6 Core Stages of the Third Party Risk Management Lifecycle

Key Takeaways:
Running a business isn’t a one-person show.
Most companies rely on a wide network of third parties, from suppliers and contractors to cloud providers and logistics partners. But with those partnerships comes risk.
That’s why third party risk management (TPRM) is a priority for teams handling compliance.
Still, it’s not just about checking vendors once and moving on.
The real value comes from following the entire TPRM lifecycle: a structured process that helps organizations manage risks effectively at every stage of the vendor relationship.
In this article, we’ll walk through the six core stages of that lifecycle and what each one involves.
Regardless of the industry you’re in, you’re bound to be working with a mix of suppliers, contractors, service providers, and strategic partners.
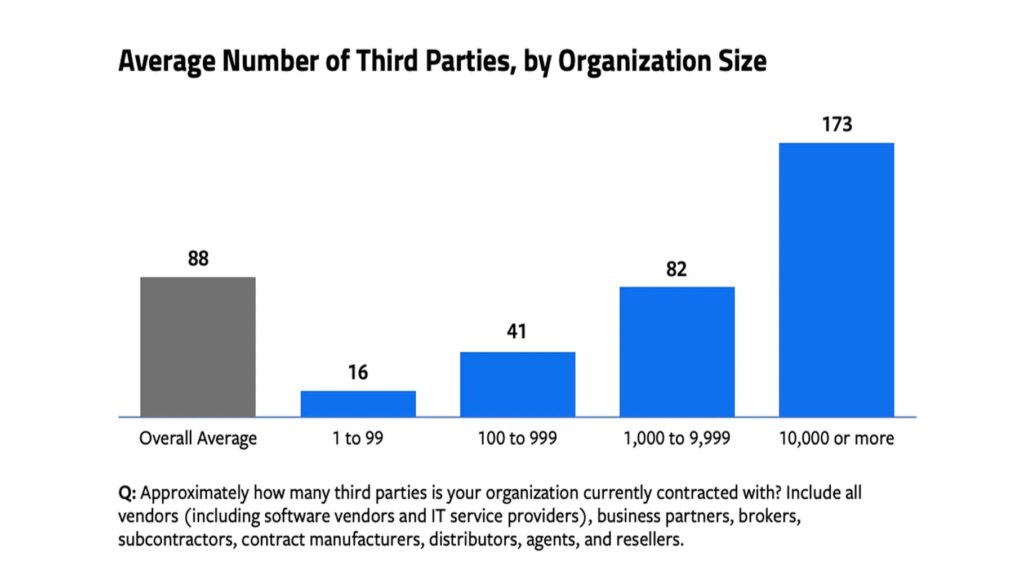
And of course, the bigger a company is, the more third-party relationships it has.
On average, businesses manage 88 third-party relationships, but large enterprises may oversee more than 170.
Source: CyberRisk Alliance
Since you can’t manage what you don’t know, your risk-management efforts should start by creating a complete inventory of every third party your business works with.
This means looking beyond the most obvious suppliers and including less visible, but equally important partners, such as:
And if you’re not sure why visibility of third parties matters, consider the cautionary tale of Target’s 2013 data breach.
During the breach, cybercriminals stole the payment information and personal data of more than 40 million customers.
This happened not by hacking Target directly, but by breaching credentials from one of its HVAC subcontractors.
The consequences were severe, ranging from lawsuits to hundreds of millions in losses.
Target even had to send letters like the one below to notify customers of the breach and provide free identity theft protection.

Source: Columbia University
The takeaway is clear: even with robust internal security and compliance measures, your organization can still be at risk due to the practices of third parties it works with.
That’s why you need to organize vendor information and classify third parties by business function.
That way, you have an overview of your extended network and won’t risk overlooking a hidden link in the chain once you start assessing risks.
Once you know who your third parties are, the next step is to screen them quickly at a high level.
The idea isn’t to dig deep into every detail just yet, though.
Rather, it is to group vendors into low, medium, or high risk so you can see which ones require a closer look later on.
But why does this step matter so much?
It’s because a staggering 98% of organizations have a relationship with a third party that has already been breached.
