7 Tips for a Successful Vendor Risk Assessment


Key Takeaways:
Your supply chain is only as secure as your weakest vendor.
With businesses managing an average of 88 third-party relationships, and large enterprises overseeing 170+, the stakes couldn’t be higher.
One compromised supplier can trigger data breaches, regulatory fines, operational shutdowns, and reputation damage that can take years to repair.
Yet most procurement teams are navigating with a foggy map, relying on outdated assessments and hoping for the best.
In this article, we’ll show you how to build a vendor risk assessment process that actually protects your supply chain: from objective-setting to automation and ongoing monitoring.
Running vendor risk assessments without clear objectives?
You’re essentially flying blind.
Most companies dive straight into generic questionnaires and compliance checklists, missing the fundamental question:
What specific risks could actually derail our operations?
This scattered approach turns what should be strategic risk management into administrative busywork.
And in procurement, busy work doesn’t just waste time. It also leaves you exposed.
The reality is, your vendor network carries multiple layers of risk at any given moment.
We’re talking regulatory compliance gaps, operational disruptions, reputational threats, financial instability, geographic vulnerabilities, cybersecurity weaknesses, and data privacy exposures.
Cybersecurity risk in particular became a huge issue during the COVID-19 pandemic, when companies were forced to forgo traditional security and vendor onboarding procedures.
Brian Alster, CEO of the people intelligence business Altrata, explains:

Illustration: Veridion / Quote: Institute for Supply Management
This reinforces how dangerous it can be to rush ahead with vendor onboarding, and how important it is to first establish a clear framework for what your risk assessments should deliver.
Without clear objectives guiding your assessment process, you’ll either miss critical risks entirely or spread your resources so thin that nothing gets the attention it deserves.
Effective vendor risk assessment starts with defining exactly what you’re trying to protect and prioritize.
You can see the main objectives every vendor risk assessment should cover in the image below:
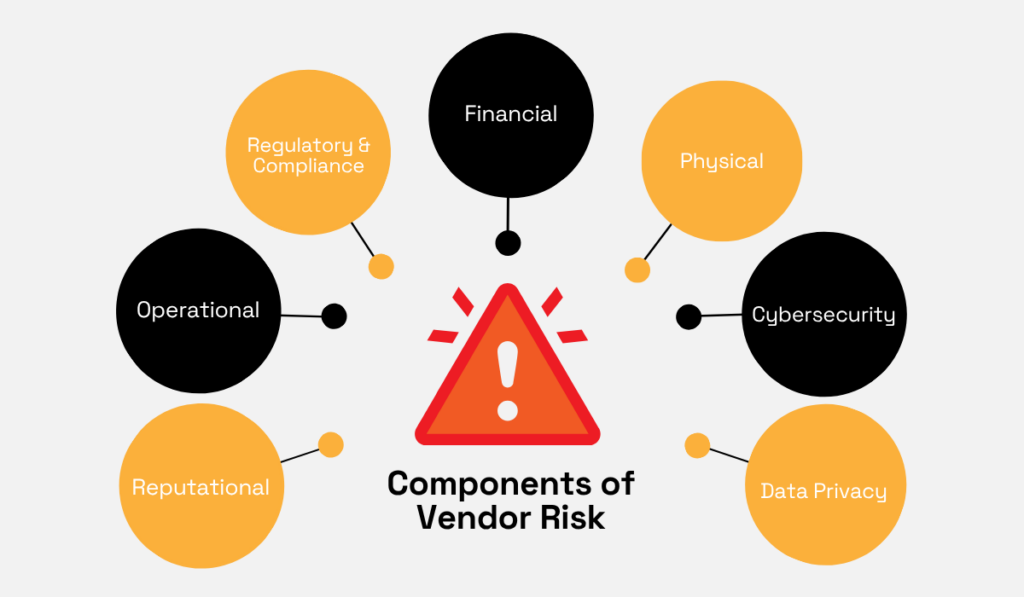
Illustration: Veridion / Data: Panorays
A vendor risk assessment only works when you know what you’re aiming for, so it’s important to set clear goals that will guide you in the right direction.
These goals will show you which suppliers deserve a closer look, instead of spreading effort thin across every partner.
