Top Main Challenges of TPRM

Key Takeaways:
Third-party risk can have serious operational impacts, from data breaches to regulatory violations and supply disruptions.
Why, then, do so many organizations still struggle with outdated information, lack of visibility, and poor governance, sometimes all at once?
TPRM gaps leave procurement teams exposed, but these risks are far from impossible to address.
Read on to explore the top challenges undermining third-party risk management today, along with key strategies to overcome them.
Fragmented risk ownership is one of the most persistent challenges in third-party risk management (TPRM).
When responsibilities are unclear, you’re looking at:
Interestingly, fragmented ownership doesn’t necessarily stem from underinvestment in risk management.
According to CyberGRX, 64% of leaders view third-party risk management as a strategic priority.
Similarly, over 80% of organizations surveyed by the Business Continuity Institute reported high or medium commitment to supply chain risk.
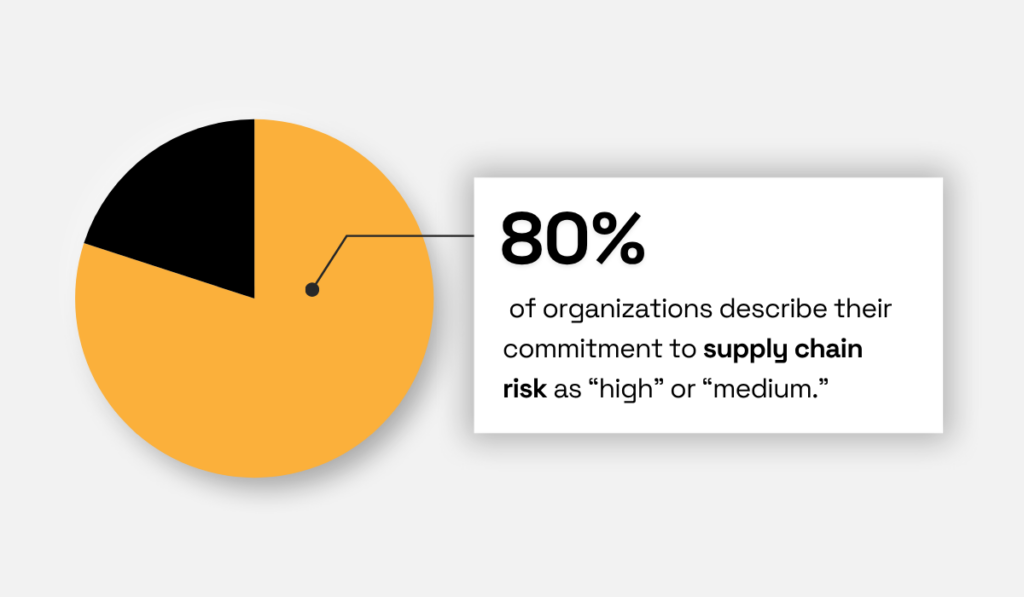
Illustration: Veridion / Data: Business Continuity Institute
Yet despite this commitment, most organizational structures struggle to mirror that priority.
Third-party risk responsibilities are typically split between procurement, legal, compliance, and information security, but without a unifying structure.
This is a reality for more than half of companies.
In 2016, 63% of organizations had no centralized control over third-party relationships.
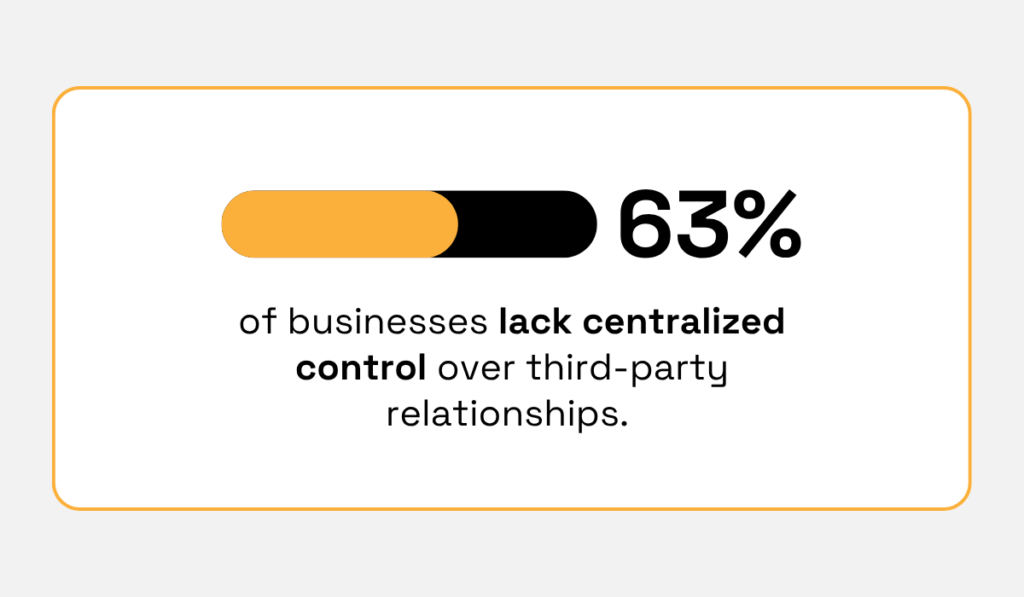
Illustration: Veridion / Data: Ponemon Institute
Without central coordination, ownership naturally becomes fragmented, leaving your business exposed to different vendor risks.
Consider a common scenario where procurement selects a vendor without full visibility into legal or cybersecurity requirements.
