5 Best Practices for Third Party Risk Management

Key Takeaways:
The only way to eliminate third-party risks like cyber breaches and compliance failures would be to avoid forming external relationships altogether.
But no business can operate in isolation, which is why effective third-party risk management (TPRM) remains indispensable.
This article explores five best practices that will help you strengthen resilience, keep TPRM aligned with your key business objectives, and ensure partnerships remain an asset, not a liability.
Let’s dive in.
Without strong C-suite and board sponsorship, TPRM programs risk underfunding, low prioritization, and weak adoption across departments.
You may have skilled risk teams and cutting-edge tools, but without executives championing the effort, your program is unlikely to gain momentum.
Worryingly enough, the data shows that executives are paying less attention to third-party risk.
Forrester found that the share of executives citing third parties as a major concern fell by more than 12 percentage points, reaching only 8% between 2023 and 2024.
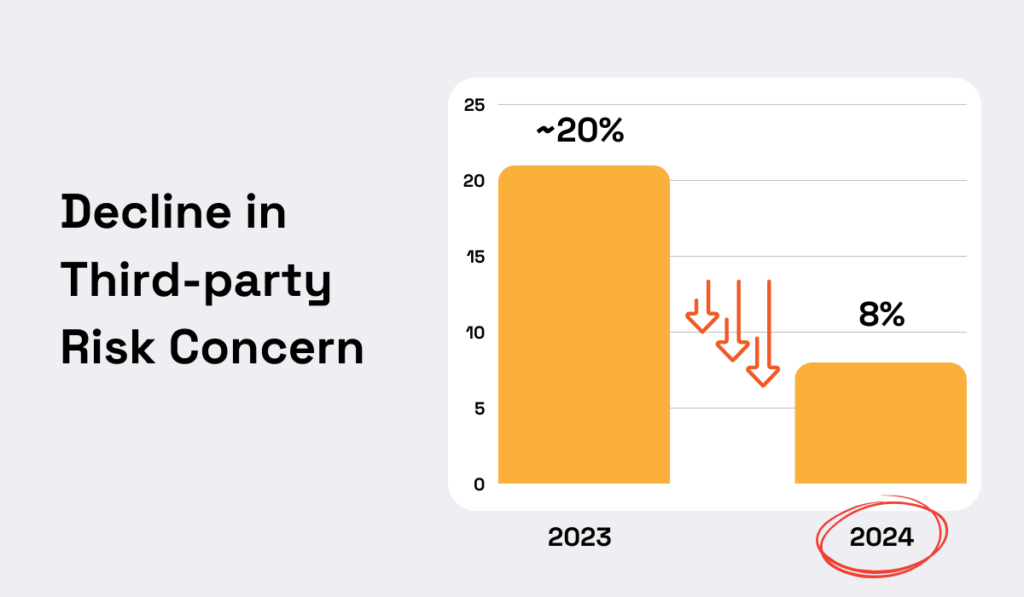
Illustration: Veridion / Data: Forrester
That decline is especially puzzling given the rising number of third-party breaches affecting organizations.
But why the mismatch?
Roughly one-third of survey respondents (32%) explain that other risk areas are simply a higher priority.
This underscores the need to establish third-party risk management (TPRM) as a company-wide priority.
Zuzana Rebrova, Third Party Cyber Risk Management Lead at Swiss Re, a Swiss reinsurance company, stresses the importance of top management buy-in.

Illustration: Veridion / Quote: Cybersecurity News
Executive buy-in accelerates approvals, secures resources, and builds a culture where risk management is not an afterthought but embedded across functions.
To get there, CISOs and risk leaders must present a clear business case, highlighting the consequences of vendor-related incidents, from financial losses and reputational damage to regulatory fines and even operational downtime.
But it’s not enough to highlight risks.
Executives also need assurance that TPRM initiatives won’t detract from other essential processes.
And this is where modern tools make the difference.
Platforms like AuditBoard, for example, use clean dashboards and data visualization to give leadership instant clarity without drowning them in reports.