Poorly defined objectives, on the other hand, can create serious problems.
In November 2024, Ahold Delhaize USA discovered that an external vendor’s file transfer system had been compromised.
Attackers accessed internal systems, exposing the personal data of over 2.2 million current and former employees.
Source: Security Week
The breach happened because their risk assessment objectives hadn’t clearly prioritized data protection requirements across every third party, especially those handling internal HR systems.
As a result, the risk was underestimated, oversight gaps went unaddressed, and preventive measures weren’t properly implemented.
Another example comes from Dior’s supply chain, which faced backlash in late 2024, after Italian authorities uncovered undocumented workers laboring in unsafe conditions at a subcontractor’s factory.
The scandal was especially damaging because the facility had already passed a vendor audit earlier that year.

Source: Lemonde
The audit objectives were set around formal compliance checkboxes, instead of uncovering deeper risks in subcontracting or worker treatment.
By prioritizing paperwork over uncovering hidden risks, Dior’s vendor risk program missed the real danger, costing the brand its reputation.
Next, let’s explore how to group vendors by risk level, so you can apply the right amount of scrutiny to each relationship.
Not all vendors carry the same level of risk.
Businesses typically manage 88 third-party relationships, while large enterprises exceed 170, which makes the risk significantly higher.
If you treat them all equally, you risk wasting resources on low-risk partners and overlooking the ones that could cause serious damage.
A smarter approach is vendor tiering: grouping suppliers by their risk profile to focus your efforts where they matter most.
Think of it like airport security.
A passenger carrying only a backpack might go through a quick check, while someone with checked luggage gets a deeper scan, because more baggage brings more risk.
Vendors work the same way.
A subcontractor that supplies office paper probably doesn’t need the same scrutiny as the cloud provider hosting your customer data.
But how do you decide which vendors deserve deeper attention?
First, look at access to sensitive data.
Vendors that handle payroll records, customer information, or financial transactions carry far more risk than those with little or no data exposure.
In fact, according to the 2025 Supply Chain Cybersecurity Trends report, 88% of CISOs and cybersecurity leaders flagged supply chain risk as a major concern.

Illustration: Veridion / Data: SecurityScorecard
Ultimately, the evidence tells a consistent story: supply chain vulnerabilities demand proactive, enterprise-level attention.
Next, consider the potential impact on operations.
Some vendors may never touch your data, but if they fail, whether through downtime, operational issues, staffing shortages, or a missed delivery, your supply chain can be brought to a stop.
Logistics providers, key parts suppliers, or cloud platforms are prime examples, because their stability directly affects your business continuity.
If they hit a bottleneck, miss a deadline, or suffer an outage, that disruption flows straight into your supply chain.
Finally, there’s vendor concentration risk, i.e., what happens when your business relies too heavily on a small number of critical suppliers.
This creates dangerous single points of failure across your entire operation.
Vendors can be grouped into four tiers, based on how critical they are to your business.
At the top are mission-critical vendors that require the strictest oversight, while those at the bottom only need light monitoring:
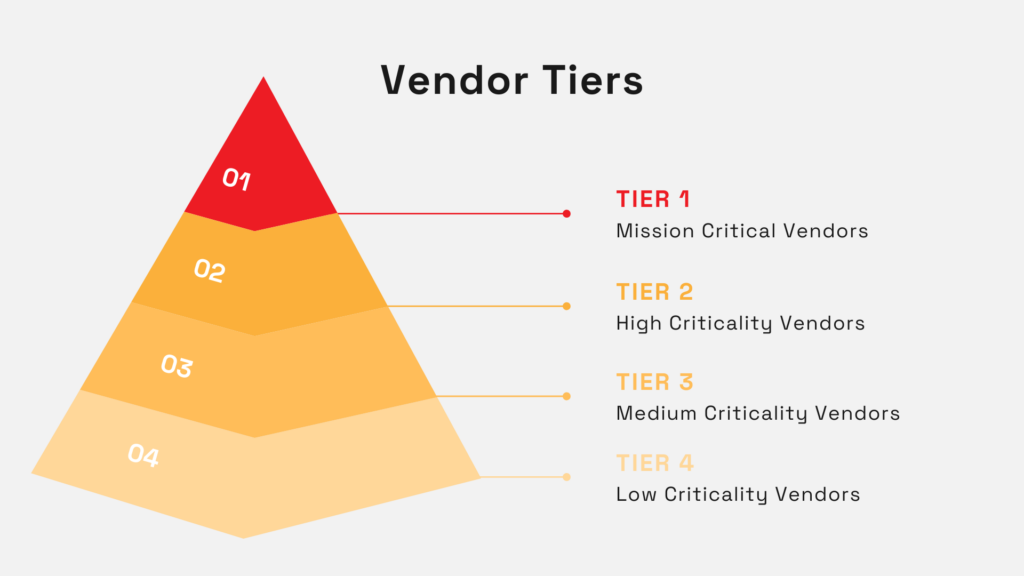
Illustration: Veridion / Data: Smarsh
This tiered approach ensures you’re applying the right level of scrutiny to each relationship.