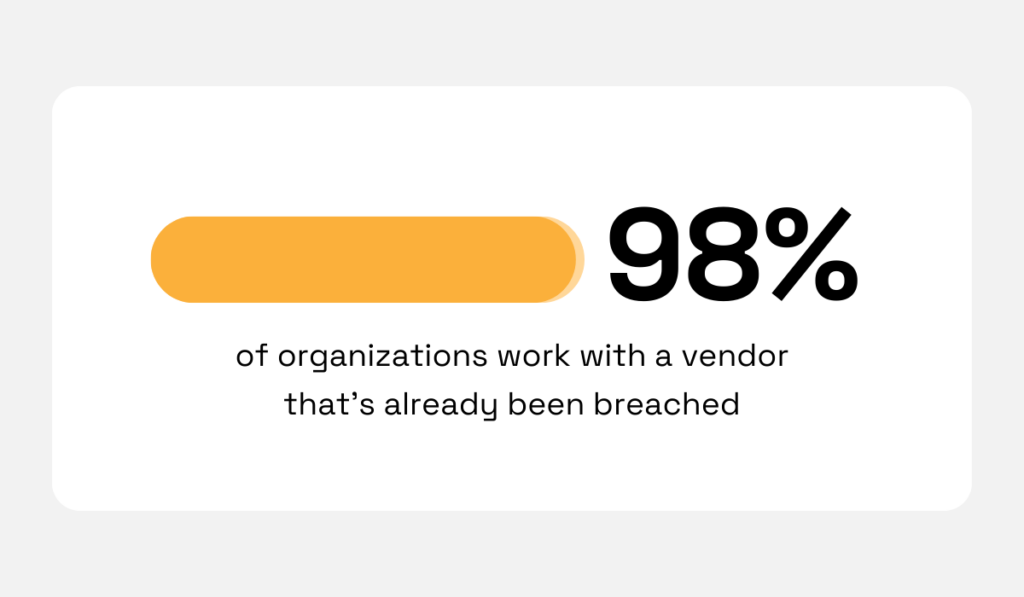
Illustration: Veridion / Data: SecurityScorecard
In other words, chances are that some risk is already in your network, and you want to spot it early.
You can conduct initial risk assessments by combining several methods—questionnaires, background checks, and automated screening tools—with each one offering a different angle on your vendors.
We outlined these three key methods in further detail in the table below.
| Method | What it covers | Use case example |
|---|---|---|
| Questionnaires | Compliance, financial health, and cybersecurity practices | Vendor self-assessment forms |
| Background checks | Sanctions, litigation history, negative press | Screening for legal red flags or corruption |
| Automated screening tools | Risk alerts pulled from different public resources | Flagging vendors with previous breaches or bad press |
From there, you can sort vendors by industry, risk level, location, applicable regulations, operational criticality, and any early warning indicators from news or public records.
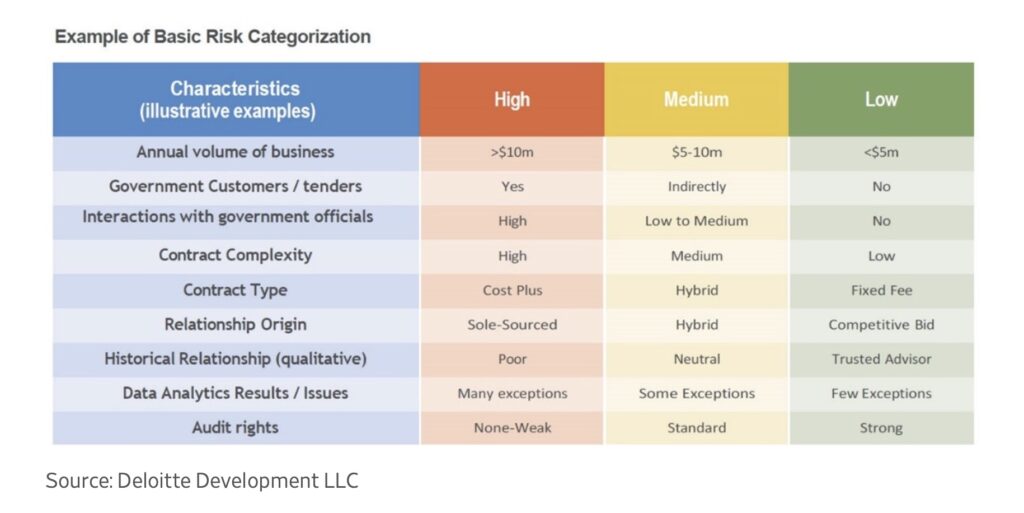
A useful way to think about this process is shown in Deloitte’s risk categorization framework.
Source: Wall Street Journal
As you can see, things like contract type, business volume, or relationship history can signal risk level.