Legal, unaware of the vendor’s onboarding status, delays contract approvals. Meanwhile, no one ensures the vendor’s access to sensitive systems is appropriately controlled.
With no shared governance, it’s all too easy for risks to slip through unnoticed.
To avoid this, organizations must clearly define ownership of each process stage.
Typically, procurement handles onboarding and performance, risk teams define frameworks and thresholds, and compliance, security, and operations act as key supporting functions.
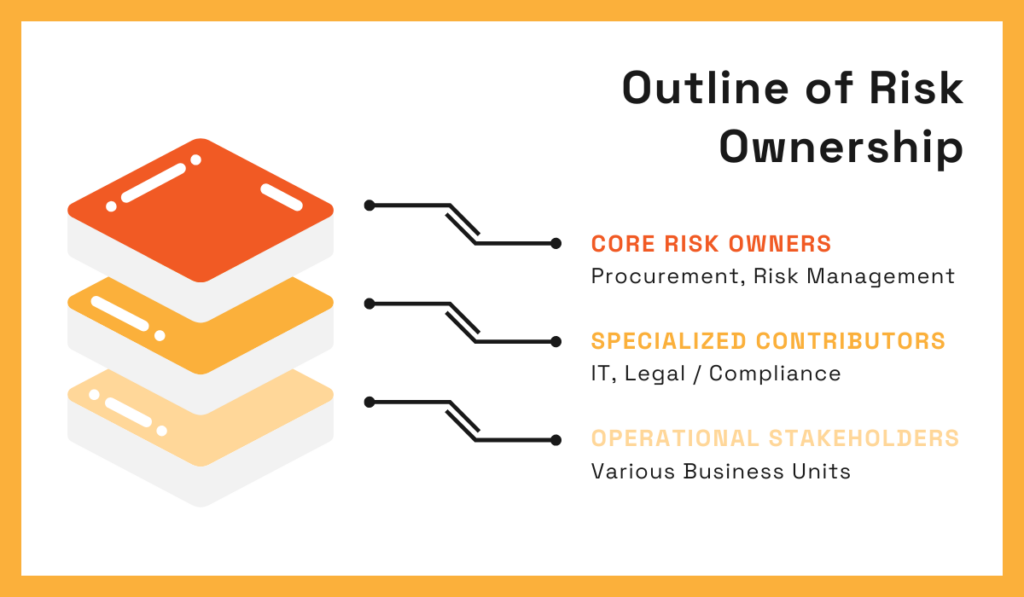
Source: Veridion
For enterprises, this structure needs to be reinforced by a consistent global policy that still allows for regional adjustments.
This brings us back to centralization.
According to a more recent 2023 TPRM survey by EY, 90% of organizations are adopting centralized risk management.
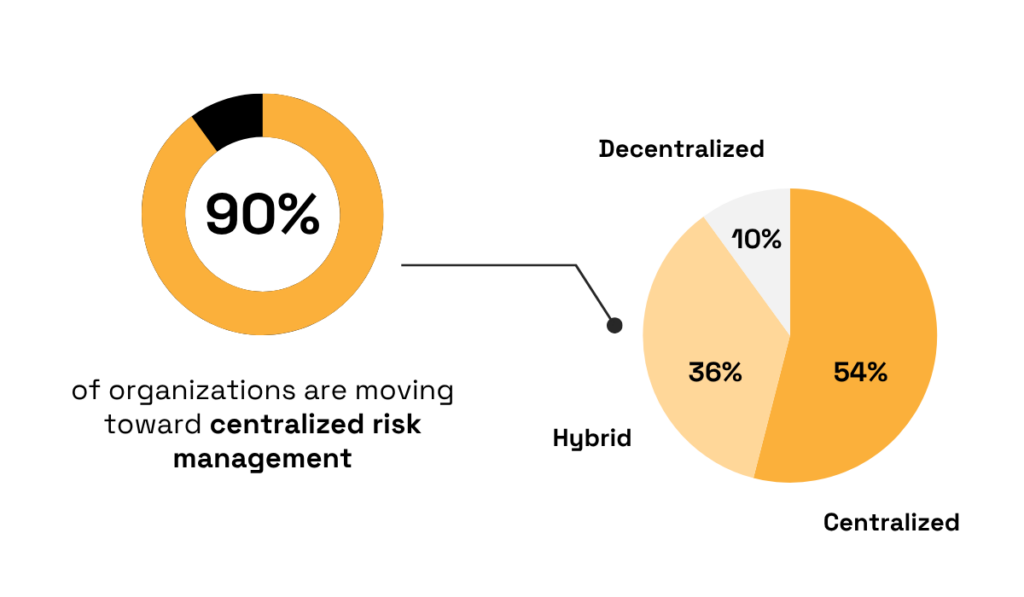
Illustration: Veridion / Data: EY
Although some organizations are still lagging, the value of this approach is well proven.
Another way to strengthen governance is by adopting the 4 Cs framework:
This framework is effective because it acknowledges the often neglected role of communication in holding TPRM together.
The Head of TPRM at Kuwait’s Gulf Bank, Yedhu Krishna Menon, explains that aligning internal and external stakeholders improves every stage of the risk process, from planning to response.

Illustration: Veridion / Quote: LinkedIn
Whether it’s aligning expectations between risk teams and business units, keeping leadership informed, or coordinating incident response, strong communication ensures everyone understands their role and can act quickly.
In short, a centralized governance model is a prerequisite for better collaboration between departments and effective third-party risk management.
