5 Mistakes to Avoid when Managing Third Party Risk


Key Takeaways:
Modern enterprises run on vast networks of third-party partnerships, which is why 90% of organizations are now investing in third-party risk management (TPRM) programs.
But investment alone won’t guarantee impact.
This article unpacks five common mistakes in vendor risk management.
Looking to replace gut-driven decisions with structured practices and smarter tools that keep risks visible, measurable, and under control?
Let’s dive right in.
Lacking a centralized vendor inventory harms workflows and creates data silos—two weaknesses that are particularly dangerous in risk management.
If procurement, compliance, and security teams are all maintaining their own lists, you’re bound to end up with duplicate records and poorly managed third-party relationships.
According to AuditBoard’s Connected Risk Report, 86% of professionals believe data silos of this kind negatively impact risk management.
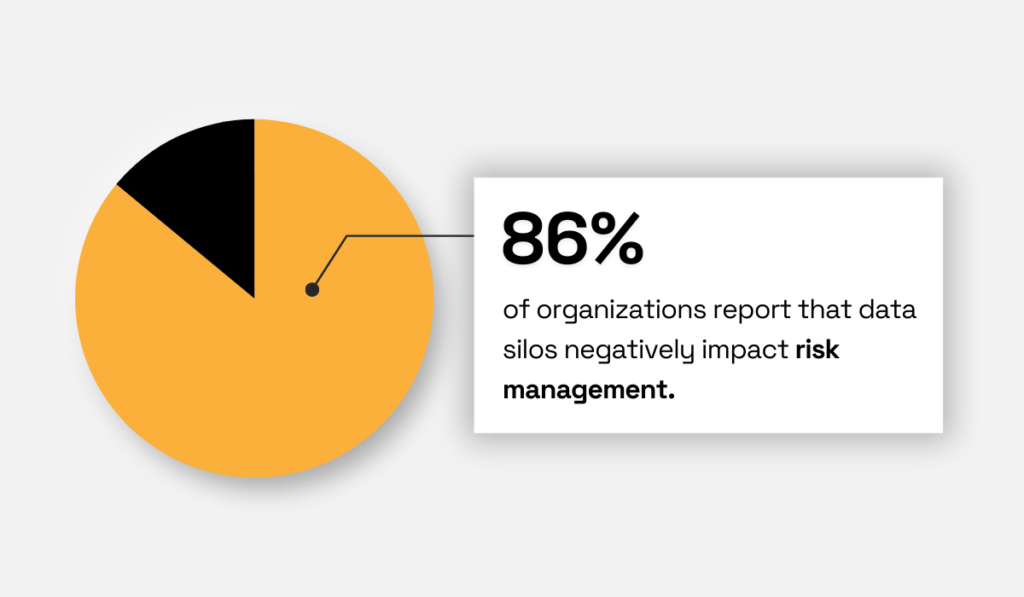
Illustration: Veridion / Data: AuditBoard
But what do these challenges look like in practice?
Consider Omaha’s new airport terminal.
Despite wage increases and incentives, the airport’s main food & beverage vendor is struggling to recruit enough staff, leaving passengers with long waits and a poor overall experience.

Source: Flatwater Free Press
Now, an airport’s closed environment may not look like a Fortune 500 enterprise, but vendor management blind spots still led to severe operational headaches.
For large enterprises managing thousands of third parties, the stakes are far higher, as is the ripple effect.
Centralization is the simplest way to start breaking down these silos.
A complete vendor inventory is the first building block of any TPRM program that:
Without it, true supply chain visibility is impossible.
For starters, consolidate all vendor records, i.e., procurement contracts, finance systems, and onboarding spreadsheets, into a single repository.
One function should be accountable for keeping it updated. Afterwards, you can integrate cyber risk ratings, financial health checks, ESG scores, and other risk streams into the same central hub.
Remember, your goal is to have a living system, not a static list.
As EY’s Consulting Partner and Risk Leader, Netta Nyholm, puts it, the organizations pulling ahead are those that succeed in including different risk lenses and working together.

Illustration: Veridion / Quote: EY
The benefits extend beyond visibility.
EY survey respondents highlighted more complete and accurate data (45%) and better risk insights during decision-making (44%) as the top advantages of a centralized approach.
