What Is Vendor Risk Management Software


Key Takeaways:
As a procurement executive, you manage a complex web of vendor relationships on a daily basis.
These relationships, which span various functions such as IT, manufacturing, and logistics, are crucial for your organization’s operations.
And while these partnerships drive innovation and efficiency, they also introduce significant risks, from cybersecurity threats to compliance violations.
More significantly, a breach or failure at any one supplier can have a ripple effect throughout your business.
Vendor risk management (VRM) software is designed to tackle this challenge head-on.
In this article, we’ll explain what VRM software is, how it works, and why you need it.
Vendor Risk Management (VRM) software serves as a centralized solution that helps identify, assess, monitor, and mitigate risks associated with your third‑party vendors throughout their entire lifecycle.
It’s not just a tool, but a strategic asset in your risk management arsenal.
At its core, VRM software replaces manual, disjointed processes with automated workflows and centralized data repositories, giving you unparalleled visibility into your third-party risk posture.
VRM software is not just a digital version of manual processes. It’s a transformation.
It automates what used to be a paper‑driven, spreadsheet‑based process, bringing efficiency and accuracy to your vendor risk management.
VRM tools consolidate all your vendor information into a single platform, giving you clear visibility and control over your vendor ecosystem.
Think of VRM software as the central nervous system for your third-party risk management program.
A robust VRM platform typically covers:
For example, when you add a new vendor, the software can automatically send a security questionnaire, collect required documents (such as insurance certificates and audit reports), and apply a standardized risk scoring model.
It can also import external intelligence—such as credit ratings, regulatory watchlists, or data breach alerts—to flag any warning signs in real time.
By consolidating all vendor data into a single interface, VRM software creates a “single source of truth” for each vendor’s health and risk profile.
Source: Veridion
This unified approach makes it far easier to identify high-risk vendors, demonstrate compliance to auditors, and collaborate across procurement, security, legal, and finance teams.
In short, VRM software automates and streamlines vendor risk workflows that were once manual and fragmented, allowing you to manage your vendor ecosystem more efficiently and securely.
Even if you have a dedicated security team, managing vendors without specialized tools can be daunting.
The expansion of digital supply chains, increased regulatory scrutiny, and growing sophistication of cyber threats targeting third parties have made manual vendor risk management approaches both inefficient and dangerously inadequate.
Manual processes are also slow, prone to error, and rarely comprehensive.
So, let’s are three significant benefits of VRM software.
Manual vendor assessments can significantly slow down procurement cycles and delay critical projects.
When relying on spreadsheets and email exchanges, security reviews can take weeks or even months to complete.
In fact, research shows that supplier onboarding typically takes about one month, but can stretch to six months at large companies.
Each step, from gathering forms to chasing signatures and verifying data, takes time.
VRM software accelerates this process by automating questionnaires, streamlining document collection, and applying AI-powered analysis to vendor submissions.
One case study found that a dedicated vendor portal cut onboarding time by over 80%.
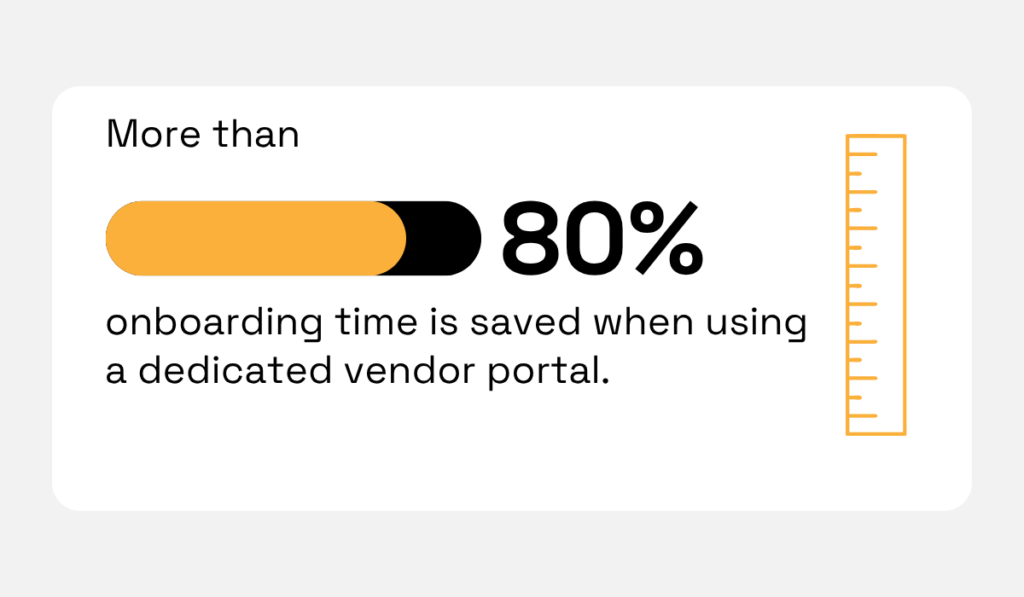
Illustration: Veridion / Data: HICX
That level of efficiency translates directly to operational agility: buyers get the supplies and services they need on schedule, and your projects aren’t held up by paperwork.
