Types of Software That Help Prevent Vendor Fraud


Key Takeaways:
Vendor fraud begins with overlooked data, loose approvals, and fragmented systems.
It’s never just one bad transaction, and as vendor ecosystems grow, so do the opportunities for manipulation.
This article breaks down five types of software designed to detect and prevent fraud at every stage of the vendor lifecycle.
Ready to eliminate key gaps in your company’s oversight? Let’s delve into it.
Vendor management systems (VMS) centralize all vendor information, contracts, and transactions into a single source of truth essential for procurement and finance teams.
By consolidating data and automating certain processes, these platforms help eliminate the blind spots that typically enable duplicate or fraudulent vendor accounts.
With a unified database, it’s far easier to identify inconsistencies, such as:
At their core, VMS platforms automate vendor onboarding, approval, and performance monitoring workflows.
As illustrated with HICX’s platform, key requirements can be determined with simple color-coded tagging systems to ensure every supplier goes through consistent validation steps before activation.
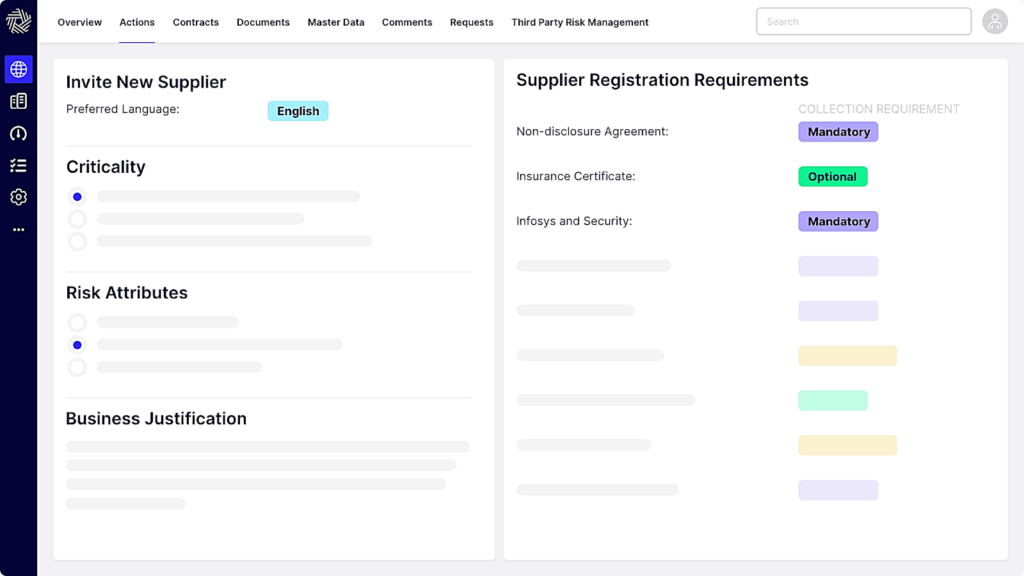
Source: HICX
In terms of specialization, solutions like SAP Fieldglass, Oracle Procurement Cloud, and Precoro offer slightly different strengths within this landscape.
SAP Fieldglass, for instance, specializes in managing large contingent workforces and all external service providers, two areas with a high risk of fraud due to multiple intermediaries and payment structures.
You can easily access each profile’s audit trail and monitor supplier spend patterns to surface irregularities before payments are processed.