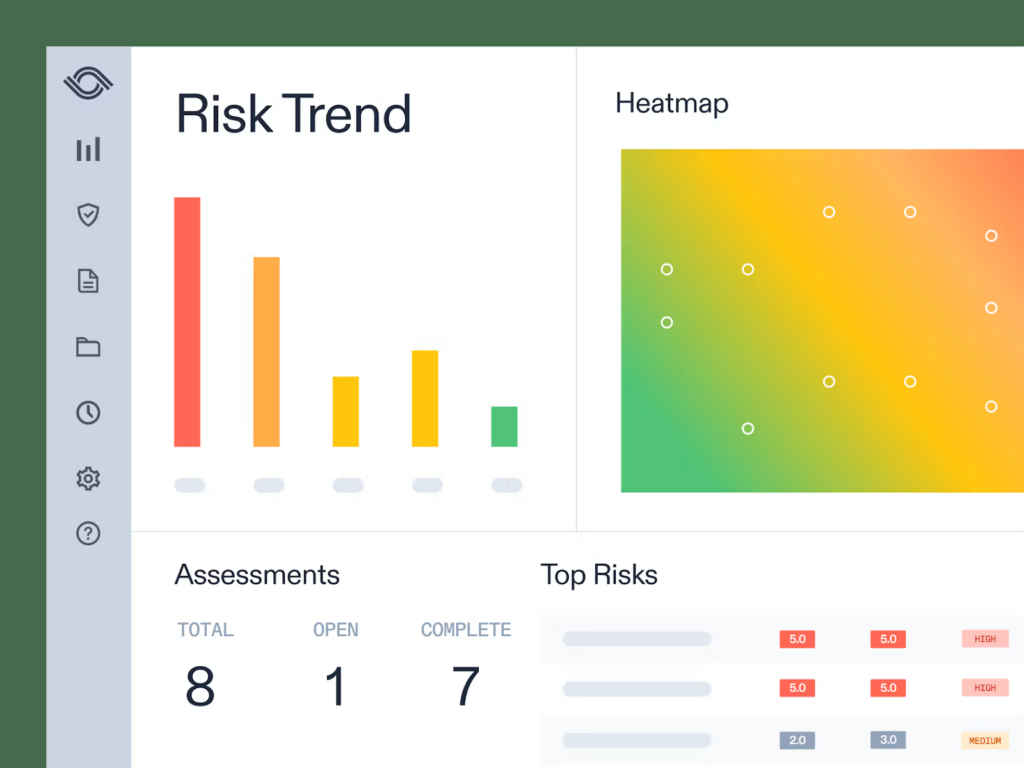
Source: Auditboard
If you were a CRO or CFO, which would you prefer: a 40-page PDF of incident logs, or a single dashboard featuring a heat map showing your top exposures at a glance?
That’s exactly the point made by David Dunn, Chief Risk Officer at FIS:

Illustration: Veridion / Quote: Buzzsprout
There are many ways to get leadership on board, but the principle holds: until executives are convinced, TPRM will remain underpowered.
So, your first step is to “sell” its value by linking it directly to company strategy, growth, and long-term resilience.
You can’t assess or manage risk without first knowing exactly which third parties your business depends on.
This explains why, according to an Economist Impact report, supply chain visibility rose from 30% to 46% in just one year in terms of procurement risk priorities.
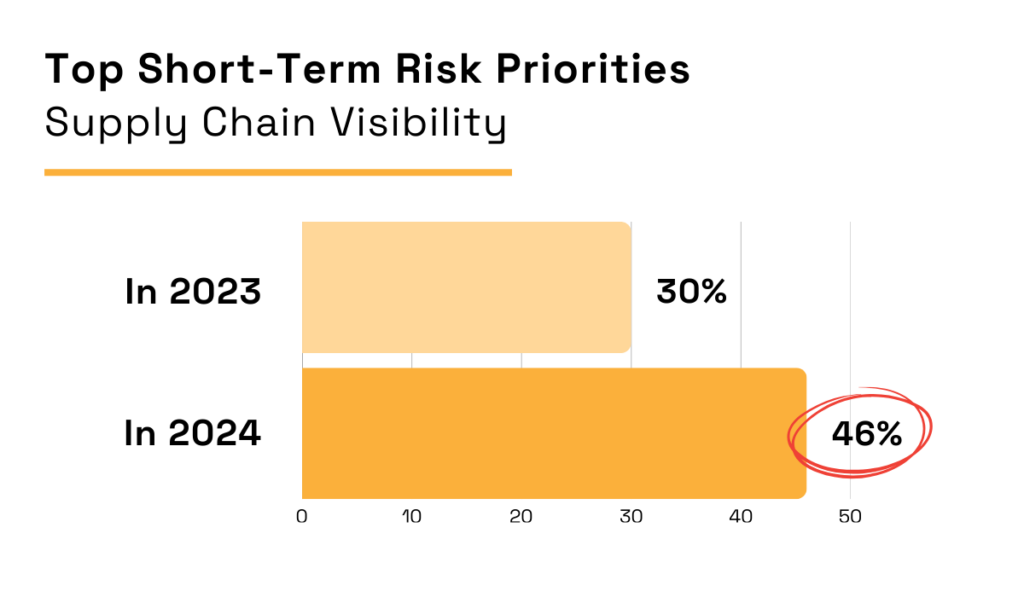
Illustration: Veridion / Data: The Economist Group
Unfortunately, many organizations still don’t have this visibility in practice.