Understanding vendor dependencies is foundational to effective third-party risk management, which makes limited visibility one of its biggest challenges.
Without a clear understanding of how your vendors are connected, you expose your organization to operational delays, regulatory missteps, and reputational damage.
Older research shows that a staggering 60% of organizations lacked a complete list of third parties with whom they share sensitive or confidential information.

Illustration: Veridion / Data: Ponemon Institute
Unfortunately, many companies still find themselves in this position today.
This lack of visibility creates two major issues.
First, it increases operational risk. If a critical vendor fails, downstream delivery grinds to a halt.
Second, it introduces serious reputational and cybersecurity risks.
If a vendor lacks proper security controls, a breach in their systems could result in stolen customer data, legal consequences, or media fallout.
And this is far from a theoretical concern.
According to the WEF’s 2024 Global Cybersecurity Outlook, 98% of organizations report that at least one of their third-party partners suffered a data breach in the past two years.

Illustration: Veridion / Data: World Economic Forum
One case in point is the satellite navigation giant, TomTom.
Following a data breach traced back to the vulnerable third-party platform MOVEit, the company had to scramble to close security gaps and strengthen safeguards.
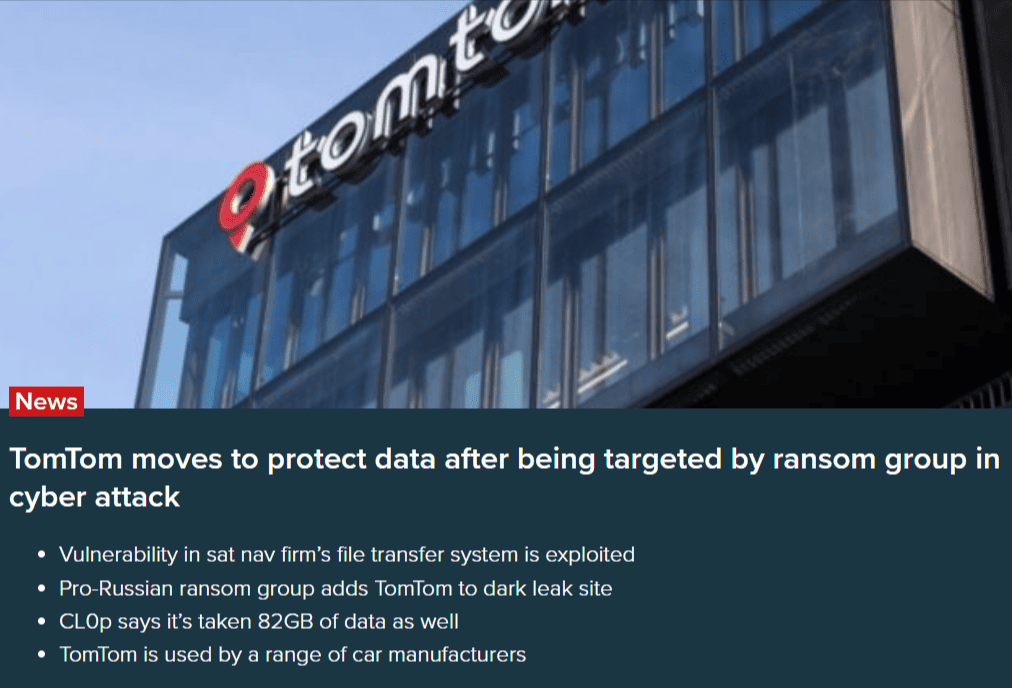
Source: Car Dealer Magazine
While TomTom didn’t suffer major reputational harm, its client list includes Uber, Verizon, and Microsoft, as well as major automotive manufacturers, whose trust the company can’t afford to lose.
So, how can procurement teams improve visibility and reduce risk?
One powerful method is supply chain mapping.
These tools trace dependencies across multiple tiers of suppliers and flag key risk areas.
Adoption surged during the COVID-19 pandemic, when disruptions exposed the fragility of global supply chains.
In 2019, only 22.6% of organizations used technology for supply chain mapping. By 2020, that figure had jumped to 40.5%.
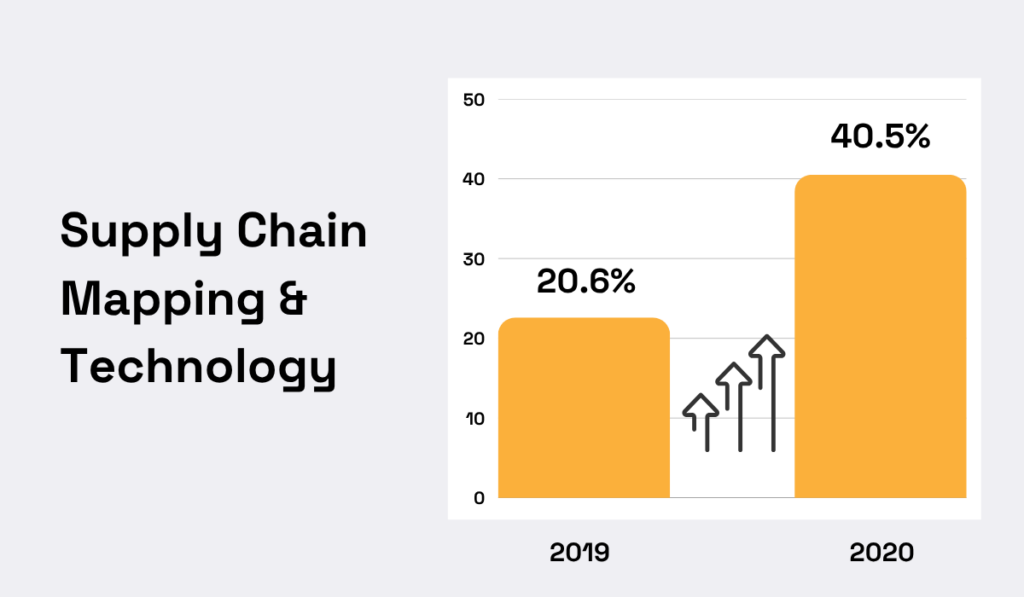
Illustration: Veridion / Data: Business Continuity Institute
Supply chain mapping often works through a “cascading invitation” model, where each vendor invites its own suppliers, revealing multi-tier relationships.