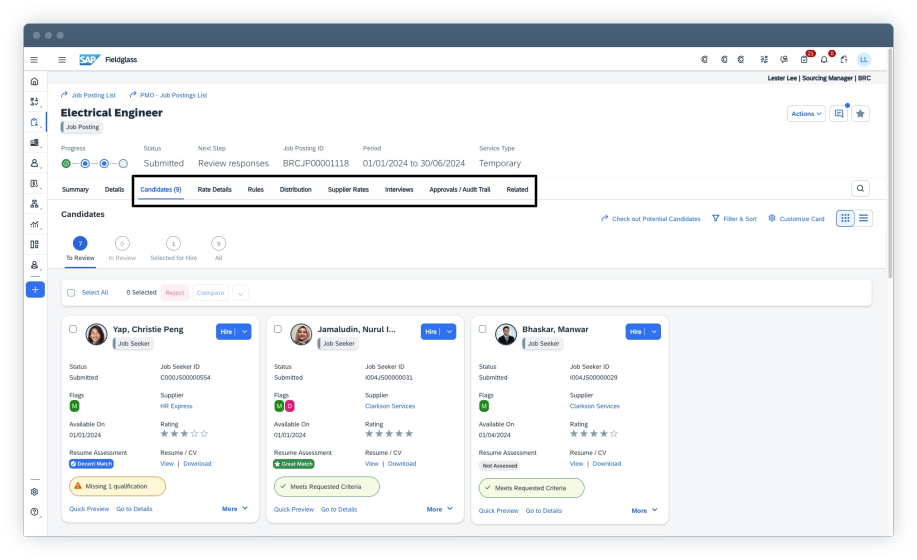
Source: SAP
Oracle Procurement Cloud takes a more integrated approach by combining supplier qualification, sourcing, and contract management in one ecosystem.
With a detailed list of qualification requirements, procurement and compliance teams can easily access detailed entries on qualification requirements and assessments, and both spot and act on any inconsistencies.
Source: Oracle Applications Cloud Tutorial on YouTube
By preventing fraudulent vendors from even entering the system, the risk of fraud is almost neutralized.
Meanwhile, Precoro stands out among mid-market solutions with its customizable workflow automation.
Defining specific approval routes also reduces the risk of manual overrides, which is a subtle but common weakness in smaller procurement setups.
Source: Precoro
When paired with built-in reporting features, this level of control allows organizations to continuously audit supplier performance and identify any behavioral anomalies, such as sudden invoice spikes or inconsistent pricing.
Ultimately, a well-implemented VMS supports consistency, traceability, and transparency, making it easier to spot and proactively address any fraudulent intent.
Spend analysis software provides a detailed breakdown of procurement and payment data to identify abnormal spending trends and potential fraud indicators overlooked by traditional systems.
While these tools are typically lauded for uncovering cost-saving opportunities, the software’s deeper value lies in its ability to surface irregularities.
This includes duplicate invoices, off-contract purchases, and inconsistent billing amounts.
By structuring spend data into categories, vendors, and time frames, teams can quickly see the signs pointing to possible vendor fraud and do so before they turn into costly incidents.
Holly Younggren, Microsoft’s Group Global Process Manager, summarized the effectiveness and key benefits of these systems perfectly:

Illustration: Veridion / Quote: EY
Younggren was commenting on the partnership between EY and Microsoft, which enabled the tech juggernaut to improve its enterprise-wide spend management.
In this case study, the system’s ability to go beyond descriptive reporting and detect patterns at scale emerged as the key differentiator.
But let’s take a step back and outline a couple of key points that define modern spend analysis tools, enabling you to spot outliers, such as vendors whose payment volume doesn’t match their contract size or service scope.
Firstly, platforms like Coupa Spend Analysis, IBM Cognos Analytics, and Zycus iAnalyze enable users to instantly visualize spend distribution across suppliers and categories, filtering by business unit, geography, or approval chain.
IBM Cognos Analytics integrates financial, procurement, and compliance data streams into a unified reporting layer, with real-time dashboards simplifying the assessment of high-risk segments.
This structured view dramatically reduces the manual effort required to investigate suspicious vendors or shadow suppliers operating outside official procurement channels.
Source: Octane Solutions
By using the new intent-driven modeling feature, IBM Cognos Analytics users can type in keywords to generate a data model for a new data set and build custom visualizations.
Meanwhile, dedicated fraud detection tools, such as Coupa’s SpendGuard, empower users to stay in the loop through instant alerts, as well as customize workflows with simple drag-and-drop functionality.