Older studies revealed that 60% of organizations lacked a complete list of third parties with whom they shared sensitive information.
EY’s more recent findings on TPRM maturity show that over a third of companies remain in the earliest stages when it comes to third-party inventory.
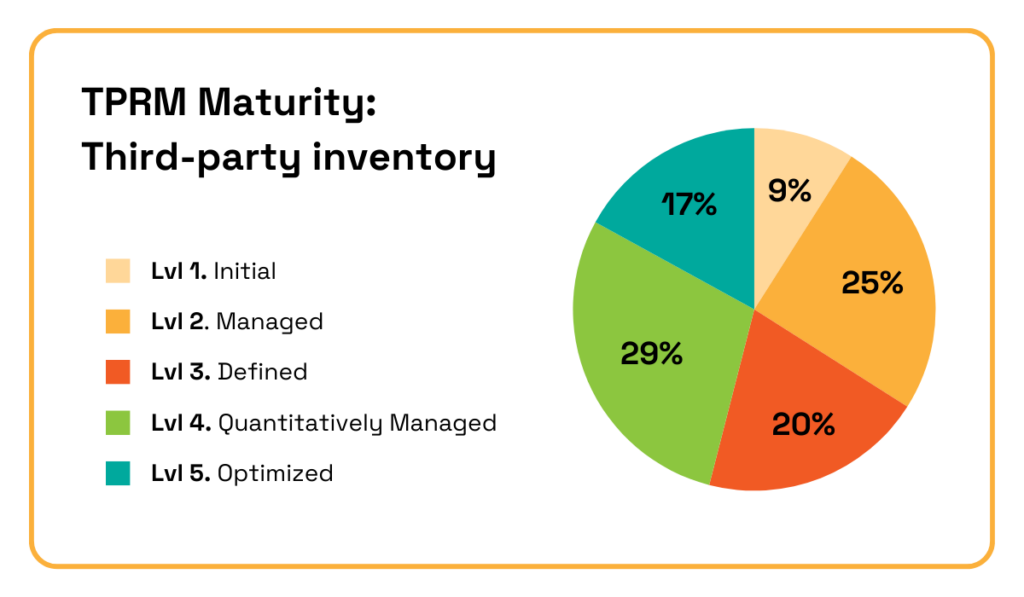
Illustration: Veridion / Data: EY
So, how do you close this gap and move toward optimization?
The foundation is an up-to-date register that serves as the single source of truth for all third-party relationships.
It’s important to note that this isn’t a one-time exercise at onboarding.
Registers must be continuously updated by integrating data from procurement, finance, and legal systems.
If you don’t want “shadow vendors” slipping through the cracks, you need to incorporate structured practices, including:
Ultimately, the most effective approach is to combine manual diligence with the automated detection capabilities of modern TPRM tools.
For instance, Security Scorecard’s Automatic Vendor Detection continuously identifies previously unknown third- and even fourth-party vendors, giving you visibility into the full ecosystem.