Tools like Sourcemap enhance this process by offering powerful visualization capabilities, such as risk heat maps pictured below.
Source: Sourcemap
However, broader visibility is only part of the solution.
Its real value comes when paired with regular assessments, centralized vendor databases, and continuous monitoring.
Don’t forget that limited visibility into your vendors means you’re not managing risk, but rather reacting to it.
Nowhere is outdated information more damaging than in third-party risk assessments.
If the data you’re using is stale, incomplete, or inconsistent, your conclusions will inevitably be flawed, impacting everything from compliance to operational performance.
It’s no surprise that 82% of organizations surveyed by McKinsey spend at least one day per week resolving master data quality issues.
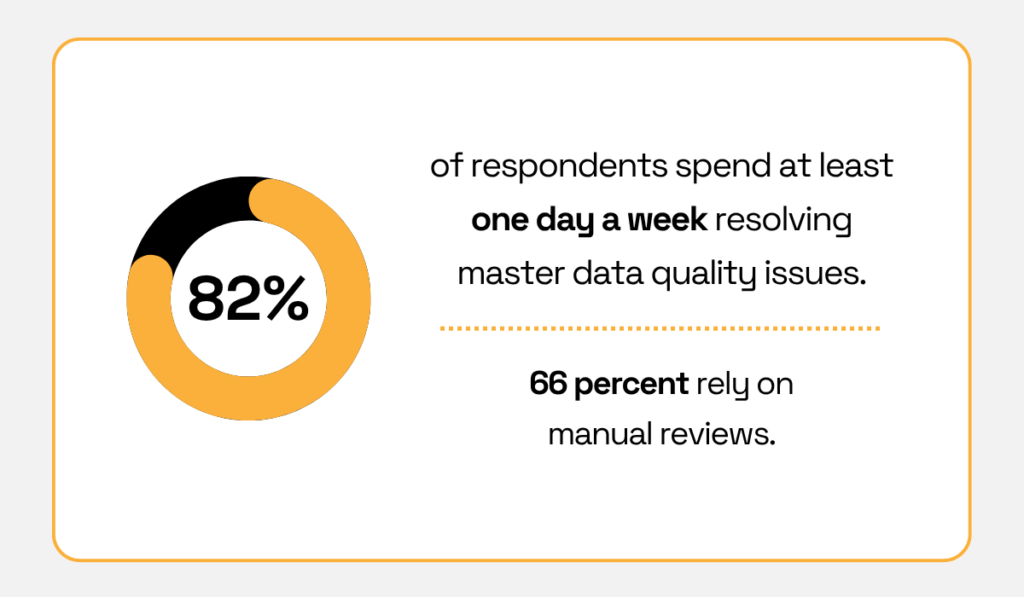
Illustration: Veridion / Data: McKinsey
Among the top problems cited were incomplete data (71%), inconsistent records (67%), and obsolete data (31%).
In TPRM, outdated information can easily conceal emerging threats, such as changes in ownership structure, financial instability, or increased exposure to high-risk regions.
The reason this happens?
Most organizations simply can’t keep up with real-time updates.
As SpendHQ reports, roughly 75% of procurement teams cannot refresh their data daily or in real time.
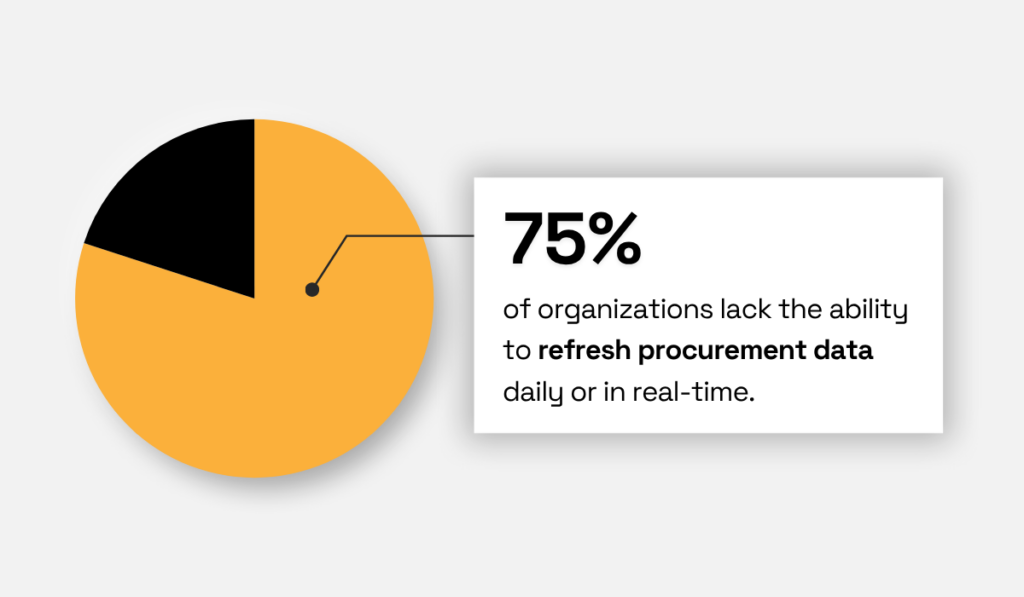
Illustration: Veridion / Data: Spend HQ
There are several ways to build this capability, but one of the most effective is leveraging advanced data analytics platforms such as Veridion.