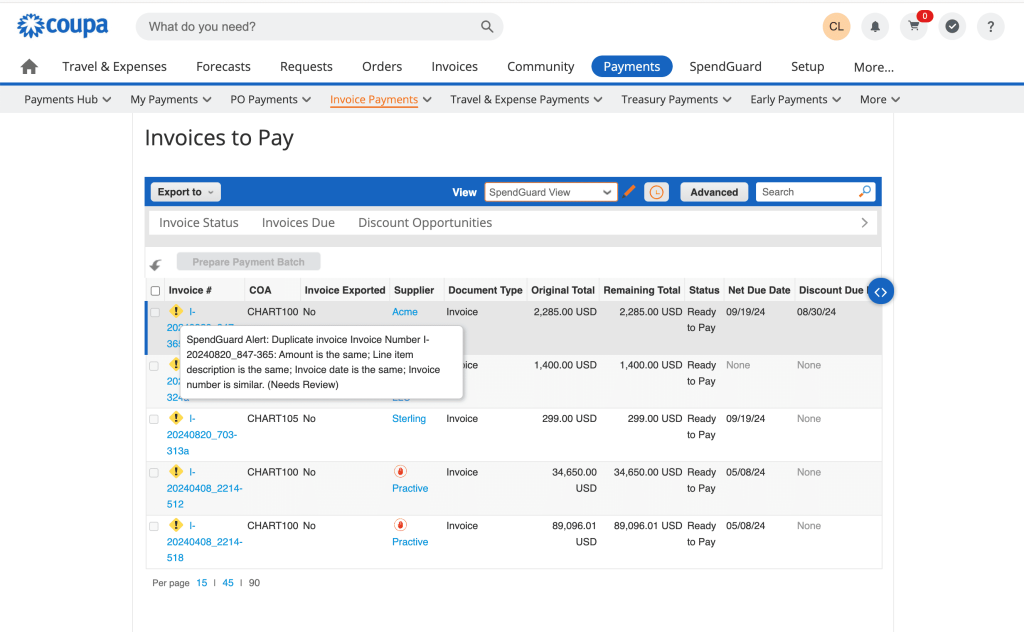
Source: Coupa
Most importantly, admins can implement plenty of guardrails to ensure these workflows can’t be changed without prior approval or admin credentials.
To further enhance risk mitigation, consider using platforms that provide AI-driven recommendations on spend management and deliver predictive insights to help you anticipate key risks ahead of time.
Ultimately, spend analysis tools uncover inefficiencies, but also increase transparency, making it easier to spot and question patterns that indicate financial misconduct.
With these early-warning systems, you will prevent vendor fraud while ensuring that every dollar you spend stands up to scrutiny.
Vendor data verification platforms ensure that every supplier your company works with is legitimate, compliant, and accurately represented.
In other words, these tools cross-check company registration details, contact information, tax IDs, and operational status against authoritative sources, minimizing the risk of onboarding fake or inactive vendors.
The importance of this is even more evident when we look at the state of vendor data quality.
According to Transparent’s database of 9.6 million vendors globally, enterprises are missing critical vendor data points, from VAT and bank account numbers to physical addresses.

Illustration: Veridion / Data: Transparent
In a procurement environment, where vendor impersonation and falsified records are common sources of fraud, maintaining verified vendor data is one of the most effective defenses available.
Our vendor data verification platform, Veridion, provides the most comprehensive and continuously refreshed datasets in this space.
The AI-powered platform gives you access to 136+ million verified company profiles, elusive SMBs included, with weekly updates that capture any changes in business status, ownership, or activity.
Source: Veridion
Considering fraudsters often exploit time gaps between data updates to create short-lived shell entities that can slip through initial checks, this data freshness is critical.
Veridion’s real-time updates ensure that those windows of opportunity disappear.
New data points are incorporated as soon as they appear, ensuring no vendor record stays outdated for long.
Of course, the breadth and depth of datasets are equally important.