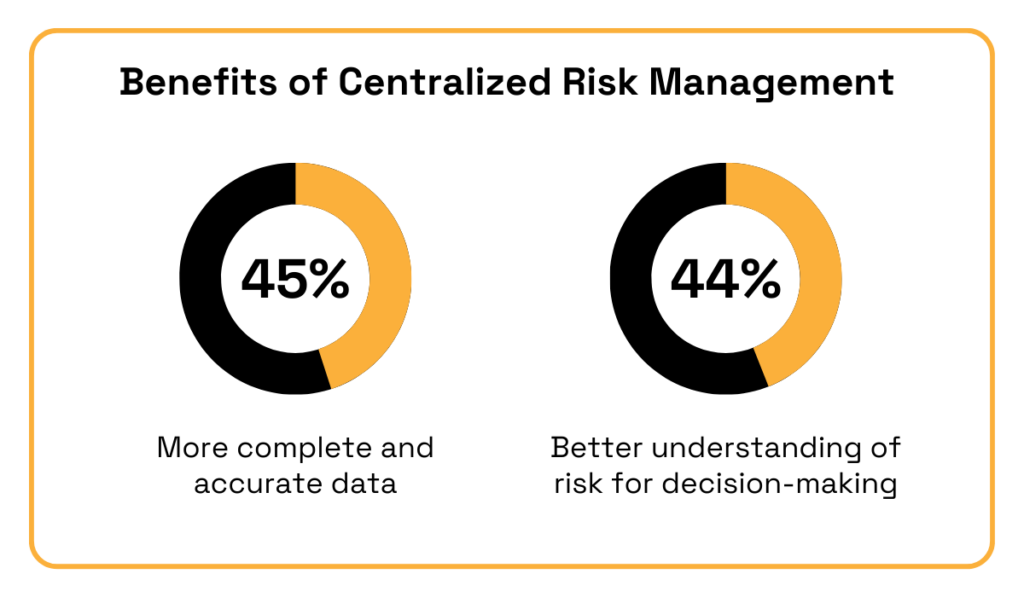
Illustration: Veridion / Data: EY
It takes effort to build, but the payoff comes quickly.
A central vendor inventory eliminates duplicates, aligns business functions, and lays the foundation for mature third-party risk management.
Without this inventory, you’re missing data, but also eroding your ability to see and act on risk before it disrupts your business.
Neglecting continuous monitoring leaves your organization exposed to vulnerabilities you won’t be able to see until it’s too late.
But while most enterprises understand the importance of risk management, few are embedding monitoring into day-to-day workflows.
According to Supply Wisdom, only 14% of procurement and 13% of supplier management professionals use continuous monitoring tools and solutions to assess suppliers.
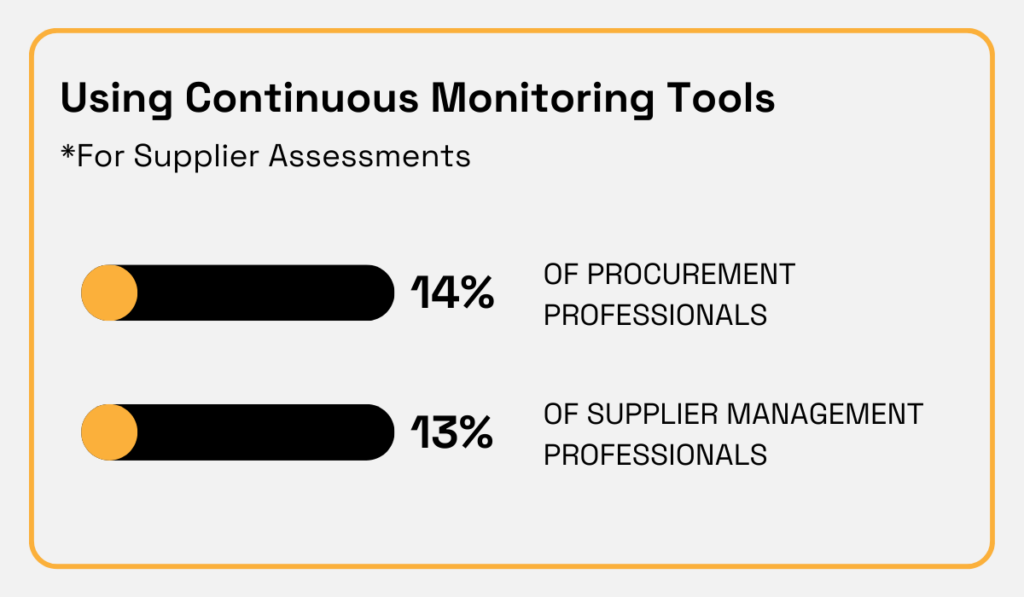
Illustration: Veridion / Data: Supply Wisdom
That gap signals a major underutilization of technology in risk assessment, exposing your organization to entirely avoidable scenarios.