In short, VRM software accelerates procurement without sacrificing due diligence.
Vendor risk is not static.
A once-trusted supplier can become a liability if its circumstances change.
Issues like financial distress, a data breach, legal trouble, or even a geopolitical event affecting its region can quickly expose your organization to new risks.
Traditional point-in-time assessments create dangerous visibility gaps between review cycles.
As one industry report revealed, 80% of legal and compliance leaders identified third-party risks only after the initial onboarding and due diligence process.
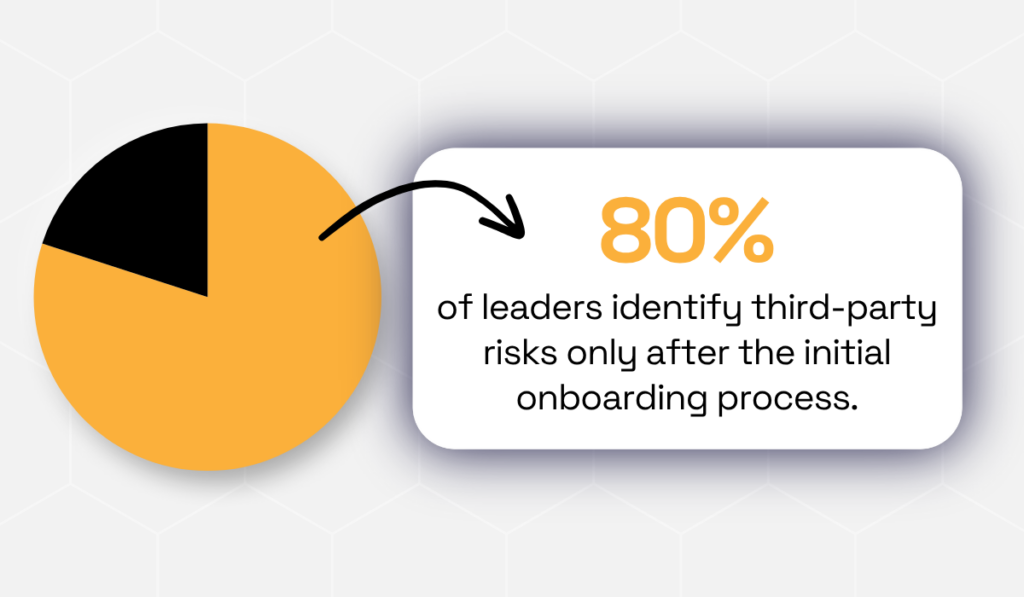
Illustration: Veridion / Data: Gartner
Just recently, the Federal Communications Commission ordered AT&T to pay $13 million after a prior vendor experienced a hacking incident exposing customer data.
AT&T and the vendor had an agreement that the vendor would destroy or delete this information years ago.
However, the vendor didn’t do so, and AT&T did not identify this failure, even after reviewing and assessing the vendor after offboarding.
VRM tools fill such gaps with ongoing monitoring and alerts.
They continuously gather fresh data and notify you of any concerning events, providing you with peace of mind and early detection of potential issues.
This proactive stance is vital because vendors may appear low‑risk on day one, but can accumulate vulnerabilities over time.
As Richard Lowe, a prolific writer of business books, puts it:

Illustration: Veridion / Quote: Smartsheet
With the cost of data breaches involving vendors averaging $370,000 more than other types of breaches, this persistent surveillance delivers substantial financial protection.
By spotting vendor issues early, you can renegotiate terms, require remediations, or even offboard the vendor to protect your company.
Without VRM software, critical vendor data lives in pieces: paper spreadsheets on someone’s desk, PDFs in email, notes on shared drives.
This fragmentation leads to the challenges outlined in the image below.