Powered by AI and machine learning, Veridion continuously updates its global database of over 130 million companies, capturing more than 200 attributes for each profile.
With fresh, weekly-updated data, organizations can respond swiftly to market shifts and emerging risks.

Source: Veridion
But what does this level of freshness and coverage mean in practice?
It transforms TPRM outcomes, thanks to a purpose-built dataset designed for risk management.
With Veridion, organizations can:
Many of these insights stem from just a few powerful data categories.
For instance, corporate family insights allow you to trace connections between vendors and uncover hidden third- or fourth-party risks.
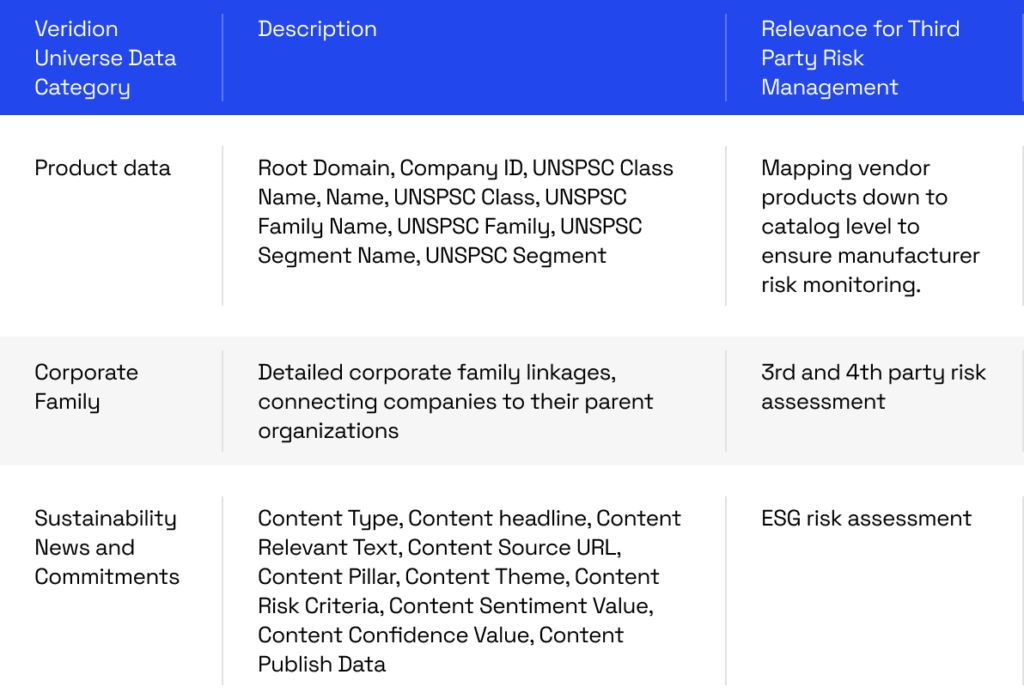
Source: Veridion
That’s something that static and outdated datasets simply can’t deliver.
In TPRM, making decisions with poor data carries a high cost.
Modern procurement demands live, structured, and actionable insights that support proactive risk mitigation.
No amount of due diligence is enough if you don’t have ongoing risk monitoring in place.
Risks evolve, and without ongoing oversight, even your most trusted third parties can become liabilities.
Unfortunately, many organizations are still playing catch-up.
According to EY’s Global TPRM Survey, less than one-third of respondents have been running a TPRM program for more than five years.
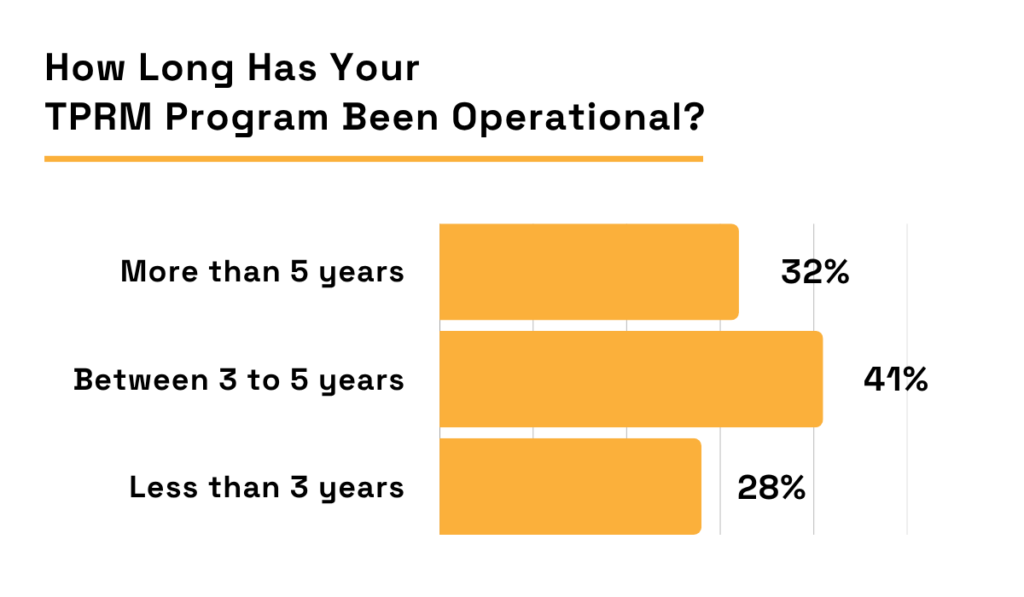
Illustration: Veridion / Data: EY
Even more telling, only 28% of respondents have launched their TPRM programs within the past three years.
