5 Biggest Benefits of Effective Third Party Risk Management


Key Takeaways:
Many organizations see third-party risk management (TPRM) only as a means to meet compliance requirements.
But in doing so, they overlook the wider benefits of effective TPRM.
What’s worse, this narrow focus can also reduce investment and make it difficult to gain stakeholder buy-in.
So, if you’ve struggled to explain the value of TPRM or aren’t fully convinced yourself, this article is for you.
We will explore its five key benefits and demonstrate that compliance is just one part of a much larger picture.
Let’s kick things off with one of the most fundamental benefits of TPRM: its ability to reduce exposure to cyber, operational, and legal risks caused by external entities.
This goal is at the core of all TPRM principles.
And, luckily, more and more organizations are starting to recognize it as TPRM’s strongest benefit.
For instance, a 2024 report by RiskRecon found that the majority of companies use TPRM primarily to reduce risk exposure.
This includes a range of risks, from those pertaining to privacy to operational and geopolitical ones.
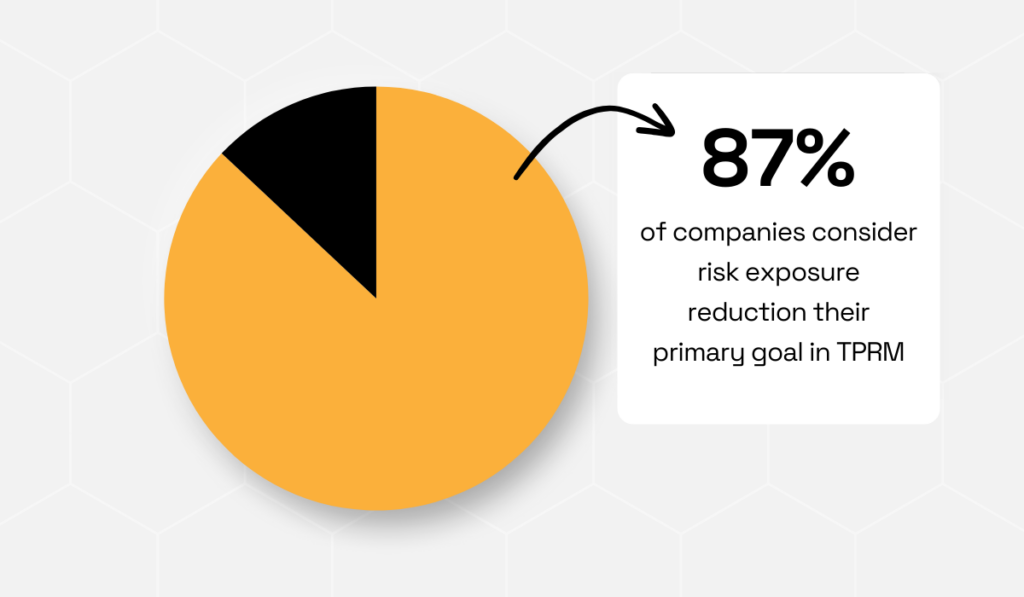
Illustration: Veridion / Data: RiskRecon
As the authors note, this is a positive sign, considering that the last report showed organizations were primarily motivated by compliance.
It seems that, today, they increasingly recognize that TPRM isn’t just about ticking off formal compliance obligations.
It’s also about protecting companies from the very real risks third parties can pose.
This growing awareness may partly come from public crises involving third parties, like the one experienced by Marks and Spencer (M&S).
In early 2025, this multinational retailer was hit by a ransomware attack that completely halted its online business.
The incident received extensive media coverage.
While this likely wasn’t appreciated by the retailer, it helped highlight an important fact: M&S was not breached directly, but through a third-party supplier.
Source: TechRadar
According to TechRadar, the attackers likely used social engineering to convince M&S’s supplier to reset authentication credentials and obtain access to deploy ransomware.
The fallout was brutal.
M&S lost over £750 million in market capitalization and was forced to shut down its online store for several weeks.
On top of that, the attackers stole customer data, leading to a potentially long-term erosion of customer trust and reputational damage for M&S.
Source: BBC
This shows just how important it is to manage third-party risks. Malicious actors don’t have to directly attack your company to do damage, but can exploit the weakest link in your network instead.
This holds true beyond cyber incidents, as similar damage can result from compliance failures, operational disruptions, or financial issues involving third parties.
That’s why, according to the aforementioned report, most companies are already assessing non-cyber risks, with many more planning to start doing so within a year.
You should do the same as part of your TPRM strategy.
Through early vendor risk identification and continuous monitoring, you can identify any type of vulnerability before it escalates.
And, as we’ll see below, this can help you not just protect your internal systems, but your brand reputation, too.
Beyond pointing out cybersecurity risk, M&S demonstrates how third-party incidents can damage brand integrity and customer trust.
For instance, the market research firm The Harris Poll UK found that fewer people are willing to recommend M&S to others following the cyber attack.
More specifically, M&S’s brand advocacy dropped by 14%, falling from 87% before the attack to 73% after it.
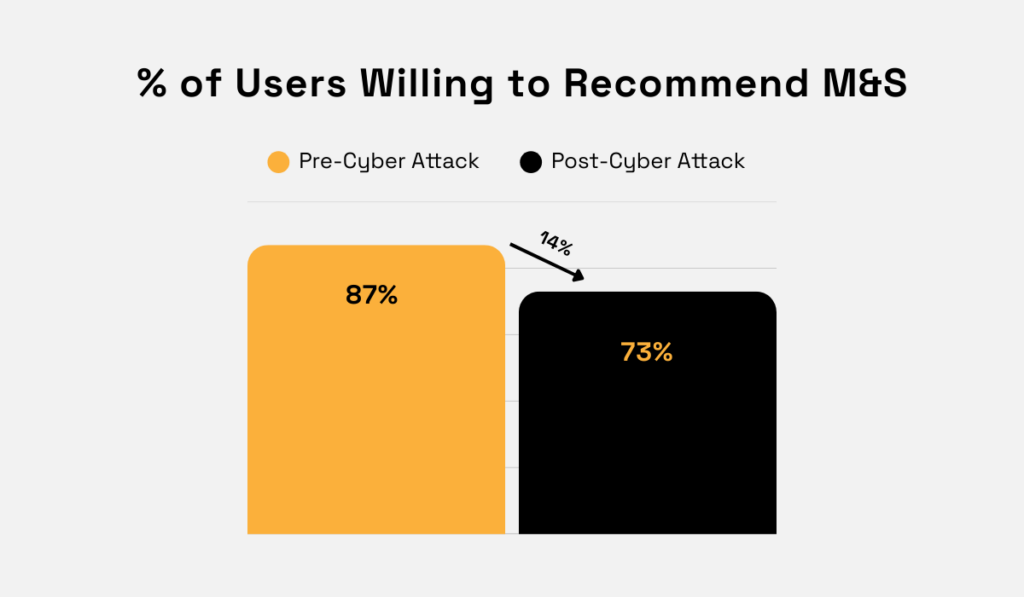
Illustration: Veridion / Data: The Harris Poll UK on LinkedIn
While this indicates a significant drop in consumer trust, other research shows that it could be much worse.
For example, Vercara’s 2023 consumer survey revealed that 66% of consumers would not trust a company that suffered cyber attacks with their data.
What’s more, 75% said they would be willing to sever ties with brands that experienced cybersecurity issues.