For example, a vendor with a big government contract might be high risk, while a trusted partner on a small fixed-fee contract would likely be low risk.
Most third parties will fall into the low-risk bucket, while a smaller share will land in medium or high.
Those are the ones that move forward into in-depth due diligence.
At the in-depth due diligence stage, you’ll want to go far beyond quick screenings.
In short, this stage is where you find out whether a vendor is not just a potential partner, but a sustainable one.
Here are some of the fundamental areas you should review:
But since checking information on this level takes more time and effort, companies are selective with in-depth due diligence.
Yet, the practice pays off.
According to NAVEX, 72% of companies say their due diligence programs significantly reduce legal, financial, and reputational risks.
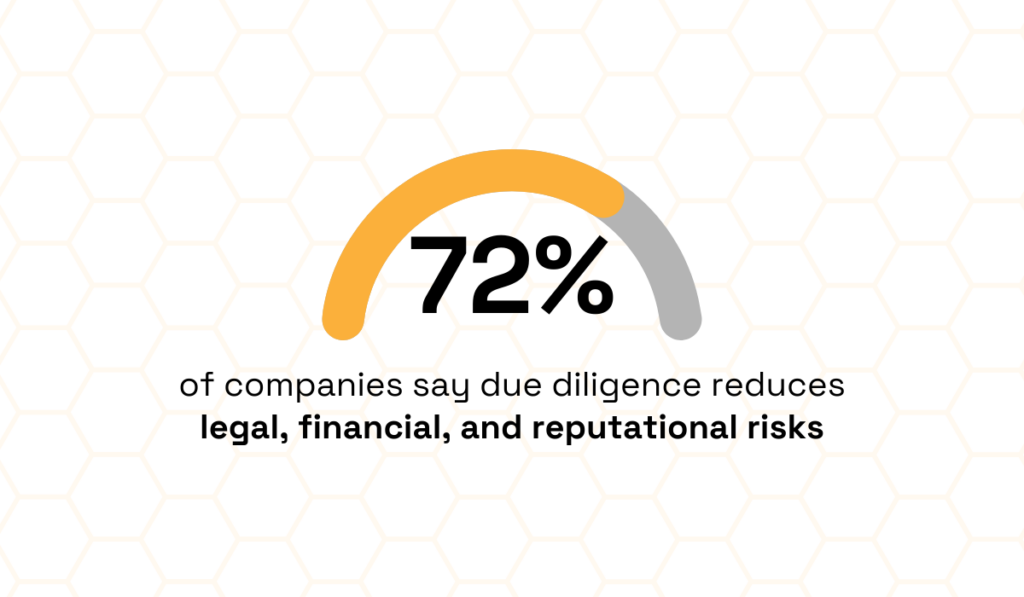
Illustration: Veridion / Data: NAVEX
To make this process both thorough and efficient, some teams use platforms like Veridion.
Veridion provides near real-time supplier intelligence across millions of companies all over the world.
So, instead of relying only on static reports, you could track sudden ownership changes, emerging ESG controversies, or gaps in certifications.
In short, Veridion helps you identify all the risks that are often hard to spot through manual checks alone, and does so in a timely manner.
This is especially useful when it comes to ESG, where risks are often hidden deep in the supply chain.
Veridion’s taxonomy covers a wide range of issues, from labor rights to carbon footprint, helping you catch risks in third parties before they impact your business.