As Cherry Hill Advisory CEO Mike Levy explains, the lack of awareness about incoming issues and slow response time means that minor issues can quickly snowball into major disruptions.

Illustration: Veridion / Quote: SC World
Levy emphasizes the cyber angle, but the risks extend well beyond that.
Take, for instance, the recent example of how palm oil suppliers to giants like Kellogg’s, Nestlé, and Colgate became linked to egregious deforestation practices in Peru.
Source: ESG News
Even large brands that are expected to have robust compliance functions failed to continuously vet their suppliers’ practices, leading to increased regulatory scrutiny and consumer backlash.
The truth is that risks evolve faster than traditional assessments can keep up.
The only way to avoid this is by leveraging the right platforms that deliver seamless monitoring experiences.
Enter Veridion.
What sets Veridion’s AI-powered data intelligence platform apart is its ability to update and enrich supplier data continuously at a global scale.
The platform covers more than 134 million companies across 250 countries, with millions of records refreshed weekly, ensuring visibility as risks emerge.
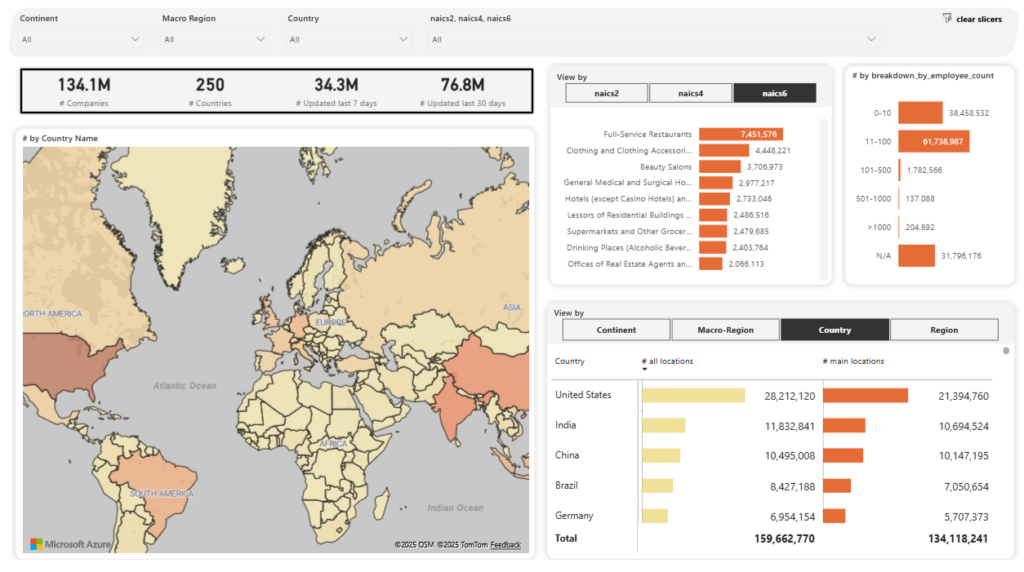
Source: Veridion
You can configure data enrichment types based on your risk profile, automate updates, and filter out irrelevant noise so only the most pressing alerts surface.
The interface itself is intuitive, supporting natural language to make monitoring as easy and insights as actionable as possible.