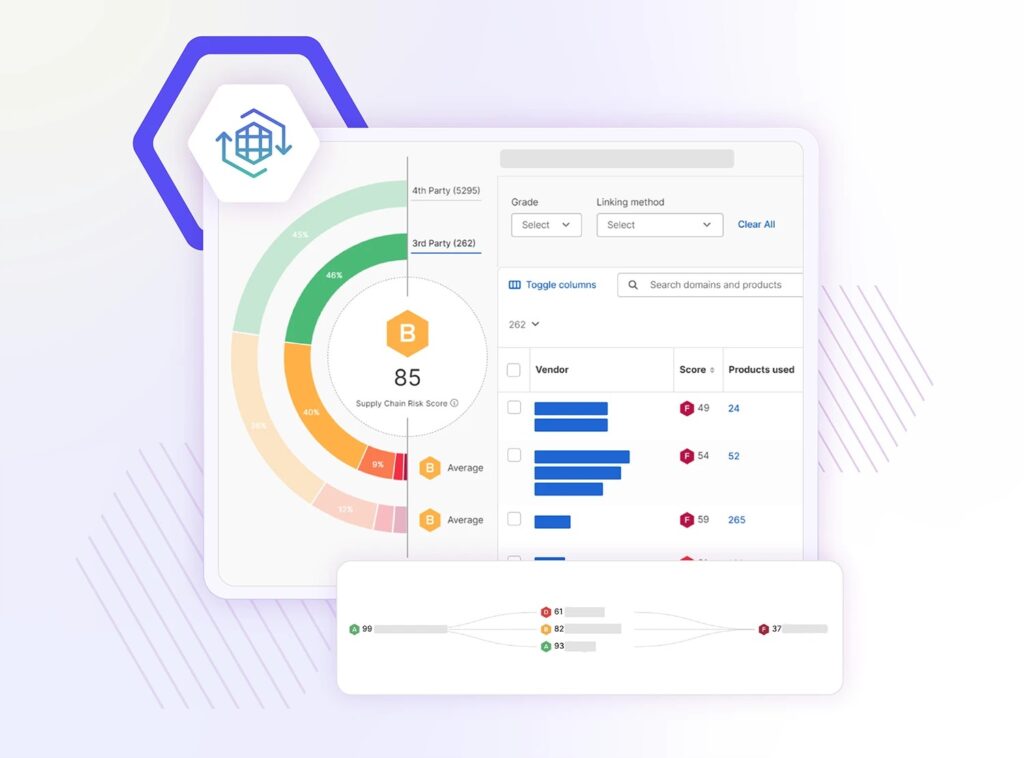
Source: Security Scorecard
Enhancing your existing practices through automation ensures your inventory remains current and comprehensive.
After all, if you don’t know who your vendors are, you can’t know where the risks are coming from.
To sum up, a complete third-party inventory is the first building block for every other element of TPRM, strengthening compliance while also reducing risk exposure from unvetted providers.
An evolving risk landscape demands continuous third-party monitoring.
It’s no coincidence that procurement leaders increasingly see data as the backbone of effective risk management.
Out of 3,000 decision-makers and senior leaders surveyed by Amazon Business, around two-thirds ranked stronger reporting and analytics as either very important or a top priority.
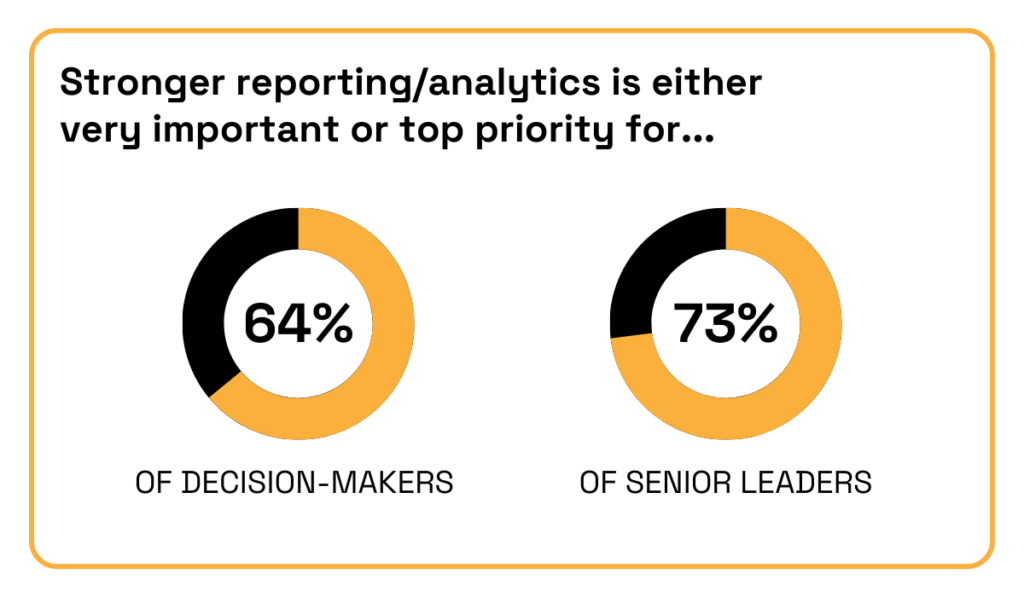
Illustration: Veridion / Data: Amazon Business
This emphasis on real-time data and visibility makes one thing clear: periodic assessments alone aren’t enough.