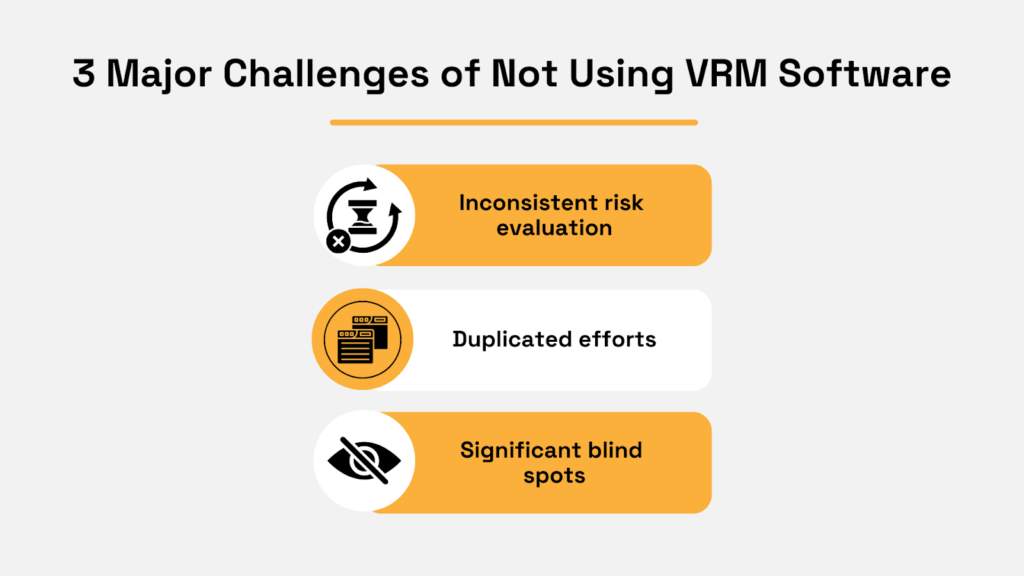
Source: Veridion
VRM software, on the other hand, establishes a centralized command center for all vendor-related information, documents, and communications.
This single source of truth improves visibility, enhances cross-functional collaboration, and strengthens accountability across your organization.
In practice, this means executives and stakeholders see the same dashboards of who’s compliant, who’s high-risk, and who needs attention.
Centralization ensures accountability, allowing procurement, security, and business units to collaborate on vendor issues instead of operating in silos.
In short, a centralized VRM system turns a patchwork of records into a unified source of truth for vendor risk.
Together, these benefits—speed, vigilance, and visibility—make VRM software essential.
Not all VRM platforms are created equal.
When evaluating VRM solutions for your enterprise, several critical capabilities should guide your selection process.
Let’s explore those next.
Look for systems that provide configurable risk assessment models with automated scoring capabilities.
A good VRM solution automatically computes a risk score for each vendor.
It pulls together multiple data inputs, including the vendor’s financial health, compliance certifications, cybersecurity rating, and even geopolitical factors.
By quantifying risk, the system removes subjective bias and speeds up decision-making.
Source: Veridion
For instance, the platform might combine a vendor’s latest revenue figures with industry attack trends to generate a numerical risk score.
Automated scoring models also let you set risk thresholds: any vendor above a specific score triggers a defined action, like enhanced due diligence.
This automation reduces the subjectivity inherent in manual assessments while ensuring consistency, as all vendors are evaluated by the same criteria every time.
By transforming complex risk profiles into standardized scores, these systems enable you to quickly identify high-risk vendors requiring immediate attention and prioritize resource allocation accordingly.
Effective VRM software should seamlessly connect with reliable external data sources for vendor verification, compliance validation, and real-time intelligence gathering.
These integrations enrich your internal assessments with broader market intelligence, ensuring your risk evaluations remain current and comprehensive.
This connectivity is particularly valuable for maintaining accurate vendor records.
Research by Tealbook shows that 93% of supply chain and procurement managers have experienced adverse effects from supplier misinformation.
According to Matt Palackdharry, Founder of Kinetic Brands, trusted supplier information is essential.

Illustration: Veridion / Quote: Tealbook
Without proper vendor information, organizations lose the ability to be agile when supply chains become overwhelming.
By integrating with external data providers, VRM systems can automatically validate and refresh vendor information, protecting your organization from decisions based on outdated or incorrect data.
For example, automatically linking to a corporate registry API can verify that a vendor is legitimate, while a cybersecurity feed can flag if that vendor has just experienced a breach.
By integrating fresh external data, VRM software ensures your vendor profiles are current.
Veridion‘s own data is an excellent example of this.
The platform maintains continuously updated company profiles for millions of companies worldwide, providing data on firmographics, financial metrics, industry codes, ESG scores, and more.
These can feed directly into a VRM platform.
Source: Veridion
By coupling Veridion’s high-quality business data with a VRM tool, you get a more comprehensive risk picture and real-time insights on each vendor.
This improves verification and risk scoring accuracy.
Ultimately, integrating such external intelligence means you spend less time hunting data and more time acting on it.