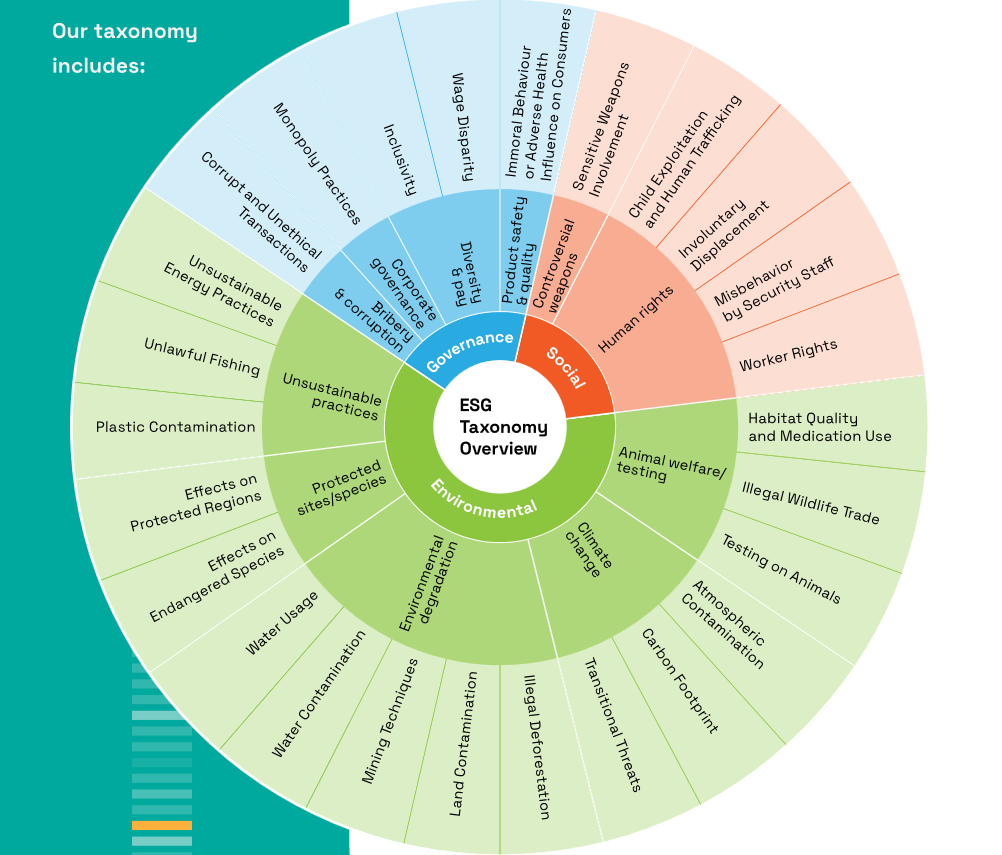
Source: Veridion
Having this kind of structured, weekly-updated data makes it easier to go beyond surface-level checks and understand if your potential partners truly meet your requirements.
So, you’ve confirmed which third parties are trustworthy, and now you feel ready to seal the deal.
But before you sign, you need to make sure that the contract does more than just outline pricing and delivery timelines.
If you fail to build in the right safeguards, you risk financial losses, compliance fines, operational inefficiencies, or even damaged relationships.
Fortunately, if you draft your contracts well, you can protect your organization, define expectations clearly, and build in risk controls that keep both sides accountable.
What you include in the contract will determine how well risks are managed later.
For instance, take a look at this Third Party Risk Management clause, explaining that the supplier is responsible for managing the risks associated with its critical suppliers, and will share risk metrics with the buyer.
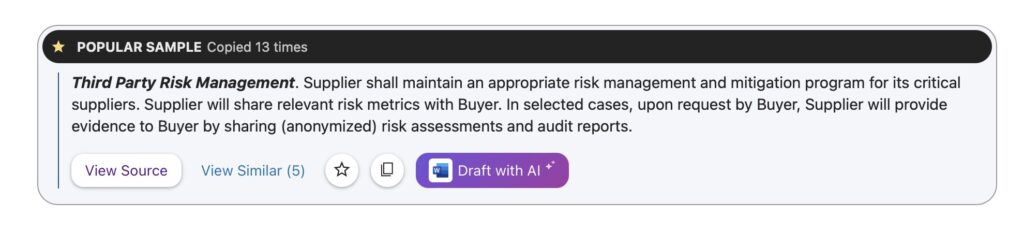
Source: Law Insider
Clauses like that one are a good start, but they don’t go far enough.
Phrases such as “maintain an appropriate risk management program” or “share relevant risk metrics” sound promising, but they leave too much room for interpretation.
What exactly counts as appropriate?
Which metrics are required: financial ratios, ESG indicators, or perhaps cybersecurity audit results?
Without specifics, suppliers can technically comply while still leaving you exposed.
Because of that, strong contracts should go beyond generic language.
Instead of broad commitments, they should set out clear requirements, such as:
When you specify what’s expected, how often, and in what format, it’s much easier to track and enforce compliance.
Your job with TPRM is not done once the contracts are signed.
Why?
Because risk predictions aren’t static. Remember how supply chains that looked stable in 2019, prior to the COVID-19 pandemic, were suddenly disrupted?
That showed how quickly circumstances can change, and how a reliable vendor today can turn into a risk tomorrow.
That’s why you should take continuous risk monitoring seriously.
Unfortunately, this is the area that many organizations struggle with.
According to research, 73% of companies experience a major disruption from a third party within three years.
Another study shows that only 13% continuously monitor vendor security risks.