Yet nearly 40% of businesses skip regular risk assessments, leaving themselves exposed to anything from supply chain disruptions to compliance failures that could have been prevented.

Illustration: Veridion / Data: Smarsh
Managing vendors without a clear assessment system can quickly become overwhelming.
You end up spending too much time on low-risk suppliers while the truly critical ones don’t get the attention they deserve.
Questionnaires serve as a crucial tool to gather comprehensive information from vendors.
They cover key factors such as financial stability, cybersecurity practices, compliance certifications, and operational procedures.
When vendors provide clear, detailed answers, you get an accurate picture of their risk profile and avoid unpleasant surprises down the road.
But when questions get skipped or answers lack substance, dangerous blind spots emerge that leave critical risks unchecked.
For example, the recent CrowdStrike supply chain incident is a stark reminder of why vague or incomplete vendor assessments are dangerous.
On July 19th, 2024, millions of Windows systems worldwide suddenly crashed with the dreaded Blue Screen of Death, shutting down businesses and critical services in an instant.
By the next day, Microsoft confirmed the cause: a faulty software update from CrowdStrike, a global cybersecurity provider.
Source: BBC
The fallout was massive.
More than 5,000 flights were canceled, and around 8.5 million computers were disabled across industries.
One vendor misstep rippled across the entire global economy.
That’s precisely why gathering detailed, specific responses is non-negotiable.
Because vendors, IT systems, and the cybersecurity landscape are constantly evolving, it’s essential to reassess vendors regularly through updated questionnaires.
But even the best questionnaires are only as effective as the framework you use to evaluate the responses.
Here’s a sobering reality: a significant portion of data breaches can be traced directly back to third-party vendors.
Data from the 2023 Global Third-Party Cybersecurity Breaches Report indicates that at least 29% of breaches involve a third-party entry point.

Illustration: Veridion / Data: SecurityScorecard
For that reason, vendor risk assessments are your first line of defense for protecting sensitive information across your entire supply chain.
Standards like NIST, ISO 27001, and industry-specific frameworks take the guesswork out of vendor evaluation and provide the consistency your program needs to actually work.
Why do these frameworks work so well in practice?
ISO 27001 is effective because it offers a structured, risk-based approach with 114 controls across 14 categories, covering everything from people and processes to technology.
It also includes dedicated third-party and supply chain controls, ensuring consistency and regulatory alignment.
As Andrew Pattison, Head of GRC Consultancy at IT Governance Europe, and ISO 27001 trainer, explains:

Illustration: Veridion / Quote: IT Governance
Put simply: trust your vendors, but rely on verification to keep your business secure.
NIST takes a flexible but rigorous approach by standardizing cybersecurity practices across vendors and including dedicated supply chain controls.
It enables consistent risk scoring, supports compliance, and improves overall organizational resilience.
In fact, for the second year in a row, NIST was ranked as the most valuable framework to 68% of cybersecurity practitioners in 2025.

Illustration: Veridion / Data: Cybersecurity Tribe
This shows just how central NIST has become for organizations aiming to strengthen their cybersecurity posture.
By mapping vendor responses against established benchmarks, you’ll get a consistent way to measure security posture across the entire supply base.
The bottom line is simple: frameworks create a common language for security that everyone understands.
