’s best interest, he used that authority to favor vendors who secretly paid him off.
In return, he helped them secure lucrative deals:
He did all this while appearing to conduct normal business operations.
But he didn’t act alone.
He collaborated with senior employees from multiple vendor companies who helped orchestrate the schemes.
Together, they inflated invoices, created fake subcontracting arrangements, and exchanged personal favors.
Caroline Sadlowski, Attorney at the United States Attorneys’ Offices, summed it up:

Illustration: Veridion / Data: Simple Flying
They even used company funds to pay for home renovations, jewelry, and electronics for employees who could influence contract decisions.
This wasn’t just one bad actor.
It was a network of corruption that ran deep and lasted for years, showing how unchecked employee–vendor relationships can open doors to serious fraud.
The takeaway here is simple but paramount:
Don’t just vet your vendors alone. Instead, vet the relationships between your employees and those vendors, too.
Conduct regular conflict-of-interest checks, monitor gift exchanges, and track contract approvals for patterns of favoritism.
When oversight is weak, loyalty can easily shift from company ethics to personal gain.
Contracts should provide clarity, but fraudsters can manipulate them to create confusion and hide schemes.
So, be wary of inconsistent terms or unexplained changes in pricing structures.
A sudden service fee, an unexpected change in the payment schedule, or contract language that clearly favors the vendor are all signs of potential manipulation.
If a price increase or quantity change appears without a solid explanation, dig deeper.
These “small” adjustments can add up to massive losses.
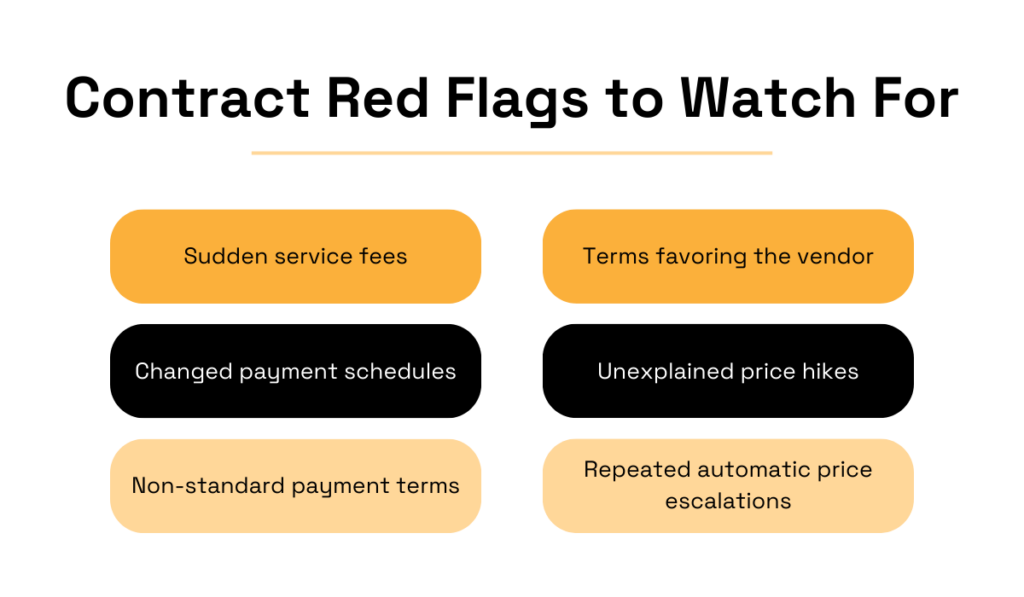
Source: Veridion
Catching these inconsistencies demands a disciplined review process.
This starts with careful contract review and clear approval hierarchies.
Every single contract, but especially amendments, needs a second set of eyes from someone outside the deal, like legal or finance.
Multiple perspectives spot what one person might miss.
Next, centralize your documents.
Storing all contracts in a single repository allows you to compare terms across suppliers and identify dangerous patterns, like repeated automatic price escalations that you never agreed to.
This is where automated contract management systems become essential.
Manual checks are slow and leave room for error, creating gaps that bad actors exploit.
An automated system, however, can instantly scan thousands of documents.
It flags irregularities for you, like higher-than-usual markups, non-standard payment terms, or terms that deviate from your company’s approved language.
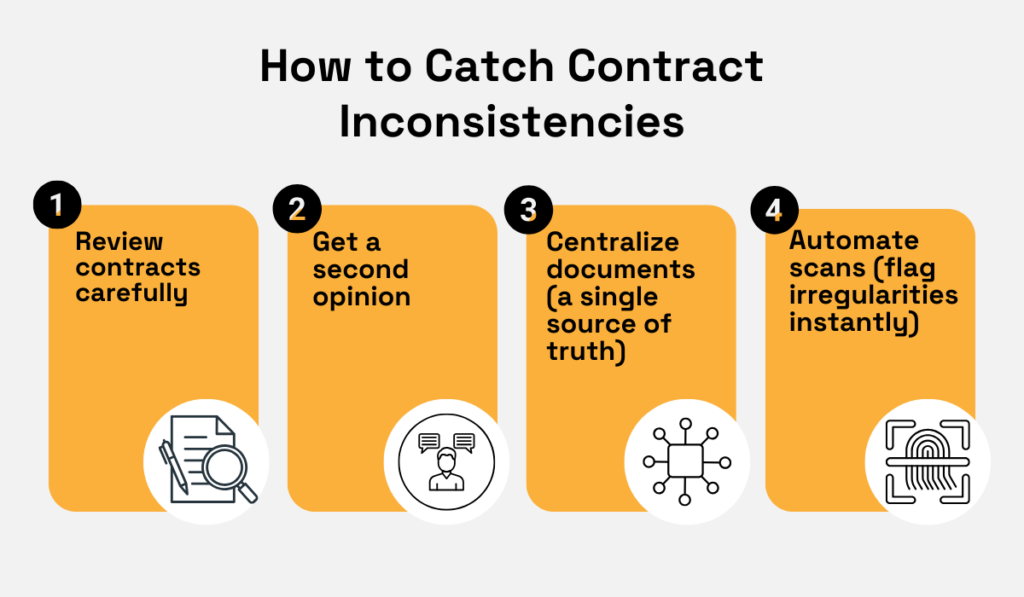
Source: Veridion
But this doesn’t replace human judgment, it simply empowers it.
By automating the tedious work of comparison, your team can focus on investigating other anomalies.
The bottom line? Don’t just file contracts away.
Use a combination of human expertise and technology to make them an active part of your fraud defense.
While we often look for discrepancies in invoices, some of the most telling red flags are behavioral.
And fraudsters’ communication tactics are becoming smarter.
In 2025, business email compromise (BEC) and imposter email scams surged by 103%, making it the top fraud approach used by criminals, according to Trustpair’s Fraud Report.