And when you’re still laying the groundwork, there can be little talk of continuous monitoring.
At a minimum, effective risk monitoring involves:
Establishing formal governance is a critical first step, but structure alone isn’t enough.
As Nicolas Walden from The Hackett Group points out, manual monitoring methods can’t compete with modern tools that leverage advanced analytics and automated alerts.

Illustration: Veridion / Quote: Procurement Magazine
There are many types of risk management tools, but they share a common strength: the ability to ingest and analyze data from multiple sources.
This is where platforms like Resolver stand out.
You can easily conduct vendor assessments, generate custom reports, and set up real-time notifications for changes in key risk profiles.
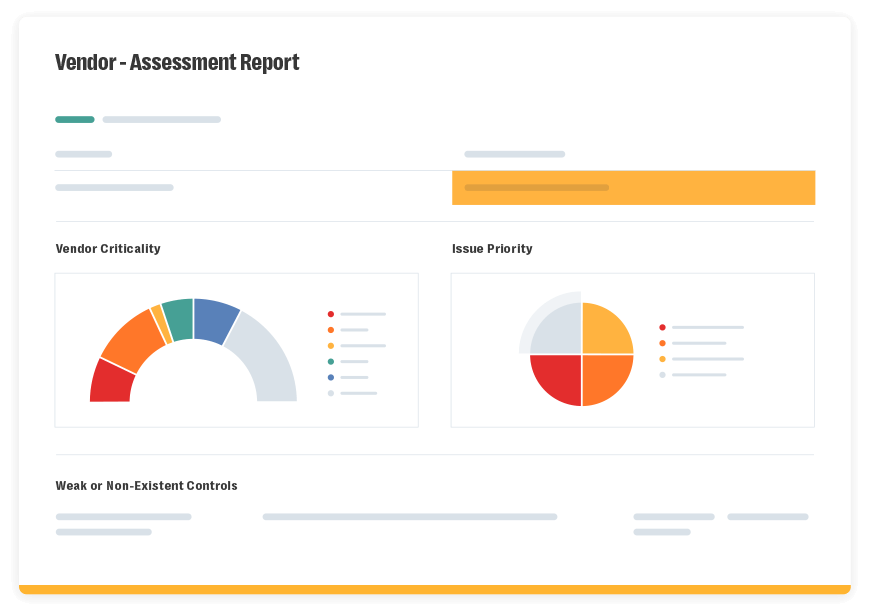
Source: Resolver
Resolver’s AI capabilities go further by aggregating intelligence from multiple sources and applying historical insights to assess current risks.
It’s how companies build a truly proactive monitoring process.
Keep in mind that many third parties outsource critical services, exposing your business to risks beyond your direct suppliers.
While these fourth parties are often overlooked, EY’s Joseph Kelly, TPRM leader, notes that this is beginning to change thanks to reliable external data sources.

Illustration: Veridion / Quote: EY
No surprise, then, that many monitoring platforms now focus on extending visibility to n-th parties.
MetricStream, for example, lets users map and monitor the associated vendors of their suppliers, bringing fourth-party risk into scope with just a few clicks.
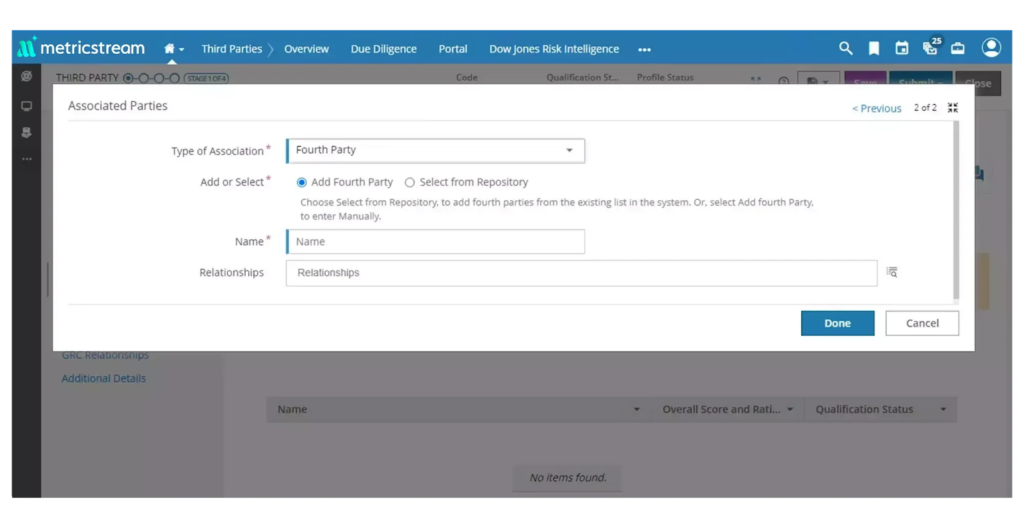
Source: MetricStream
Failing to invest in ongoing monitoring is a serious TPRM shortcoming.