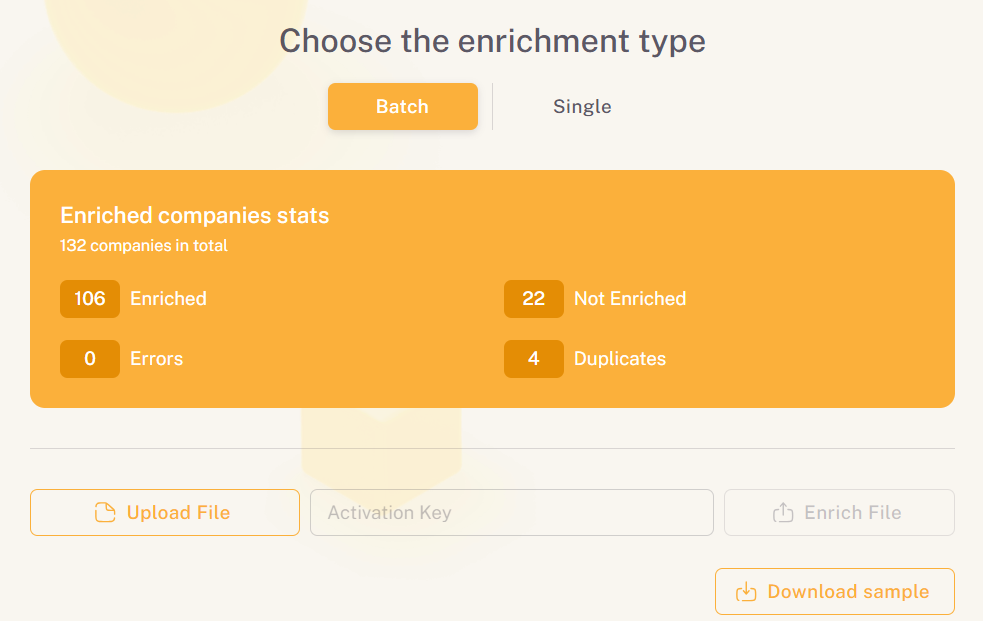
Source: Veridion
Moreover, legal identifiers, ESG indicators, sustainability scores, and operational data points can all be layered into a single dashboard, giving you a multidimensional view of supplier health.
Here’s just a glimpse of Veridion’s TPRM-specific data points.
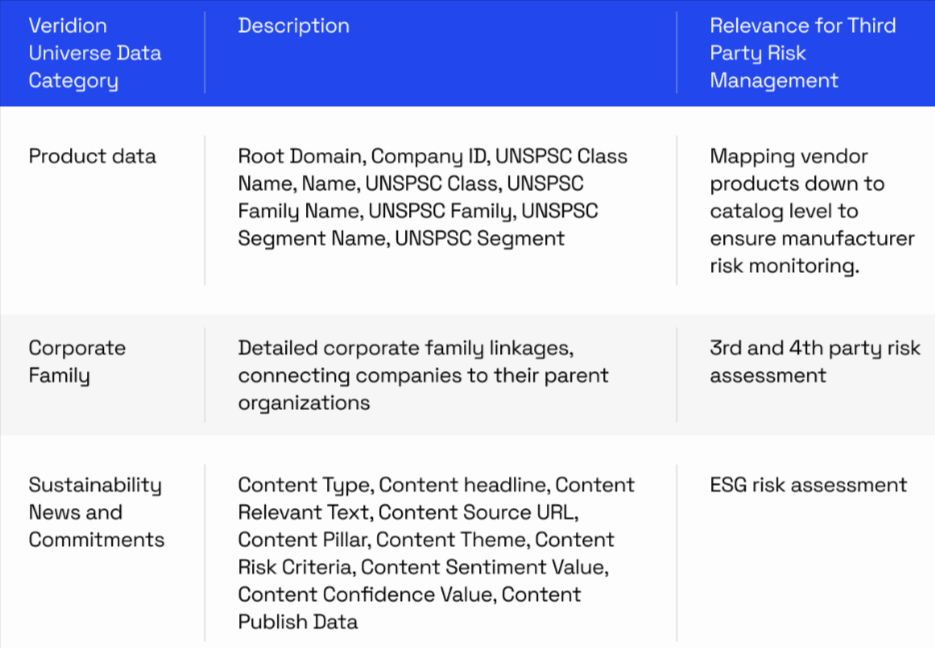
Source: Veridion
Staying informed about regulatory, financial, and ESG-related changes across your supplier base translates to a proactive approach that reduces risk exposure over time.
The bottom line is simple: when monitoring is automated and intuitive, you don’t need to “remember” to do it, and risks can be contained before they spiral.
Failing to document third-party risk management activities inevitably shows up as missing or outdated records, derailing audits, slowing onboarding, and creating confusion.
Worse, it leaves organizations unable to prove compliance or trace how key vendor decisions were made.
The importance of documentation is most visible in incident response.
When something goes wrong, whether it’s a data breach, service disruption, or regulatory inquiry, logs of past issues provide the baseline for analysis and prevention.
As explained by Andrew Tabona, Senior Vice President of Cybersecurity at a Fortune 500 company, effective incident response boils down to preparation and learning how to prevent future issues.

Illustration: Veridion / Quote: Cloud Security Podcast on YouTube
Consider a hypothetical scenario where a supplier delivers faulty components that lead to repeated service disruptions.
Without an incident log, the issue can’t be tied back to specific dates, communications, or remediation attempts.