Seek out platforms that offer configurable alert systems that immediately notify relevant stakeholders when a vendor’s risk profile changes significantly.
Why is this important?
Because changes can happen fast, and the ability to receive instant alerts when they do is a game-changer.
For instance, if a vendor is affected by a data breach or undergoes a management shake-up, a VRM system can immediately flag this in your dashboard and notify your team.
These alerts give you precious lead time to act.
You might suspend the vendor’s access, demand remediation, or switch to an alternate supplier before your project suffers.
Simply put, real-time alerts shrink the window of exposure.
Without them, you might only learn of problems months after they occur. With them, your response is proactive rather than reactive.
Furthermore, catching disruptions early can protect you from expensive emergency measures.
You’ll have enough time to, for instance, adjust delivery schedules, source materials from alternative suppliers, or change transportation routes.
By ensuring the right people receive timely intelligence about vendor issues, these notification systems help your organization prevent disruptions before they impact your operations.
Robust reporting capabilities are essential for demonstrating program effectiveness, meeting regulatory requirements, and informing strategic decision-making.
So, look for solutions that offer dashboards you can customize and detailed analytics that visualize risk trends, track KPIs, and document compliance activities.
With advanced reporting features, you can generate comprehensive reports tailored to various stakeholders.
This includes anything from detailed risk assessments for your technical teams to executive summaries for board-level review.
For example, dashboards may display trends in vendor risk over time, counts of high-risk vendors by region, or the average time to remediate issues.
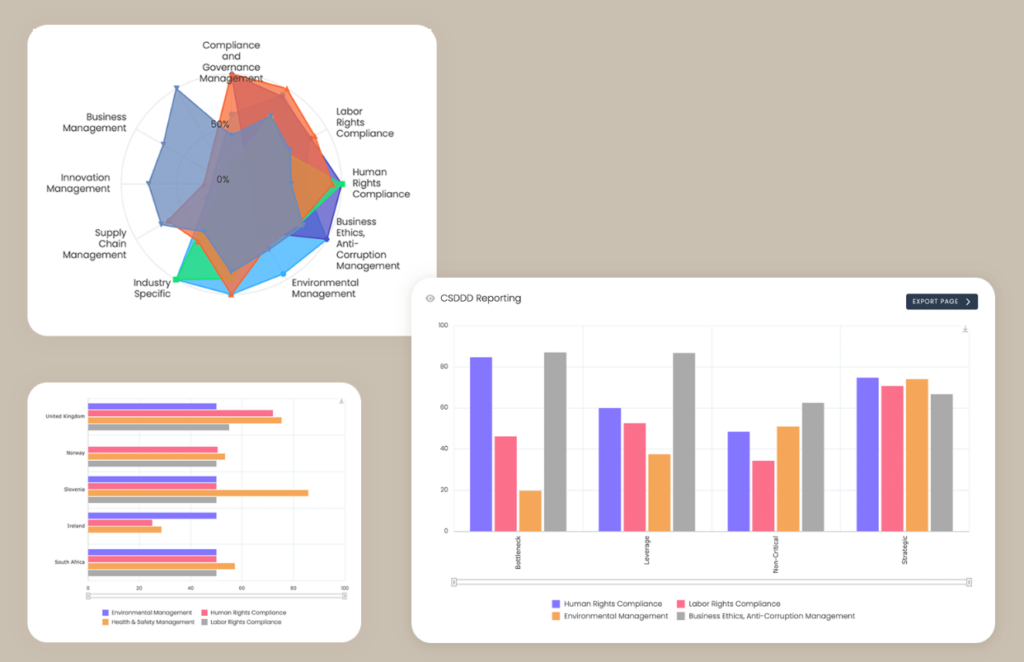
Source: Kodiak Hub
This transparency strengthens both strategic planning and regulatory readiness, ensuring you can quickly produce evidence of your due diligence processes during audits or examinations.
In practice, VRM reporting tools let you generate audit-ready reports at the push of a button, which is a powerful advantage over email chains.
Ultimately, robust analytics and visualization transform raw data into actionable insights, showing you not just where risk is today but also how it’s changing.
Vendor risk management software has evolved from a compliance necessity to a strategic enabler in modern business operations.
By centralizing vendor data, automating labor-intensive processes, and providing real-time risk intelligence, VRM tools empower procurement leaders to make more informed decisions, accelerate safe onboarding, and protect their organizations from third-party threats.
Don’t wait until a vendor lets you down. Start building your VRM program now.
Get a solution that seamlessly integrates into your existing workflows while providing the depth of insight that will empower your procurement team to move swiftly and securely.