But building the right processes and adopting the right tools delivers clear, lasting ROI.
Automating third-party risk management workflows saves time, but it’s also essential for improving consistency and scalability of your TPRM efforts.
In contrast, organizations that rely on manual, traditional workflows often spread data across spreadsheets and emails, leading to siloed systems and slower responses to emerging risks.
Research shows that automation efforts are still lagging.
According to EY, only 7% of companies have fully optimized their use of automation in TPRM.
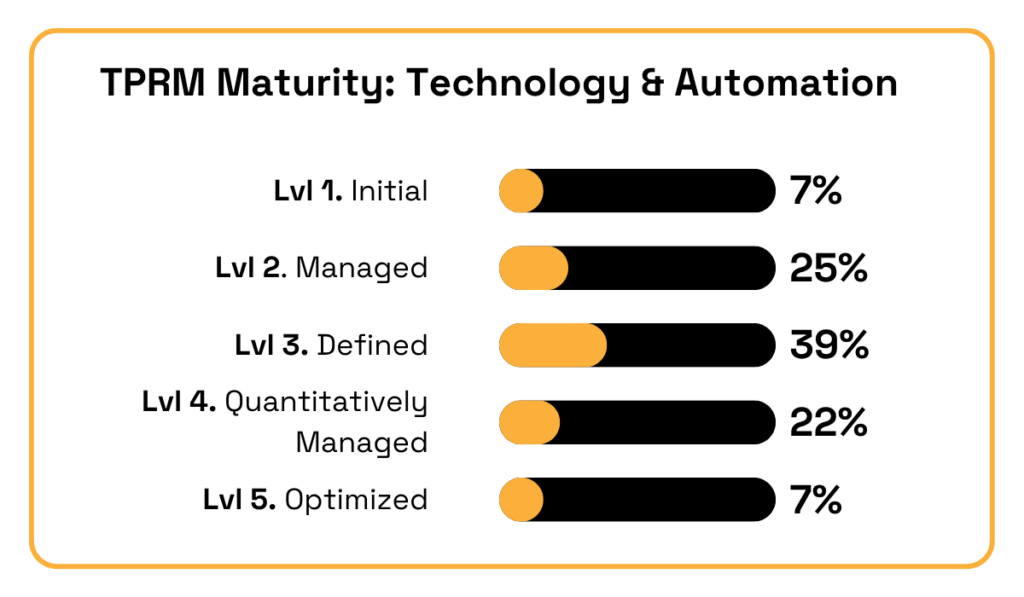
Illustration: Veridion / Data: EY
Meanwhile, around one-third remain stuck at a purely reactive stage, using automation in isolated cases instead of embedding it across the entire program.
How is this possible, given the heavy investments in technology?
In the aforementioned report, EY breaks TPRM down into seven capability pillars, one of which is automation.
A more mature TPRM program means that the organization is better at aligning its workflows with leading practices and standardizing processes across the enterprise.
As pointed out by Michael Giarrusso, EY Americas FSO Third Party Risk Leader, without this intentionality, companies risk undermining even the best technology.

Illustration: Veridion / Quote: EY
Take manual data entry, a major bottleneck and a common drain on productivity.
So significant, in fact, that 32% of CPOs view even minimal reductions in manual data entry as a significant efficiency boost for procurement teams.
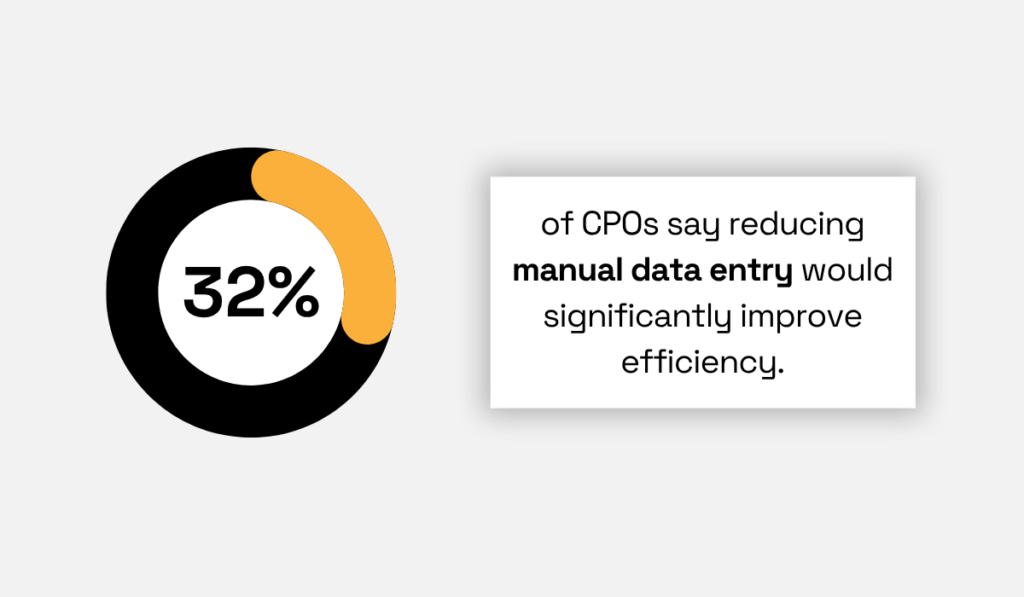
Illustration: Veridion / Data: TealBook
Automating this single task would free up resources for higher-value activities such as risk assessment and strategic planning, while also reducing the likelihood of costly errors.