Vendor risk assessment criteria put those frameworks into action by evaluating a vendor’s security protocols, regulatory compliance, and operational reliability.
While standards like ISO 27001 or NIST create a solid starting point, they must be tailored to fit each organization’s needs.
To fully capture risk, companies should adapt them to industry-specific requirements, whether that’s healthcare, finance, or critical infrastructure.
In the next section, we’ll explore how automation can eliminate the manual burden of vendor risk assessments.
Manual vendor risk assessments are resource killers.
They’re slow, error-prone, and drain your team’s capacity for strategic work that actually moves the needle.
Relying on manual spreadsheets and reports drags out the process and produces inconsistent results.
But automation transforms this administrative burden into a strategic advantage.
Instead of drowning in data entry and chasing vendors for updated information, your team can focus on analyzing high-risk relationships and developing actionable mitigation strategies.
The reality is that automation is only as strong as the data behind it.
This is where a solution like Veridion helps close that gap.
By providing verified market and vendor data, Veridion ensures that assessments are built on accurate, up-to-date information, rather than outdated spreadsheets or self-reported answers.
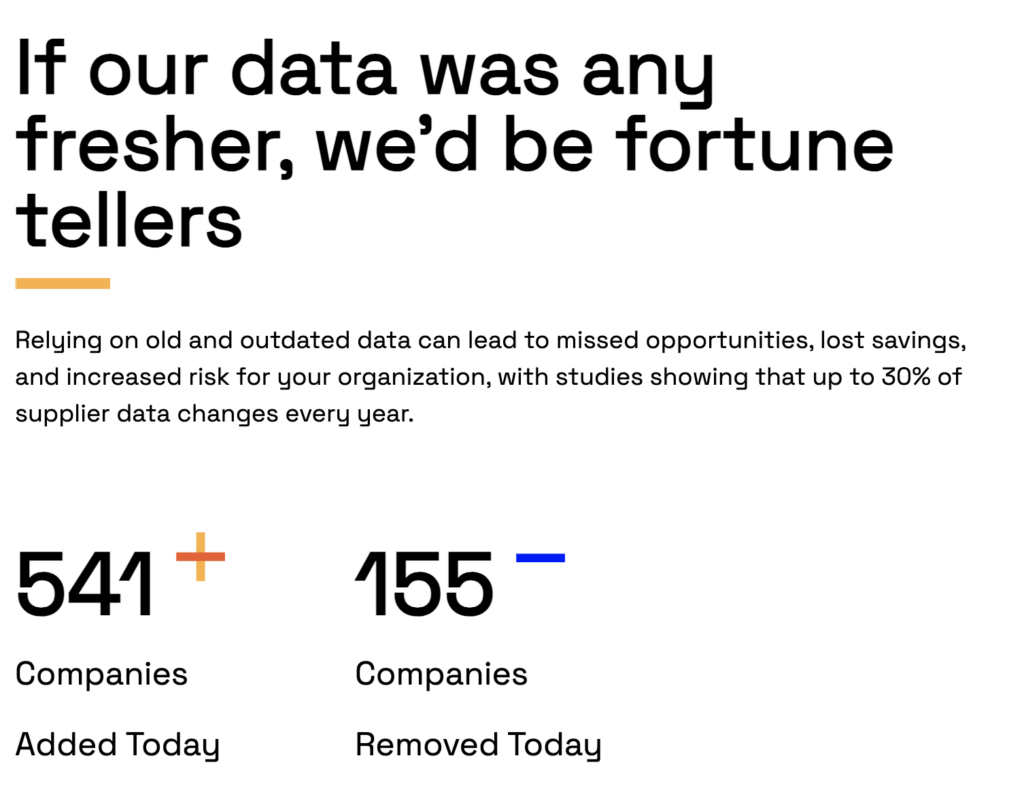
Source: Veridion
With fresh data delivered via API or batch files, teams can cut weeks of manual work into minutes, flag risks earlier, and score vendors with greater confidence.
The result is a faster, more accurate risk assessment process, and a supply chain that’s both agile and resilient.
Vendor risk isn’t static. It shifts as vendors change, threats evolve, and new regulations appear.
In other words, your assessments aren’t done after onboarding.