From small regional suppliers to global distributors, each entity profile covers over 320 data points, covering all the key vendor authenticity factors, such as industry classification, ownership structure, and contact channels.
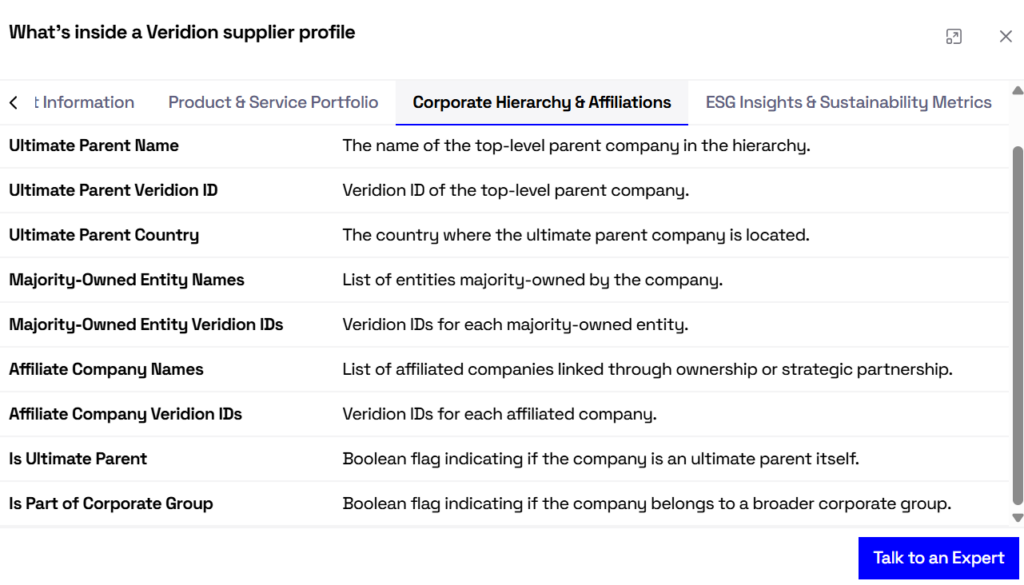
Source: Veridion
Verification alone, however, isn’t enough. Organizations need an efficient way to operationalize verified data.
That’s where Veridion’s data enrichment capabilities come in.
The platform integrates directly with ERP and procurement systems through APIs and enables batch updates to automatically update records and enrich existing datasets.
It also ensures that, when new suppliers are added, they’re automatically checked against the latest verified records rather than static spreadsheets or outdated registries.
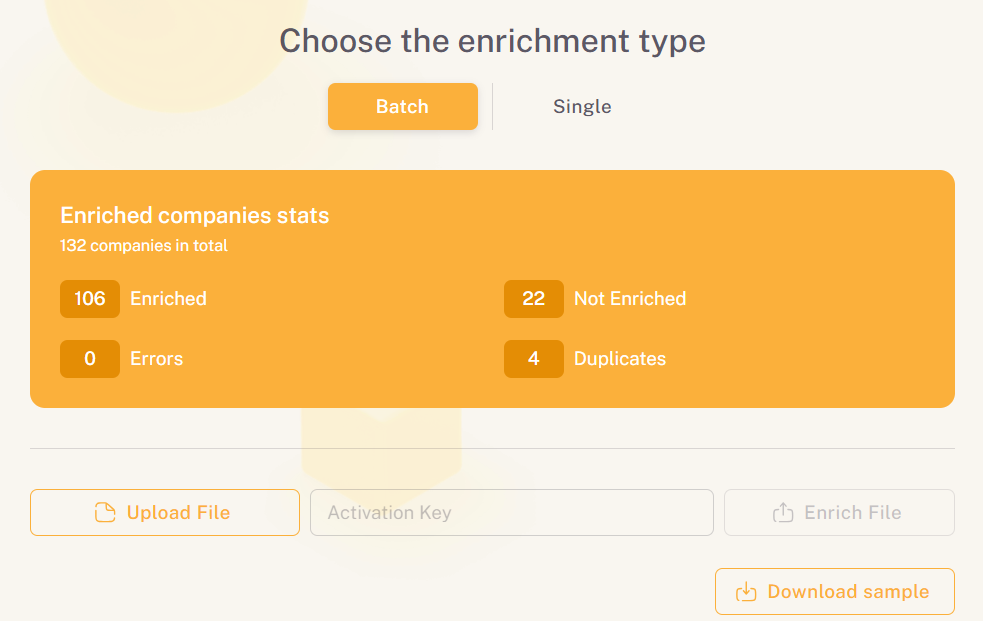
Source: Veridion
This steady flow of data eliminates the need for manual verification while embedding trust directly into your vendor onboarding process.