That said, automation should be applied gradually and strategically.
Start by identifying your most critical vendors and the risk categories that would benefit most from structured, automated workflows.
Some industries are already seeing faster adoption out of necessity.
In fashion, where supply chain scrutiny is increasing, tools like Trust Trace are raising the bar.
Trust Trace uses AI to automate traceability, connecting supplier declarations and documentation to actual shipments.
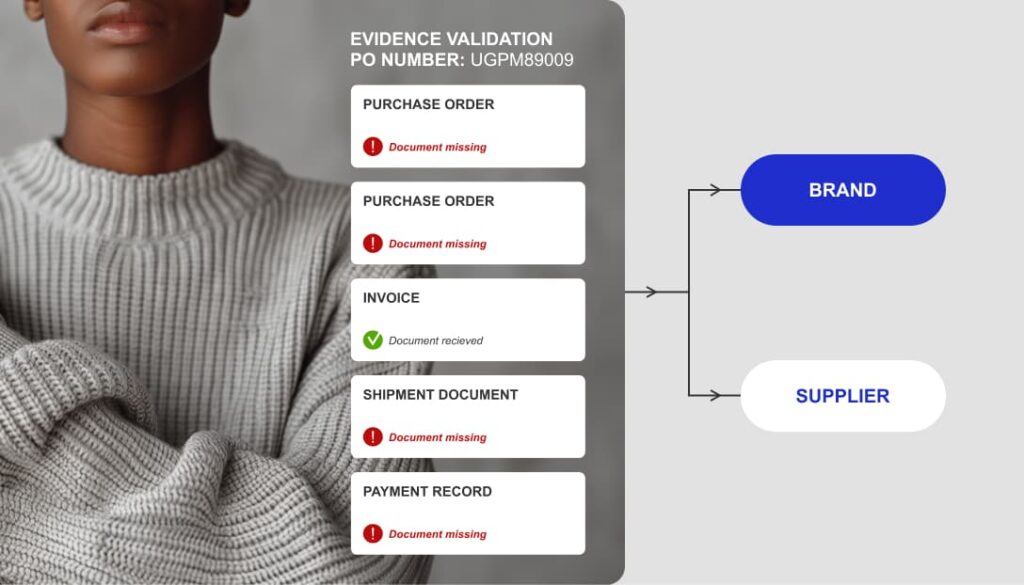
Source: Trust Trace
This helps detect nonconformities such as forced labor risks more quickly, supporting compliance with regulations like the UFLPA and CBAM.
Equally important, its smart alert system ensures that relevant procurement team members are instantly notified of risks, no matter how deep they are within the supply chain.
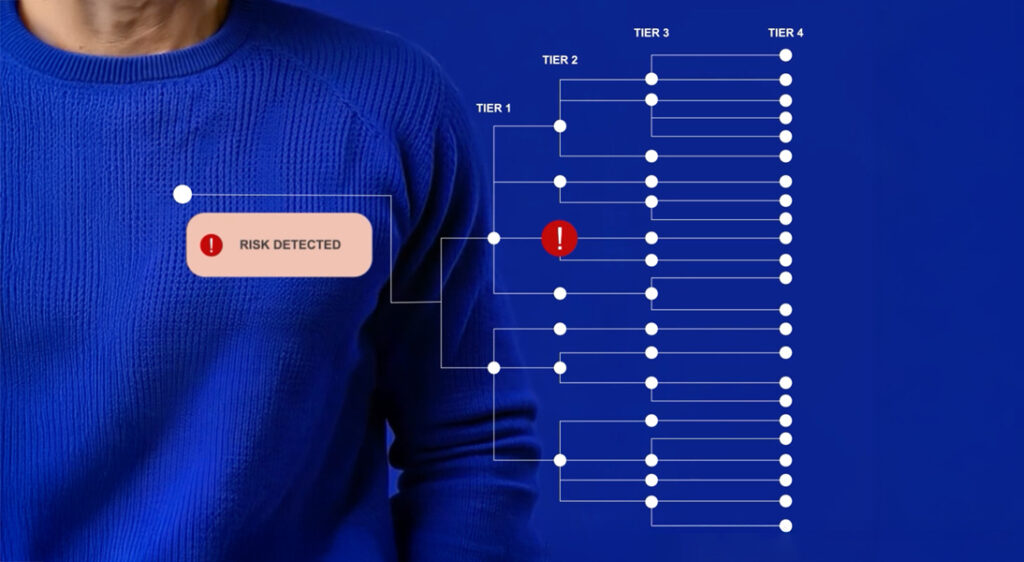
Source: Trust Trace
Ultimately, automation in TPRM shouldn’t be understood as merely task digitization.
The sooner your enterprise moves from ad hoc automation to organization-wide, integrated workflows, the better positioned you’ll be to stay ahead of evolving risk.
Fragmented workflows, outdated data, and a lack of centralized oversight delay procurement while also leaving you with dangerous blind spots across the organization.
Ultimately, third-party risk management can’t be treated as a one-off checkbox or a handoff between departments without clear accountability.
To keep pace with evolving risks, organizations need real-time visibility, integrated systems, and scalable automation.
That’s why so many leaders are now prioritizing modern, tech-enabled TPRM solutions.
Those who invest today will be best positioned to protect operations, safeguard their reputation, and build long-term resilience.