Illustration: Veridion / Data: Vercara
So, what can we learn from this?
Two key things.
First, public trust is hard-earned but quickly lost in the wake of data breaches or compliance failures.
Demi Ben-Ari, CTO and co-founder of the third-party cybersecurity firm Panorays, agrees.
He also warns that, even if you’re able to regain trust, the cost of doing so will likely be substantial.

Illustration: Veridion / Quote: Panorays
Second, minimizing third-party incidents is key to preserving trust and brand image.
So, TPRM is not just about reducing risk exposure, but also about protecting your brand from the consequences of unmanaged risks.
It makes you aware of potential vulnerabilities and helps you tackle them silently, before they escalate into public crises.
And if you think “we’d know if third parties endangered our reputation,” it’s time to reconsider.
Reputation damage can be caused by subtle risks, such as vendors’ legal disputes, poor customer feedback, and bad press.
Without a strategic approach, you’re unlikely to spot and address such seemingly minor threats in time.
As we’ve mentioned, the main motivation for TPRM programs has recently shifted from regulatory compliance to risk exposure reduction.
While this is encouraging, the truth is that regulatory demands for third-party oversight are, in fact, rising across industries.
As Dimple Thomas, Managing Director at Deloitte Financial Advisory Services India Private Limited, put it, regulators are no longer satisfied with organizations merely complying with laws and regulations.
They now see this as a bare minimum, and expect significantly more.