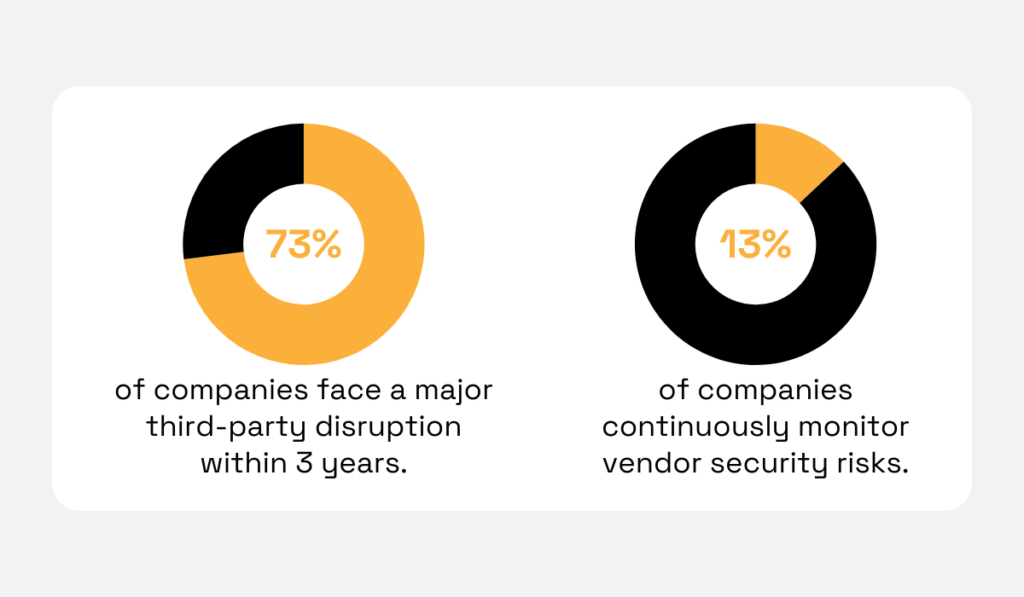
Illustration: Veridion / Data: KPMG and Panorays
The gap between these figures leaves room for unpleasant surprises.
Still, monitoring doesn’t mean tracking every single move a vendor makes.
Instead, it should be about putting systems in place that alert you when something significant changes.
And since you can’t predict every disruption, it helps to set up clear triggers that automatically prompt a risk reassessment when something does change.
These can include:
When these triggers occur, they act as an early warning system.
In other words, they give you time to reassess risks before they turn into financial losses, compliance fines, or reputational damage.
Now, you may feel like you’re babysitting or micromanaging your vendors, but that is not the case.
You’ve invested resources, and you’re simply making sure that what was true at onboarding remains true throughout the entire relationship.
Let’s say that you’ve assessed risks with a vendor, signed a contract, had a relationship that has lasted several years, and now it’s time to part ways.
Even when relationships end, risk management doesn’t.
In fact, a poorly handled offboarding process can leave behind open security gaps, compliance issues, or even legal liabilities.
So, you should close every door you’ve opened during the partnership.
Nick Xiao, Principal at The Hackett Group, agrees.

Illustration: Veridion / Quote: Financier Worldwide
The safest way to handle this is with a structured exit plan that protects your assets and prevents disruptions.
Below, you can find an overview of the key steps in vendor offboarding, why they matter, and how they work in practice:
| Step | Why it’s important | Example |
|---|---|---|
| Recover or delete sensitive data | Prevents data leaks or unauthorized use of confidential information | Collecting all shared financial files, wiping old logins |
| Cut off system and facility access | Stops vendors from getting into your systems or facilities | Removing ex-vendors from email, VPN, or office badges |
| Hand work over smoothly | Keeps business running with new vendors | Switch shipments to another logistics partner |
| Document lessons learned | Helps you avoid the same potential mistakes with future vendors | Note delays or issues and notice them during screening next time |
All in all, if you end the relationship professionally, you stay protected and keep the option of working together again if there’s ever a need for that.
And with that, you’ve completed the final stage of the third party risk management lifecycle.
TPRM is not a one-time task, but an ongoing cycle that protects your business at every stage of the relationship with vendors.
When you pay attention to each stage, from identifying vendors to managing a smooth exit, you set yourself up for fewer disruptions and a more secure future.
The key idea is simple:
Risks will always change, but with a solid TPRM lifecycle in place, you’ll be ready to handle them.