Instead, you need continuous monitoring to catch changes in vendor performance, compliance, or market conditions.
So how do you keep up with changes in your vendors?
Start by using vendor scorecards: structured tools that track performance across areas like service quality, security, and compliance.
They give you an objective, repeatable way to compare suppliers using the same criteria, instead of relying on gut instinct or scattered feedback.
And because everything is measured the same way, scorecards make it easier to spot early warning signs—missed SLAs, rising risk levels, slipping quality—before those issues turn into operational problems.
Here’s an example of what that looks like in practice.
A vendor scorecard that evaluates performance across key categories, each rated from 1 to 5, with 5 representing top-tier performance.
It gives teams a clean, structured snapshot of how a supplier is really doing:
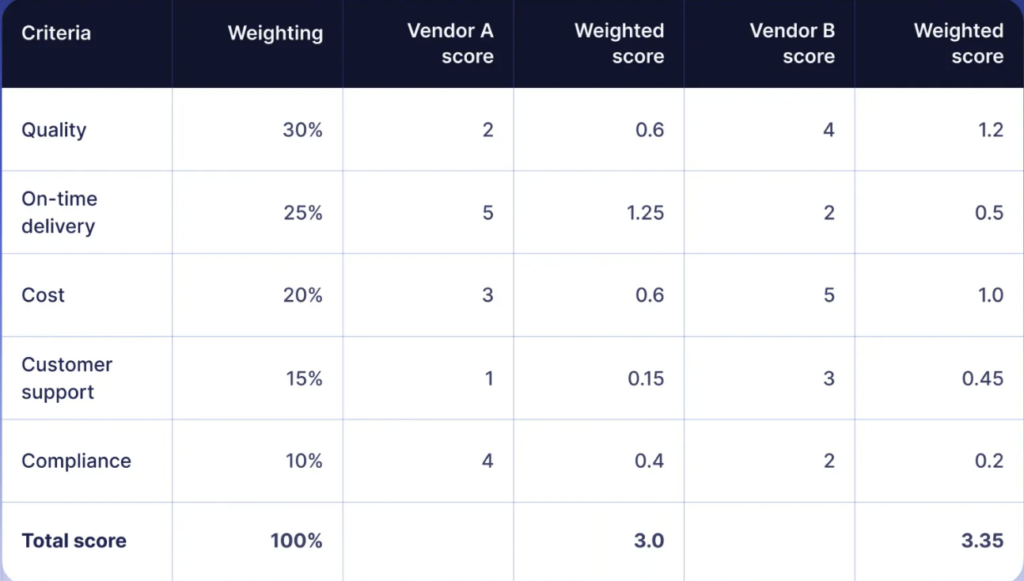
Source: Precoro
Next, set up automated alerts.
Continuous monitoring tools can flag real-time changes in a vendor’s security posture, compliance status, or exposure to breaches.
They’ll give your teams instant visibility into new vulnerabilities, expired certificates, policy violations, or threat-intelligence alerts that would normally go unnoticed between annual reviews.
This will allow you to react quickly: freezing access, requesting remediation, or escalating risk, before the issue impacts operations.