Organizations need continuous monitoring to detect and respond to risks as they emerge.
Scott McCowan, EY Americas Risk Management Leader, says that continuous monitoring is both a benefit and an integral part of data-driven approaches.

Illustration: Veridion / Quote: EY
Yet, the ability to monitor continuously depends on how well systems are structured.
The aforementioned Economist Impact report shows that 64% of organizations with centralized risk structures can complete control assessments in 31–60 days, compared with only 43% of those with hybrid structures.
A centralized model that integrates procurement data, GRC systems, and assessment tools makes continuous monitoring possible.
Plus, it helps you overcome key TPRM challenges.
Even so, structural alignment alone is not enough. Many organizations still struggle to use the data they collect.
McKinsey found that 82% of firms spend at least one day per week resolving master data quality issues, with two-thirds doing it manually.
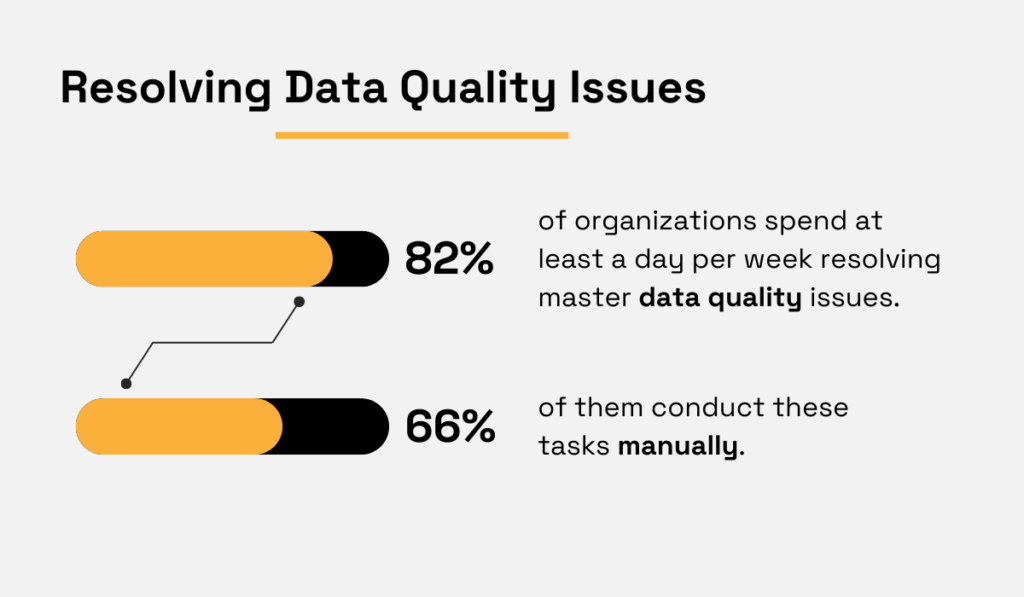
Illustration: Veridion / Data: McKinsey
To overcome these data-related challenges, companies can turn to AI-powered data intelligence platforms like Veridion.
With Veridion, you gain access to a global database of over 130 million businesses, with enriched company profiles refreshed weekly.