For procurement and compliance leaders, the implications are clear: vendor fraud prevention requires advanced analytics, but it starts with verified data.
Building your vendor base on real-time, continuously validated company information helps you reduce fraud risk while strengthening every aspect of vendor management, from onboarding to spend analysis.
Fraud detection tools specialize in detecting a variety of risk and fraud indicators that other systems may only skim over.
While vendor management or spend analysis platforms can flag duplicate invoices or mismatched payments, dedicated fraud detection software specializes in real-time anomaly detection.
This translates to continuously scanning:
Research indicates why this is so important.
According to Medius’ 2022 report, U.S. companies lost an average of $300,000 per business in one year to fraudulent invoices, and one in four finance professionals can’t even estimate their exposure to invoice fraud.

Illustration: Veridion / Data: Medius
This gap in awareness underscores the value of proactive, automated systems built to detect fraud as it happens.
Unlike tools that analyze spend data in batches, fraud detection platforms operate on high-frequency alerting and adaptive learning models, instantly notifying users when risk thresholds are exceeded.
This allows organizations to react to issues before invoices are paid or funds are transferred.
Take Sumsub’s verification platform, for example.
The platform detects suspicious words, phrases, and instructions from watchlists within your Transaction Monitoring system, flagging repeated payment attempts or inconsistent approval timings across multiple systems at once.
Behavioral patterns are fused with historical data to generate an overall anomaly score and indicate whether there’s a need for additional scrutiny.

Source: Sumsub
Moreover, Sumsub is equipped with 300+ pre-built rules customized for different industries like fintech, traditional finance, crypto, e-commerce, and more, making it easier to adjust it to your setting.
Actimize, on the other hand, specializes in financial services applications and provides cross-channel visibility.
The platform delivers detailed risk profiles with features such as enterprise fraud investigations that streamline collaboration between teams in case of suspicious activity.
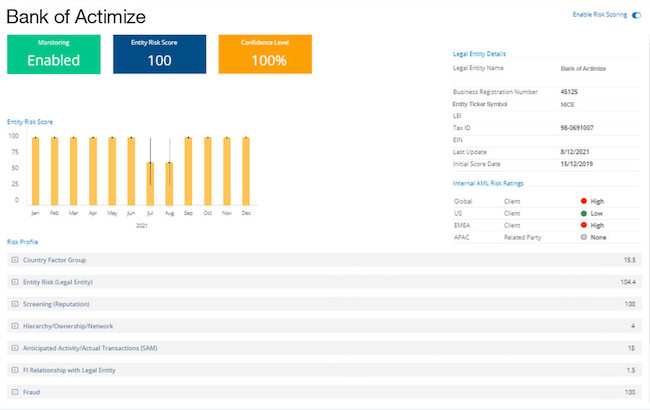
Source: Help Net Security
These capabilities are especially relevant for collusion cases, where fraudulent actions may span departments or even partner organizations.
Fraud.net prioritizes a similar collaborative approach by combining AI-driven scoring with a shared intelligence network.
If a fraud tactic, such as using duplicate vendors, is identified by one client, that knowledge feeds into the platform’s global model, helping others block the same attempt before it reaches them.