For example, UpGuard is a continuous monitoring platform that continuously scans vendors for security vulnerabilities, flags compliance gaps, and sends instant alerts the moment a vendor’s risk score changes:
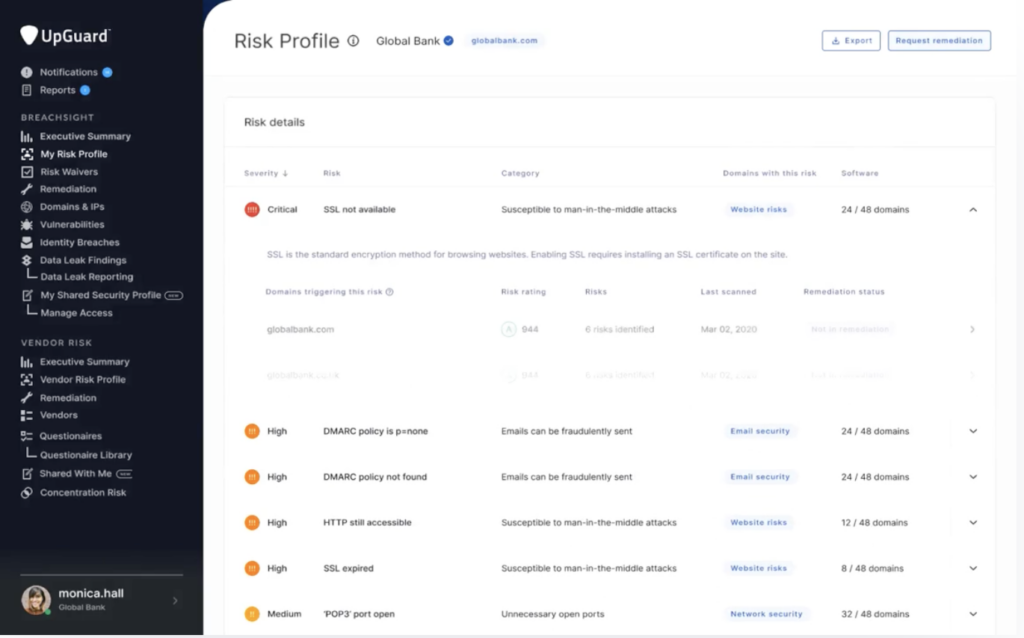
Source: Upguard
This is the kind of visibility that will let your team breathe easier, because you’re no longer discovering problems months later, but the moment they happen.
Finally, build in periodic reviews.
They act as intentional checkpoints: structured moments to step back, reassess the relationship, and verify that performance and risk levels haven’t shifted beneath the surface.
These reviews will ensure that decisions are based on current realities, not outdated assumptions.
As Amy S. Mushahwar puts it, effective vendor management has to stay dynamic:

Illustration: Veridion / Quote: Clinician
High-risk vendors need quarterly reviews, while low-risk ones can wait a year.
This approach keeps your team focused on real threats without wasting time on vendors that aren’t going anywhere.
Ongoing monitoring delivers one significant advantage: you catch problems while they’re still manageable.
Instead of discovering that a vendor’s financial situation collapsed months ago or learning about a compliance violation from an auditor, continuous tracking lets you spot trouble the moment it starts brewing.
That means you can address issues before they cascade through your supply chain, rather than scrambling to contain damage that’s already spread.
But even the best vendor monitoring means nothing if you’re not keeping pace with the regulatory landscape.
Regulations change fast.
New data privacy laws and security requirements can go from proposal to law with little warning.
When your vendor risk assessments stay tied to a fixed point in time, they stop being useful the moment that laws change.
This is especially applicable to global supply chains, where vendors operate across multiple regions and industries.
For example, the EU’s Corporate Sustainability Due Diligence Directive (CSDDD) is set to hold companies legally accountable for human rights and environmental risks across their supply chains, including third-party vendors.
Privacy laws are evolving just as quickly.
California recently expanded the CCPA/CPRA regulations, requiring businesses and their vendors to perform regular cybersecurity audits and risk assessments.
Similar shifts are happening worldwide: from GDPR enforcement in Europe to sector-specific laws like HIPAA in U.S. healthcare.
A notable example of what happens when organizations fail to keep pace with regulatory expectations came in November 2024.
So, what happened?
The UK’s ICO issued a provisional £6 million fine against Advanced Computer Software Group Ltd after a ransomware attack compromised the personal data of nearly 83,000 people.

Source: Doyle Clayton
The ICO determined that Advanced had not put adequate safeguards in place to protect sensitive healthcare data, including medical records, phone numbers, and even access details for the homes of 890 patients receiving in-home care.
For this reason, continuous oversight is necessary.
Ongoing vendor monitoring allows you to detect when compliance slips, regulations change, or contractual terms are at risk of being violated.
Without it, organizations can face not only financial fines but also reputational damage that can take years to repair.
Vendor risk assessment isn’t optional anymore. It’s key for business survival.
Many organizations have adopted security ratings and frameworks, but struggle with continuous monitoring and regulatory changes.
The solution is straightforward: implement these seven practices systematically.
Define clear objectives, tier vendors by risk, use proven frameworks, automate processes, and build in ongoing monitoring.
Your supply chain’s resilience depends on it.