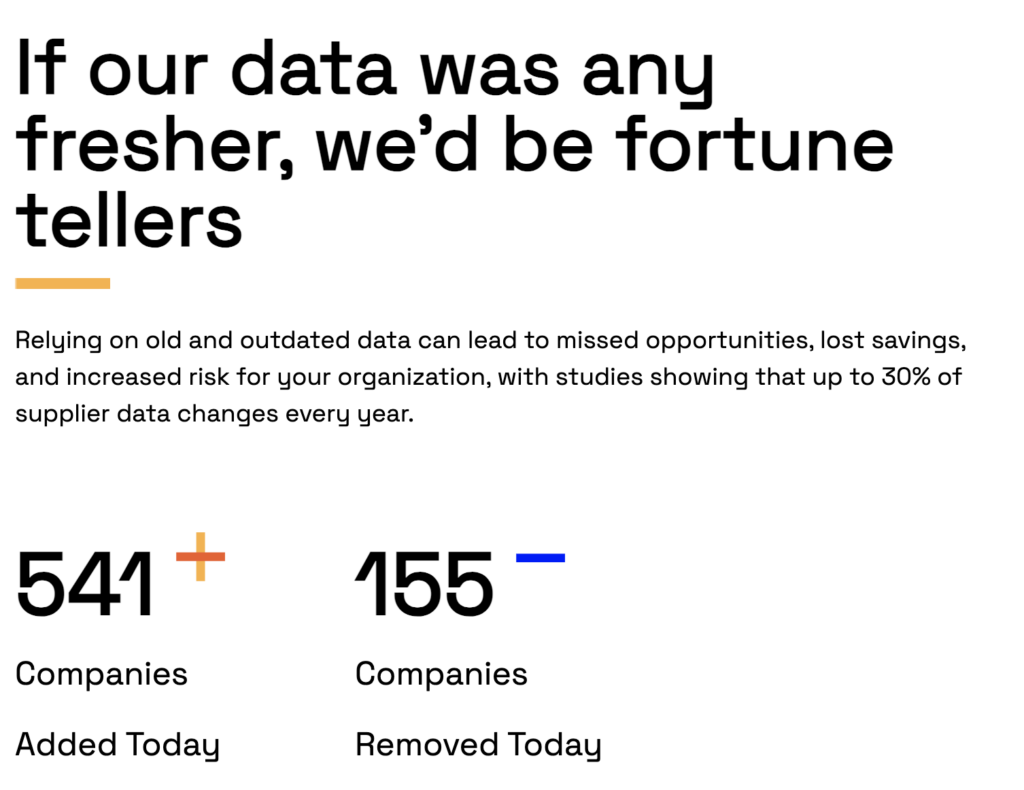
Source: Veridion
If a company has a digital footprint, Veridion ensures it’s captured, providing real-time enrichment, weekly monitoring, and automated alerts.
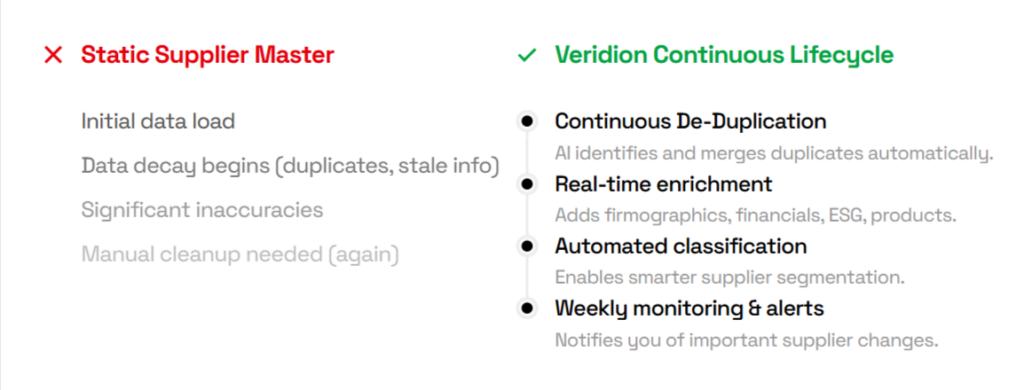
Source: Veridion
This TPRM data integrates seamlessly into your systems, eliminating gaps and manual cleanup.
In practice, this means gaining proactive intelligence across multiple risk categories:
| FOCI (Foreign Ownership, Control, or Influence) | Spot hidden foreign ties that could pose security risks |
| Regional Risk | Track supplier location shifts and mitigate geopolitical exposure |
| Operating Risk | Assess vendor stability and prevent non-compliance |
| Supply Chain Risk | Trace dependencies and anticipate disruptions |
| Financial Health Risk | Monitor key financial indicators to avoid fragile partners |
| Product Risk | Evaluate and mitigate product-related risks |
| ESG Risk | Flag unsustainable or non-compliant practices |
Ultimately, continuous monitoring transforms TPRM from a compliance activity into an early-warning system.