Illustration: Veridion / Data: Trustpair
These schemes often start with subtle psychological pressure and shifts in tone or urgency.
A fake vendor or impersonated employee might bypass official channels and insist on phone calls instead of corporate email, for instance.
Then, they pressure you to expedite payments under the guise of an “urgent” invoice, thus creating a sense of crisis to make you skip your normal verification steps.
What’s more alarming is that 70% of companies would only flag a vendor if the address or payment details came from a high-risk or international location.

Illustration: Veridion / Data: Creditsafe
This means an over-reliance on data-point checks misses the human element of the deception: an unusual email tone, unexpected payment requests, or vendors avoiding official communication channels.
The solution is twofold: train your people and fortify your processes.
First, training your procurement and finance teams to recognize these unusual communication patterns is non-negotiable.
Encourage a culture of healthy skepticism. If a message feels overly urgent, secretive, or emotional, verify it immediately.
Fraudsters use fear or time pressure to push you into skipping verification.
Second, this training must be backed by clear communication protocols and email monitoring.
These systems maintain accountability and traceability, creating a safety net.
Insist that all vendor communication goes through an approved vendor-master update process.
By combining consistent training on red flags with ironclad protocols, you build a solid human firewall.
Vendor fraud isn’t always obvious, and that’s what makes it dangerous.
But the good news is you can spot it before it causes any damage.
By verifying vendor details, tracking payment patterns, reviewing contracts, and watching for unusual communication or relationships, you build a system that leaves no room for deception.
Technology strengthens that system even more. It automates checks, flags inconsistencies, and helps you act before losses pile up.
The key takeaway is simple: vigilance pays.
Fraud thrives in silence, but proactive monitoring keeps your organization one step ahead.
So, don’t wait for warning signs to appear. Strengthen your defenses today, stay alert, and make fraud prevention a habit, not an afterthought.