And in case of a regulatory investigation, leadership has no clear trail to show how the risk was tracked or addressed, which is likely to lead to fines, if not reputational damage.
Research confirms that this lack of preparedness is widespread.
An Economist Impact survey of 560 C-level executives across Asia-Pacific found that engagement with internal stakeholders is dwarfed by other risk management strategies.
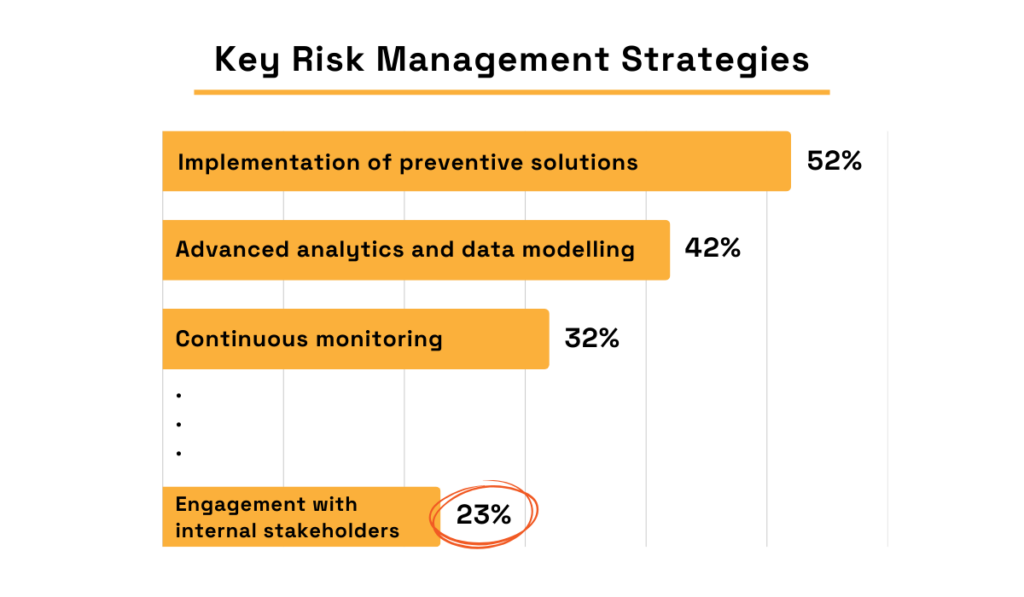
Illustration: Veridion / Data: Economist Impact
Since it’s essential for defining and enforcing documentation practices, a lack of internal engagement often manifests as fragmented records.
Think contracts that are tracked by legal but not linked to procurement data, performance reviews stored in spreadsheets, and compliance reports scattered across email threads.
To prevent this, organizations need processes that support documentation and internal reporting across the full vendor lifecycle, including:
It’s helpful to think of it as standardizing processes across five distinct TPRM areas.
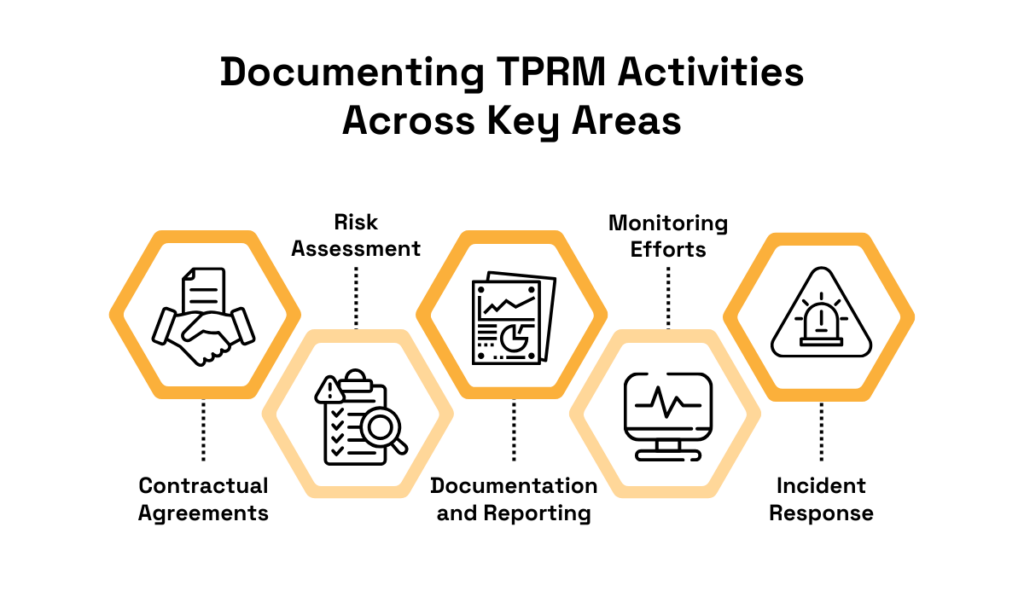
Source: Veridion
Specialized tools help streamline these efforts further.