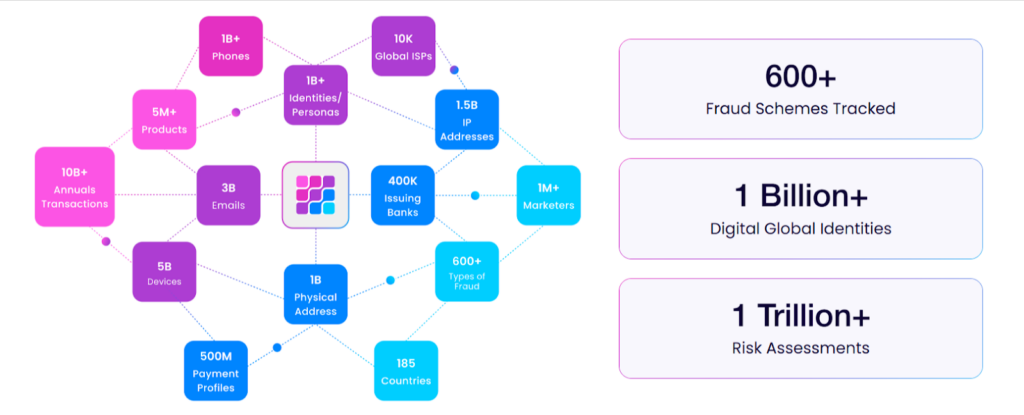
Source: Fraud.net
Together, these solutions offer the speed and precision that embedded modules can’t match.
By uniting real-time alerts, pattern learning, and shared intelligence, fraud detection tools transform reactive auditing into continuous protection, empowering finance and procurement teams to stop vendor fraud before it leaves the ledger.
Finally, contract management software helps you close one of the most overlooked gaps in vendor fraud prevention: the contract lifecycle itself.
While spend and fraud detection tools analyze transactions, contract management solutions ensure that agreements governing those transactions remain transparent, compliant, and tamper-proof.
In other words, you’re saying goodbye to:
By centralizing contract creation, negotiation, approval, and renewal, these platforms enable you to maintain a single source of truth for every vendor relationship.
But of course, modern systems like Ironclad, Icertis, and ContractWorks go beyond document storage to provide real-time visibility into contractual obligations and financial exposure.
This is done through automated approval workflows, better version control, and application of user-level permissions, so even minor edits are logged and auditable.
For example, Ironclad’s Workflow Designer enables users to define every step of a contract’s journey using the now-standardized drag-and-drop logic.
This includes defining the details of accessing and managing archive records.

Source: Ironclad
And once the process is active, the platform ensures that no document can bypass required sign-offs, closing the door on backdoor approvals or undisclosed terms.
ContractWorks similarly focuses on simplicity and security, offering quick search functionality across contract repositories, instant alerts for key milestones, and a dedicated e-signature dashboard.
Every signature and change can be verified, strengthening accountability across procurement and legal teams, while the process itself is made more efficient with e-sign templates.
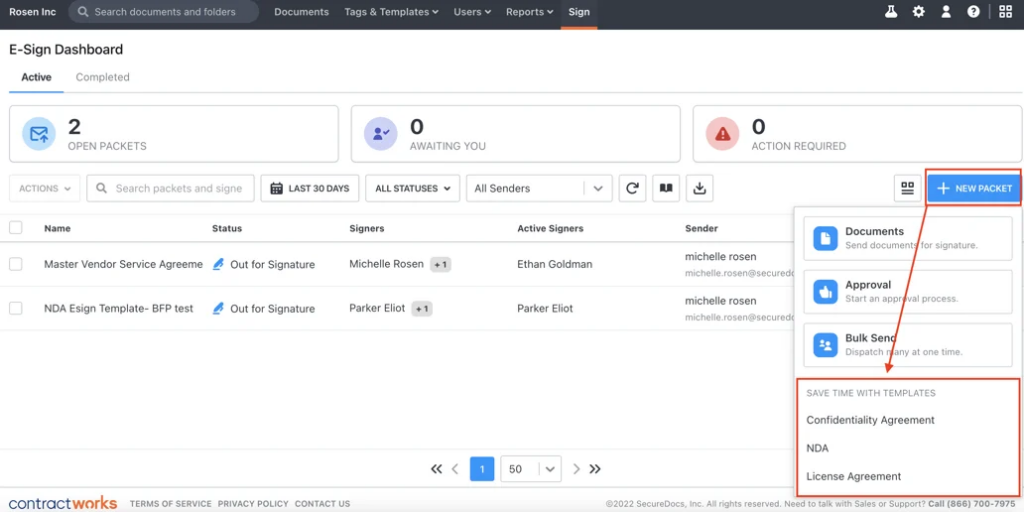
Source: ContractWorks
Meanwhile, CLM solutions like Icertis add an advanced analytics layer by linking contract data with enterprise systems like ERP and CRM.