Illustration: Veridion / Quote: The Wall Street Journal
At the moment, this is especially true for finance, healthcare, and data protection.
But we can expect the same standards to apply to all sectors shortly.
To meet these requirements, organizations must adopt TPRM.
Without it, it will be nearly impossible to properly manage and oversee external parties.
Consider that, according to Navex, 27% of organizations treat all vendors the same in their risk management processes.
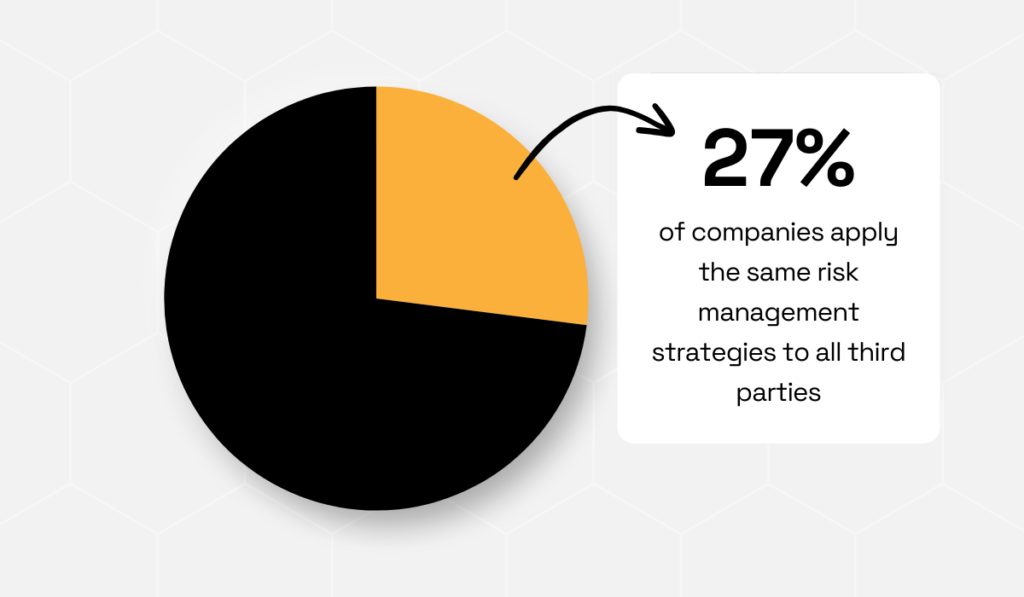
Illustration: Veridion / Data: Navex
There’s no distinguishing between higher- and lower-risk vendors, which makes it highly unlikely that all are managed properly.
TPRM can help you manage them better by enforcing risk-based vendor segmentation and continuous monitoring.
Segmentation starts with risk assessments for each supplier and other third parties.
Once you complete the initial assessment, you should assign each external entity to one of three categories:
This segmentation will give you a clearer understanding of how to manage each individual third party in your network. Some might require more oversight and training, while others may require less.
Keep in mind, however, that risk profiles aren’t fixed. They can change over time, and a previously low-risk supplier can eventually become high-risk.
To ensure your management strategies remain adequate, you’ll need to continuously monitor external entities.
For example, you should regularly watch for any negative publicity or signs of non-compliance.
By doing so, you’ll secure compliance and make audit-readiness a standard practice.
TPRM standardizes supplier onboarding, risk evaluation, and approval flows.
It streamlines these processes by embedding them into structured, repeatable workflows that every vendor must go through.
This, in turn, increases internal efficiency for procurement teams.
Some case studies show that adopting unified TPRM systems and processes can speed up vendor onboarding by 25%.
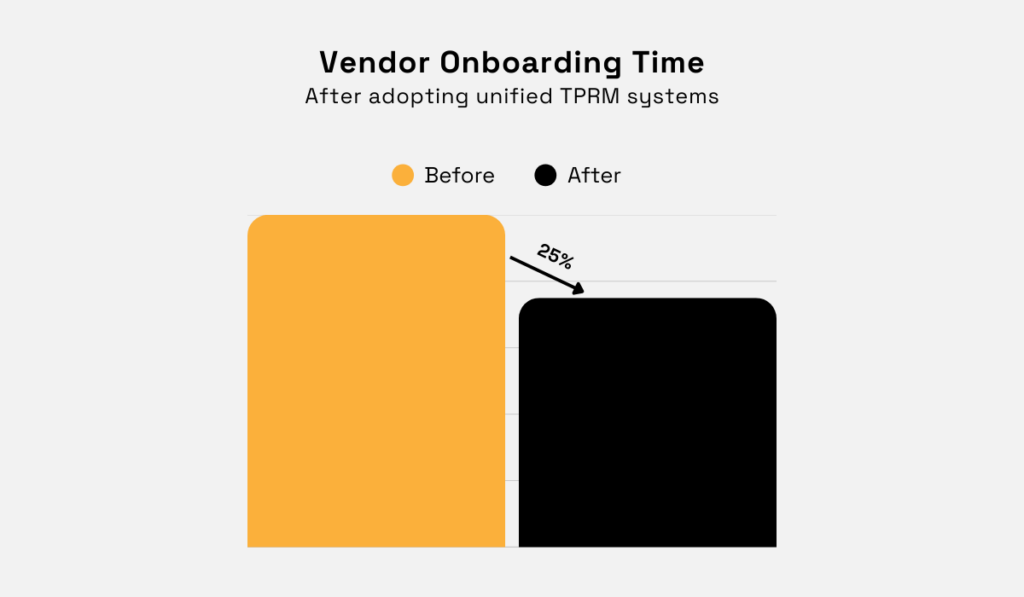
Illustration: Veridion / Data: Diligent
This is possible because standardized processes eliminate confusion.
There are no ad-hoc and duplicative evaluation efforts, and no time wasted deciding who should do what or how.
Everything is streamlined and clear from the get-go.
However, as mentioned, formalized practices are only part of the equation. Another part is adopting solutions that can further speed up and standardize procurement tasks, such as vendor data platforms.
Take Veridion, for example.
Veridion automatically collects data on over 10M manufacturers and 40M service providers, eliminating this task from procurement’s to-do list.
You can integrate the collected data with your TPRM platform to enrich vendor profiles in real time.