For instance, UpGuard employs AI to automate compliance management and keep the relevant data at your fingertips.
Meanwhile, SecurityScorecard provides features like the “Evidence Locker” to make documentation shareable and audit-ready, with easily accessible activity logs.
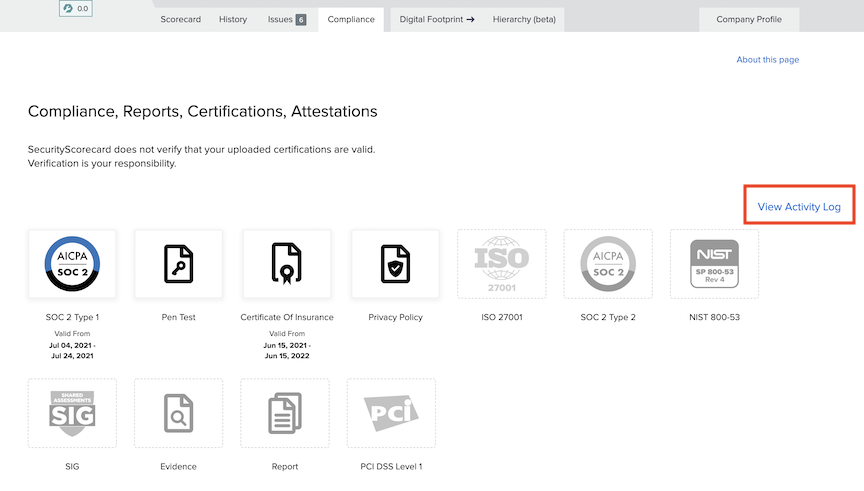
Source: Security Scorecard
With robust records and tools in place, you’ll be prepared for audits and emerging incidents, as well as able to continuously improve your TPRM framework.
Vendors often handle sensitive data on behalf of the organizations they serve, but too many enterprises still fail to validate their security practices or enforce protections in contracts.
With companies exposed to breaches and fines, the consequences are hard to ignore.
According to the Cyber GRX report, while 64.3% of executives treat cybersecurity as a strategic imperative, 35.7% still see it as a purely technical issue.
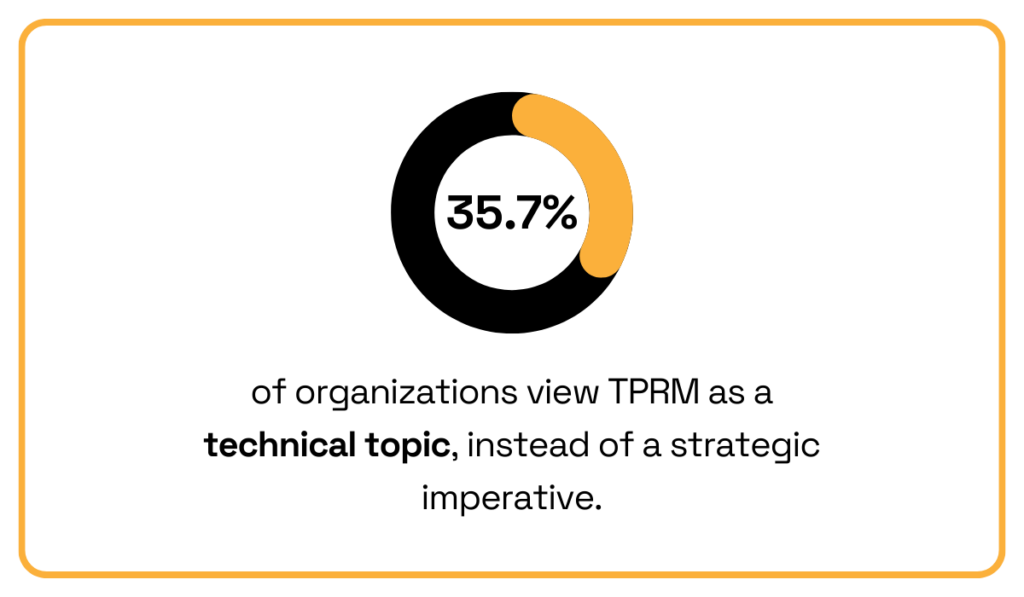
Illustration: Veridion / Data: Cyber GRX
That disconnect helps explain why 61.7% of surveyed organizations reported at least one cybersecurity incident in the span of one year.