Contracts remain the most practical tool for enforcing resilience, security, and compliance standards with third parties.
They define obligations, establish accountability, and give procurement leaders leverage to demand evidence of proper risk management.
This is especially critical in light of research conducted by Black Kite, which shows that third parties accounted for over 41% of all breaches in the healthcare industry.
Black Kite also found that more than half (51.7%) of publicly disclosed third-party breaches result from unauthorized network access, often tied to misconfigurations and poor access controls.
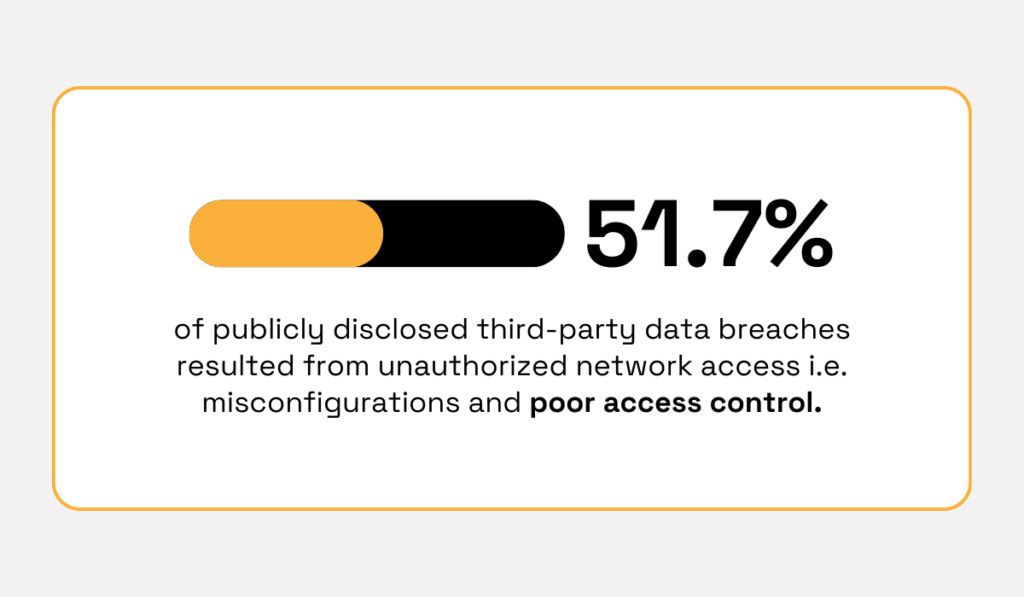
Illustration: Veridion / Data: Black Kite
That’s precisely the kind of exposure that strong contractual provisions are designed to mitigate.
Effective contractual risk controls typically include:
Here are the key areas at a glance.

Source: Veridion
Security requirements such as encryption standards, multi-factor authentication, and timely patching of vulnerabilities are newer, but essential additions for countering cybersecurity risks.
However, drafting and enforcing these clauses can be resource-intensive, which is why procurement teams are turning to AI support.
Roman Belotserkovskiy, partner at McKinsey, points out that AI tools accelerate procurement decisions in different ways, including by evaluating contract clauses.

Illustration: Veridion / Quote: The Economist Group
Icertis’ Risk Assessment Copilot is one of them.
This tool enables organizations to scan supplier contracts, flag risky clauses like liability caps or data privacy gaps, and compare them against company playbooks.
As showcased in the video below, it then generates automated risk scores, allowing teams to prioritize which contracts need legal review versus those that can be fast-tracked safely.
Source: Icertis on YouTube
The benefits of this are tangible, from faster cycle times and fewer overlooked exposures to tighter alignment between procurement, compliance, and business objectives.
Put simply, with well-crafted contracts and the technology to manage them, written obligations become active safeguards.
It’s one thing to launch a TPRM program, but how do you know if it’s working?
Performance metrics are essential for the job because they reveal gaps, highlight areas of underperformance, and provide a basis for strategic decisions.
In fact, these assessments show why 90% of organizations are investing in improving the effectiveness of their TPRM programs.