Source: Veridion
That way, you automatically get accurate company intelligence and continuous risk signals.
The data is updated weekly and pulled from various sources, from news outlets to company websites, to ensure maximum freshness and credibility.
What’s more, this comprehensive data allows you to assess all types of third-party risks, from product and financial health risks to supply chain, regional, and ESG risks.

Source: Veridion
With one TPRM platform, you can discover, assess, and monitor suppliers with speed and accuracy, giving procurement more time to focus on strategic sourcing and value generation.
It’s a win-win on all fronts.
The last TPRM benefit we’ll mention is strengthening supply chain resilience.
Modern supply chains are highly interdependent, which means that any vendor-related incidents can quickly ripple through the entire network.
For instance, we already mentioned it was a vendor breach that ultimately exposed M&S to a cybersecurity attack.
However, the ripple effect unfortunately didn’t end with M&S.
As the BBC notes, M&S’s suppliers were affected, too, with some resorting to pen and paper for order tracking and placement, and others ramping up deliveries to mitigate potential supply gaps.

Source: BBC
It would be wrong to think this is an isolated incident.
“That could never happen to us” mindset is exactly the kind that leaves companies vulnerable.
Cybersecurity issues caused by external entities are, in fact, more common than most of us would like to believe.
In The state of third-party access in cybersecurity report, as many as 42% of US organizations reported experiencing a cyber attack or data breach in the past 12 months due to third parties accessing their network.

Illustration: Veridion / Data: Imprivata
The situation is even bleaker in some other countries, like the UK and Germany, where 52% of companies fell victim to the same cybersecurity incidents.
Of course, supply chain risks are not exclusively tied to cybersecurity.
Other issues, like a supplier’s financial health, can very much cause disruptions, too.
For example, in 2024, the British manufacturer of off-road vehicles, Ineos, had to pause its entire car production due to one supplier’s “pre-insolvency situation.”
Source: Carscoops
The pause rippled across its supply chain, affecting other vendors as well.
The bottom line is this: every supply chain is prone to similar vulnerabilities that can affect operational continuity, customer delivery, and other critical business outcomes.
TPRM helps guard against these scenarios.
Simply put, it helps organizations plan and be prepared for the worst.
It does so in many ways, including identifying critical suppliers, assessing their continuity plans, and implementing fallback options to reduce downtime.
To mitigate these risks, your processes need to be solid from the ground up. TPRM helps ensure this by forcing you to confront risks directly and make the necessary adjustments.
We’ve explored the five biggest benefits of TPRM, from reducing risk exposure to improving supply chain resilience, and showed how TPRM can protect your brand, operations, and bottom line.
The key takeaway is simple: third-party risks cannot be ignored.
By acting now to strengthen your TPRM program, you can reduce vulnerabilities, stay compliant, and position your business for long-term stability and trust.