Audiboard’s CTO, Haibei Wang, stresses that one of the greatest challenges in TPRM is protecting data even as companies adopt new systems and approaches.

Illustration: Veridion / Quote: SC World
If security measures don’t evolve in parallel, gaps open up fast.
The Interserve case shows just how costly this oversight can be. The UK outsourcing giant was fined £4.4 million after hackers gained access to personal information on 113,000 employees.
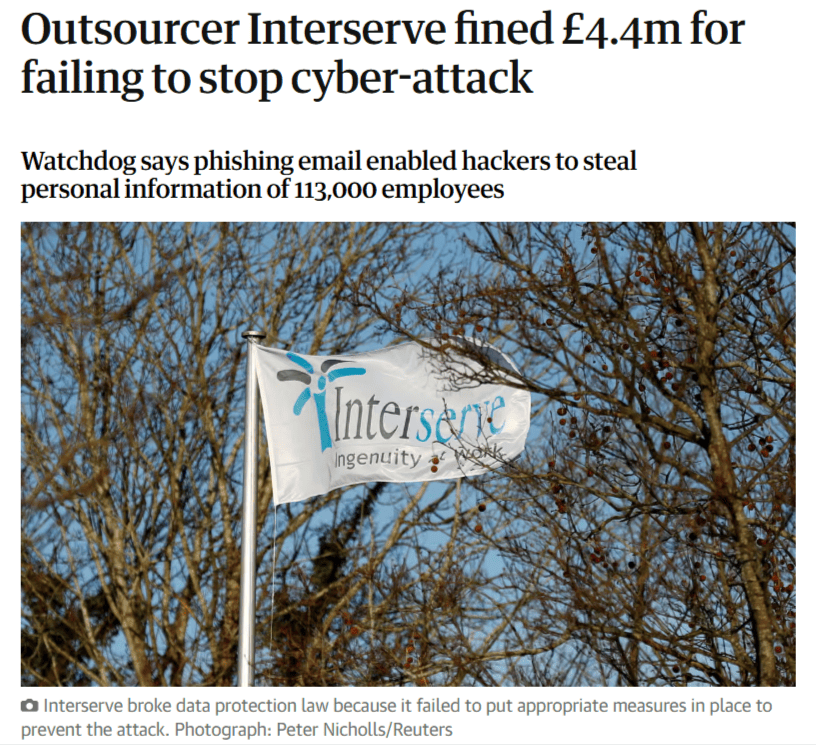
Source: The Guardian
The breach started with a phishing email that bypassed the firm’s defenses.
Since the subsequent anti-virus alert was ignored, attackers succeeded in compromising 283 systems, 16 accounts, and even uninstalling Interserve’s anti-virus software.
Needless to say, the stolen employee data triggered regulatory penalties but also long-lasting reputational damage.
So how can enterprise organizations reduce exposure and enhance data security?
Access management is one cornerstone of data security.
After the initial onboarding and thorough vetting, Role-Based Access Control (RBAC) ensures only authorized users can view or modify sensitive data.
Reviewing user permissions and checking audit trails will help you detect any anomalies on time.
Finally, having a vendor exit strategy ensures your organization’s data, systems, and business operations are secure after the relationship ends.
Here’s what you should keep in mind:
| Terminate access | Revoke access to all user accounts and system credentials. |
| Retrieve sensitive data and assets | Require vendors to return or securely delete all sensitive data. |
| Conduct an exit security review | Perform a final security audit. |
| Update contracts and SLAs | Review and update all outstanding legal documentation. |
| Perform residual risk monitoring | Continue monitoring for any residual risks. |
Keep in mind that while departure strategies are the norm for high-dependency vendors, especially when software-related, they don’t need to be so thorough for all your third parties.
Ultimately, treating vendor data security as a strategic rather than technical matter ensures you stay compliant, protect sensitive information, and avoid becoming the next cautionary headline.
Monitoring third-party risk without using clear KPIs erodes the efficiency and effectiveness of your entire program.
Simply put, no metrics means you end up relying on a gut feeling instead of evidence.