Illustration: Veridion / Data: EY
But how are these improvements implemented in practice?
A practical starting point is to evaluate your program’s overall maturity in several categories.
Joe Toley, Director of Program Management at Prevalent, a software provider specializing in risk management, recommends assessing the core pillars of TPRM to map strengths and weaknesses before selecting specific KPIs.

Illustration: Veridion / Quote: Prevalent Inc. on YouTube
Prevalent’s model divides TPRM into five essential categories: coverage, content, roles and responsibilities, remediation, and governance.
In the example below, increasing the overall score of 2.94 requires an in-depth understanding of key areas for improvement, particularly content and governance.
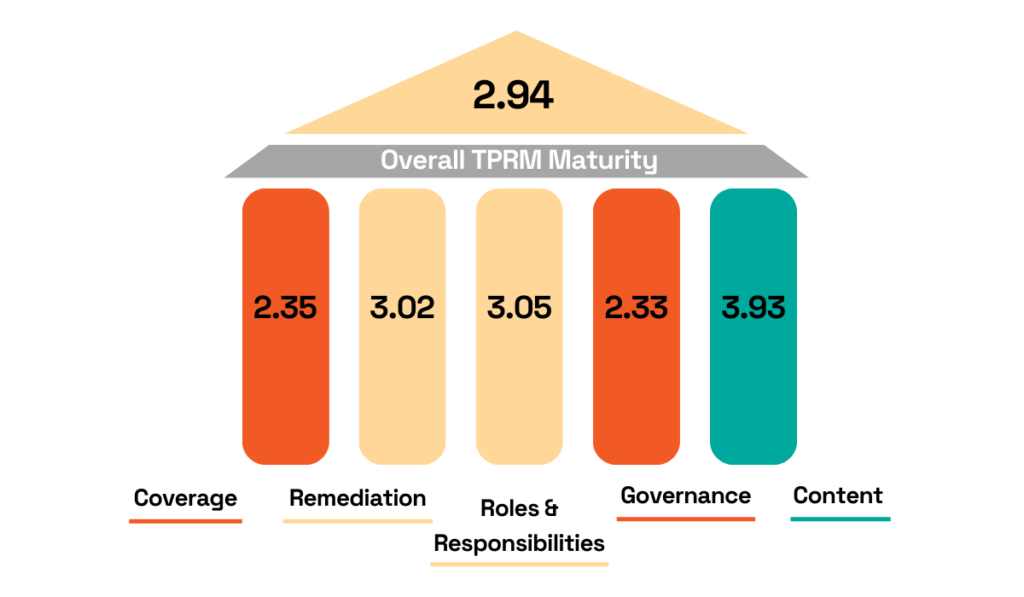
Illustration: Veridion / Source: Prevalent Inc. on YouTube
Governance is the area most directly tied to performance, and is often the one most in need of improvement.
The problem is usually simple: companies don’t track the right metrics.
And relying on gut feeling leaves no basis for strategy.
So, what should you measure?
Here are six key KPIs that procurement and risk leaders can adopt:
| Number of Identified Vendor Risks | Measures program coverage and ability to uncover exposures. |
| Number of Reduced Risks | Tracks how many risks have been mitigated or closed. |
| Cost of Managing Third-Party Risks | Quantifies ROI by comparing direct/indirect costs against losses prevented. |
| Time to Detect Vendor Risks | Indicates efficiency, as faster detection limits potential damage. |
| Time to Mitigate Risks | Reflects risk-response capabilities and resilience in reducing vendor-related threats. |
| Time to Complete Risk Assessments | Balances risk diligence with business efficiency, supporting smoother vendor onboarding. |
Tracking these KPIs does more than produce nice dashboards.
It allows you to demonstrate tangible business value and show evidence of reduced risk exposures, faster response times, and lower costs.
With the right metrics in place, TPRM evolves from a compliance checkbox into a measurable driver of organizational resilience.
Third-party risks will never vanish. They simply evolve.
Organizations that want to do more than survive should treat TPRM as a continuous, data-driven discipline, rather than a one-off compliance project.
The practices we explored, from keeping a complete vendor register to adopting continuous monitoring and KPI tracking, share a common thread.
Strong governance must be paired with the right technology.
Begin assessing gaps and building a roadmap to strengthen your vendor ecosystem today.