You can visualize risk trends, monitor payment terms and compliance, and quickly detect any clause deviations.
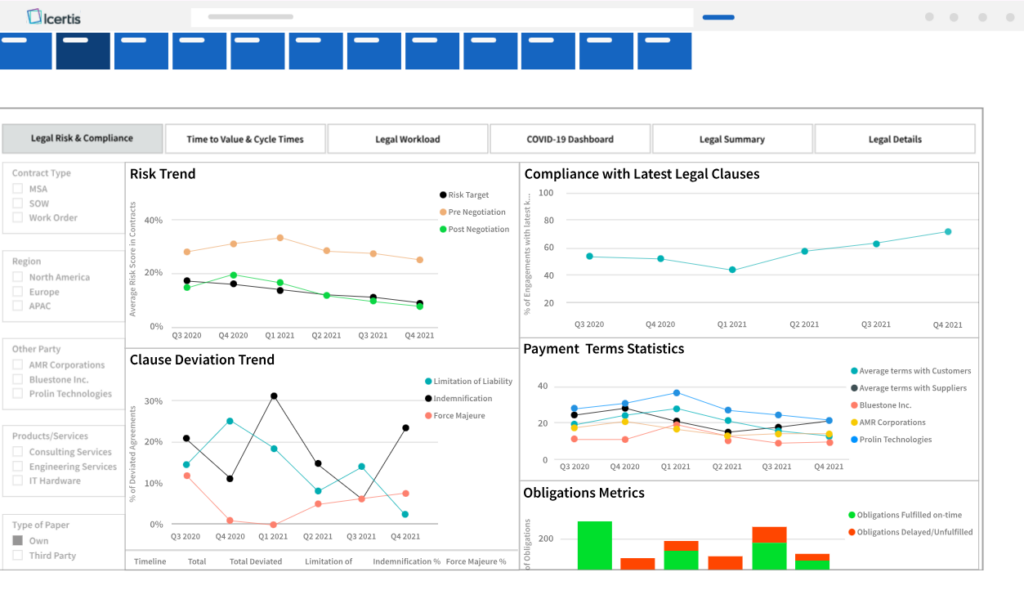
Source: Icertis
With intuitive dashboards and fresh insights, spotting inconsistent commercial terms and disadvantageous rebate structures, and flagging potential cases of fraud has never been easier.
Add to that new contract AI assistants like Icertis’ Vera that can instantly answer pressing questions and clarify contractual relationships, and it’s clear that these capabilities safeguard against manipulation while improving vendor transparency across your organization.
In the end, contract management software complements every other fraud prevention layer by tying vendor vetting, spend analysis, and fraud detection into a single, controlled framework.
Each software category we described in this article plays a distinct role in identifying and counteracting vendor fraud.
Vendor management and verification tools help build the foundation of trust, spend analysis and fraud detection solutions keep the flow of money transparent, while contract management ensures that every agreement can stand up to internal or external scrutiny.
Together, they form a continuous feedback loop of data and control.
So, equip your teams with systems that enhance efficiency and data accuracy, and your vendor management practices will form a proactive line of defense that prevents losses and protects your profitability.