As Chris Gida, Former Sr. Manager of Technology Audit and Compliance at Asurion, notes, this approach leaves organizations in a vulnerable position when it comes to vendor risk.

Illustration: Veridion / Quote: Cyber Sierra
Operating on instinct may work in isolated cases, but at enterprise scale, it leads to inefficiency, poor prioritization, and exposure to risks that should have been flagged long before they escalated.
Consider the much-talked-about oversight issues between Boeing and its key supplier, Spirit AeroSystems.
In 2024–2025, repeated quality failures led to production delays, delivery disruptions, and intense regulatory scrutiny, leading to the worst year since the pandemic.
Source: BBC
Boeing has since invested in stricter controls and technology to detect supply chain and production issues earlier, but it was a costly lesson.
But the lesson for any enterprise is clear: without defined metrics, you only discover problems once they’ve already become costly.
So how do you ensure you’re tracking the right data?
Start by linking metrics to the goals of your TPRM program.
The aforementioned Cyber GRX report shows that most organizations emphasize threat intelligence and monitoring (40.9%), while others focus on understanding risks through threat data (38.3%) or ensuring compliance (20.8%).
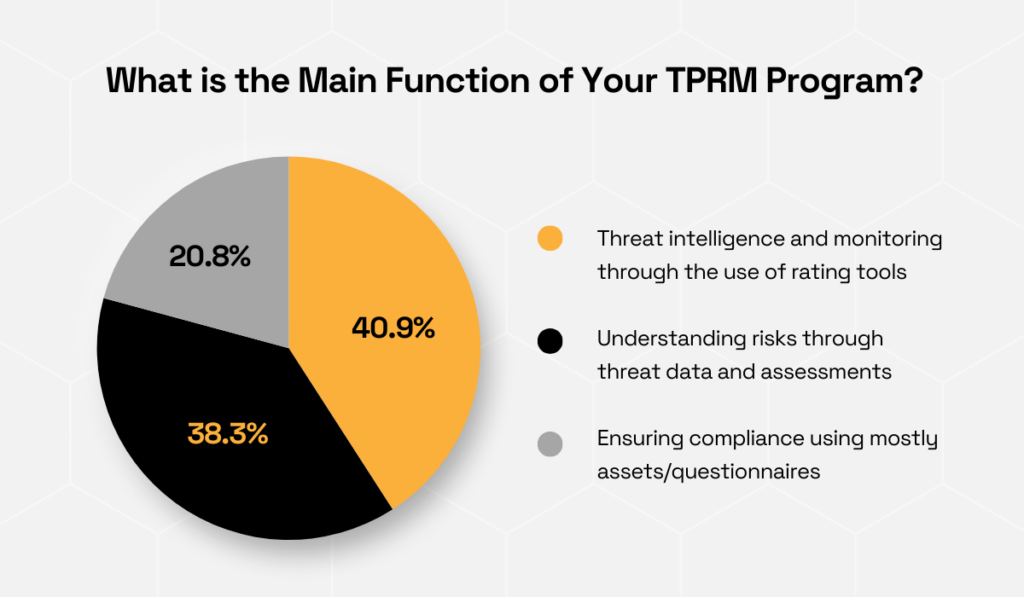
Illustration: Veridion / Data: Cyber GRX
To operationalize this, you can follow three steps:
Some essential TPRM metrics include financial health, performance data, security posture, ESG compliance, and concentration risk.
For example, tracking vendor financial health through credit ratings, liquidity ratios, or payment history helps anticipate bankruptcies or instability before they threaten supply continuity.
Likewise, measuring concentration risk ensures you’re not over-reliant on a single supplier or region, where one disruption could create a dangerous ripple effect.
These types of metrics are much more than abstract scoring, giving procurement and compliance leaders the ability to spot and address vulnerabilities early.
Remember, by defining and tracking the right metrics, you transform TPRM from a reactive checklist into a proactive framework that both drives and safeguards your operations.
Third-party risks can never be fully eliminated—only contained.
TPRM mistakes are similar.
Once you can track and understand them, you’ll be able to act before they trigger repeated disruptions that erode company profit and reputation.
Naturally, mistakes like shallow due diligence, weak monitoring, or neglected KPIs will always invite problems and must be addressed at the source. As we’ve established today, the key to doing so lies in disciplined practices and modern technology.
By refining your program and leveraging tools that surface early warnings, you are sure to reduce third-party risk and create a foundation for long-term business success.